Ravack ransomware (Improved Guide) - Virus Removal Instructions
Ravack virus Removal Guide
What is Ravack ransomware?
Ravack ransomware – a malicious piece of software that is spread via Movavi Video Editor Plus 20 2.0
Ravack ransomware is file-encrypting malware that has rooted in the Hakbit ransomware family. First spotted by dnwls0719 who announced the findings on Twitter,[1] this virtual parasite is distributed as the fake installation setup of Movavi Video Editor Plus 20 2.0 via an executable file. The main purpose of Ravack virus is to search for encryptable files and block them by using complex algorithms such as AES or RSA. When the encryption proceeds, the .ravack appendix is attached to each filename and the HELP_ME_RECOVER_MY_FILES.txt ransom note appears in a Notepad window.
Ravack ransomware developers are not that greedy as others and urge for a 0.02 BTC ransom price that is about $170. However, a high chance of getting scammed still exists. Crooks try to convince the victims to pay the demanded money by giving them the possibility of sending some files for free decryption via unlockransomware@protonmail.com email address. Also, Ravack ransomware states that all of the files that are saved on the infected machine will be permanently corrupted if the ransom price is not transferred within 48 hours. Nevertheless, hackers want the payment so bad that they even threaten the users that their personal information was collected and will be exposed if they do not agree to pay.
| Name | Ravack ransomware |
|---|---|
| Type | Ransomware virus/malware |
| Family | Hakbit ransomware |
| Discovered | This malicious piece of software was first discovered by a cybersecurity researcher known as dnwls0719 who announced his findings on the Twitter social platform at the start of March this year |
| Extension | When all of the files and documents that are located on the infected Windows computer system get locked with a unique cipher, the .ravack appendix is added to each filename |
| Demands | Crooks urge for a ransom payment that is equal to 0.02 Bitcoin via the HELP_ME_RECOVER_MY_FILES.txt message and give the users two days for transferring the money |
| Distribution | It is known that Ravack virus is spread as a fake installation setup via Movavi.Video.Editor.Plus.20.2.0.exe file. Also, ransomware can get delivered through malicious email messages, malvertising, and other computer viruses |
| Removal | If you have been dealing with this virtual parasite lately, you should speed up its removal process, otherwise, you risk receiving an additional malware infection. For this process, employ only reliable antimalware software that would be capable of terminating the ransomware |
| Data restore | You should avoid paying ransom demands as there is a big chance of getting scammed by the cybercriminals. Instead of following their commands, try some other file recovery alternatives that we have provided at the end of this article |
| Fix tip | If you have discovered any system corruption and are looking for a tool that would help to repair things, you can try employing a piece of software such as FortectIntego |
Ravack ransomware is a dangerous malware form that can run multiple processes during one session. This makes the infection even more complex and difficult to get rid of. Nevertheless, the ransomware virus can run an information collecting operation that aims to gather personal data about the user. Afterward, such types of details might be used for exposure and identity theft.
To continue, Ravack ransomware is able to modify and eliminate system files and information that is stored on the computer, so you need to be quick and get rid of the infection as soon as possible. Nevertheless, the malicious module includes connection with the Windows Mount Manager that provides interaction with remote drives and servers where important information can also be stolen from.
Ravack ransomware can also modify both the Windows Task Manager and Registry and fill them with malicious processes and files. The malware can even initiate the deletion of Shadow Volume Copies by running PowerShell commands. This is a way to harden the recovery process for the victims. Some ransomware viruses even corrupt Windows hosts files to prevent the victims from visiting security-related forums and websites.
