Secure Color Search adware (Free Guide)
Secure Color Search adware Removal Guide
What is Secure Color Search adware?
Secure Color Search is a potentially unwanted browser extension that distributes ads everywhere you go online
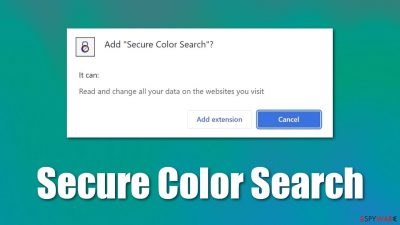
Secure Color Search is advertised as a tool that can change the color of the visited website. However, looking deeper into its functionality, it becomes clear that it has some additional, unhelpful features, including intrusive advertisements and unwanted data tracking. This is why the app is generally considered to be adware – a type of deceptive software that neglects its promised features and instead, heavily focuses on advertising and its monetization.
| Name | Secure Color Search |
| Type | Adware, potentially unwanted browser extension |
| Distribution | Bundled software, redirects, misleading ads |
| Symptoms | Shows fake ads and promotes potentially unwanted applications |
| Risks | Installation of potentially unwanted software, such as browser hijackers; redirects can also lead to other malicious websites, resulting in monetary loss or personal data disclosure to unknown parties |
| Removal | Remove the unwanted browser extension, you should access your browser's settings section. Checking the system with SpyHunter 5Combo Cleaner security software can also ensure that there is no adware or malware running in the background |
| Other tips | You can employ FortectIntego to clean your browsers from trackers and fix any issues that could arise due to adware/malware infections |
Adware distribution
Potentially unwanted software is named so mainly because of its distribution methods (although its functionality, which includes showing intrusive ads, is also unwanted by people). Users don't install adware intentionally – at least if they know the true purpose of the app.
The problem is that it might be difficult to know which programs are ad-supported and which ones aren't, as it only becomes apparent once the software is installed and running. To avoid this, make sure you never download apps from torrents and similar insecure places and always refer to user reviews and feedback before installing an unknown program.
More often than not, users find adware running on their systems without expecting it to happen. Software bundling[1] is one of the main reasons for that – this technique allows third-party websites to insert optional components into the installers and then hide them in various deceptive ways.
To not fall victim to this tactic, make sure you pay close attention to the installation process of freeware[2] – remove all ticks from pre-ticked checkboxes, read the fine print, watch out for misplaced buttons and, most importantly, always choose Advanced/Custom installation settings instead of Recommended/Quick one.
How does Secure Color Search operate?
Adware varies on the level of damage it can pose when running in the background. Mostly, it would show ads on the homepage or in search results and also insert a virtual layer that would result in ads appearing outside of the visited page. Without a doubt, that can be intrusive and frustrating, although this is not the main danger of adware.
Secure Color Search might push advertisements of dubious nature, which may include promotions of other potentially unwanted applications, phishing messages, or even redirects to malicious websites. Adware developers are often associated with insecure advertising networks which do not adhere to security protocols, which results in such behavior. This is also one of the reasons why the removal of such apps is vital for one's computer security.
Secure Color Search removal steps
Luckily, the removal of potentially unwanted software is usually not that difficult. Unlike malware, it doesn't use many persistence[3] mechanisms, although some apps can use clever tricks to stay on the system for as long as possible. In the case of Secure Color Search, you must find the browser extension and remove it, as it is the way the app works. If you have never had to deal with browser add-ons, you can follow the instructions below.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
MS Edge (legacy)
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.
![Remove extensions from Edge Remove extensions from Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Internet Explorer
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
![Remove add-ons from Internet Explorer Remove add-ons from Internet Explorer]()
The second step when it comes to the elimination of adware is making sure that the browsers are cleaned from leftover files. Once installed, adware places tiny files known as cookies on the local machine, which allows it to track various information about your browsing habits and technical information of your device.
This tracking may continue for as long as trackers are present on the system, so we strongly recommend removing them after adware removal. If you prefer an automatic solution, you could employ FortectIntego instead, saving you a lot of time and also fixing any damage that adware could have caused.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies, and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
MS Edge (legacy)
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.
![Clear Edge browsing data Clear Edge browsing data]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
It is important to note that adware could also be installed on the system level as a program. Below you will find tips on how to remove these applications from Windows and Mac operating systems. If you are not entirely sure about what should stay and what should be removed, leave this job for SpyHunter 5Combo Cleaner or Malwarebytes security software.
Not only would it find and remove Secure Color Search adware from your system, but it also can eliminate invisible malicious components at once. Likewise, if updated regularly, anti-virus software is the best way to protect yourself against dangerous cyberattacks and malware infections.
How to prevent from getting adware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Bundled Software. Techopedia. Professional IT insight.
- ^ What Is Freeware?. Lifewire. Tech News, Reviews, Help & How-Tos.
- ^ Common malware persistence mechanisms. InfoSec. Malware analysis.