Wetransfer virus (Free Guide) - Removal Instructions
Wetransfer virus Removal Guide
What is Wetransfer virus?
Wetransfer virus is the malicious email campaign that sends malware via WeTransfer platform
The most important thing to note about this WeTransfer Email virus is that anything can be sent to you via those file transfer links, so opening any of them and following with download can lead to trojan infections and even more serious issues regarding the personal privacy and security of your device. The trojan that is, reportedly, distributed with the help of these spam campaigns is a password-stealing trojan that also can be considered banking malware because the most valuable credentials are the ones linked to online banking sites. This high-risk malware can possibly have a wide range of abilities and be set to take control of your device and exfiltrate data or damage the machine entirely. You need to be cautious and react to this infection as soon as possible, so crucial damage can be avoided.
| Name | WeTransfer virus |
|---|---|
| Type | Malware delivering email campaign/ Trojan |
| Tactics | Emails with claims about purchase details, company messages, and other requests get sent to random people and include links to file transfer platform where the people get to download archived data or an executable file malware payload |
| Spreads | It is known for delivering the payload of Kryptik trojan |
| Distribution | Social engineering campaigns allow malicious actors to obtain email addresses of people, data leaked during some security incidents and other deceptive methods allow to access such details, so various random users online receive these malicious emails with malware delivering links and file attachments |
| Danger | This phishing campaign[2] can easily spread various malware and lead to hacker attacks or campaigns of data exfiltration and so on. Viruses that spread via these stealthy methods can be set to damage machines and perform other background processes |
| Elimination | WeTransfer virus removal is not the easiest procedure, but you can get the best results with anti-malware tools that manage to find and remove all kinds of files and applications that may get placed all over the machine during the infection |
| Repair | You should also think about the damage that virus causes on an affected system, so get FortectIntego or a similar tool that repairs files or at least can help with system performance and optimization |
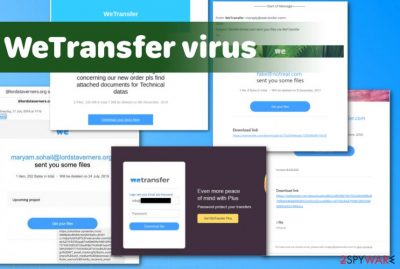
WeTransfer Email virus message can include banners, logos, and other identifiable information that resembles the legitimate platform to fake the secureness and legitimacy and trick people into downloading attached files this way. The email itself is a brief text about the file that is included in the download link.
Recipients who click on the provided link are led to the login page of the WeTransfer platform, and this is where phishing begins because this landing page is the form where you fill in the information and trigger the malicious installation.
Users who encountered the Wetransfer virus message stated that once the information is put in the message states about incorrect password and the phishing stops here. The message looks like this:
Click 'Download images' to view images
********
sent you some documents PDF
2 item, 768 KB in total ・ Will be deleted on 30 October, 2019
Our company profile as requested and Purchase Order.pdfGet your files
Download link
hxxps://kingsdoggy.blaucloud.de/index.php/s/*****
2 items
Company profile.pdf
Purchase Order.pdf
700 KB
To make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
About WeTransfer ・ Help ・ Legal ・ Report this transfer as spam
Additionally, the Wetransfer virus relies on other methods that help to look like genuine notifications. High-quality graphical elements, branding, and logos allow them to mimic the popular file-sharing platforms and take advantage of more gullible people. The email intrigues and tells receivers that a new file is arriving after the phone conversation or additional exchange of emails. Driven by their curiosity, people follow the suggestion to click on the provided link.
You need to remove Wetransfer virus infection possibility by deleting the email as soon as you receive it, so there is no opportunity for the malicious payload to get triggered and dropped on the machine. If that happens you will need more powerful tools to tackle the malicious infection. Trojans malware and even ransomware can get installed like this, so the only way to get back the machine in your control is anti-malware programs. 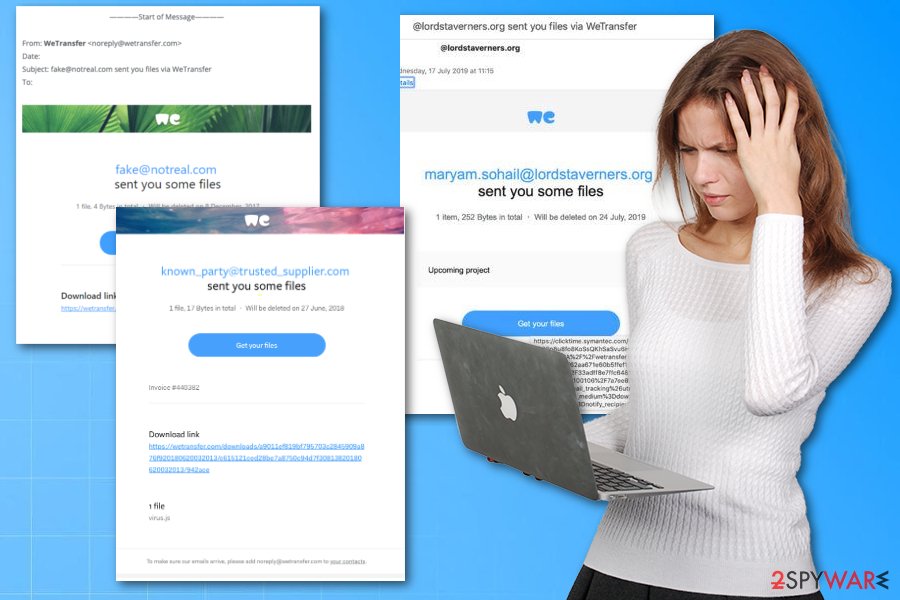
WeTransfer Email virus removal can get difficult if your device gets affected further by the malware delivered from the download link. Experts comment on these issues and possible phishing ploys helping to get users' attention:
Here, the threat actor will often write a note stating that the file is an invoice to be reviewed.
