Trins ransomware (virus) - Free Instructions
Trins virus Removal Guide
What is Trins ransomware?
Trins ransomware is a file-encrypting virus that demands ransom for a decryption tool
Trins is a ransomware-type virus that targets Windows-based computers. First spotted attacking victims at the end of May 2022; it doesn't seem to be related to any previously known malware family. Nonetheless, the damage it can cause to victims is still significant, and the infection should always be treated seriously.
As soon as Trins ransomware manages to break into the system, it begins to look for files to encrypt[1] – be it documents, databases, pictures, videos, or any other personal data, all of it would become inaccessible after this process is finished. Users can easily see that their files have been altered due to them losing their original icons and are appended with .trins extensions.
In order to recover access to files, users have to pay an undisclosed amount of money via a bitcoin transaction. As stated in a ransom note RECOVERY.txt, which is dropped on the desktop after the data locking process, victims have to download the Tor browser and create a special email, sending their personal ID via the Retailgaze@onionmail.org email.
| Name | Trins virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .trins |
| Contact | Retailgaze@onionmail.org |
| Ransom note | RECOVERY.txt |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
The ransom note analysis
Trins virus seems to be yet another attempt from cybercriminals to earn money from victims. In order to increase the chance of this happening, crooks make sure that a ransom note is delivered to users as soon as the file encryption is complete. In fact, this is very typical behavior that most malware of this type exhibit – without communication means, victims are unlikely to pay.
The description of what users have to do to restore their files is relatively brief; most negotiations about ransom size and other peculiarities between both parties happen via the email – that's why the attackers ask people to make an email account via Tor, making the communication anonymous and undetectable. Cybercriminals often take precautionary measures to hide the tracks of their illegal business.
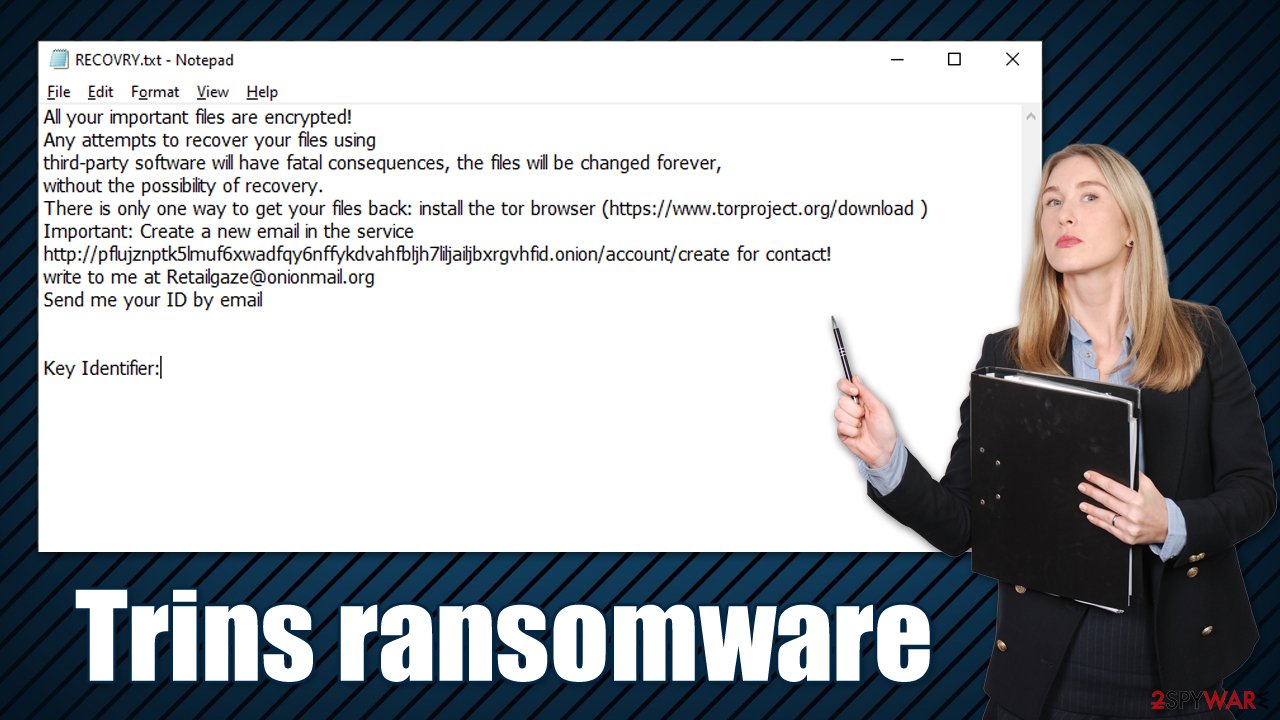
The note informs victims that the crooks' goal is to receive payment in Bitcoin, and there is no other way to recover data apart from paying (they also say that users shouldn't try to restore files themselves). This may or may not be true, although decrypting files without a unique key assigned upon encryption might be extremely difficult, if not impossible.
