Reminderapp.store scam (fake) - Free Guide
Reminderapp.store scam Removal Guide
What is Reminderapp.store scam?
Reminderapp.store tries to trick people into installing a PUP by showing a fake Apple Security message
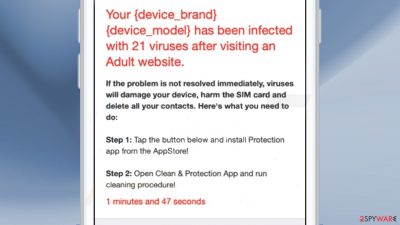
Reminderapp.store is a deceptive site that tries to trick people into thinking that their device is infected with multiple viruses. It uses social engineering[1] methods to scare people and get them to act without thinking. The full message that people see reads as follows:
Apple Security
Your {device_brand} {device_model} has been infected with 21 viruses after visiting an Adult website.If the problem is not resolved immediately, viruses will damage your device, harm the SIM card and delete all your contacts. Here's what you need to do:
Step 1: Tap the button below and install Protection app from the AppStore!
Step 2: Open Clean & Protection App and run cleaning procedure!
As you can see, the primary targets of this phishing scam are the people who own iPhones. The site is designed to look like a legitimate alert from Apple Security. The site claims that viruses infected the machine after visiting an adult website. In fact, it may be that an adult page caused the scam to appear.
Usually, pages that engage in illegal activities or shady sites in general, are unregulated, they may use rogue advertising networks that place ads leading to dangerous websites that try to trick people into providing personal information, downloading PUPs (potentially unwanted programs),[2] or even malware.
| NAME | Reminderapp.store |
| TYPE | Phishing scam; adware |
| SYMPTOMS | A suspicious page suddenly opens saying that the user's iPhone has been infected by viruses |
| DISTRIBUTION | Shady websites, deceptive ads, freeware installations |
| DANGERS | People can get tricked into installing potentially unwanted programs or malware |
| ELIMINATION | Scan your device with anti-malware tools |
| FURTHER STEPS | Use a repair tool like FortectIntego to fix any remaining damage |
The danger of potentially unwanted programs
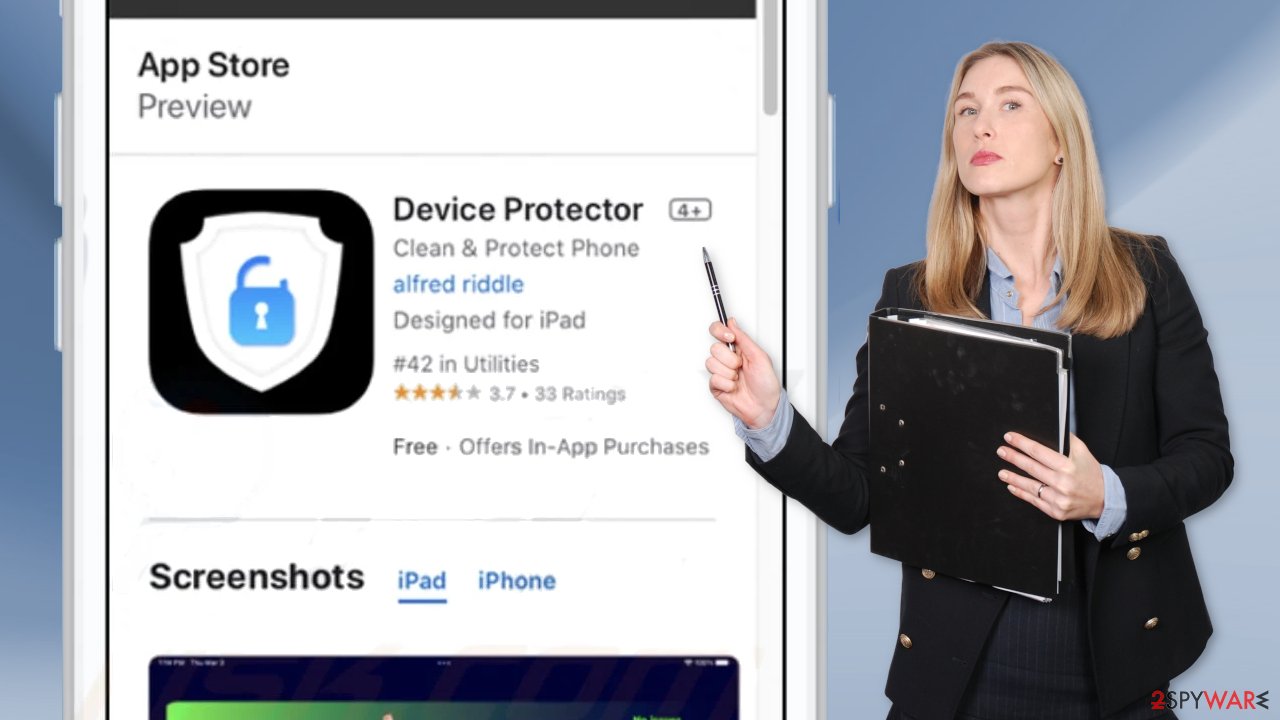
The Reminderapp.store page, redirects users to the app store and encourages them to install “Device Protector.” It is unknown if the application is safe to use. It may be a PUP that has hijacking or adware[3] capabilities. People may start experiencing an increased amount of commercial content, like pop-ups, banners, and redirects.