When WeTransfer Email virus campaign results in the trojan, banking malware or another virus infection, you need to get involved in serious malware-fighting procedures with tools that can detect[4] this malicious software. The various analysis may show that the file ad link can be detected by AV tools before it goes on the machine, but you need to keep your anti-malware tools up-to-date, so the program is properly working. This is not the case for many people.
Keep the machine safe and avoid anything related to WeTransfer virus removal by using system optimization tools, security software like FortectIntego that can indicate suspicious emails, sites, and links for you before you trigger any infections. These spam emails can deliver anything and everything, and there are many versions of emails, notifications, links, and file transfer forms.
WeTransfer virus baiting techniques are trendy among malicious actors, and several active campaigns employed such methods to target sensitive information. HTML elements may get used to hiding malicious URLs from the antispam features of security software. You may encounter advanced techniques and malware that show no symptoms, so rely on AV tools that are reliable and scan the machine fully to clean the system and get rid fo the virus damage. 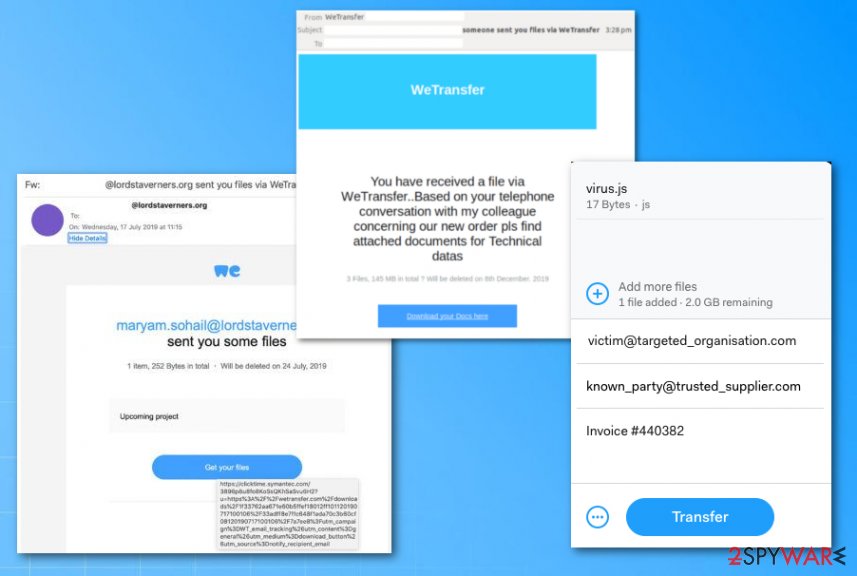
Spotting the difference between legitimate and phishing emails
If you are communicating with any services like this platform, you may fall for the phishing campaign and install the malicious program without considering to look out for red flags. Opening the suspicious email notification alone can trigger the drop of the trojan or virus, so pay attention to:
- the layout of the email and differences with previous emails;
- typos, grammar mistakes;
- what domain is on the link that you got redirected to;
- senders' address;
- attachments, links, and other active buttons on the email itself.
You need to defend your inbox by practicing good common sense and keep these scammers in mind every time you receive a suspicious email. Keep proper security tools on the machine and run it occasionally on the system, so any possibly dangerous files get blocked in advance.
Remove Wetransfer virus with proper tools, so all trojans get terminated
You need to take this WeTransfer Email virus seriously and clean the machine from any possible intruder or malicious file, so there are no risks of getting hacked or lose data from the machine directly or by getting on phishing sites and providing your personal details to malicious actors.
To remove Wetransfer virus properly, you need to clear any suspicious emails from the inbox and make sure to delete them from the trash too. Resetting the browser may be optional, but also helpful when some of the redirects include PUPs and shady methods of exposing the user to dangerous sites.
Wetransfer virus removal gives better results, however, when you clean the whole machine. Get FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes and run a full system check to find and eliminate all possible threats. Some of the trojans and malware can block these apps, so rely on Safe Mode first and then run the anti-malware program.
Getting rid of Wetransfer virus. Follow these steps
Manual removal using Safe Mode
You can reboot the machine in Safe Mode and try to eliminate Wetransfer virus this way
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Wetransfer using System Restore
Clean the machine with the help of System Restore feature
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Wetransfer. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Wetransfer and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Tom Spring. Popular File-Sharing Service WeTransfer Used in Malicious Spam Campaigns. Threatpost. Breaking news in cybersecurity world.
- ^ Phishing. Wikipedia. The free encyclopedia.
- ^ Reporting a transfer as SPAM and what to do if you think you've received spam. Wetransfer. Customer help center.
- ^ Malicious email link AV detection. Virustotal. Online malware scanner.





















