Wwka ransomware (virus) - Decryption Methods Included
Wwka virus Removal Guide
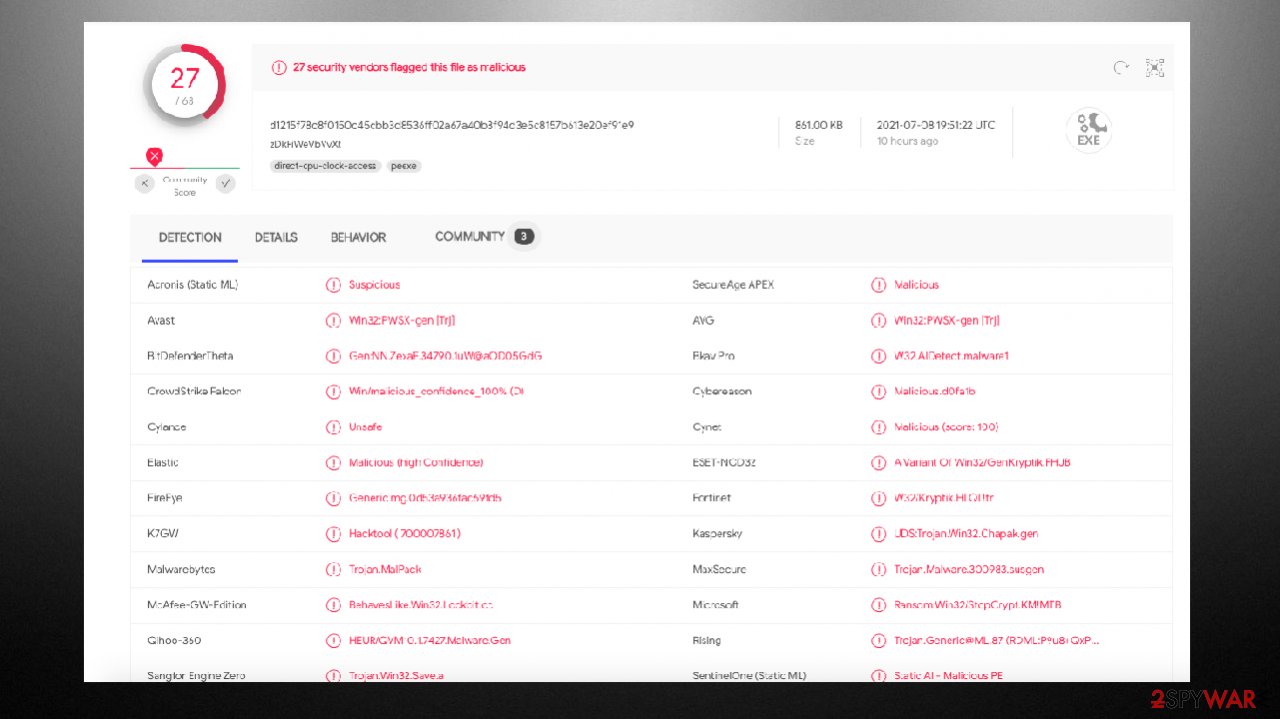
What is Wwka ransomware?
Wwka ransomware encrypts your files and demands ransom
Wwka ransomware is an infection targeting Windows OS users around the world. When it infects your computer, all personal files are encrypted with the RSA-2048 coding algorithm and are rendered useless until a specific decryption software is used to unlock them. Unfortunately, a unique key is used for each victim, which makes file recovery without acquiring it rather difficult. Luckily, since this infection belongs to the Djvu ransomware family, there is a chance that an offline key was used to lock your data, providing an opportunity for a specially-crafted, free Emsisoft decryption tool to work.
