Qoqa ransomware (virus) - Free Instructions
Qoqa virus Removal Guide
What is Qoqa ransomware?
Qoqa ransomware is a type of malware that tries to extort money from you
Qoqa is a malicious computer program that encrypts all personal files, such as photos, videos, databases, documents, and more, rendering them inaccessible. The virus employs the RSA encryption algorithm, which makes the files unusable until they are decrypted using a key that is kept on the cybercriminals' servers.
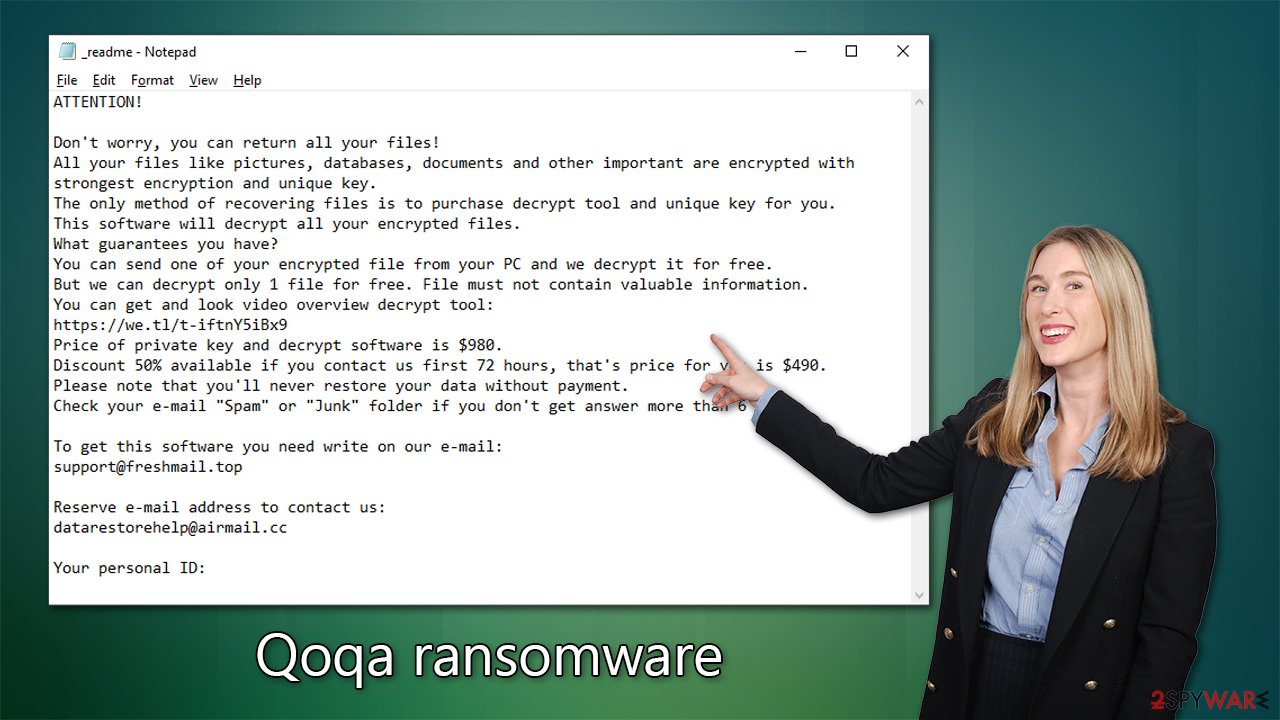
The virus appends the .qoqa extension to the personal files, and their usual file icons disappear, making it impossible for users to open them. A Windows error message pops up, indicating that the file is unrecognizable. The cybercriminals who launched the attack take advantage of the situation and demand payment of $490/$980 in bitcoin to restore access to the encrypted data. They also provide email addresses, support@freshmail.top and datarestorehelp@airmail.cc, for communication.
The Djvu malware family includes over 600 variants, such as Iowd, Vvoo, Mztu, and many others. In this article, we'll talk about how to cope with the hazardous Qoqa infection and provide guidance on how to recover encrypted files without paying the cybercriminals.
