Proton ransomware (virus) - Recovery Instructions Included
Proton virus Removal Guide
What is Proton ransomware?
Proton ransomware is a malicious program that is used by cybercriminals to extort money
Proton ransomware is a file-locking virus that prevents users from opening personal files such as photos, videos, documents, and other files. After the malicious program has infiltrated the computer, files are encrypted using complex algorithms.
The affected files are labeled with the email address kigatsu@tutanota.com, the victim's ID, and the .kigatsu extension. Typically, victims become aware of the infection during this time. The file names are something like picture.jpg.[tutanota.com][546735HY].kigatsu, video.mp4.[Kigatsu@tutanota.com][538993YH].kigatsu, and the icons become white pages, making thumbnails unavailable.
The malware then creates a text file called README.txt. This is known as a ransom note. In the note, hackers explain what happened to victims' data and request payment in exchange for a decryption key. Ransomware attacks can be catastrophic for those who do not have backups. To avoid this in the future, we recommend that you thoroughly read the guide.
| NAME | Proton |
| TYPE | Ransomware, cryptovirus, data locking malware |
| DISTRIBUTION | Email attachments, peer-to-peer file-sharing platforms, malicious ads |
| FILE EXTENSION | .kigatsu |
| RANSOM NOTE | README.txt |
| FILE RECOVERY | It is almost impossible to recover the files if you do not have backups |
| MALWARE REMOVAL | Scan your machine with anti-malware software to eliminate malicious files. This will not recover your files. |
| SYSTEM FIX | Windows reinstallation can be avoided with FortectIntego maintenance tool, which can fix damaged files |
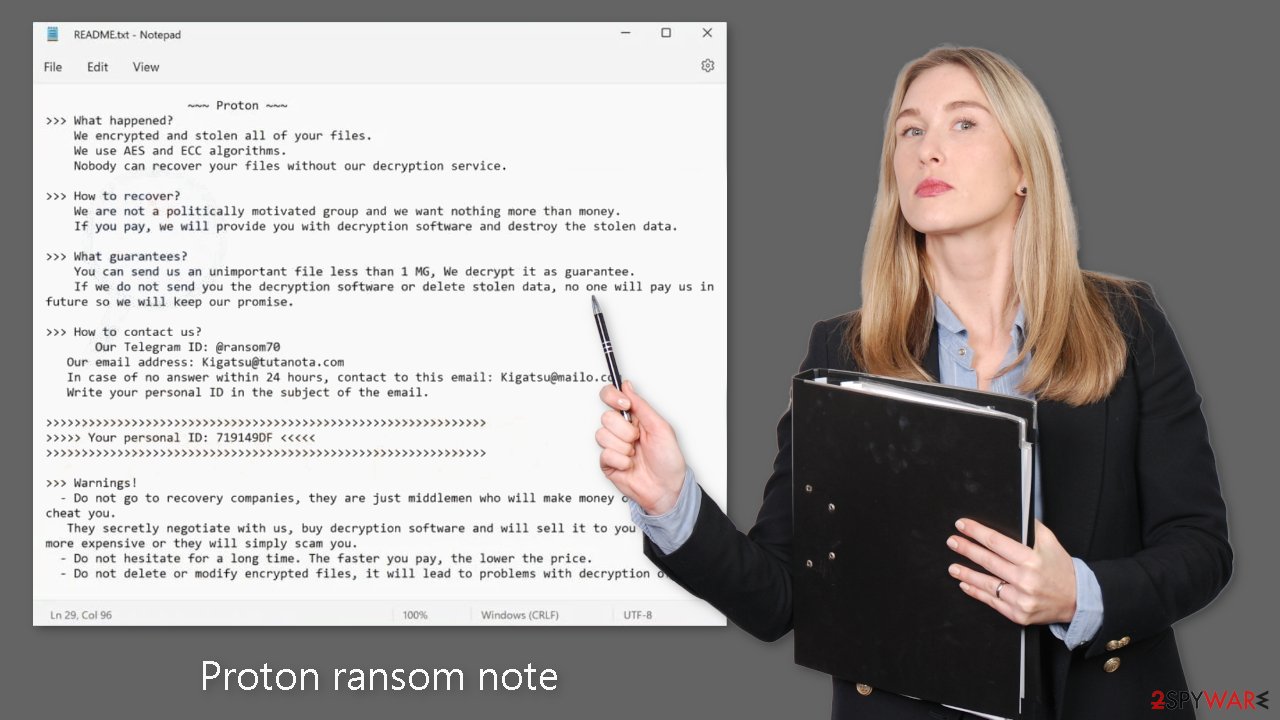
The ransom note
Proton ransomware drops a README.txt ransom note on the affected machine:
~~~ Proton ~~~
>>> What happened?
We encrypted and stolen all of your files.
We use AES and ECC algorithms.
Nobody can recover your files without our decryption service.>>> How to recover?
We are not a politically motivated group and we want nothing more than money.
If you pay, we will provide you with decryption software and destroy the stolen data.>>> What guarantees?
You can send us an unimportant file less than 1 MG, We decrypt it as guarantee.
If we do not send you the decryption software or delete stolen data, no one will pay us in future so we will keep our promise.>>> How to contact us?
Our Telegram ID: @ransom70
Our email address: Kigatsu@tutanota.com
In case of no answer within 24 hours, contact to this email: Kigatsu@mailo.com
Write your personal ID in the subject of the email.>>>>> Your personal ID: – <<<<<
>>> Warnings!
– Do not go to recovery companies, they are just middlemen who will make money off you and cheat you.
They secretly negotiate with us, buy decryption software and will sell it to you many times more expensive or they will simply scam you.
