The Pray Time browser hijacker (virus) - Free Guide
The Pray Time browser hijacker Removal Guide
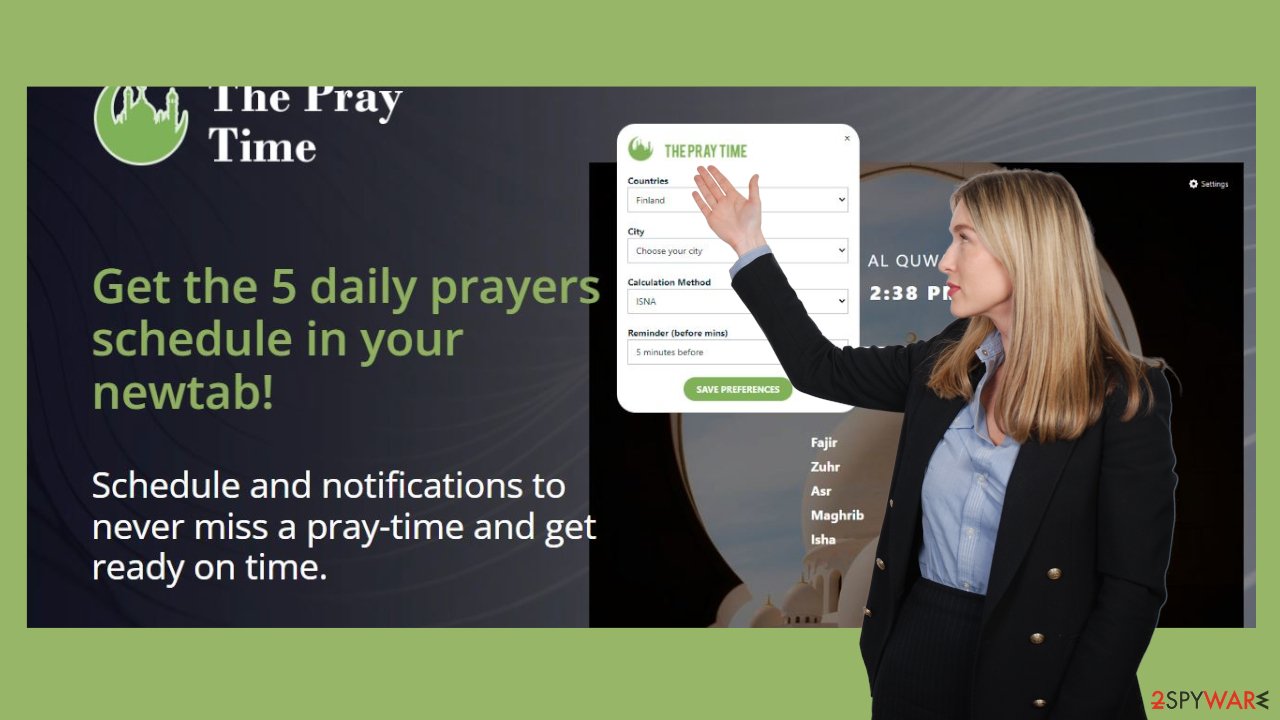
What is The Pray Time browser hijacker?
The Pray Time changes browser settings under the guise of providing a praying schedule

The Pray Time app functions as a browser hijacker that is intended to advertise a fraudulent search engine. Similar to other apps in the same category, The Pray Time alters a web browser's configuration settings in order to perform browser hijacking. This is achieved by replacing the homepage, new tab page, and default search engine with thepraytime.xyz, a fake search engine that reroutes users to google.com, the actual search engine.
Nevertheless, using The Pray Time or thepraytime.xyz does not ensure a secure online experience. Users are frequently exposed to false information and shady adverts by fraudulent search engines, which frequently provide inaccurate and untrustworthy search results.
Furthermore, these phony search engines and browser hijackers have the potential to illegally gather and exploit user data, such as search terms, browsing habits, and private data. Additionally, browser hijackers can cause serious performance problems and considerable browsing slowdowns, which can be frustrating for users who experience lags, crashes, or freezes when trying to access the web.
| NAME | The Pray Time |
| TYPE | Browser hijacker; potentially unwanted program |
| SYMPTOMS | The main settings of the browser get changed, like the homepage, new tab address, and search engine |
| DISTRIBUTION | Shady websites, deceptive ads, freeware installations |
| DANGERS | Users might get redirected to shady sites that can trick people into downloading PUPs or even malware |
| ELIMINATION | Remove the extension in your browser settings |
| FURTHER STEPS | Use FortectIntego to fix any remaining damage and optimize the machine |
Distribution methods
Browser hijackers use a variety of techniques to spread around the Internet. Some crooks make websites specifically devoted to promoting their plugins, which they subsequently advertise on questionable online forums. As such, it is essential to proceed with caution and not to take any internet adverts at face value. Avoid clicking on random buttons and links, especially on websites that participate in illegal activities. These websites frequently contain hidden redirects and misleading adverts.
While we always recommend purchasing browser extensions from trustworthy internet retailers, it's important to understand that con artists have developed strategies to get around strict review procedures. Because of this, some browser hijackers, like The Pray Time can obtain listings on trustworthy websites like the Chrome Web Store.
Make sure you do your homework well in order to protect your online experience. Assess the number of users a plugin has garnered, read user reviews, evaluate ratings, and consider other feedback. Select programs that have a significant number of satisfied users and comments. Examine the plugin's description carefully, paying close attention to grammar and spelling; any discrepancies in this area should serve as a warning sign.
The Pray Time hijacker removal steps
Browser hijackers are considered relatively minor infections, falling short of the malevolence exhibited by Trojans, ransomware, or other forms of malware. Consequently, users typically encounter minimal difficulty in eradicating them. By diligently adhering to our detailed, step-by-step guide, you should be able to expel the intruder effortlessly.
Typically, hijackers establish a presence within web browsers, necessitating the removal of the primary culprit – the browser extension – to fully eliminate the potentially unwanted program (PUP). If you have limited experience dealing with browser add-ons, we have provided comprehensive instructions below for your assistance.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Check your system for PUPs
The Pray Time works as a browser plugin, however you should be aware that other programs could be covertly doing harmful things to your computer. This situation becomes particularly important if you obtain software from dubious sources regularly. It is important to proceed carefully while installing bundled installations since they can unintentionally add other software to your system. For this reason, you should check your computer's installed software list.
Freeware platforms are frequently utilized for the distribution of adware and other potentially unwanted programs (PUAs). For software installation, we strongly advise using only official web stores or developer websites. Select “Custom” or “Advanced” installation, carefully read the Terms of Use and Privacy Policy, and make sure the checks next to unnecessary apps are left unchecked when looking through the file list.
To successfully remove PUAs from your device, think about doing a thorough scan with reliable anti-malware programs like SpyHunter 5Combo Cleaner, Malwarebytes. This step guarantees that any hidden malicious programs and background processes are found and eliminated. There is a higher chance of malware infection for users who browse dangerous websites. Since these programs are frequently hidden, it can be difficult for regular computer users to detect the existence of malware without the aid of security software.
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till the uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
3. Clean your browsers
Cookies are small pieces of data that are used to include all sorts of settings. While they cannot be malicious by themselves, they can be stolen by third parties and used for malicious purposes. They can store information such as your IP address, geolocation, websites you visit, links you click on, and things you purchase online.
Therefore, security experts advise cleaning web browsers regularly. You can employ automatic cleaning tools such as FortectIntego, although you can also refer to the manual instructions below.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
How to prevent from getting browser hijacker
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.












