Poaz ransomware (virus) - Free Instructions
Poaz virus Removal Guide
What is Poaz ransomware?
Poaz ransomware is a dangerous computer virus that stems from a well-established malware family known as Djvu
Ransomware attacks continue to pose significant threats to individuals and organizations worldwide, with one of the latest players being the Poaz ransomware. A variant of the notorious Djvu malware family, Poaz utilizes an RSA encryption algorithm, rendering all files inaccessible to the user.
This invasive software makes its presence known by appending a .poaz extension to each encrypted file. After the malicious operation, it leaves a file named “_readme.txt” on the victim's computer. This text file delivers the ultimatum: pay a ransom amounting to $490 or $980 to regain access to the encrypted files. For communication purposes, crooks provide two email addresses that victims should use for contact:
- datarestorehelp@airmail.cc
- support@freshmail.top
While the urgency to restore files might push victims to consider paying the ransom, this is not a course of action we advise. Succumbing to the demands of these cybercriminals not only funds their illicit activities but also offers no guaranteed solution. Often, payments are made with no restoration of access, or worse, additional malware is deployed.
Fortunately, there exist alternative solutions to this problem. Multiple methods and resources can aid in removing the malware from your system and possibly recovering your data. These procedures vary in complexity and effectiveness based on several factors, such as whether or not the data was encrypted with an online or offline ID.
The following sections provide detailed information on how to deal with the Poaz ransomware attack. This includes instructions for malware removal and suggestions for data recovery.
| Name | Poaz virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .poaz extension affixed to all personal files, rendering them useless |
| Family | Djvu |
| Ransom note | _readme.txt dropped at every location where encrypted files are located |
| Contact | support@freshmail.top and datarestorehelp@airmail.cc |
| File Recovery | Without backups, there's no foolproof recovery method for encrypted files. Options include: paying the ransom (not advised due to potential monetary loss), using Emisoft's decryptor tool (limited success) or third-party recovery software |
| Malware removal | After disconnecting the computer from the network and the internet, do a complete system scan using the SpyHunter 5Combo Cleaner security program |
| System fix | Upon installation, the malware can inflict significant damage to critical system files, leading to system instability issues like crashes and errors. The automatic repair of any such damage is feasible with the use of FortectIntego PC repair |
Ransom note overview
Ransom notes are a critical component of ransomware attacks. Cybercriminals often use them as a tool to communicate their demands, outline their terms, and sometimes instill fear or urgency. The delivery of these digital missives marks the transition from a covert operation to an overt threat. In the case of Djvu variants like Poaz, ransom notes are largely similar, with variations typically present in the contact details.
The ransom note for the Poaz ransomware reads:
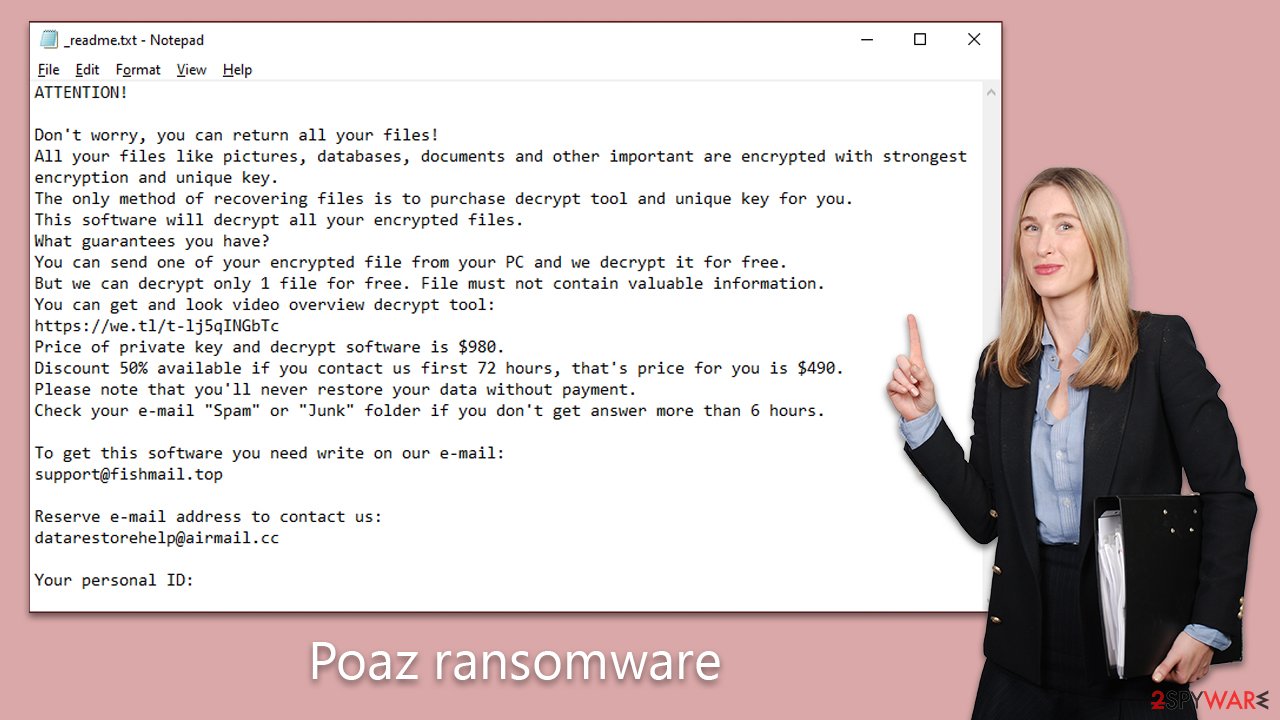
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-rmxjMZAZBJ
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshmail.topReserve e-mail address to contact us:
datarestorehelp@airmail.ccYour personal ID:
As part of their strategy, attackers often use persuasive language to convince victims that paying the ransom is the only way to recover their encrypted files. The ransom note states that all files have been encrypted with the 'strongest encryption and unique key,' and a decrypt tool must be purchased to restore the files. The attackers even offer a “guarantee” by promising to decrypt one file for free, an attempt to provide a false sense of assurance.
