RCRU64 ransomware (virus) - Free Instructions
RCRU64 virus Removal Guide
What is RCRU64 ransomware?
RCRU64 ransomware authors double the ransom demand if you are not quick enough

If your files have been marked with .03rK, .q6BH, or .IalG extensions and you can no longer access them, your computer has been infected with the RCRU64 virus. Ransomware is a type of computer malware that gains access via deceptive means, locks all files on the system, and then demands a ransom to be paid in exchange for a decryptor that could be used for automatic data recovery.
This particular threat uses a combination of AES and RSA[1] cryptographic algorithms to lock all pictures, videos, documents, and other files located on the infected Windows computer. This process usually does not take a long time, so victims are unable to interrupt the process by shutting down the machine.
Once encryption is finished, users can view two files – Read_Me!_.txt and ReadMe_Now!.hta, which serve as messages from the attackers. According to the contents of the ransom note, cybercriminals are asking to send an email to FilesRecoverEN@gmail.com (FilesRecoverEN@protonmail.com is listed as a backup email), including personal user ID, to negotiate the ransom amount to be paid in Bitcoins. They also warn that the price will double if victims fail to contact them within 48 hours.
Paying cybercriminals is quite risky, however, as there is no guarantee that they will send the required decryptor. Besides, below we will list a few alternative methods that should be able to help you to restore at least some of the encrypted files for free. Nevertheless, you should first ensure that you remove RCRU64 ransomware from your system correctly.
| Name | RCRU64 |
|---|---|
| Type | Ransomware, data locking malware |
| Encryption method | AES + RSA |
| File extension | .03rK, .q6BH, .IalG |
| Ransom note | Read_Me!_.txt and ReadMe_Now!.hta |
| Contact | FilesRecoverEN@gmail.com, psychopath7@tutanota.com, Myfiles.sir@gmail.com |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases |
| Malware removal | Perform a full system scan with powerful security software, such as SpyHunter 5Combo Cleaner |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
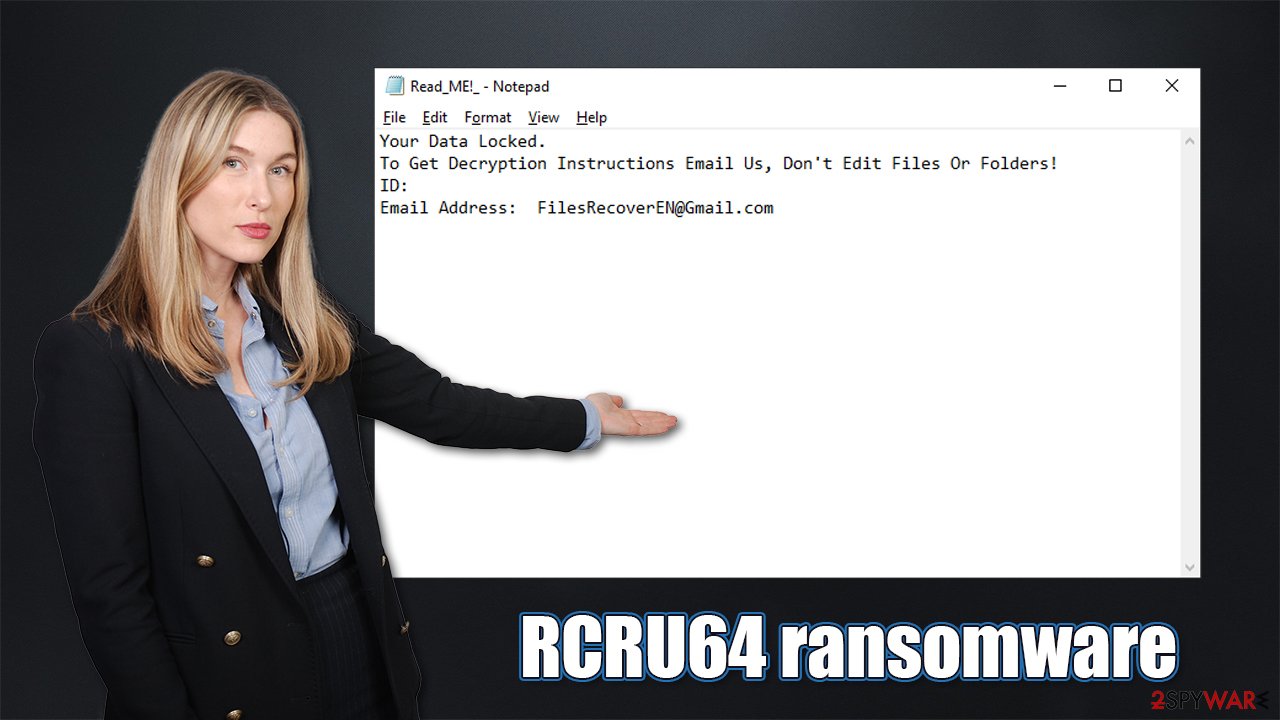
A ransom note is the primary communication means between the attackers and victims. It is not uncommon for cybercriminals to deliver several messages (we observed that in many Dharma ransomware variants); typically, one is sent in a .txt format, while the other uses HTA.
The .txt file ransom note contents are as follows:
Your Data Locked.
To Get Decryption Instructions Email Us, Don't Edit Files Or Folders!
ID : [ID]
Email Address: FilesRecoverEN@gmail.com
In another message, which is uses HTA format, crooks provided much more details about the attack:
All Your Files Have Been Encrypted!
All Your Files Encrypted Due To A Security Problem With Your PC. If You Need Your Files Please Send Us E-mail To Get Decryption Tools.
