Wikipedtoday.com scam (fake) - Free Instructions
Wikipedtoday.com scam Removal Guide
What is Wikipedtoday.com scam?
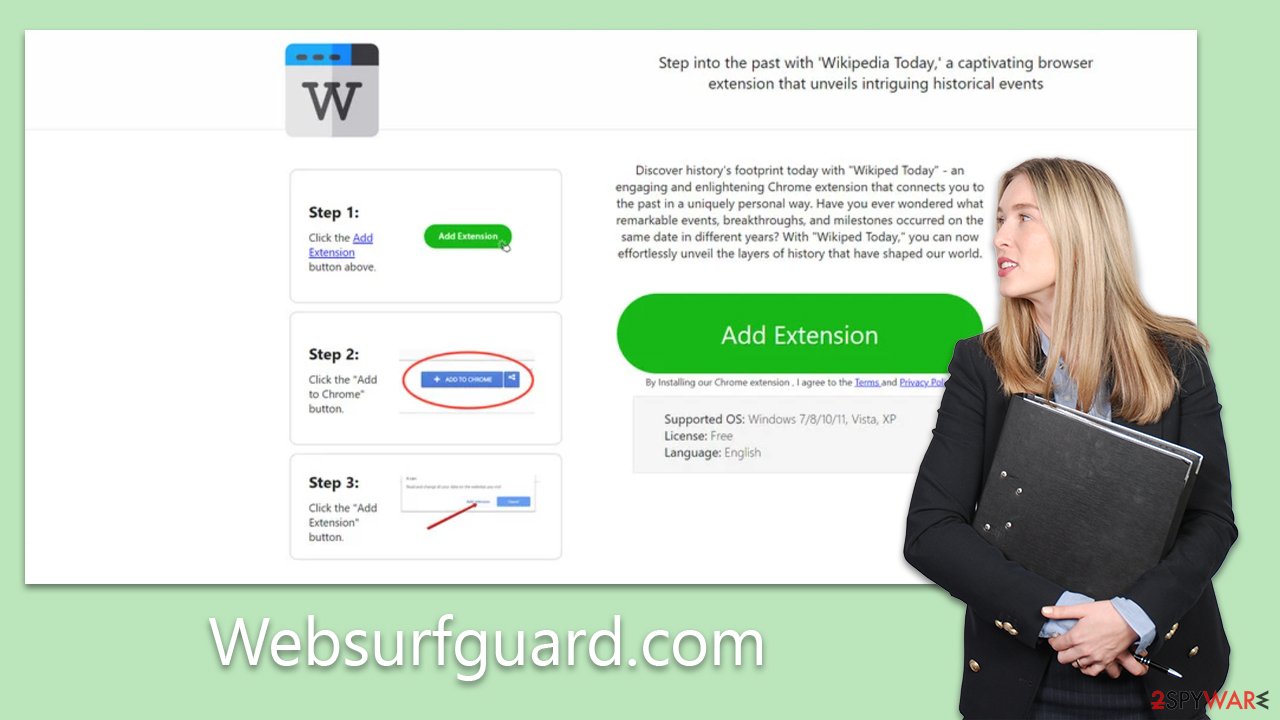
Wikipedtoday.com shows fake messages urging users to install suspicious extensions
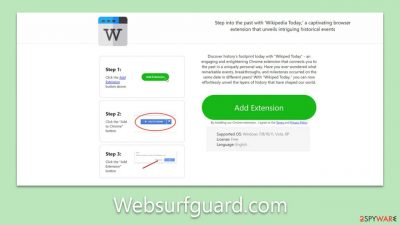
In the landscape of the internet, there are websites that operate to the detriment of unsuspecting users. Wikipedtoday.com stands out as one such problematic site. At its core, it specializes in displaying deceptive messages that encourage users to download questionable browser extensions. The aftermath can be intrusive and compromising for those who fall prey to these prompts.
Once these extensions are installed, they often inundate browsers with unsolicited ads, disrupting the user experience. Furthermore, they may also alter crucial browser settings, sometimes without the user's awareness. However, the concerns do not end there. These extensions often have the added capability to monitor and record user data, putting personal and private information at risk. Such actions can have both immediate and long-term implications for security and privacy.
