OnlineClient Mac virus (Tutorial)
OnlineClient Mac virus Removal Guide
What is OnlineClient Mac virus?
OnlineClient is malware that should be removed from a Mac as soon as possible

OnlineClient is a rogue application that targets Mac users. It belongs to a widespread malware known as Adload, which has numerous versions released since its launch in 2017. These variants are delivered at a rapid pace, and there are little to no changes between them when it comes to their distribution and operation, although some visual variations in the icon used or a few technical details are present.
Just like its previous versions TrackFrequency or ProgressionLegion, the OnlineClient virus is primarily spread using malicious installers downloaded from pirated software distribution sites. Another known delivery method is using fake Flash Player update prompts, which many people confuse to be legitimate.
Once installed, the malware establishes persistence and installs the OnlineClient browser extension on Safari or another used browser. This allows the virus to use its adware/browser hijacker[1] component – change homepage and new tab settings, set a different search provider, and insert ads on various websites that users browse.
| Name | OnlineClient |
| Type | Mac virus, adware, browser hijacker |
| Family | Adload |
| Installation | Pirated software installers, fake Flash Player updates, misleading ads |
| What it does |
|
| Removal | The easiest way to eliminate unwarned and malicious software on Macs is by performing a full system scan with security software. Manual instructions are also provided below |
| System optimization | Malware and adware can meddle with your system, reducing its performance. If you want to quickly fix various issues, we recommend you try using automated tools like FortectIntego |
How Adload variants are spread and how to avoid them
Adload managed to become one of the most prevalent adware strains for Macs. It reached this status by using effective distribution methods, which, surprisingly, includes users installing the virus themselves. The below methods are very simple yet proven to be extremely successful, and hundreds of users get infected with Adload virus variants daily.
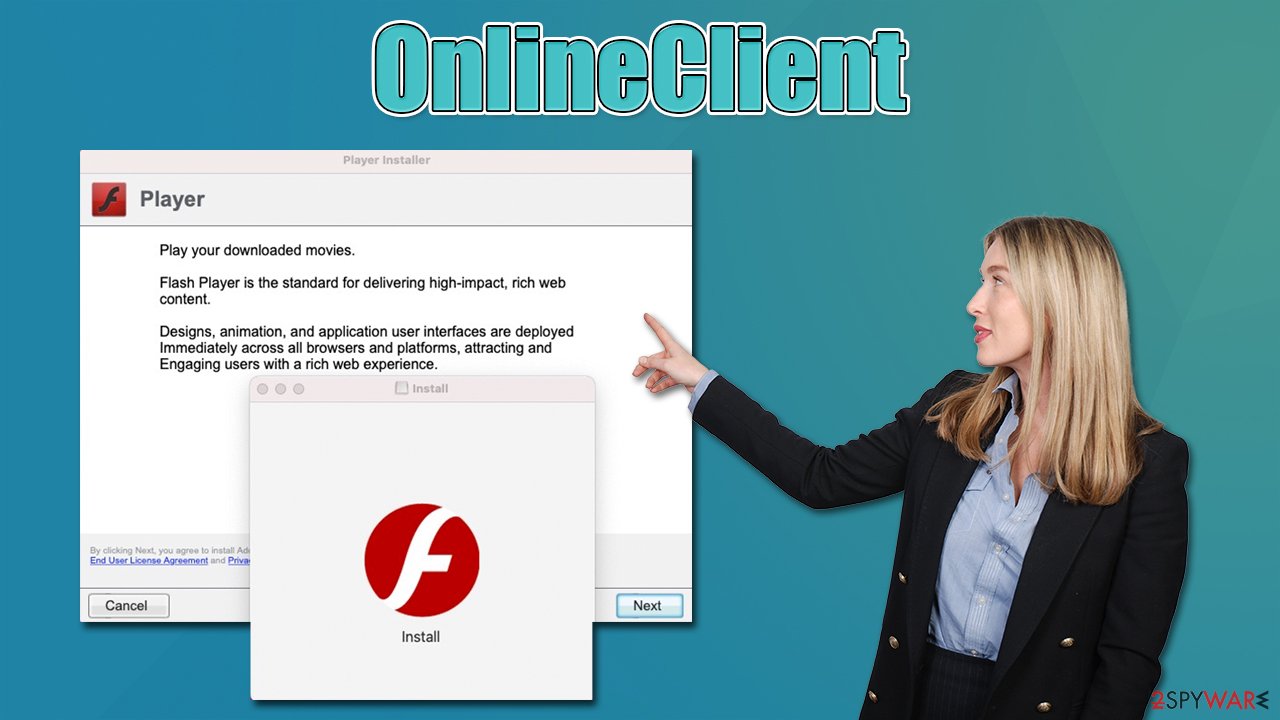
Fake Flash Player update or install prompts
Flash Player is an iconic software released by Adobe in 1996, which served as the main component which allowed multimedia playback on the internet for many years. This is why so many users are familiar with the plugin, as the newest versions were required to access some content online or play the latest Flash games.
