Oneadvupfordesign.com ads (spam) - Free Guide
Oneadvupfordesign.com ads Removal Guide
What is Oneadvupfordesign.com ads?
Oneadvupfordesign.com is a bogus site created by crooks to generate revenue from pop-up ads
Oneadvupfordesign.com is a fraudulent website that was created by scammers with the intention of making money through pay-per-click advertising. The site employs social engineering[1] tactics to trick users into clicking the “Allow” button. It displays a deceptive message claiming that users must confirm that they are not robots.
Despite the implication that allowing notifications will grant access to the site's content, the page contains no other content. Instead, users are bombarded with obnoxious pop-up advertisements, which can appear even after the browser has been closed.
| NAME | Oneadvupfordesign.com |
| TYPE | Push notification spam; adware |
| SYMPTOMS | Pop-up ads start appearing in the corner of the screen after the “Allow” button is pressed |
| DISTRIBUTION | Shady websites, deceptive ads, redirects, freeware installations |
| DANGERS | Links embedded in the push notifications can lead to dangerous websites where users can be tricked into providing their personal information and suffer from monetary losses |
| ELIMINATION | Users can block push notifications via browser settings |
| FURTHER STEPS | It is recommended to use a repair tool like FortectIntego after the removal to fix any remaining damage |
Distribution methods
If one is not cautious, browsing the internet can be a dangerous activity. Crooks are constantly on the lookout for new ways to exploit the vulnerabilities of unsuspecting users, and they frequently do so via shady websites. These sites are difficult to detect and may appear legitimate at first glance, but they can cause significant harm to users' devices and personal information.
To avoid these risks, it is critical to follow the safe browsing security guidelines recommended by experts. Avoiding unregulated and suspicious websites, such as illegal streaming sites, is one of these guidelines. These websites are well-known for their deceptive advertisements and hidden redirects, which can lead users to shady websites or infect their devices with malware.
Look for warning signs, such as URLs that do not match the site's content or excessive pop-up ads, to help you identify these websites. Furthermore, users should ensure that their devices have reliable antivirus software installed and that it is kept up to date in order to protect against known threats.
Social engineering techniques
Crooks use various messages and images to gain trust and appear legitimate. Users often encounter messages, like:
Press Allow to verify your age is 18+
Click Allow to watch the video
Download is ready. Click Allow to download your file
Press Allow to verify that you are not a robot
The ultimate goal of these sentences is to trick users into subscribing to push notifications unknowingly. The method used is to prompt users to confirm that they are not robots, similar to how captcha verification works. This, however, is a scam tactic, as a legitimate verification process would not require users to click “Allow” on a browser prompt.
Once users have agreed to receive notifications, fraudsters can begin earning money in a variety of ways. Unfortunately, these criminals may employ rogue advertising networks that feature advertisements that direct users to dangerous websites. Users may be directed to fraudulent websites that attempt to obtain personal information, promote potentially unwanted programs (PUPs),[2] or even install malware. These malicious activities can result in financial losses, identity theft, and operating system damage.
Clear your browsers
Cookies can be used to track users' browsing activity on nearly every website they visit. Cookies are small data files that can store information like the user's IP address, geolocation, links clicked, and online purchases. This information could be sold to advertising networks or other third parties, raising serious concerns about user privacy and security.
Because of these risks, security experts strongly advise users to clear their browser data, including cookies, on a regular basis. A maintenance tool like FortectIntego can automatically delete cookies and cache, optimize the system, and repair any damage left behind, which is especially useful after a virus infection. This tool can assist users in maintaining their online privacy and security.