When files are encrypted and the .ravack appendix is added, Ravack ransomware provides a ransom note on the user's computer screen and places a copy of the message in each file that holds encrypted data. Crooks state that they will share the collected personal information if the victims do not agree to pay the 0.02 Bitcoin price. However, you risk losing your money and receiving no key at all. Besides, there is no guarantee that hackers will not misuse your data and post it online. The main goal of this infection is to capture files, provide a ransom message and urge for money from the infected users:
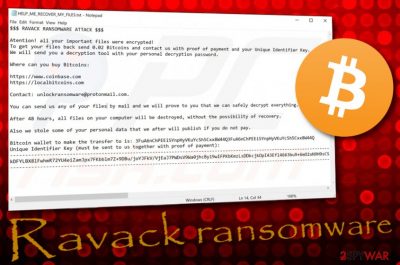
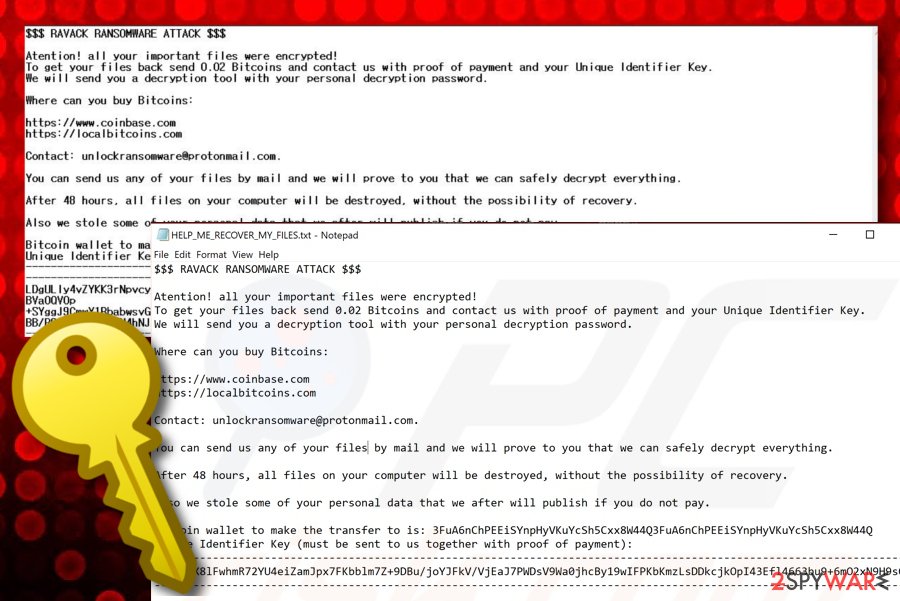
$$$ RAVACK RANSOMWARE ATTACK $$$
Atention! all your important files were encrypted!
To get your files back send 0.02 Bitcoins and contact us with proof of payment and your Unique Identifier Key.
We will send you a decryption tool with your personal decryption password.Where can you buy Bitcoins:
hxxps://www.coinbase.com
hxxps://localbitcoins.comContact: unlockransomware@protonmail.com.
You can send us any of your files by mail and we will prove to you that we can safely decrypt everything.
After 48 hours, all files on your computer will be destroyed, without the possibility of recovery.
Also we stole some of your personal data that we after will publish if you do not pay.
Bitcoin wallet to make the transfer to is: 3FuA6nChPEEiSYnpHyVKuYcSh5Cxx8W44Q3FuA6nChPEEiSYnpHyVKuYcSh5Cxx8W44Q
Unique Identifier Key (must be sent to us together with proof of payment):
——-
–
——-
Crooks who are behind Ravack ransomware urge for a Bitcoin ransom as cryptocurrency transfers allow them to stay unidentified. In some other cases, ransom demands can be even bigger than $1000 and $2000. However, big sums are mostly demanded from wide organizations and well-known firms as regular users might not even have that kind of money that is needed for receiving the decryption key.
Besides encrypting files and providing ransom demands, Ravack ransomware can also bring other cyber threats into the computer system. Ransomware viruses can carry trojans, worms, spyware, and other types of parasites. If you do not get rid of the infection as soon as possible, you are likely to experience additional malware delivery that can relate in software corruption, system destruction, file or money losses.
Ravack ransomware can install in the computer system as the Movavi.Video.Editor.Plus.20.2.0.exe file and run in the Task Manager disguising as a legitimate process. This executable has been detected by 24 AV engines out of the total 67, according to VirusTotal.[2] However, some other antivirus products might not be able to detect the malware because it can keep blocking specific software.
If you are having trouble with Ravack ransomware removal from your Windows computer properly, you should enable Safe Mode with Networking to disable malicious processes one of which might be blocking your antivirus software. Afterward, perform a thorough computer scan and discover all malware-laden products that are lurking on your machine. If you find any damaged areas, you can try repairing them with a tool such as FortectIntego.
When you remove Ravack ransomware and fix all of the corruption that the virus might have caused, you can continue with data recovery. Even though the official decrypter has not yet been discovered and paying the demanded ransom is not advisable, you still have some options left. Go to the end of this article and try file restoring software some of which might appear to be helpful.
Misleading emails and software cracks carry malicious payload
Ransomware infections are virtual parasites that aim to enter computers by employing deceptive and stealth tactics as no one who knew that they are going to install malware would opt for such a process. Distribution techniques can differ from a particular virus to another, however, crooks are most likely to use one of the following sources for spreading ransomware:
- Cracked software. Products that come provided on secondary downloading sources such as p2p networks are illegitimate and can be infected with malware. This can be key generators, fake installation setups, and other misleading components.
- Email spam.[3] This is also a very common way of spreading ransomware viruses when cybercriminals pretend to be some type of legitimate healthcare, banking, or shipping company and deliver misleading information that encourages users to click on the infectious hyperlink that comes included into the email message or open some type of clipped attachment that usually comes as a Word document or executable and carries the malicious payload.