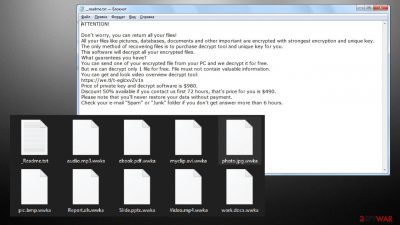
As soon as the data-locking process has transpired, users are presented with a _readme.txt pop-up message. Within the ransom note, the developers are trying to convince you that the only way to recover those files is by purchasing their decryption tool.
The attackers are demanding $980/$490 in Bitcoin. While it might be a lot for some and minuscule for others, paying the crooks should be the last resort. Instead, several alternative methods might work just fine, and we provide all of them below. But that's the final step of the process. First, we'll provide detailed instructions on removing the file-locking parasite and repairing damaged system sectors.
It's pretty easy to identify whether your device was infected with this ransomware or some other strain. First and foremost, if your personal files, such as pictures, documents, archives, databases, etc., are appended with the .wwka extension, and you should be shown a ransom note. Besides that, your machine should work just fine, although it does not mean that system files and certain Windows sectors were not affected (the underlying changes malware makes are rarely visible to end-users).
The ransom note does not really differ much from other Djvu variants – cybercriminals do not alter the body text within the file for a while now, as their goals remain the same.
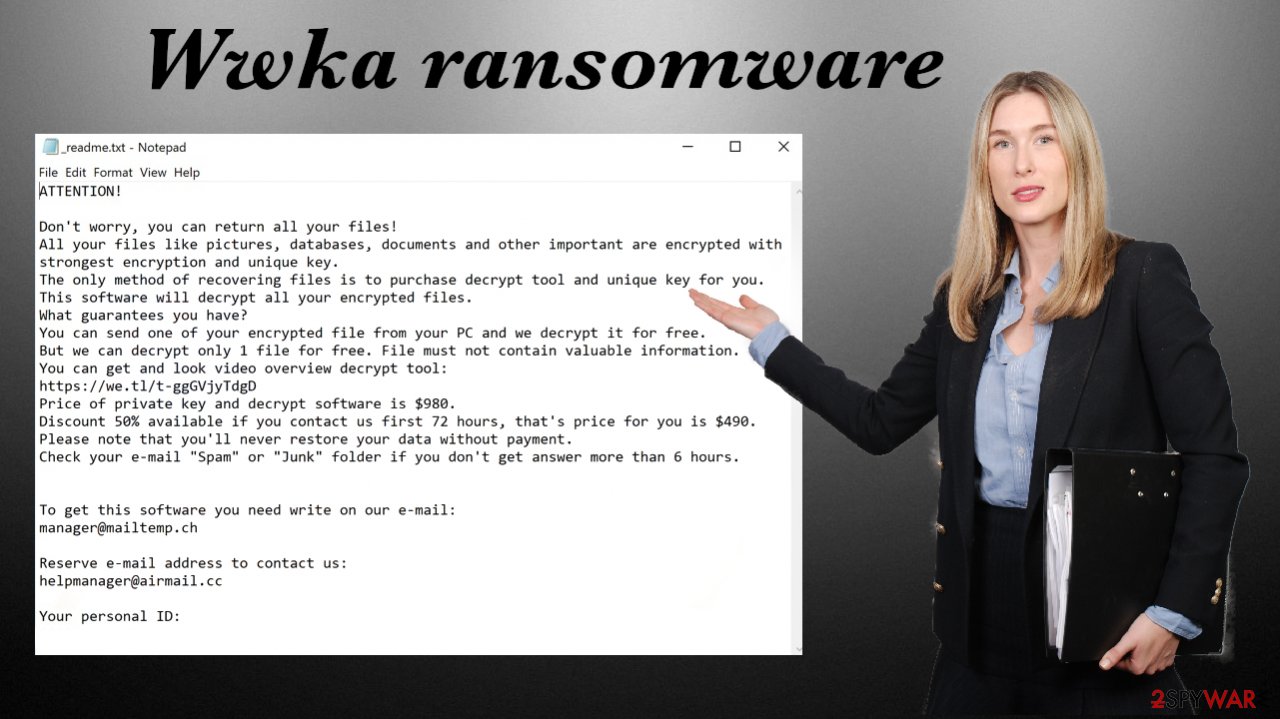
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-fhnNOAYC8Z
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
manager@mailtemp.chReserve e-mail address to contact us:
helpmanager@airmail.ccYour personal ID:
Malware's primary distribution method is via file-sharing platforms, such as torrent websites. You or someone else using your device might have downloaded a software or game crack containing the virus payload file and executed it by thinking that they will illegally unlock some type of software.
