Solidbit ransomware (Free Instructions)
Solidbit virus Removal Guide
What is Solidbit ransomware?
Solidbit is a ransomware-type virus that attempts to extort money from affected victims
Solidbit ransomware is a type of computer virus that injects malicious code into Windows to encrypt all personal files located on it. At this time, all the files receive a randomly-generated, unique extension of four alphanumeric characters and become inaccessible. The main goal of cybercriminals is to prevent users from accessing their important data, leaving them no choice but to pay the demanded ransom in exchange for a decryptor that would return their files back to normal.
However, cybercriminals should not be trusted, especially when the Solidbit virus is a relatively new strain with not many documented cases. Instead, we recommend checking the information below on how to deal with the infection correctly and how to attempt file recovery using alternative methods.
| Name | Solidbit virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | Generates a random extension consisting of four alphanumeric characters, e.g., “picture.jpg” is turned into “picture.jpg.5r1g” |
| Encryption type | AES + RSA |
| Ransom note | RESTORE-MY-FILES.txt and a pop-up window |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
Solidbit ransom note
Ransomware is probably the most devastating cybersecurity threat in the wild for both regular consumers and companies or businesses. It might prevent users from accessing their files and stealing sensitive corporate data, which may later be sold to the highest bidder on the dark web, disclosing company secrets and personal details of employees, partners, customers, and more. This is why a ransomware attack on a corporation is not considered a data breach.
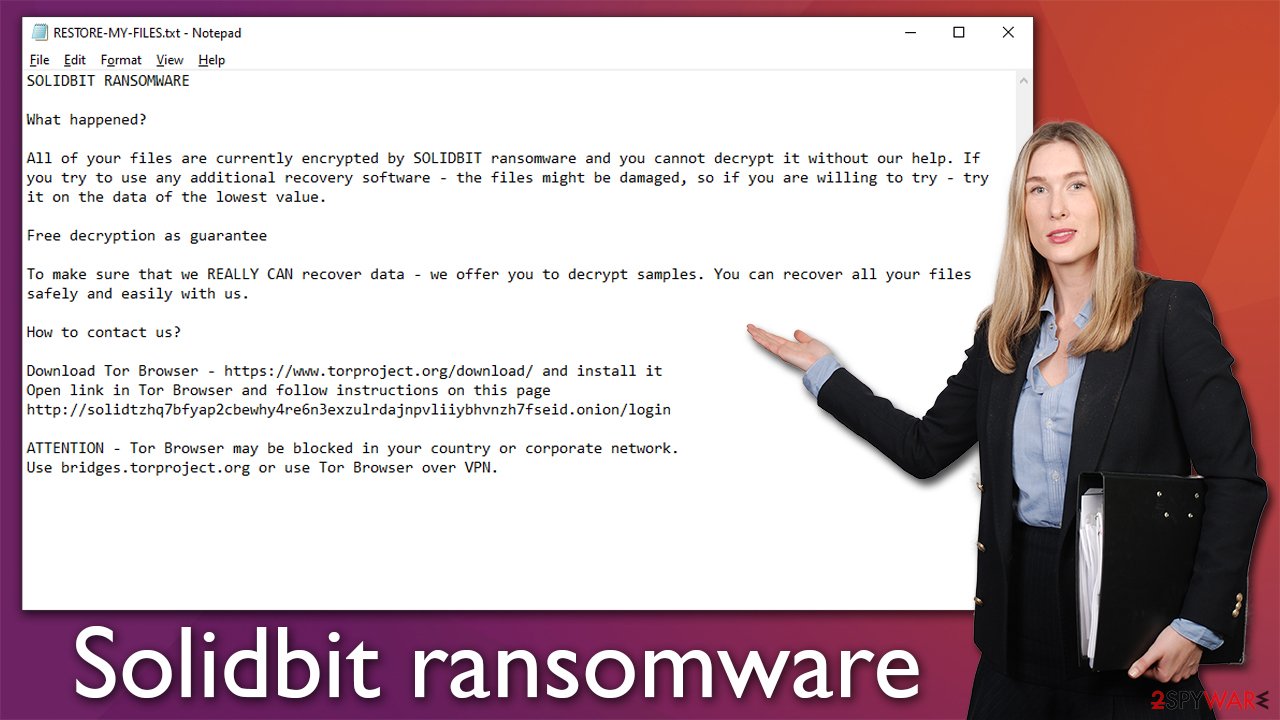
In the case of Solidbit ransomware, it targets regular computer users, and it is evident from the ransom note RESTORE-MY-FILES.txt (or a pop-up window) it provides as soon as the encryption is finished:
SOLIDBIT RANSOMWARE
What happened?