Such threats are known for spreading via software cracks and pirating platforms. You should avoid any content and downloads from suspicious sources. More serious threats like Vidar or Raccoon that steal data from users can spread the same way and silently. Later on, ransomware and other threats get to access infected machines quickly after the initial injections.
| Name | Qoqa virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .qoqa appended to all personal files, preventing users from opening them |
| Family | Djvu |
| Ransom note | _readme.txt |
| Ransom size | $480/$980 |
| Contact | support@freshmail.top and datarestorehelp@airmail.cc |
| File Recovery | There is no guaranteed way to recover locked files without backups. Other options include paying cybercriminals (not recommended, might also lose the paid money), using Emisoft's decryptor (works for a limited number of victims), or using third-party recovery software |
| Malware removal | After disconnecting the computer from the network and the internet, do a complete system scan using the SpyHunter 5Combo Cleaner, Malwarebytes security program |
| System fix | As soon as it is installed, malware has the potential to severely harm some system files, causing instability problems, including crashes and errors. Any such damage can be automatically repaired by using FortectIntego PC repair |
The ransom note example and what the attackers want
After a device is infected with ransomware, a ransom note appears on the user's screen. The note provides details on how to pay a specified ransom amount in exchange for the decryption of data encrypted by malicious software. The ransom note displayed by the virus demands payment in the form of cryptocurrency, such as Bitcoin, and includes instructions on how to make the payment. Here are the contents of the message:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-iftnY5iBx9
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshmail.topReserve e-mail address to contact us:
datarestorehelp@airmail.ccYour personal ID:
We cannot stress enough that it is strongly advised not to pay the ransom demanded by ransomware attackers. There is no guarantee that they will follow through with their promises or that the decryptor they provide will work as intended. By paying the ransom, victims indirectly support criminal activity and encourage the attackers to continue spreading their malicious software to more unsuspecting users. This, in turn, fuels the development of more advanced forms of ransomware and increases the risk of further attacks.
How malware spreads
Malicious hackers may use various methods to distribute the Qoqa virus, although it is commonly spread through cracked software installers from illegal websites. Regardless of the distribution method, victims often unknowingly download the virus and remain unaware until they observe the initial symptoms of infection.
To protect yourself from being infected with ransomware like Qoqa, it is important to take certain precautions. First, avoid downloading and installing software from untrusted or illegal websites, as these are common sources of malware. Stick to reputable sources for software downloads and be wary of any offers for free software or services that seem too good to be true.
Secondly, make sure to keep your operating system and other software up to date with the latest security patches and updates. This helps to close any known security vulnerabilities that could be exploited by cybercriminals.
Lastly, it is essential to regularly back up your important files to an external hard drive or cloud storage service. This way, even if your system is infected with ransomware, you can still access your files and restore them after removing the virus.
A lot to unpack: do not panic
Many people infected with Qoqa ransomware might not truly realize what has happened, as many victims do not expect an attack to happen. In fact, many might not even know what ransomware is. Indeed, a ransomware attack could end in total file loss, and it can be devastating for many.
If you have been infected with ransomware, it is crucial not to panic, despite the harsh implications of the fact. The attackers behind ransomware rely on the victim's fear and desperation to force them to pay the ransom. However, paying the ransom does not guarantee the safe return of your data, and it may encourage the attackers to continue their illegal activities. Instead, it is essential to remain calm and assess the situation.
How to deal with ransomware
When confronted with a ransomware attack, the initial response should be to remove the malware from the computer. Since the malware may communicate with the attackers via the internet, the first step is to disable the WiFi or Ethernet connection to stop further data exchange. After that, antivirus software such as Malwarebytes or SpyHunter 5Combo Cleaner can be downloaded and used to clean the infected computer thoroughly.
It's worth noting that in some cases, malware can prevent the operation of security software to ensure that it continues to encrypt files or run other malicious activities in the background. In such cases, accessing Safe Mode may be necessary to remove the ransomware from the system.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
![Recovery Recovery]()
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
Windows systems can suffer significant damage from malware, sometimes necessitating a complete reinstallation. Infections can cause harm by modifying the Windows registry database, damaging bootup files and other critical components, removing or corrupting DLL files, and more. Unfortunately, antivirus programs are unable to recover damaged system files, so specialized software like FortectIntego is recommended as one of the best solutions available.
Data recovery options
It is important to understand that security software is not capable of restoring personal files that have been encrypted by ransomware. Its primary function is to detect and remove malicious programs and protect against future threats. Recovering encrypted data requires a completely different approach that cannot be done by anti-malware software alone. Nonetheless, installing security software on your device is crucial for detecting potential issues and safeguarding your system against threats.