The Only Way Of Recovering Files Is To Purchase For Decryption Tools (Payment Must Be Made With Bitcoin). If You Do Not E-mail Us After 48 Hours Decryption Fee Will Double.
Our E-mail Address: FilesRecoverEN@Gmail.com
Your Personal ID:
Sent E-mail Should Be Contains Your Personal ID.If Don't Get a Response Or Any Other Problem Write Us E-mail At: FilesRecoverEN@Protonmail.com
Check Your Spam Folder Too.
—
What Guarantee Do We Give You?
You Can Send Some Files For Decryption Test (Before Paying). File Size Must Be Less Than 2MB And Files Should Not Contains Valuabe Data Like (Backups, Databases etc …).
————————————————– ——————————
How To Buy Bitcoins
Get Buy Bitcoin Instructions At LocalBitcoins:
https://localbitcoins.com/guides/how-to-buy-bitcoins
Buy Bitcoin Instructions At Coindesk And Other Websites By Searching At Google:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/
————————————————– ——————————
Attention !!
Do Not Edit Or Rename Encrypted Files.
Do Not Try To Decrypt Files By Third-Party Or Data Recovery Softwares It May Damage Files Forever.
In Case Of Trying To Decrypt Files With Third-Party, Recovery Sofwares This May Make The Decryption Harder So Prices Will Be Rise.
Please do not make decisions just by reading the ransom note, as it is quite risky. Keep in mind that cybercrimianls are not your friends, and all they care about is money. They might simply take your money and never provide you with a decryptor. Therefore, we recommend you avoid doing that and only agree to pay if it is an absolute last resort.
If you have decided not to pay and you have no file backups available, you should make a copy of all the important encrypted files. Otherwise, if you attempt to use security or recovery software immediately, you might permanently damage your files, and even a working decryptor then would not be able to save them. You can use cloud storage or USB flash for this purpose.
Before that, however, you should remove the RCRU64 virus from your machine with powerful anti-malware software, such as SpyHunter 5Combo Cleaner or Malwarebytes. If ransomware is tampering with your security tool or disabling it, you should access Safe Mode with Networking and performing the scan from there:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.
![Update & Security Update & Security]()
- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.
![Recovery Recovery]()
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
![Press F5 to enable Safe Mode with Networking Press F5 to enable Safe Mode with Networking]()
After using security software (either in Safe Mode or normal mode), you can then backup all your files. Encrypted data is not dangerous – there is simply no malicious code within it.
Variants
RCRU64 ransomware was first discovered at the start of April of 2021 and described by a security researcher Amigo-A. It is a brand new malware strain and was not found to be related to any previous ransomware families. Cybercriminals behind it are not are willing to stop any time soon, as there have been two more versions released since the initial virus appearance.
Currently, there are three prominent versions of malware:
- The initial malware uses the .03rK extension and FilesRecoverEN@gmail.com (FilesRecoverEN@protonmail.com) contact emails.
- A second variant, first discovered in early July, uses .q6BH file extension and psychopath7@tutanota.com contact email.
- The third version was spotted in mid-July. It uses .IalG extension and Myfiles.sir@gmail.com email.
All of the variants are using the same ransom note names with slight variations inside. Keep in mind that it is likely that threat actors will deliver new versions in time, so you should be very vigilant.
In order to avoid being infected with ransomware, you should equip your system with powerful anti-malware software with real-time protection features, never open suspicious emails with attachments (“Enable Content” within MS Office documents should not be an option!), avoid torrent and crack sites, and be overall more careful when clicking on links or downloading software from third-party websites.
Malware damage and how to fix it
While you might only notice changes to your personal files (inability to open them, default icon change to a blank one, etc.), there are thousands of command lines and changes performed within an infected Windows machine. First of all, once the malicious file is executed, the virus bypasses a very important security feature in Windows – User Account Control. It also disables any built-in defenses such as Windows Defender.
Furthermore, it modifies the Windows registry in order to be booted each time the PC is launched. To make it impossible for users to recover files using automatic backups known as Shadow Copies,[2] RCRU64 removes them. Finally, it alters Group Policy settings and terminates many vital Windows processes and features. This effectively hijacks users' computers – this is why accessing Safe Mode might be necessary when trying ransomware removal.
Due to these modifications, Windows might start malfunctioning, even after malware is removed, hence you might experience crashes, errors, and similar issues. To address this, there is no need to reinstall Windows – we recommend using a PC repair tool instead. Here's how:
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
The app can also be extremely useful when dealing with computer issues outside of malware infections; for example, it can quickly fix BSODs,[3] crashes, DLL errors, registry issues, and much more.
Recovery options
First of all, it is important that you backup the encrypted files that are important to you on a separate medium and remove malware from the system with anti-virus software, as we explained above. Once these two steps are complete, you can try alternative methods when it comes to data recovery.
First of all, let's start from data recovery software:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![RCRU64 ransomware RCRU64 ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
The second thing you could do is look for decryption software that might be ready for you from prominent security companies and researchers. Here's the list:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Keep in mind that decryptors for some strains might not be available straight away – if ever. Encryption, when done right, is almost impossible to be broken, as even quantum computers would not be able to calculate the correct keys required to unlock files for each victim individually.
Finally, you should consider reporting the attack to your local authorities. It can help with the investigation and increase the chances of the culprits getting caught.
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Ron Franklin. AES vs. RSA Encryption: What Are the Differences?. Precisely. Data integrity.
- ^ Jason Faulkner. What Are “Shadow Copies”, and How Can I Use Them to Copy Locked Files?. How-to Geek. Site that explains technology.
- ^ Blue Screen of Death (BSoD). Techopedia. Professional IT insight.

