Block Oneadvupfordesign.com notifications
Because push notifications are subscription-based, they can be turned on and off only manually. We have a detailed guide for the most popular browsers below:
Google Chrome (desktop):
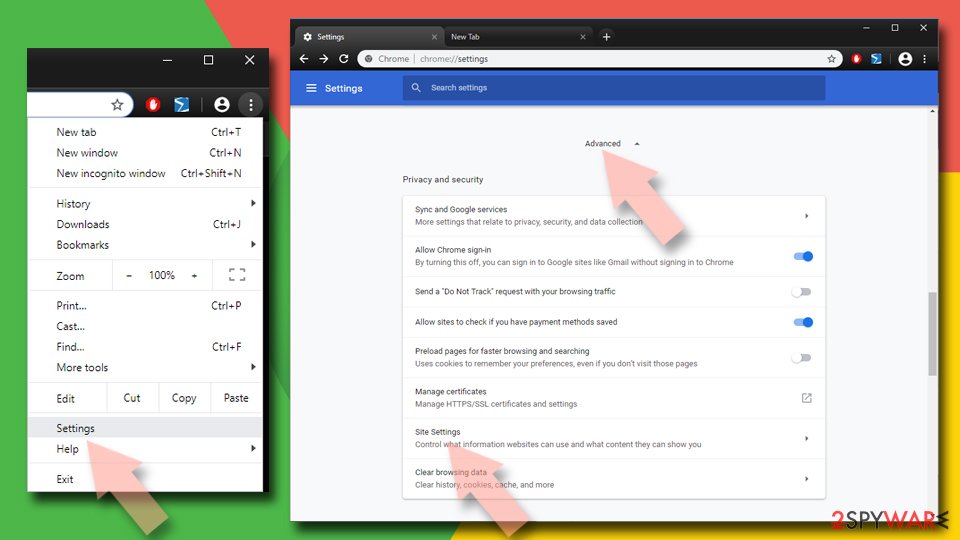
- Open Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
![Stop notifications on Chrome PC 1 Stop notifications on Chrome PC 1]()
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Google Chrome (Android):
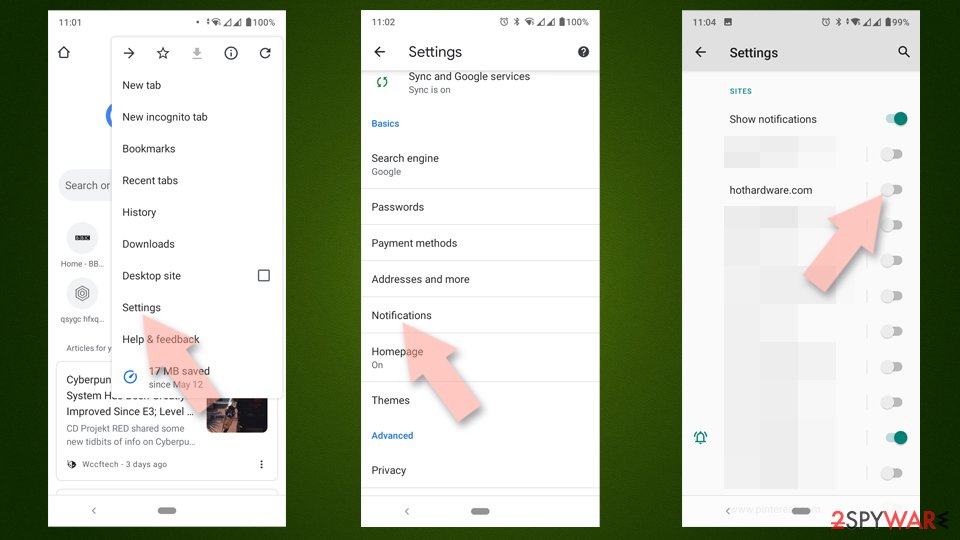
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).
![Stop notifications on Chrome Android Stop notifications on Chrome Android]()
Mozilla Firefox:
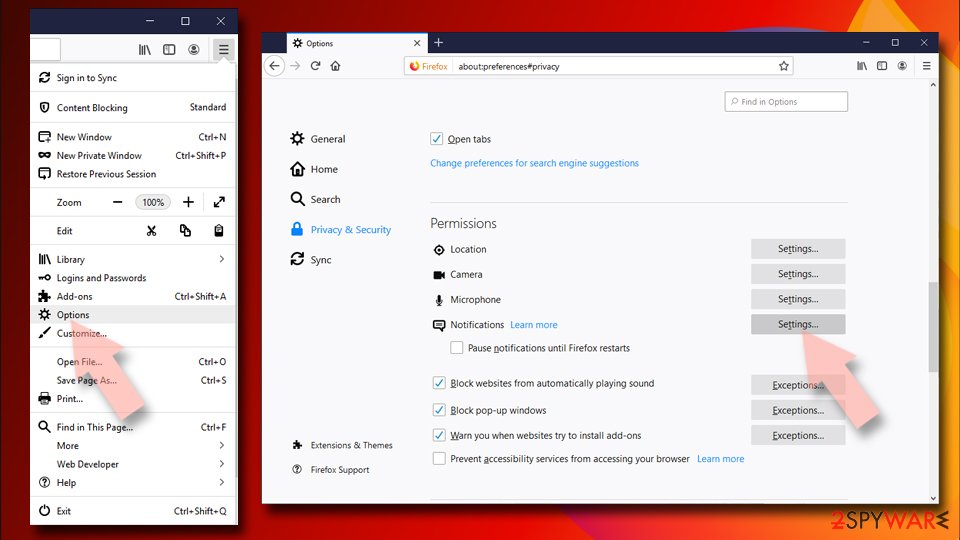
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click Settings button next to it.