However, ransomware is not always perfect, and errors during the encryption might occur. For example, malware might fail to remove Shadow Volume Copies (an automatic Windows data backup system), in which case data recovery would be pretty easy. We do not recommend paying the attackers, as it would only encourage them to infect more people. Besides, they may never send a working decryption tool, even after the money is transferred.
The ransom note presented by the Trins virus upon infiltration:
All your important files are encrypted!
Any attempts to recover your files using
third-party software will have fatal consequences, the files will be changed forever,
without the possibility of recovery.
There is only one way to get your files back: install the tor browser (https://www.torproject.org/download )
Important: Create a new email in the service http://pflujznptk5lmuf6xwadfqy6nffykdvahfbljh7liljailjbxrgvhfid.onion/account/create for contact!
write to me at Retailgaze@onionmail.org
Send me your ID by email
How to remove Trins ransomware from the system correctly
Many users who get infected with ransomware have never dealt with it before, which can be a rather frustrating experience. It is extremely important to proceed with removal and recovery steps in the correct order, or data may get permanently corrupted under certain circumstances.
Your first task is to make sure that the affected Windows computer is not connected to a network or the internet. The connection to Command & Control[2] can be severed in this way as well.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Without the network and internet connections, the attackers can no longer communicate with ransomware, which is a good time to begin the Trins ransomware removal process. This step can be easily achieved with the help of powerful security software, such as SpyHunter 5Combo Cleaner or Malwarebytes – simply update the app to the latest version and perform a full system scan. If malware prevents security software from functioning correctly, you can access Safe Mode and try from there:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
![Recovery Recovery]()
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
![Press F5 to enable Safe Mode with Networking Press F5 to enable Safe Mode with Networking]()
Attempt data recovery
Before you proceed with the file recovery process, there are a few pointers that are extremely important:
- Make a copy of your encrypted files and place it on a separate medium, such as a USB drive;
- Security software won't and can't recover .trins files – it is simply not designed for it;
- Even if the solutions below do not work, this might change in the future, as cybercriminals could get captured or bugs[3] inside malware detected.
Decryption tools might also be created for certain ransomware strains thanks to the efforts of security researchers. In some cases, law authorities seize the servers of malicious actors,[3] which allows the keys to be released by the public – reputable security vendors usually do this. Here are a few links you might find helpful:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

In case there is no decryptor available (which is usually the case with new malware strains), you should not give up just yet. A special data recovery software might still be useful. As we already mentioned, malware might fail to remove Shadow Copies from the system, which would allow recovering of previous versions of files. Proceed with the following:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Trins ransomware Trins ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Fix damaged system files
Malware infection might damage Windows system files, and security software would not be capable of repairing them. Anti-malware is there to delete all infections from your system, and it can't do anything more. However, after the ransomware is eradicated, it may come to light that the system starts to crash, returns errors, or fails to launch applications.
In this case, Windows Registry or other relevant files might have been corrupted. While you may think that Windows reinstallation is necessary to correct these issues, it is not the case at all, as you can instead use a powerful PC repair tool that could replace damaged sectors with brand new ones automatically:
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ What is Data Encryption?. Kaspersky. Resource Center.
- ^ Command and Control [C&C] Server. Trend Micro. Security research blog.
- ^ Software Bug. Techopedia. Technology Dictionary.


















