Roblox ransomware (Tutorial) - Recovery Instructions Included
Roblox virus Removal Guide
What is Roblox ransomware?
Roblox ransomware is data-locking malware made by cybercriminals
Roblox ransomware is a malicious program designed for Windows operating systems. First encountered in the second half of October 2022, this virus belongs to a stain known as Jigsaw, a very popular ransomware family known for years to cybersecurity researchers, and it has caused havoc around the world.
Once installed on the system, the Roblox virus would immediately search for files to encrypt. When found, all pictures, videos, documents, etc., are then appended with a .Encrypted_Roblox@mail.com extension, rendering them useless. This means that each time victims would try opening their files, they are shown an error message instead.
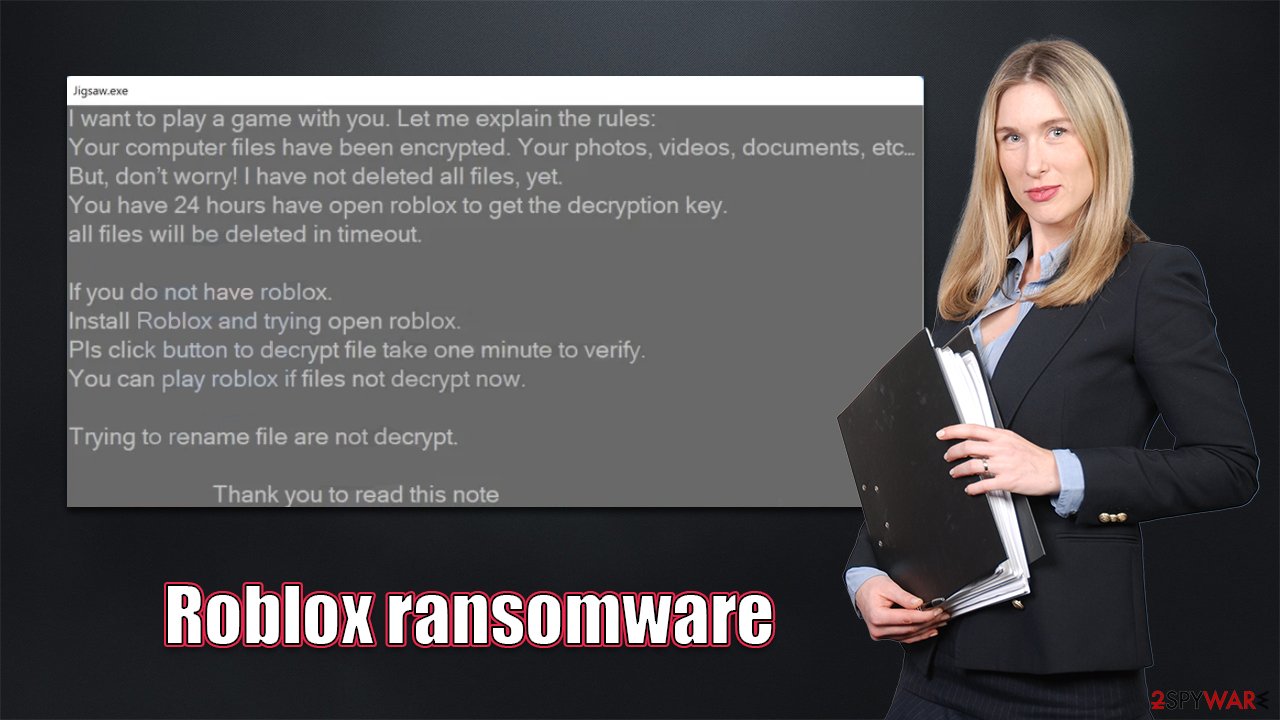
Soon after finishing encryption, malware delivers a ransom note, how_to_back_files.html, which opens a pop-up window titled “Jigsaw.exe.” The file holds the message from the malware authors and explains to users that they need to play the Roblox game in order to restore their data back to normal.
| Name | Roblox virus |
|---|---|
| Type | Ransomware, file-locking malware, cryptovirus |
| File extension | .Encrypted_Roblox@mail.com |
| Ransom note | how_to_back_files.html |
| Family | Jigsaw |
| Data Recovery | If no backups are available, recovering data is almost impossible. However, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Malware removal | Manual virus removal is not recommended, as it might be difficult for regular users. Instead, SpyHunter 5Combo Cleaner or other anti-malware tools should be used |
| System fix | Malware can seriously impact a Windows computer's performance and stability after it is removed. We recommend scanning the system with FortectIntego to remedy it and avoid significant stability issues |
Promises to decrypt files if users would play Roblox
Ransomware authors usually have financial goals – that's why malware like Tohj, T_TEN, or Ash asks users to transfer Bitcoin to a specified crypto-wallet, which makes a lot of sense. Cybercriminals have the decryptor, and the victims have a reason to pay – to restore their files.