Once ransomware infects a device, it generates a unique ID and encryption key that is sent to the attackers. The attackers will then demand payment in exchange for the decryption key needed to access the encrypted data. However, paying the ransom is not recommended as it supports the attackers' malicious activities and does not guarantee that the decryption key will work.
Instead of paying the ransom, alternative solutions are available such as using decryption tools. Before attempting to restore encrypted data, it is essential to create a backup copy, as the recovery process may cause corruption. One such decryption tool is Emsisoft, which may or may not successfully restore your files.
- Download the app from the official Emsisoft website.
![Qoqa ransomware Qoqa ransomware]()
- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.
![Qoqa ransomware Qoqa ransomware]()
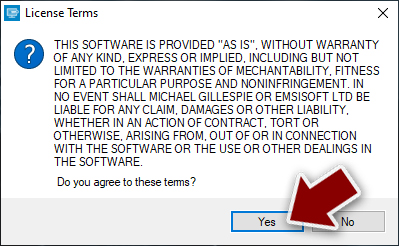
- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
![Qoqa ransomware Qoqa ransomware]()
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.
![Qoqa ransomware Qoqa ransomware]()
- Press Decrypt.
![Qoqa ransomware Qoqa ransomware]()
From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
If this method does not work, try other solutions listed below. Don't forget to remove the “hosts” file from your system as well, as you won't be able to access certain websites on the web otherwise.
Getting rid of Qoqa virus. Follow these steps
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Find a working decryptor for your files
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains such as Djvu or Dharma use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you can't find a decryptor that works for you, you should try the alternative methods we list below. Additionally, it is worth mentioning that it sometimes takes years for a working decryption tool to be developed, so there are always hopes for the future.
Restore Windows "hosts" file to its original state
Some ransomware might modify Windows hosts file in order to prevent users from accessing certain websites online. For example, Djvu ransomware variants add dozens of entries containing URLs of security-related websites, such as 2-spyware.com. Each of the entries means that users will not be able to access the listed web addresses and will receive an error instead.
Here's an example of “hosts” file entries that were injected by ransomware:
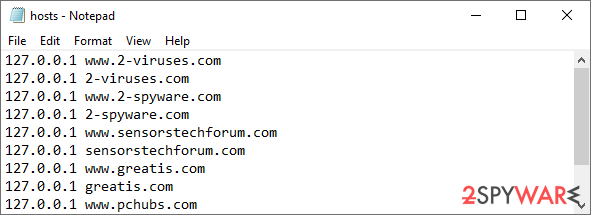
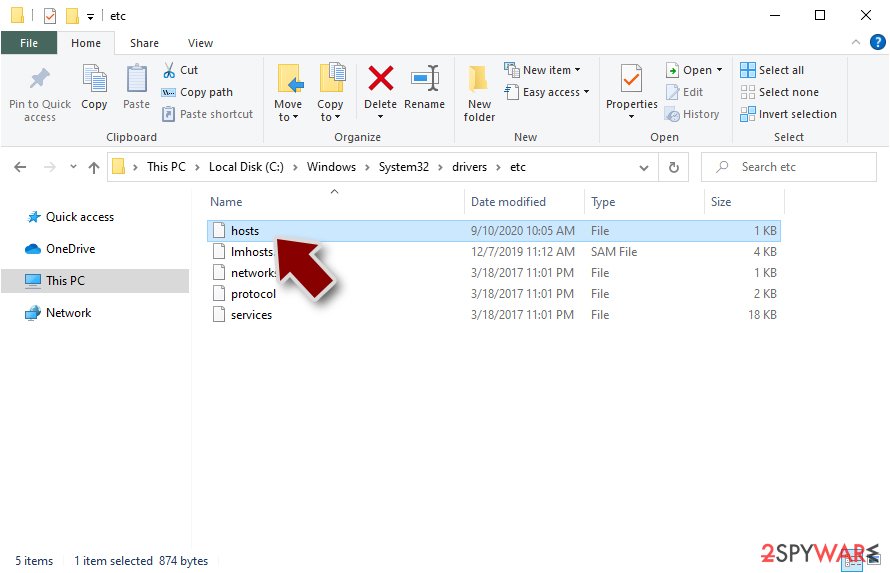
In order to restore your ability to access all websites without restrictions, you should either delete the file (Windows will automatically recreate it) or remove all the malware-created entries. If you have never touched the “hosts” file before, you should simply delete it by marking it and pressing Shift + Del on your keyboard. For that, navigate to the following location:
C:\\Windows\\System32\\drivers\\etc\\
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Qoqa and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.