It is never a good idea to install apps when you are prompted by shady websites. If you want a system tool, you should look for it yourself and do your research – read the reviews, look at the ratings, and the number of users it has. It is best to choose those that have plenty of positive feedback and thousands of users.
Protect your privacy
You have probably noticed that almost every website you visit asks permission to use cookies.[4] Generally, this is not a bad thing as it helps websites to personalize the user experience. However, it can cause a lot of issues if the page does not have strong security. Cookies can be hijacked and used for malicious purposes. Untrustworthy pages can also sell them to advertising networks and other third parties.
Cookies can store data like your IP address, geolocation, websites you visit, links you click on, and things you purchase online. This is why it is important to clear your browsers regularly. The process can be automated with a maintenance tool like FortectIntego. It can delete all cookies and cache and also fix system damage, errors, and registry issues which is especially helpful after a virus infection.
Get rid of the fake security alert scam
The Reminderapp.store page could have appeared because your browser is hijacked, so you should check your device for malicious extensions. The site is also capable of displaying annoying push notifications. You can find a detailed removal guide below.
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Remove unwanted notifications:
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
Reset Safari:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.
![Reset Safari Reset Safari]()
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Remove unwanted notifications:
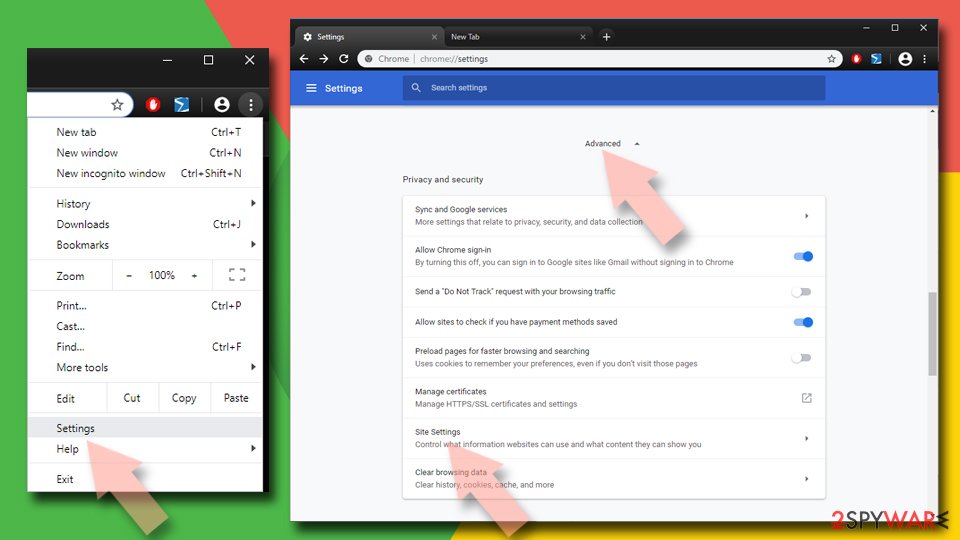
- Open Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate Privacy and security section and pick Site Settings > Notifications.
![Stop notifications on Chrome PC 1 Stop notifications on Chrome PC 1]()
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Clear cache and web data:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.
![Reset Chrome 2 Reset Chrome 2]()
Scan your device for adware
If the above method did not get rid of unwanted symptoms, there is a possibility that your device is infected by adware. Such programs can perform various tasks in the background, like generating pop-ups, banners, and redirects. Most often, users get infected by adware from freeware distribution platforms.
They include bundled software in the installers to make a profit. To avoid that, always choose the “Custom” or “Advanced” installation method, read the Privacy Policy and Terms of Use. The most important part is to check the file list and untick the boxes next to any unrelated files that you do not want to install.
Generally, PUAs are hard to remove because fraudsters disguise them as handy tools. We suggest using professional security software like SpyHunter 5Combo Cleaner and Malwarebytes that can scan your system and detect suspicious processes running in the machine. Besides, anti-malware tools can issue warnings if a file trying to enter your system seems suspicious. However, if you still want to do this yourself, here are the steps you need to follow:
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
How to prevent from getting adware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Social engineering (security). Wikipedia, the free encyclopedia.
- ^ Chris Hoffman. PUPs Explained: What is a “Potentially Unwanted Program”?. Howtogeek. Technology Magazine.
- ^ Lucian Constantin. What is adware? How it works and how to protect against it. Csoonline. Security news, features and analysis about prevention.
- ^ Chris Maus. What Are Cookies and Are They Dangerous?. Qkey. Secure Online Payment Providers.