- Malvertising. Malicious advertisements and the redirecting links that are included in them aim to distribute various malware forms such as ransomware viruses. When the user clicks on the infected ad or hyperlink, he initiates the downloading process of the computer virus.
- Other malware. Sometimes crooks employ other malicious software to distribute ransomware-related payload. Usually, Trojan viruses are expected to be carriers of additional virtual parasites.
According to cybersecurity experts from LosVirus.es,[4] it is very important to learn how to protect yourself from ransomware if you want to have a properly-functioning, clean computer system and safe files. Regarding this fact, we have decided to provide our readers with the most popular ways of ransomware prevention. If you are keen on figuring them out, keep reading the below-provided paragraphs.
Tips for computer and file safety
To begin with, it is very important to employ reliable antimalware software as protection against ransomware viruses. Read experts' recommendations on the Internet and find the tool that works for you. Also, make sure that you keep your antivirus program regularly updated, otherwise, it might not operate properly.
Furthermore, avoid downloading software cracks and get all of your wanted products from trustworthy websites and reliable developers. Do not visit peer-to-peer sources such as The Pirate Bay, eMule, and BitTorrent. Also, prevent yourself from clicking on unknown advertisements that appear on the Internet. To avoid unexpected appearances of ads, you can get and adblocking tool for your browser app.
Last but not least, it is very important to be able to recognize misleading email messages in order not to get lured in a malicious scheme. Always identify the sender, check if the email address is coming from a reliable company/person or not. Look through the email's content and search for possible grammar mistakes. Also, do not open any clipped attachments without scanning them with antimalware software.
For file safety, you should always have backups of your data. It is best to store copies of important files and documents on remote devices such as a USB drive. Also, you can keep your information in places such as Dropbox and iCloud. It would be even better if you kept copies of your files in multiple safe directories.
An advanced removal guide for Ravack ransomware
Opt for Ravack ransomware removal as soon as you discover files with the .ravack appendix and find the Bitcoin-demanding ransom message. There is no time to waste as the malware can easily bring other serious threats to your Windows computer system and you will also not be able to recover your encrypted files.
If you are looking for a safe and effective way to remove Ravack ransomware, you should decline the manual option. By trying to get rid of the parasite yourself, you might make damaging mistakes or skip some infectious content that can, later on, relate in the renewal of the ransomware virus. For the removal process, choose a reliable antimalware tool that would be capable of eliminating all of the malicious content.
When .ravack files virus is gone, you should search your Windows PC for possible corruption by employing software such as SpyHunter 5Combo Cleaner and Malwarebytes. If these tools discover any damage, you should try repairing it with another product – FortectIntego. Afterward, you can continue with the file recovery process. Below we have provided some possible techniques that can be a great alternative for the decryption key.
Getting rid of Ravack virus. Follow these steps
Manual removal using Safe Mode
To diminish malicious settings and deactivate the ransomware virus itself, you should consider rebooting your Windows computer in Safe Mode with Networking. Below you will find some helpful instructing steps for this method.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Ravack using System Restore
To disable the ransomware virus and get rid of all the compromised settings from your Windows operating system, opting for the System Restore feature might be an option for you.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Ravack. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Ravack from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If you have encountered files with the .ravack appendix, you should have also received the ransom note where Bitcoin is demanded. To avoid monetary losses and possible scamming, you should try other options for data recovery. Below we have provided some restoring software that might help you in this case.
If your files are encrypted by Ravack, you can use several methods to restore them:
Try employing Data Recovery Pro for file restoring purposes.
If you have been currently looking for some type of software that could allow you to recover blocked, corrupted, or deleted files, you should try using this product as there is a chance of reaching positive results.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Ravack ransomware;
- Restore them.
Windows Previous Versions feature might allow you to recover some files.
Try employing this piece of software if you are looking forward to recovering some files. However, make sure that you have booted your computer via System Restore in the past.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Employ Shadow Explorer for data restore.
If the ransomware virus did not permanently damage or corrupt your files' Shadow Volume Copies, you should give this tool a try.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Currently, no official .ravack files decrypter has been released yet. Cybersecurity experts are still working on the tool.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Ravack and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ dnwls0719. Ravack ransomware. Twitter. Social platform.
- ^ Movavi.Video.Editor.Plus.20.2.0.exe. VirusTotal. File information.
- ^ Margaret Rouse. Email spam. Search Security. Tech Target.
- ^ LosVirus.es. LosVirus. Cybersecurity news source.





















