Tk ransomware (Removal Instructions) - Bonus: Decryption Steps
Tk virus Removal Guide
What is Tk ransomware?
Tk ransomware demands 1 BTC in exchange for the decryption key

Tk virus functions as a ransomware-type infection which uses AES algorithm[1] to encrypt the most valuable data. It was first discovered at the beginning of January 2017 demanding to pay 1 Bitcoin for the decryption tool. The original filename of this file-encrypting virus is your files have been encrypted.exe.
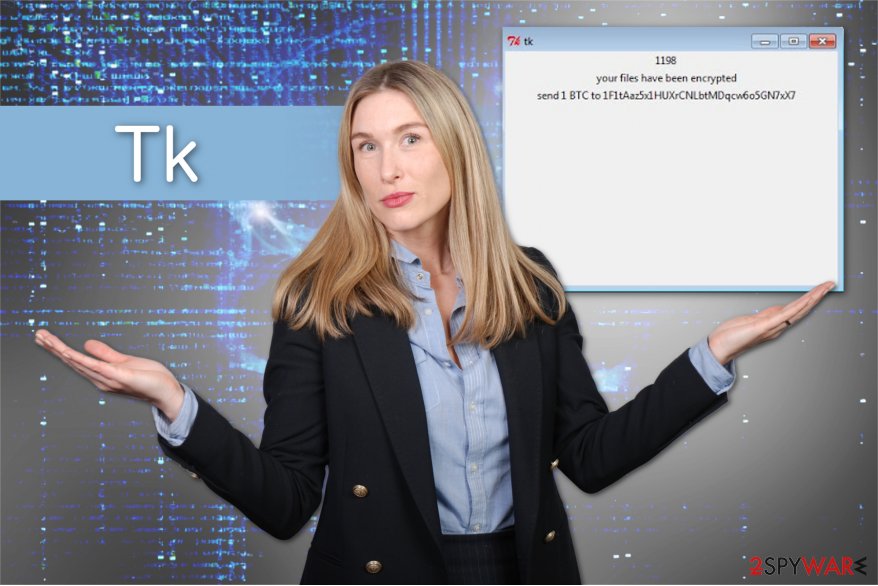
Users report receiving the following message after Tk attack:
1198
your files have been encrypted
send 1 BTC to 1F1tAaz5x1HUXrCNLbtMDqcw6o5GN7xX7
Usually, criminals indicate a specific e-mail address for contact purposes. However, Tk ransomware directly provides the Bitcoin account to which people should make the transaction to recover encrypted files. Although, obeying the rules of the crooks is not the best decision.
There are numerous cases when people agreed to pay the ransom and were tricked by the empty promises of the cybercriminals. Therefore, we suggest you to remove Tk virus instead of paying the demanded money. You can always recover encoded information from the backup copies stored in the cloud.
If you do not have them, feel free to use alternative data restore techniques which are presented at the end of this article. However, do not forget that you will only be able to proceed to retrieving your data after Tk removal. You can do that with the help of FortectIntego or SpyHunter 5Combo Cleaner depending on your preference.
Please, do not try to eliminate TK ransomware virus from the system on your own. These attempts might end up with the irreparable damage to the system. File-encrypting viruses can affect legitimate system processes or hide under the safe-looking names, so you might be tricked and uninstall wrong entries.
Watch out suspicious spam emails and questionable software installers to avoid ransomware
Ransomware mostly spreads via malicious spam emails. These letters are perfectly crafted using social engineering strategies. Therefore, users can be easily tricked into opening a safe-looking attachment.[2]
Usually, these emails inform about a serious issue or ask to check the information provided in the attached Word, Excel, or another legitimate-looking website. However, once opened, malware executable is dropped on the system.
However, other malware distribution might be used to spread TK ransomware as well. For instance, criminals might use fake software downloads or updates that might be delivered in the form of pop-up or available on the questionable file-sharing websites, torrents or P2P networks.
Security specialists from virukset.fi[3] also suggest being careful with eye-catching ads, installing software and OS updates, and secure remote desktop connections. Additionally, creating backups should be on your priority's list as well. You can never know what tricks developers of ransomware might create for you.
Delete Tk ransomware virus with anti-malware software
Tk ransomware removal requires using professional malware removal software, such as FortectIntego or Malwarebytes. It's important to use security programs to terminate malicious components safely. Malware may have injected malicious code into legit system processes and installed numerous files that are responsible for hazardous tasks.
To remove Tk ransomware with all its components manually is nearly impossible without damaging the system if you are not experienced IT specialists. Thus, in order to avoid further damage, you should use anti-malware tools.
Once you get rid of Tk virus, you can restore your files from backups or use alternative methods. You can find available recovery options below, as well as detailed instructions how to disable malware in case you encouter some obstacles with its removal.
Getting rid of Tk virus. Follow these steps
Manual removal using Safe Mode
Typically, ransomware-type viruses are able to prevent you from installing a security software. Thus, you must disable Tk malware by rebooting your computer to Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Tk using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Tk. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Tk from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Tk, you can use several methods to restore them:
Experts recommend Data Recovery Pro
We strongly suggest you try recovering files with this professional tool. Additionally, it can help you to restore files if you have accidentally deleted them.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Tk ransomware;
- Restore them.
Windows Previous Versions feature can be handy
You must first check if System Restore was enabled before Tk virus infiltration to use this application. If it was, follow the guidelines below.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer can be useful
Fortunately, Tk ransomware currently does not delete Shadow Volume Copies from the victimized computers. Likewise, you are free to use this alternative recovery software.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Sadly, but there is no official Tk decryptor yet
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Tk and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Advanced Encryption Standard. Wikipedia. The free encyclopedia.
- ^ Bert Rankin. Top 10 Malicious Email Threats. Lastline Blog. Cyber security news.
- ^ Virukset. Virukset. Latest security and malware news.





















