TigerVideoSearches hijacker (virus) - Free Guide
TigerVideoSearches hijacker Removal Guide
What is TigerVideoSearches hijacker?
TigerVideoSearches extension hijacks your browser
If your search engine has changed to feed.tigervideosearches.com your browser has been hijacked by TigerVideoSearches extension or a potentially unwanted program. Besides changing your homepage, this unwanted extension alters your search results and does not disclose which links are promotional, so users think all the results are honest.
It is believed that browser hijackers have originated from a group of software companies in Tel Aviv, Israel, called “Download Valley,”[1], which produces software that monetizes freeware. Some of the software produced by these companies are adware, spyware, and hijackers.
At first glance, this extension can look useful with features such as a PDF converter, calculator, regular currency, and cryptocurrency converter and an option to save your favorite websites. Even so, you probably have not added this tool yourself but have been tricked into it by a deceptive ad or by downloading freeware that added it to your browser.
Potentially unwanted programs spread by bundled software methods[2] can cause a lot of unusual behavior. So it is best to stay away from free or cracked versions of programs provided by questionable websites instead getting an application you want through legitimate sources.
| NAME | TigerVideoSearches |
| TYPE | Browser hijacker |
| DISTRIBUTION | Deceptive ads, bundled software, freeware installation |
| SYMPTOMS | The homepage and new tab address have changed to something else; a customized search engine; search results are filled with sponsored links and ads without disclosure |
| DANGERS | Privacy issues because of the information gathering, users might get tricked into installing unsafe software |
| ELIMINATION | You can get rid of unwanted extensions manually via browser settings |
| FURTHER STEPS | Use a remediation tool FortectIntego for your web browsers to try and fix any damage left |
Security threats you need to worry about when using extensions
Browser extensions can be more sneaky than people realize. These tools often have access to everything you do online so that they can capture the websites you visit, links you click, items you purchase. Often they also insert advertisements into web pages you visit. Popular browser extensions are sometimes sold to shady companies or hijacked, and automatic updates can turn them into malware.
Adverts displayed by this addition are not filtered, so they can lead to dangerous websites and trick you into giving away your personal data or install untrustworthy software. All the developers of these kinds of programs care about is revenue generated from pay-per-click ads. This is a negative environment for a user when you are constantly exploited for others' gain and do not know which websites you click on are legitimate and which ones are placed by advertisers.
There definitely are ways for you to protect yourself from intruders. One of the most effective things you can do is research before adding anything to your machine. Read the reviews and see if there are any serious complaints or if the reviews look overly positive and repetitive. They might have been posted by bots.[3] The next smart move is to read the privacy policy and determine how your information will be used. For example, TigerVideoSearches Privacy Policy states:
By Using the Product, you may enable us or third parties to access, use, and collect a variety of information, regarding your Internet Browser, your browsing habits, and information about your computer including by usage of cookies.
As you can see, having this add-on allows it to collect any information, which might later be forwarded to third-parties. This is not a good situation if you care about your privacy and should take action immediately. You can remove TigerVideoSearches manually by following our step-by-step instructions.
Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Microsoft Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.
![Remove extensions from Edge Remove extensions from Edge]()
Microsoft Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Mozilla Firefox:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
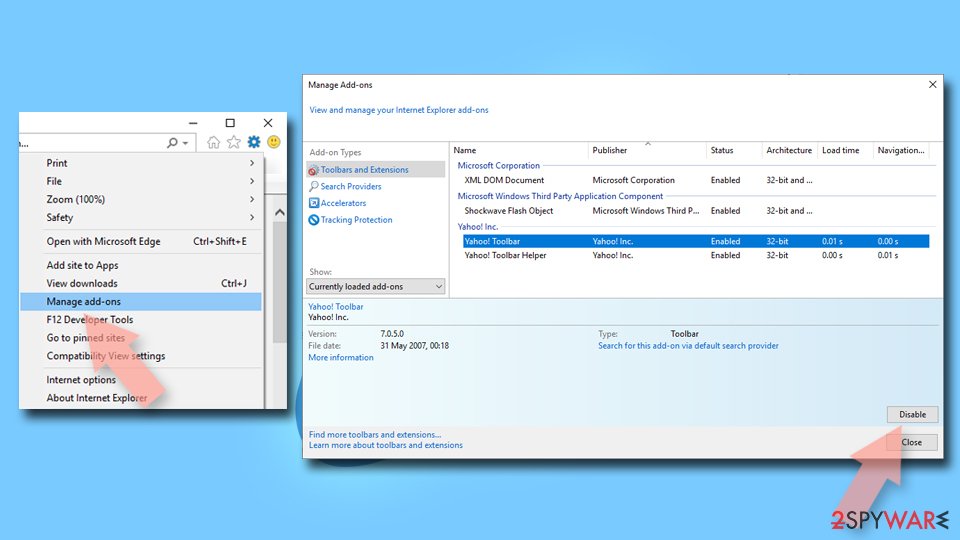
Internet Explorer:
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
![Remove add-ons from Internet Explorer Remove add-ons from Internet Explorer]()
Cookies and cache
Web browsers such as Firefox, Safari, Chrome, and Internet Explorer keep a local copy of web pages and other related items in your memory to speed up the reloading time of previously visited pages. While this generally improves your browsing experience, it can slow down your device if the cache gets too big. This can also prevent a web page from loading in the most up-to-date information. If you are having either of these problems, try clearing your browser cache.