That's why we always recommend refraining from using such high-risk portals as they're crawling with various types of malware. But what's done is done. Now all that matters is how you respond to this nightmare of an incident. You could contact the criminals through the given emails (manager@mailtemp.ch, helpmanager@airmail.cc) and forward them the demanded amount with or without the offered 50% discount, but please note that criminals are criminals for a reason.
You might never receive the promised decryption software, or it might not work. Besides, by succumbing to the assailants' demands, you would only motivate them to attack more innocent people and provide funding to develop new, more devastating ransomware and more effective distribution techniques.
Besides, as we've already mentioned, there are alternative ways to recover your encrypted data. Thus there's no need to contact the criminals or pay the ransom. Instead, remove the virus with the help of the instructions provided below and try out the suggested data recovery options. Of course, if you had backups, you can skip the recovery part.
| name | Wwka ransomware |
|---|---|
| Type | Cryptovirus, file-locker |
| Family | Djvu/STOP ransomware |
| Symptoms of infection | Non-system files are inaccessible and renamed; ransom notes scattered throughout the infected machine; can't open security-related websites or launch security software |
| Ransom note | _readme.txt |
| Appended file extension | .wwka |
| Distribution | File-sharing platforms, especially most popular torrent websites |
| Data recovery | Use our suggested techniques described in detail in this article |
| Elimination | To safely and completely remove the infection from your computer, you must use a professional anti-malware software |
| System health check | Ransomware does extensive damage to system files without encrypting them. To repair them, you can use the FortectIntego PC repair tool |
Here's how to remove the virus and repair damaged Windows components
Ransomware infections are a nightmare, and they're getting more and more frequent. These viruses are spread in various ways, from infected email attachments and RDP attacks[1] to file-sharing platforms. Since we all make mistakes, reliable anti-malware software like the Malwarebytes is a must for every computer user.
A proper security tool is your frontline defense against countless computer viruses lurking on the internet. If constantly updated, such software would stop all cyber infections, from ransomware to PUPs, at the doorstep and keep you and your device safe and sound.
It can also be used to remove Wwka ransomware. Therefore we highly recommend downloading either the SpyHunter 5Combo Cleaner or the abovementioned software, updating the chosen tools virus definitions database, and performing a full system scan of the infected computer. But before proceeding to removal, copy all encrypted files from the infected machine to a USB, SSD, or another offline storage device.
Either of the suggested tools will automatically detect and isolate the ransomware along with all of its components. When the scan is complete, you will be provided with the choice to remove all of them. Please stick to the recommendations and get rid of all suspicious/malicious files/entries.
Users have reported that Wwka file virus blocked them from opening their security software. The virus does that to establish persistence. You can overcome this deception by rebooting your infected machine in Safe Mode with Networking, and here's how that's done:
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
![Reboot Reboot]()
- Select Troubleshoot.
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.
![Enable safe mode Enable safe mode]()
Once you've successfully entered the needed Windows OS mode, you can download the above-mentioned trustworthy security software and proceed with the ransomware removal. To prevent such perils in the future, refrain from using file-sharing platforms and frequently perform full system scans with the AV engine of your choice.
Once the Wwka virus is removed, you need to repair the damage caused to various system files and settings. As we've mentioned before, ransomware does extensive damage to them to establish persistence. It heavily modifies the registry, host file, and other core system directories.
