Searchoverus.com browser hijacker (virus) - Free Guide
Searchoverus.com browser hijacker Removal Guide
What is Searchoverus.com browser hijacker?
Searchoverus.com is an URL that may be a sign of browser hijacker infection
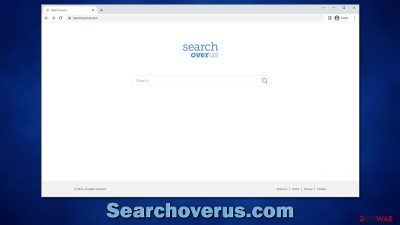
Searchoverus.com is a fake search engine that shows inaccurate search results to users in order to profit from promotion links. Most commonly, users find that the homepage of Google Chrome, Mozilla Firefox, or another web browser has been unexpectedly altered to this address because they are unaware they have a browser hijacker installed on their systems.
The potentially unwanted application[1] is likely to be installed as a browser extension, which would immediately change the way users browse the web. By replacing the search provider with its own, the app authors put as many ads at the top for users to click and receive revenue for each of these clicks.
Unfortunately, Searchoverus.com hijack is not good news for regular users because they may be exposed to advertisements pushing other potentially unwanted programs, having their information being tracked, and experiencing more suspicious material while browsing the web. If you have found that your homepage has suddenly changed, we recommend you follow the instructions below to remove the PUP and check your device thoroughly for other infections.
| Name | Searchoverus.com |
| Type | Browser hijacker, potentially unwanted application |
| Distribution | Software bundles, ads, redirects |
| Symptoms | Homepage and new tab address hijacked by the extension; homepage and new tab set to searchoverus.com; promotional links are displayed as top search results; intrusive ads on visited websites |
| Risks | Data tracking from various third parties, exposure to malicious ads, redirects to phishing sites |
| Removal | You should access your browser's settings to remove the unwanted browser extension. Checking the system with SpyHunter 5Combo Cleaner security software can also ensure that there is no adware or malware running in the background |
| Other tips | Third parties can employ cookies to continue tracking your online activities, so we recommended clearing browser caches and other leftover PUP files with FortectIntego |
How browser hijackers spread and how to avoid them
The most common way to become infected with potentially unwanted applications is through software bundling.[2] This technique is employed by almost all third-party websites that distribute freeware or shareware, as well as embedded advertising. As a result, whenever you visit such a site, keep in mind that if you don't pay attention when installing new apps, you might end up installing additional software you never asked for.
In order to avoid this scenario, you should always pay close attention to the installation process of freeware and other software you download online. For example, if you choose Advanced or Custom settings instead of Recommended ones, you would be provided with much more control over what is actually being installed on your system.
Do not forget to untick checkmarks from pre-selected checkboxes, read the fine print, and watch out for misplaced buttons – do not rush. Keep in mind that employing official stores and sites removes the chance of software being bundled, so try to stick to these. Visiting pirated software distributors is asking for trouble, as these are known to get people infected with Trojans, ransomware,[3] and other dangerous malware.
Searchoverus.com hijacker removal
Unexpected browser changes can occur after you install new software on your device, primarily from unofficial websites or suspicious ads. Regardless of whether you were expecting these changes or not, you should not tolerate them, as, despite the promises of PUP developers of “seed boost” or “better search results,” the only thing you are actually getting with them is the annoying advertisements and changes to your search provider, which is usually unwelcomed at all.