Unlike these typical viruses, Roblox ransomware goes a surprising route and is likely to be created as a joke. Roblox is an extremely popular video game platform that allows users to create their own games. There are around 42 million players that enjoy the game worldwide. Ransomware authors are fans of the game or are simply encrypting users' files as a prank because they are asking victims to install and play the game in order to restore the encrypted data.
According to the ransom note, users have 24 hours timeframe window before all their files will be deleted if the demands are not met:
I want to play a game with you. Let me exmplain the rules:
Your computer files have been encrypted. Your photos, videos, documents, etc…
But, don't worry! I have not deleted all files, yet.
You have 24 hours have open roblox to get the decryption key.
all files will be deleted in timeout.If you do not have roblox.
Install Roblox and trying open roblox.
Pls click button to decrypt file take one minute to verify.
You can play roblox if files not decrypt now.Trying to rename file are not decrypt.
Thank you to read this note.
The request is highly unusual and does not benefit the attackers in any financial way. There might be a chance that files would indeed be restored when the game is installed and played, so trying this solution wouldn't help.
However, crooks behind ransomware can often not be trusted, so everything can fall apart really fast. We recommend taking action against Roblox ransomware immediately if installing and playing the game does not work out. The first step is to isolate the machine from the internet and then remove malware from the system.
1. Disconnect the device from the network and internet
It is normal for users to experience an immediate sense of fear when they cannot access their data because ransomware has encrypted them. However, this response is unnecessary because the infection is already present. In fact, worried individuals could make errors that cause even more data loss. A few crucial actions must be taken one after another in order to stop additional damage.
Making sure that ransomware can no longer communicate with the remote server known as Command & Control[1] is your first job. To accomplish that, you must first disconnect your computer from the internet and, if applicable, the network. Take the following actions:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
2. Remove malware
While some ransomware does have a tendency to self-destruct after encrypting data, this isn't always the case. For instance, it frequently spreads alongside other malware, such as data-stealers or keyloggers[2] therefore, it's crucial to get rid of all malware components at once. The simplest method is using powerful anti-malware software, like SpyHunter 5Combo Cleaner or Malwarebytes. Before using the security program, it is essential to disconnect the system from the internet.
Keep in mind that sometimes malware might make security software less effective, which can lead to incomplete removal or other problems. In this situation, you can enter Safe Mode and remove the Roblox malware there:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
![Recovery Recovery]()
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
After the infection has been eliminated, we strongly urge you to use the FortectIntego PC repair tool. Malware may corrupt Windows system files, and security applications may not be able to fix it. Users may consequently encounter system crashes, BSODs,[3] errors, and other typical technical issues as a result of malware eradication. The repair program has the capacity to add new system files by replacing corrupted ones.
3. Recover your files
Many people believe that any encrypted files will be restored after their computer has been scanned by security software. That isn't the case, though, because data encryption is typically permanent – at least until a special key is applied. Additionally, believing that the files are corrupted or destroyed is incorrect because encryption does not truly harm files.
If installing Roblox did not work out, you can always try alternative methods of data recovery. It is important to note that they might not work for everybody, but it is worth a try. You should make copies of encrypted data before continuing by the way, as files might get damaged in the process.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Roblox ransomware Roblox ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Decryption tools might also be created for certain ransomware strains thanks to the efforts of security researchers. In some cases, law authorities seize the servers of malicious actors, which allows the keys to be released by the public – reputable security vendors usually do this. Here are a few links you might find useful:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Command and Control [C&C] Server. Trend Micro. Security blog.
- ^ Keyloggers 101: A definition + keystroke logging detection methods. Norton. Security Center.
- ^ Blue screen of death. Wikipedia. The free encyclopedia.











