SilentDeath ransomware (Virus Removal Instructions) - Free Guide
SilentDeath virus Removal Guide
What is SilentDeath ransomware?
SilentDeath ransomware – a file-locking parasite that demands to purchase tools for its decryption in Bitcoins
SilentDeath ransomware is a malicious computer virus that locks files on a targeted Windows machine and demands to pay its developers in cryptocurrency for the necessary decryption key. Criminals claim to have the only solution for data recovery. Although this cryptovirus was first detected in July 2019, it's still actively spreading and causing trouble for people worldwide.
When a computer gets infected with SilentDeath ransomware virus, the encryption starts instantly, and all files can be locked within a couple of minutes. During which, all personal files, such as pics, docs, databases, etc., get renamed by appending a .SilentDeath extension to their original filenames.
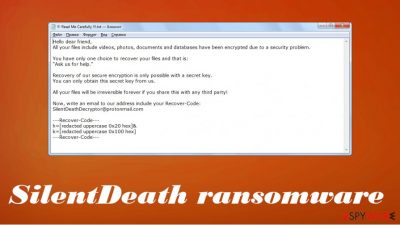
Also, a ransom note, titled !!! Read Me Carefully !!!.txt is generated and placed on the desktop so victims could find it with ease. If you've encountered this file-locking parasite and thus can't access your files, then we're happy you came to us to solve this issue. Please don't contact the assailants by their given email (SilentDeathDecryptor@protonmail.com). Please read this article to find out how this malware spreads, its removal options, and other subtleties.
| name | SilentDeath ransomware |
|---|---|
| Type | File-locker, cryptovirus, ransomware |
| Distribution | Spam emails, file-sharing platforms, deceptive ads |
| Appended file extension | All encoded data gets marked with a .SilentDeath extension after the original filename |
| Ranson note | !!! Read Me Carefully !!!.txt can be found on the desktop |
| Criminal contact details | SilentDeathDecryptor@protonmail.com |
| Malware Elimination | Victims should remove SilentDeath ransomware with professional anti-malware tools that would do the job properly and leave no pieces behind |
| System health check | To restore your system to a pre-contamination phase, a system repair tool such as the FortectIntego app must be used |
Usually, ransom notes of file-locking parasites are long and informative. The one from SilentDeath ransomware isn't anything like that. The threat actors behind the attack just state that files are encrypted, and the only way to retrieve them is by contacting them via a provided email and purchasing their decryption key.
The whole message from !!! Read Me Carefully !!!.txt file states:
Hello dear friend,
All your files include videos, photos, documents and databases have been encrypted due to a security problem.You have only one choice to recover your files and that is:
“Ask us for help.”Recovery of our secure encryption is only possible with a secret key.
You can only obtain this secret key from us.All your files will be irreversible forever if you share this with any third party!
Now, write an email to our address include your Recover-Code:
SilentDeathDecryptor@protonmail.com
Contacting the criminals and paying the ransom is highly unrecommended. The payoffs only encourage them to intensify their attacks, develop more sophisticated malware, and research more effective distribution methods. Also, after payment is made, any of these scenarios could come to life:
- No decryption tool is sent.
- More money is asked.
- Additional malware is sent instead of the decryption key.
- The decryption key doesn't work.
- Cybercriminals disappear altogether.
Victims should have only one thought in their heads “how do I remove SilentDeath ransomware and forget about this nightmare”. And here we come to the rescue. First of all, you'll need a professional anti-malware tool for this task. If you don't have one, we recommend getting either SpyHunter 5Combo Cleaner or Malwarebytes.
Launch your security software and pick the entire system scan. Once it's finished, eliminate all suspicious files. For the second part of SilentDeath ransomware removal, you'll need a system repair tool. Once again, if you don't own one, we advise getting the powerful FortectIntego tool. Open it, scan the whole system, and restore any corrupted or damaged system files.
Avoid file-sharing platforms to evade malware infections
There are tens of thousands of various computer viruses waiting to infect the devices of regular people. Not only Windows machines can get infected, but also Macs and Androids. When it comes to malware delivery, cybercriminals have many techniques at their disposal, including spam emails, drive-by downloads,[1] and so on.
One of the most pervasive methods used to spread all kinds of malware[2] is file-sharing platforms. Hackers prefer this method because they don't have to bend over backward to reach their goals. Due to the lack of end-to-end security, they just have to think of a catchy name and upload their creations.
Malware can be camouflaged as the latest game crack, expensive unlocked software, or similar illegal downloads. It can be hidden as any filetype. If you value your privacy, security, and finances, don't use file-sharing platforms. Support software developers by purchasing their products directly from them.
SilentDeath ransomware virus removal options from infected devices
If you've noticed any of the symptoms that your Windows computer is infected with the SilentDeath file virus, then this article is for you. Follow our instructions, and you'll get rid of it in a couple of minutes, once and for all. Start by copying all essential encrypted data to an offline storage device. There's no decryptor available at the moment, but there's always hope.
Open your security tool. If it's the same one that let the malware through, we recommend upgrading your cybersecurity level by acquiring a trustworthy anti-malware program like SpyHunter 5Combo Cleaner or Malwarebytes. Scan the whole device, and remove SilentDeath ransomware along with any other questionable files.
Since malware infections tend to make alterations to the system registry and other key system settings, a system repair is in order. To restore all system values and files back to normal, following SilentDeath ransomware removal, experts from UdenVirus.dk[3] advise using the FortectIntego system repair tool.
Getting rid of SilentDeath virus. Follow these steps
Manual removal using Safe Mode
Computer infections can be eliminated in Safe Mode with Networking
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove SilentDeath using System Restore
Threat elimination with System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of SilentDeath. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove SilentDeath from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by SilentDeath, you can use several methods to restore them:
File retrieval with Data Recovery Pro
Third-party tools might sometimes prove useful to restore .SilentDeath extension files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by SilentDeath ransomware;
- Restore them.
Remove .SilentDeath extension with Windows Previous Version feature
This Windows feature might help to recover encrypted files.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Data recovery with Shadow Explorer
This open-source app might be able to restore old data.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryption tool is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from SilentDeath and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Forrest Stroud. Drive-By Download. Webopedia. Online tech dictionary.
- ^ Roger A. Grimes. 9 types of malware and how to recognize them. Cso. Security news, features and analysis.
- ^ Udenvirus. Udenvirus. Spyware and security news.





