When it comes to the so-called Searchoverus.com virus, you should check your browser from suspicious extensions and remove them at once. If you haven't previously done this, we provide all the details below, just make sure you follow the instructions for the browser you are using.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Internet Explorer
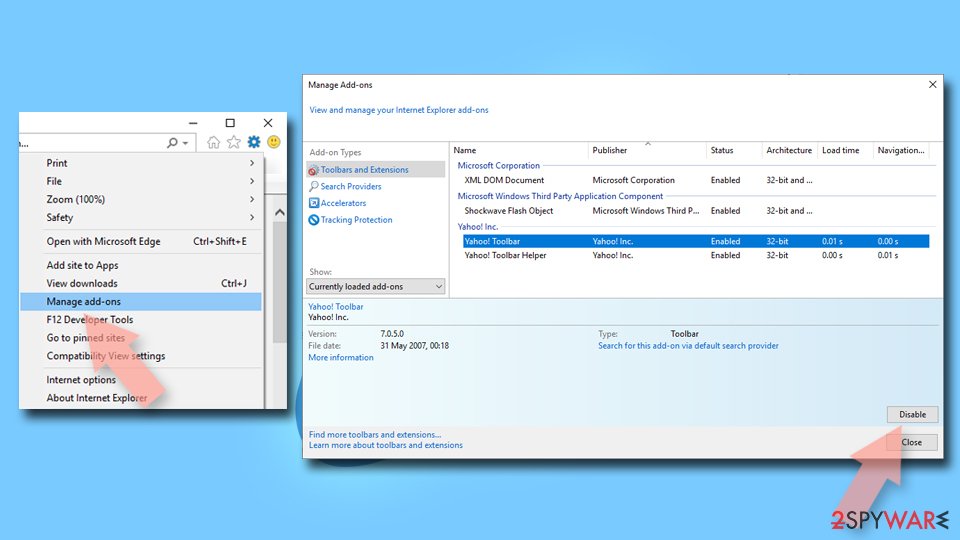
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
![Remove add-ons from Internet Explorer Remove add-ons from Internet Explorer]()
Take care of your privacy and security
As browser hijackers spread using software bundling, there may be a chance that there are other potentially unwanted or malicious applications installed on your device, so ads and other suspicious activity will not stop until you remove them. Keep in mind that Trojans and other malware may not show up under the installed program list and never run any active windows – malware is nowadays very stealthy and does not emit any symptoms.
Therefore, scanning the system with reputable anti-malware is strongly advised. Make sure you install all the relevant updates before you proceed with the scan, as the virus definitions used should be the newest version. Security software is also very effective when it comes to defending users from incoming virus attacks, so never ignore these warnings.
Searchoverus.com may also continue tracking various information about you (cookies, visited websites, links clicked, search queries, and more) unless you remove trackers from your local cache folders. If you are looking for an automatic solution, we highly recommend FortectIntego maintenance utility. For manual steps, check out the guide below:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Internet Explorer
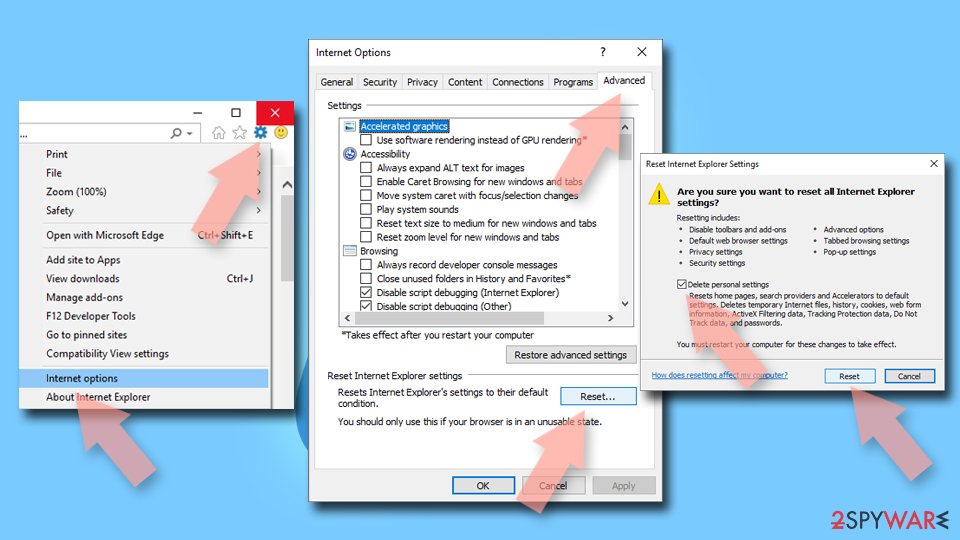
- Click on the Gear icon > Internet options and select the Advanced tab.
- Select Reset.
- In the new window, check Delete personal settings and select Reset.
![Reset Internet Explorer Reset Internet Explorer]()
How to prevent from getting browser hijacker
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Potentially Unwanted Application. Trend Micro. Security solutions.
- ^ Bundled software. Computer Hope. Free computer help.
- ^ Ransomware. Imperva. Application and data protection.