Some websites store information in a small text file called a “cookie” on your hard disk. Cookies typically contain information about you and your preferences for a website. That way, the site can personalize the pages you see on the next visit. Cookies can be a bad and a good thing depending on the website you visit in terms of who will acquire access to your data and what they will do with it.
It would be best if you stayed away from unencrypted websites with HTTP and not HTTPS in the link. If a website is not encrypted, then it is not protecting your privacy. It is better to decline cookies on websites like this or delete them if you already accepted.
Third-party cookies let a website owner sell your browsing data to third parties like advertisers. In this case, you would have no control over what the third parties do with your data. Unknown sources could use your personal data to commit online crimes.
Even though they are small, cookies take up space on your computer. If it has been a long time since you last cleared them, they could slow down the speed of your computer and other devices.
It is recommended to clear your cookies and cache after removal of TigerVideoSearches to delete any information that was collected about you. You can do this yourself by looking at the guide below or by getting FortectIntego to do this for you automatically.
If none of these steps helped you get rid of the hijacker, that could mean that it is not just a simple extension added to your browser but a potentially unwanted program that does such things without your knowledge. How to remove a program from your computer manually, you can find at the very bottom of this post. If you do not know which program could be responsible for your inconveniences, you shall use SpyHunter 5Combo Cleaner or Malwarebytes professional security software to help you with this task.
Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Clear cookies and other browser data from MS Edge:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.
![Clear Edge browsing data Clear Edge browsing data]()
Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Clear cookies and site data on Mozilla Firefox:
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
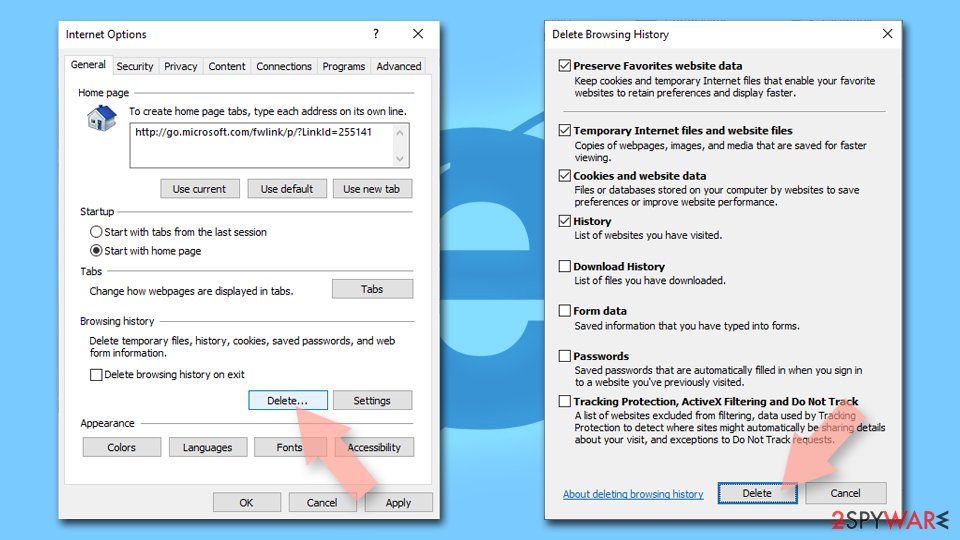
Delete temporary files from Internet Explorer:
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
![Clear temporary files from Internet Explorer Clear temporary files from Internet Explorer]()
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of TigerVideoSearches hijacker. Follow these steps
Uninstall from Windows
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of TigerVideoSearches hijacker registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting browser hijacker
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Wikipedia. Download Valley. Wikipedia. Free Encyclopedia.
- ^ Will Dormann. Bundled Software and Attack Surface. Carnegie Mellon University. Software Engineering Institute.
- ^ Reevoo. The bot army — the latest threat to open review systems. Reevoo. Learning Hub.