![Stop notifications on Mozilla Firefox 1 Stop notifications on Mozilla Firefox 1]()
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
Safari:
- Click on Safari > Preferences…
- Go to Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
MS Edge:
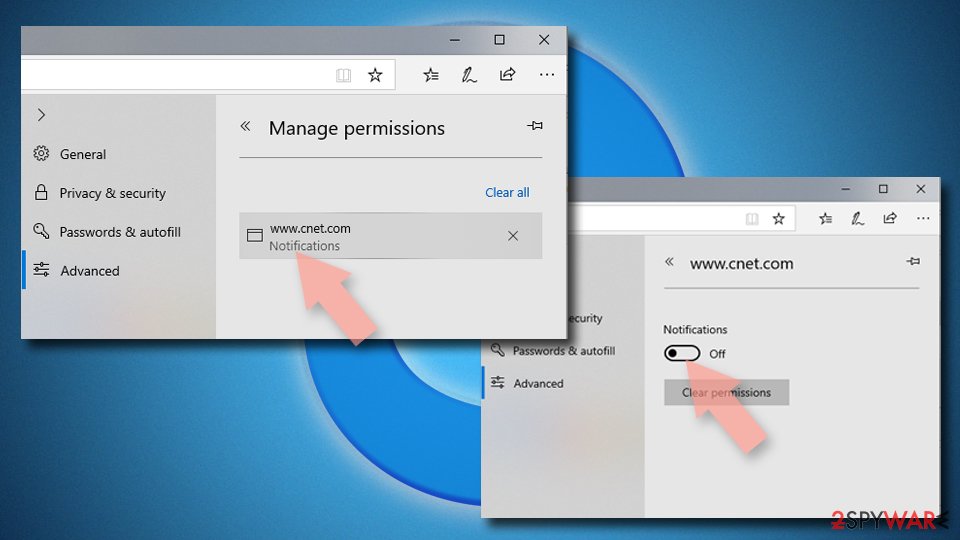
- Open Microsoft Edge, and click the Settings and more button (three horizontal dots) at the top-right of the window.
- Select Settings and then go to Advanced.
- Under Website permissions, pick Manage permissions and select the URL in question.
- Toggle the switch to the left to turn notifications off on Microsoft Edge.
![Stop notifications on Edge 2 Stop notifications on Edge 2]()
MS Edge (Chromium):
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
Check your machine for adware
Undesirable browser behavior can often be attributed to Potentially Unwanted Programs (PUPs). In some cases, pages like Oneadvupfordesign.com may appear without any user interaction, which is often caused by adware[3] – a program that can generate commercial content, including pop-ups, banners, and redirects. Many adware programs are disguised as “useful” tools, making them harder for the average user to detect.
To combat these issues, it is crucial to have professional security tools such as SpyHunter 5Combo Cleaner and Malwarebytes. Anti-malware software can scan the computer and detect any suspicious processes running in the background. It can also prevent infections by alerting users to potentially harmful files attempting to enter the system. However, for those who prefer to take matters into their own hands, we have provided step-by-step instructions for both Windows and Mac machines:
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.
![Uninstall from Windows 7/XP Uninstall from Windows 7/XP]()
- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Social Engineering. Imperva. Learning Center.
- ^ Chris Hoffman. PUPs Explained: What is a “Potentially Unwanted Program”?. Howtogeek. Technology Magazine.
- ^ Adware. Malwarebytes. Cybersecurity Basics.