The ransom demand is set at $980, with a 50% discount if the victim reaches out within the first 72 hours. This reduction is a common tactic used to pressure victims into making quick and often hasty decisions.
However, paying the ransom is a grave mistake. First, it does not guarantee that you will get your files back. The hackers are criminals, and their promises are inherently unreliable. Second, by paying the ransom, you are financing further criminal activities, reinforcing their success, and encouraging future attacks. Finally, even if you pay and get your files back, the ransomware may still reside in your system, and the attackers could strike again. Consequently, finding alternative methods to remove the malware and restore your files is strongly recommended.
How to deal with ransomware
When dealing with ransomware such as Poaz, it's crucial to understand that the malware may not always be completely purged from the system after it has encrypted the data. Sometimes, it may leave behind modules that continue to pose a risk. Moreover, it's common for ransomware to be bundled with other malicious software. For instance, previous versions of Djvu were known to come coupled with the Vidar Trojan, adding an extra layer of threat to the infected system.
Given this, the first step in malware removal should be to disconnect the system from the internet to prevent further spread or damage. Then, the user should initiate a full system scan using reputable security software such as SpyHunter 5Combo Cleaner or Malwarebytes. These software solutions are equipped with advanced features capable of detecting and removing various forms of malware, including ransomware and Trojans.
In addition to this, it is advised to navigate to the following location on your system:
- C:\Windows\System32\drivers\etc
Here, users should locate and delete the “hosts” file. Ransomware often modifies this file to block access to specific websites, typically those offering guidance or solutions for malware removal and data recovery. In addition, it is recommended to run a scan with a powerful PC repair tool FortectIntego, which is capable of restoring damaged Windows files and making sure that the system operates flawlessly. Otherwise, you might experience crashes or other instability issues.
After ensuring that the malware and all associated threats have been thoroughly removed, users can then focus on data recovery. It is vital to ensure that all traces of the ransomware have been eradicated before beginning this process to avoid further data loss or re-encryption. More information about data recovery will be provided in the subsequent section. This phased approach – malware removal followed by data recovery – offers the most secure path toward reclaiming your digital assets.
Possible .poaz files recovery solutions
Understanding the nature of ransomware-induced data encryption is crucial to debunking common misconceptions about the effects of a ransomware attack. When files are encrypted by ransomware like Poaz, they are not irreversibly damaged or altered at their core. Instead, the files are effectively 'locked' using a unique key — a complex series of characters that, when applied correctly, can unlock or decrypt the affected files.
This key is generated and held by the cybercriminals behind the ransomware attack. The premise of their ransom demand is the promise to provide this key in exchange for payment. However, as previously mentioned, succumbing to these demands often does not result in the desired decryption, and it reinforces the criminal's activities.
Another common misconception is the belief that security software can restore encrypted files to their original state. It's crucial to note that while security software plays a vital role in the removal of malware from infected systems, it does not have the capability to decrypt files. The primary function of security software is to detect and eradicate malicious entities, preventing further damage. It isn't designed to reverse the sophisticated encryption algorithms applied by ransomware.
Since this malware is a part of the large Djvu family, a description tool produced by Emsisoft researchers is available. However, certain things must be true for this to work – other victims must have retrieved the key from cybercriminals, and the files must have been locked with an offline ID.
- Download the app from the official Emsisoft website.
![Poaz ransomware Poaz ransomware]()
- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.
![Poaz ransomware Poaz ransomware]()
- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
![Poaz ransomware Poaz ransomware]()
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.
![Poaz ransomware Poaz ransomware]()
- Press Decrypt.
![Poaz ransomware Poaz ransomware]()
From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
If this method proves unsuccessful, you can consider turning to specialized data recovery software as an alternative recourse.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Poaz ransomware Poaz ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.