The urgency to address this issue cannot be understated. If you have these extensions, they should be removed promptly. Notably, if you find your browser redirecting to dubious websites like Wikipedtoday.com, it's a strong indicator that a potentially unwanted application (PUA) might already be operational on your device. Below, you will find information about the scam and the removal of potentially unwanted software from the system.
| Name | Wikipedtoday.com |
| Type | Redirect, scam, phishing, adware |
| Distribution | Software bundles, malicious websites |
| Symptoms | Shows fake ads and promotes potentially unwanted applications |
| Risks | Installation of potentially unwanted software, such as browser hijackers. Redirects may also lead to dangerous sites, resulting in financial loss or personal data exposure to unknown parties |
| Removal | Do not interact with scam content; if you did, uninstall the unwanted browser extension and check your system for other infections with SpyHunter 5Combo Cleaner anti-malware |
| Other tips | Remove caches and other web data to prevent data tracking – use the FortectIntego repair and maintenance tool. You can also repair damaged system components with it |
How the scam operates
Online fraud is pervasive, and most internet users, at some point or another, will likely encounter it. These unpleasant encounters often arise when users inadvertently visit suspicious websites such as Syscod.xyz or Empermin.com. But sometimes, even reputable sites aren't immune; they can be compromised by cybercriminals who exploit vulnerabilities, turning them into temporary traps for unsuspecting visitors.
A recurrent tactic employed by these malicious actors is redirection. Imagine you're surfing the web, perhaps reading an article or checking out a popular forum. Suddenly, your screen changes, and you're ushered – often without your explicit consent – to a site like Wikipedtoday.com. Here, the bait is laid out: a seemingly useful browser extension.
Sometimes, it's presented as a tool with a benign function, like a “Quick Weather Checker” or an enticing “Superfast Download Manager.” In other instances, they might appeal to a broader audience by promoting extensions that promise to block annoying ads, further masquerading their true intent.
The psychology behind these scams is rooted in our inherent desire for convenience and enhancement of our online experience. By presenting tools that ostensibly improve browsing, scammers prey on this universal human inclination. They understand that an average user, faced with the promise of a more streamlined or ad-free browsing session, might be quick to install without much skepticism.
However, the true nature of these extensions is far from their advertised capabilities. Once installed, they rarely deliver on their promises. Worse, they often kickstart a series of nefarious activities almost instantaneously. Beyond bombarding users with ads or changing browser settings, they might collect personal data, track online behaviors, or even introduce other malicious software to the device.
In conclusion, while the allure of a better browsing experience is tempting, it's essential to approach such offers with caution. Scams, like the one perpetuated by Wikipedtoday.com, rely on deceiving users and exploiting their trust. Awareness of their tactics is the first line of defense against them.
Wikipedtoday.com removal
While adware infections are mostly not grave threats to your device's health, their effects can still be perturbing. The symptoms are all too familiar: unexpected pop-ups, disruptive ads, and a general decline in browsing quality. Such nuisances may indicate an adware infection. To reclaim your online experience, it's imperative to address and remove the root of the disturbance.
We strongly suggest starting with a comprehensive system scan using reputable anti-malware solutions such as SpyHunter 5Combo Cleaner or [3]. These tools are adept at swiftly identifying and eliminating malware, ensuring a thorough purge. Employing them ensures not only the removal of the primary malicious software but also the associated files and processes that could be lingering stealthily in your system.
However, the intricacies of modern malware mean that some browser extensions might elude these security tools. Even trusted platforms like the Chrome Web Store aren't impervious to cunning malicious actors. On occasion, malevolent extensions have managed to circumvent Google's rigorous security checks, making their way to the store.
Consequently, they might deceive countless users into downloading them before they're eventually flagged and taken down. As such, it's essential to be proactive in checking and managing your extensions. To do this, consider the following steps:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the window's top-right).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Once you've successfully purged your system of any unwanted applications, it's crucial to then address potential vulnerabilities within your browsers. PUPs (Potentially Unwanted Programs) and certain malware variants often deploy tracking tools such as cookies. These tools surreptitiously gather a range of data about users, from their browsing habits to the technical specifics of their devices.
To halt such invasive tracking, it's advisable to clear web data from your browsers. Regularly practicing this not only disrupts unwanted tracking but also helps in avoiding cache-related errors and the gradual build-up of data trackers that might slow down or compromise your browsing experience. For a hassle-free and comprehensive cleanup, consider employing FortectIntego, a dedicated PC repair and maintenance utility. However, for those who prefer a hands-on approach, a manual method is provided:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.