All of your files are currently encrypted by SOLIDBIT ransomware and you cannot decrypt it without our help. If you try to use any additional recovery software – the files might be damaged, so if you are willing to try – try it on the data of the lowest value.
Free decryption as guarantee
To make sure that we REALLY CAN recover data – we offer you to decrypt samples. You can recover all your files safely and easily with us.
How to contact us?
Download Tor Browser – https://www.torproject.org/download/ and install it
Open link in Tor Browser and follow instructions on this page
http://solidtzhq7bfyap2cbewhy4re6n3exzulrdajnpvliiybhvnzh7fseid.onion/loginATTENTION – Tor Browser may be blocked in your country or corporate network.
Use bridges.torproject.org or use Tor Browser over VPN.
Just as it is typical for other cybercriminals behind ransomware, they attempt to convince users that their best bet to restore files to normal is to pay the ransom. While crooks are not wrong about alternative data recovery methods damaging files beyond repair (files might indeed get damaged in the process of alternative recovery methods), there are ways to go around this.
Cooperating with the attackers is not recommended, as you may end up being a victim of a scam, regardless of what the ransom note claims. While some cybercriminals keep their promises and deliver a working decryptor, you can never be sure – these people are criminals and don't really care about their victims' wellbeing, so they might not bother sending you the decryptor after receiving the payment.
Malware removal steps
Ransomware spreads in deceptive methods, including spam email attachments, drive-by downloads, software vulnerabilities, pirated software installers, and more. In other words, users are either tricked to install the Solidbit virus or it's done via more sophisticated methods that they aren't aware of. Thus, the infection comes as a big surprise and disbelief – so much so that some people panic.
While ransomware is a serious infection, panicking won't solve anything after data has been encrypted. Your first goal is to remove malware from your system to prevent it from running on your machine – you should start by disconnecting it from the internet and the network if available.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
As soon as the system is no longer connected, you can then proceed with Solidbit ransomware removal, which you should perform using sophisticated security software, for example, SpyHunter 5Combo Cleaner or Malwarebytes. In some cases, malware might start interfering with the removal process to remain on the system as long as possible; if that is the case, access Safe Mode and perform the full system scan from there. Note that you should update the security software to the latest version before doing this.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
Alternative file recovery methods
Many users may become really confused after realizing that their files have been locked, as they can no longer access them. People tend to either believe that their files are permanently corrupted or can be easily restored by performing a system scan with anti-malware. Neither of these beliefs is true.
Cybercriminals use sophisticated encryption algorithms known as AES and RSA,[1] which are known to be very secure. The used key to lock data consists of a randomly-generated alphanumeric string, which is simply impossible to guess without knowing precisely what it is. At this point, some users might be devastated, as paying crooks can be especially pricy, and losing the files can also be extremely damaging.
We recommend a third option – trying data recovery software. Even though this method can't help all the victims, some people manage to restore at least some of their files. Before proceeding, you should make a copy of all encrypted files to prevent data corruption.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Solidbit ransomware Solidbit ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Some ransomware is simply programmed much worse than others and contains several bugs.[2] By finding them, cybersecurity researchers can create a working decryption tool that victims can use to recover their files for free. Keep in mind that this might or might not happen at all or it may take a long time. We recommend checking the following links for the decryptors from time to time:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Fix system Windows damage
As soon as malware manages to break in into the system, it no longer operates as it previously did – some files might be altered and even damaged due to virus removal or during its operation. As a result, some users might start suffering from system crashes, program errors, and more technical issues.
Instead of reinstalling Windows, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system, thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs,[3] etc.
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ What is a DLL. Microsoft. Docs.
- ^ Software bug. PCMag. The Latest Technology Product Reviews, News, Tips.
- ^ Mackrine Awino. Understanding AES and RSA Encryption Algorithms. Section. Edge computing for enterprises and developers.
