These changes will result in Blue Screens of Death,[2] freezes, complete system failure, or even infection renewal if left unattended. Therefore, after you remove the file-locking parasite, it's essential to repair all of these modifications. Unfortunately, you won't be able to fix all these system issues manually.
Therefore, cybersecurity specialists[3] highly recommend entrusting this process to the patented FortectIntego PC repair tool. By downloading and performing system diagnostics with this software, it will fix the registry, broken DLLs, and other system-related irregularities that would cause system stability, performance, and other issues.
We also vouch for this software, so here's what you need to do to repair the ransomware caused damages:
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
If you didn't skip any of the aforementioned steps, you have completed the virus removal and repaired all damages caused to the system files and settings. Only now can you safely retrieve your data from backups if such were kept. If not, proceed to the next chapter, where we present the best data recovery options that we've compiled during our 20 years of helping people get out of sticky situations without losing a dime.
Best options to recover Djvu ransomware encrypted files
In this part of the article, we present the two best options to recover .wwka files. Please try the second one only if the first one doesn't work. Not let's begin with the free decryptor from Emsisoft. This company dedicates its time and money to help Djvu family ransomware victims to get their files back without the intervention of the criminals.
The company is doing that because the file-lockers from this lineage account for more than half of all ransomware infections worldwide. It's worth mentioning that the free decryption software won't work for everyone. It will help victims if the ransomware during the infection had problems connecting to the remote assailants' server and encrypted their data with an Offline ID.
No matter what ID was used to lock up your precious files, you have to try this tool out as it's free and have nothing to lose. Please follow the guidelines below and keep your fingers crossed:
- Download the app from the official Emsisoft website.
![Wwka ransomware Wwka ransomware]()
- After pressing the Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe, should show up – click it.
- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
![Wwka ransomware Wwka ransomware]()
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.
![Wwka ransomware Wwka ransomware]()
- Press Decrypt.
![Wwka ransomware Wwka ransomware]()
Suppose the free software from Emsisoft was able to unlock .wwka files, a prompt with “Decrypted!” will be shown. That's the best-case scenario, as now you can freely use your data again. Please learn from this incident and always use the recommended security software to keep your devices and you safe from various malware.
When the “Error: Unable to decrypt the file with ID:” appears, it means that no one has yet sent needed copies to the company, so it hasn't cracked the code of this particular ransomware. Arm yourself with patience, and try the free decryptor within a few days.
The worst outcome is when the “This ID appears to be an online ID, decryption is impossible” message appears. That means that, unfortunately, the Emsisoft decryptor is not able to recover encrypted files as an Online ID was used when your files were being encrypted. But don't lose hope, as all is not lost yet.
Our second recommended software could do the trick. But use it only if the last message from the Emsisoft decryptor was delivered. Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
But since it helped numerous ransomware victims, maybe it will also prove useful in your case. Follow this step-by-step guide:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
We truly hope that all of these instructions helped you to remove the Wwka file virus, fix your damaged system, and most importantly, recover the encrypted files. The particular ransomware is one of the newer variants in this family, so decryption options are limited. However, you can store some of the virus-affected pieces and restore them later when the additional decryption tool gets released.
As of now, the online ID forming method keeps those files unrecoverable since there is no other option to obtain the needed key without paying the ransom. But that is not the solution. Especially, when it comes to this well-known family of cryptocurrency extortionists. Make sure to remove the threat properly using SpyHunter 5Combo Cleaner or Malwarebytes before getting any files recovered or replaced with safe versions from backups. Do not risk getting your files encrypted again.
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Kapua Iao. What Is a Remote Desktop Protocol Attack?. Paubox. Security blog.
- ^ Chris Hoffman. Everything You Need To Know About the Blue Screen of Death. Howtogeek. Online technology magazine.
- ^ Dieviren. Dieviren. Spyware news and security.