– Do not hesitate for a long time. The faster you pay, the lower the price.
– Do not delete or modify encrypted files, it will lead to problems with decryption of files.
The ransom note is a message from the Proton ransomware group in which they claim to have encrypted and stolen all of the victim's files using advanced encryption algorithms such as AES and ECC. If the victim pays the ransom, the note promises to provide decryption software.
The group emphasizes that they are not political in nature and that their only goal is to obtain money from the victim. They provide reassurance by allowing the victim to send a small file (less than 1 MB) that they will decrypt as proof that they have the decryption software.
The ransom note warns the victim not to contact recovery companies because they are considered middlemen who will cheat and profit from them. The group also advises the victim not to wait too long because the ransom price will rise over time. Finally, they warn the victim not to delete or modify any encrypted files, as this will cause decryption problems.
Victims should not pay the ransom because there is no guarantee that the group will provide the decryption software once payment is received. The group's claim that they will destroy the stolen data is also untrustworthy, given that they have already shown that they can encrypt and steal the victim's data. Paying the ransom only helps criminals and may not result in the recovery of the victim's files.
Distribution methods
Cyber criminals spread malicious programs through a variety of methods, including email attachments, fake software updates, unofficial websites offering “cracked” programs,[1] and peer-to-peer file-sharing platforms. When downloading email attachments, especially from unknown senders, exercise extreme caution.
Fake software updates frequently contain malware and should be avoided. Never update software via a web browser; instead, go to the official software page or open the program itself to check for available updates. It is also critical not to download anything from random pop-ups.
Exploiting software vulnerabilities[2] is another method used by cybercriminals to distribute ransomware. It is critical to keep both the operating system and software up to date to prevent hackers from exploiting security flaws. Software developers release security patches that address known vulnerabilities on a regular basis, so it is best to install them as soon as possible.
Ransomware removal
Attempting to recover data on your own may lead to permanent loss or further encryption of your files by malicious programs. To stop the encryption process, it is necessary to remove the malicious files causing it. However, it is not recommended to try removing the program yourself. Instead, use reliable anti-malware tools such as SpyHunter 5Combo Cleaner or Malwarebytes to scan your system.
These security software programs are designed to detect and remove all related files and entries automatically, ensuring complete removal without leaving any traces behind. Sometimes, malware can disable your antivirus software, making it difficult to remove the malicious program. In such cases, it is recommended to access Safe Mode first, which will provide a secure environment to run anti-malware tools and remove the threat.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.
![Update & Security Update & Security]()
- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.
![Recovery Recovery]()
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
![Press F5 to enable Safe Mode with Networking Press F5 to enable Safe Mode with Networking]()
File recovery using third-party software
If you have not backed up your files prior to the encryption, only the hackers possess the decryption key that can unlock them. This means that without the key, your files may be lost permanently. Although third-party data recovery software can be attempted, it may not always be successful in decrypting the files. We recommend attempting this method as a last resort.
Before proceeding with data recovery, it is crucial to remove the Proton ransomware and make a copy of the encrypted files to a USB flash drive or another storage device. It is important to note that this should only be done after removing the ransomware.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Proton ransomware Proton ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Fix the operating system
Malware infections can cause significant performance, stability, and usability issues on a computer, to the extent that a full Windows reinstall may be necessary. Such infections can manipulate the Windows registry database, damage critical bootup and other sections, and delete or corrupt DLL files. Once a system file is damaged by malware, antivirus software may not be able to restore it.
To address this problem, FortectIntego was developed. It is designed to repair a variety of damage caused by malware infections, such as Blue Screen errors,[3] freezes, registry errors, and damaged DLLs, which can render a computer completely unusable. By utilizing this maintenance tool, it is possible to avoid the need for a complete Windows reinstallation.
Getting rid of Proton virus. Follow these steps
Isolate the infected computer
Some ransomware strains aim to infect not only one computer but hijack the entire network. As soon as one of the machines is infected, malware can spread via network and encrypt files everywhere else, including Network Attached Storage (NAS) devices. If your computer is connected to a network, it is important to isolate it to prevent re-infection after ransomware removal is complete.
The easiest way to disconnect a PC from everything is simply to plug out the ethernet cable. However, in the corporate environment, this might be extremely difficult to do (also would take a long time). The method below will disconnect from all the networks, including local and the internet, isolating each of the machines involved.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
If you are using some type of cloud storage you are connected to, you should disconnect from it immediately. It is also advisable to disconnect all the external devices, such as USB flash sticks, external HDDs, etc. Once the malware elimination process is finished, you can connect your computers to the network and internet, as explained above, but by pressing Enable instead.
Report the incident to your local authorities
Ransomware is a huge business that is highly illegal, and authorities are very involved in catching malware operators. To have increased chances of identifying the culprits, the agencies need information. Therefore, by reporting the crime, you could help with stopping the cybercriminal activities and catching the threat actors. Make sure you include all the possible details, including how did you notice the attack, when it happened, etc. Additionally, providing documents such as ransom notes, examples of encrypted files, or malware executables would also be beneficial.
Law enforcement agencies typically deal with online fraud and cybercrime, although it depends on where you live. Here is the list of local authority groups that handle incidents like ransomware attacks, sorted by country:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Georgina Torbet. 5 Security Reasons Not to Download Cracked Software. Makeuseof. Lifestyle Magazine.
- ^ Danny Palmer. The 25 most dangerous software vulnerabilities to watch out for. Zdnet. Computer Security.
- ^ Blue screen of death. Wikipedia, the free encyclopedia.

















