“Terra Wallet – Unlock Your Wallet” scam (Free Guide)
“Terra Wallet – Unlock Your Wallet” scam Removal Guide
What is “Terra Wallet – Unlock Your Wallet” scam?
“Terra Wallet – Unlock Your Wallet” is a scam that tries to impersonal a legitimate blockchain site
Online scams have been prevalent for almost as long as the internet became widely accessible to the population. Since then, there have been plenty of deceptive and fake websites created for one purpose – to make people do what they otherwise wouldn't with the help of clever social engineering tricks.
“Terra Wallet – Unlock Your Wallet” is a spoofing[1] website that is created by malicious individuals to steal users' personal details and is just one of a million fake domains that could be encountered around the web. Blockchain websites have been increasingly popular, and many users create accounts in order to trade, purchase and sell digital assets such as NFTs.[2]
Terra Wallet is just another such site and is legitimate to use. Crooks, however, often impersonate popular websites in order to steal users' login credentials for personal gain. Thus, if you have encountered the “Terra Wallet – Unlock Your Wallet” scam, you should ignore it completely and never enter your sensitive information, such as login details.
Frequent redirects to malicious websites might be a sign of adware infection, though we do recommend checking the system thoroughly. We also explain what to do to recover after being affected by an online scam such as this one and provide solutions to negate or minimize the risks.
| Name | Terra Wallet – Unlock Your Wallet |
| Type | Scam, spoofing website, phishing |
| Distribution | Redirects from other malicious websites, fake links, spam emails |
| Operation | Impersonates the official blockchain website to steal users' passwords and acquire their financial details |
| Dangers | Monetary losses, privacy issues, identity fraud |
| Solution | Do not interact with the fake site and scan your device with SpyHunter 5Combo Cleaner to detect and remove malicious software |
| Additional steps | After you remove malware/adware from your system, you should also clean your browsers to avoid further privacy issues. Employ FortectIntego for that or use the manual guide below |
Scammers aim to steal your Terra Wallet account
Website spoofing (an act where a legitimate login page of a service or a website is being impersonated for the sake of tricking users into providing their passwords or other data) has been around for many years. Cybercriminals typically employ well-known names in various industries, such as Netflix, Google, or Microsoft.
With the help of visual clues such as logos, text formatting, or similar attributes, it makes victims believe that the messages are legitimate and trustworthy, without paying attention to the red flags that would otherwise be clearly seen.
Usually, potential victims receive a fake email to their inbox which claims that there is something wrong with their Terra Wallet account. In this case, crooks claim that the account has not been verified and that if no action is taken, access to it would be suspended.
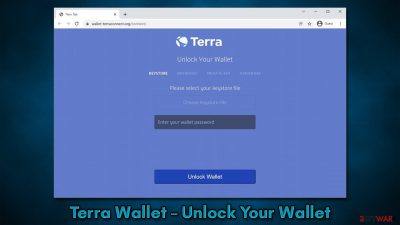
If the button, which is a link, is clicked, users are redirected to what seems like a login page to the Terra Wallet. They are asked to select the keystone file and enter the wallet password; at the bottom is the “Unlock Wallet” button as well, which is meant to finish the alleged verification process.
The scheme mimics various verification techniques practiced by legitimate service providers, hence many users could be tricked by this if not being careful. Once the information is entered and the button is pressed, the password is sent directly to cybercriminals, which would allow them to access victims' personal accounts.

It goes without saying that this could lead to various negative consequences for users, which include monetary losses and even identity theft. If you have not entered any personal details on the Terra Wallet – Unlock Your Wallet scam page, you should be relatively secure, although we do recommend checking the below section for tips on how to check the device for adware and clean cookies for better security.
Remediation tips
The recovery from the scam highly depends on the steps you took prior, as they determine what type of damage could be done to your privacy and security. If you have entered your password or any other details, there is a chance of a personal data leak.
The first thing you should do is access the original Terra Wallet account and change your password immediately. If crooks already changed your password, you should contact website support and let them know of what happened, they should be able to help you with account recovery. If you are reusing the same password anywhere else (which you should never do by the way), you should change the passwords on those accounts as well.
If you have not entered any details into the spoofing site, you are likely to be safe. Clicking the button that directs you to the spoofing site is usually not harmful, although there is a slim chance of malware infections under certain circumstances. Therefore, we recommend you check your system with SpyHunter 5Combo Cleaner or Malwarebytes security software to be safe.
Another check you should perform is adware. While security software should be able to deal with the most aggressive PUPs and all types of malware, redirects might be caused by browser extensions or apps that do not trigger detection. Thus, use the following instructions:
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
Browser extensions can also be the cause of redirects and ads. You should check the extension section and remove all the suspicious apps. Note that, in some cases, seemingly trustworthy apps might go rogue, so we recommend removing them all and then checking the ads and redirects stop.
Also, take your time to clean your browsers, as some components might result in privacy risks. For example, cookies might be stolen by criminals and personal accounts accessed. To avoid this, either rest your browser or remove caches, cookies, and other web data from them. To speed up this process, you can use FortectIntego.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
How does the scam spread and how to avoid it
There are several ways how users might be affected by an online scam. Spoofing websites are usually targeted, although some users might encounter them accidentally. Let's start from the most probable scenario though.
As we already explained, threat actors create a legitimately-looking website that is actually fake. The only thing that's left is to make people visit it and provide personal information that can later be sold on the dark web or used for other malicious purposes, such as targeted phishing[3] attacks.
This is the email that could lead you to the “Terra Wallet – Unlock Your Wallet” scam:
Dear customer,
Our system has shown that your Terra Wallet has not yet been verified. This verification can be done easily via the button below.
Unverified accounts will be suspended on [date]. Please make sure to verify your wallet as soon as possible. We are sorry for any inconvenience we cause doing this, but please keep in mind that our intention is to keep our customers safe and happy.Thank you for your understanding
The email looks legitimate because cybercriminals use almost identical email address spelling and most people would not spot anything wrong with it if not looking carefully. In some cases, the sender might be something entirely different, and it's the first sign of deception.
When in doubt, we strongly recommend you use your browser to access the account in question directly. Do not use links within emails (unless you are absolutely sure that they are secure and legitimate) to then enter personal details – keep in mind that the looks of the page are really easy to replicate.
It is unlikely that you would encounter a spoofing website after being redirected from somewhere, although it's not impossible. Avoid using high-risk websites (torrents, cracks, illegal video streaming, etc.) and employ tools such as ad-blockers to prevent redirects and malicious scripts from being executed.
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Website spoofing. Wikipedia. The free encyclopedia.
- ^ Mitchell Clark. NFTs, explained. The Verge. Technology, science, art, and culture.
- ^ What is Phishing?. Check Point. Software technologies.