However, the software is known to be extremely flawed, and cybercriminals constantly abuse its vulnerabilities. Due to its prevalence, Flash is constantly used in various scam and phishing campaigns. For that reason, Adobe discontinued the plugin at the end of 2020, and all the requests to install it are fake.
Pirated software installers
Users visit torrents, software cracks, peer-to-peer networks, and similar places in order to bypass the licensing process if otherwise paid application. This way, they are able to install the app for free. However, not only is that illegal and might result in fines or similar issues, it poses a great security risk.
Malware can be disguised as useful applications or may be bundled into a standalone installer. For example, you may believe that you are installing a pirated app, only to find out later that you also installed OnlineClient as well.
OnlineClient removal explained
As soon as users enter their AppleID to install the malicious app, it uses the built-in AppleScript to establish a multitude of malware-related components on the system, which includes new profiles, login items, PLIST files, and much more. This allows the virus to run at elevated permissions, avoiding detection of the built-in Mac defenses.
Therefore, we strongly recommend you perform a full system scan when trying to remove the OnlineClient Mac virus – using SpyHunter 5Combo Cleaner or Malwarebytes security software is a good idea. Using one of these tools can help you to eliminate the infection automatically, and you could skip the manual instructions below (with the exception of the browser cleansing process).
Stop malware-related processes and remove the main app
In order to prevent malware from interfering with a smooth elimination, you should first stop all the malicious processes that could be running on behalf of malware:
- Open Applications folder
- Select Utilities
- Double-click Activity Monitor
- Here, look for suspicious processes and use the Force Quit command to shut them down
Your next step is to find and remove the main application installed on your device:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
However, this step might fail due to other active components in the background. Namely, you should go to the Preferences > Accounts > Login items folder and remove all the related items. Additionally, you should check for malicious profiles in the System Preferences > Users & Groups > Profiles section.
Once that is complete, you should delete the remaining files that belong to the ConnectedPlatform virus.
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- Look for any suspicious entries in the Application Support folder and delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
Delete Login Items and unwanted Profiles
The OnlineClient virus creates new items in the Profiles and Login items sections to perform its malicious activities. They can be found and removed from the following locations:
- Go to Preferences and pick Accounts
- Click Login items and delete everything suspicious
- Next, choose System Preferences > Users & Groups
- Find Profiles and remove unwanted profiles from the list.
Remove the leftover files
Plist files are configuration files that might enable adware to work more efficiently and result in reinfection. Find and remove them at once:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any malicious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
Take care of the browser extension
Web browsers are important tools for adware to fulfill its functions. With the help of an extension, it can deliver promotional campaigns and gain financial benefits from sponsored links and ads in the process. The first task is to eliminate the malicious extension from the browser:
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Note that you might not be able to remove the extension due to its persistence[2] mechanisms used by malware. In this case, we recommend resetting the browser:
Safari
- Click Safari > Preferences…
- Go to the Advanced tab.
- Tick the Show Develop menu in the menu bar.
- From the menu bar, click Develop, and then select Empty Caches.
![Reset Safari Reset Safari]()
Google Chrome
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.
![Reset Chrome 2 Reset Chrome 2]()
If the extension was removed successfully, make sure you clean the web browser's caches in order to prevent tracking cookies[3] from doing their job:
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Browser hijacking. Wikipedia. The free encyclopedia.
- ^ Common Techniques by Which Malware Makes Itself Persistent. Lifars. Cyber Security.
- ^ Cookies and Web Beacons. NTT. NTT Communications.








