Yandex ransomware (virus) - Recovery Instructions Included
Yandex virus Removal Guide
What is Yandex ransomware?
Yandex ransomware is a malicious program designed to extort money from innocent users
There is plenty of malware created, and the pace is increasing rapidly. Ransomware is particularly active – more and more attacks are conducted against regular computer users and corporations annually. The malicious activity skyrocketed after the pandemic began – a time when more users need to work from home and spend more time at the computer. This easily explains why so many new ransomware strains are showing up on a regular basis, and Yandex virus is one of them.
As soon as malware manages to breach a Windows computer or a network, it imports its own malicious files, infecting the device. The most critical change is that one performed to various non-system data, including pictures, videos, documents, and similar personal files, which get encrypted with a military-grade encryption algorithm. Likewise, such files receive a .yandex extension and can no longer be accessed or modified.
Despite popular belief, the data does not get corrupted by rather locked behind a complex, uniquely generated password. It is impossible to guess it – it consists of a long string of alphanumeric characters, so even sophisticated computing calculations would not be enough to solve it. This is why cybercriminals win here – they have the required key that could unlock all files, although they are not willing to provide it for free.
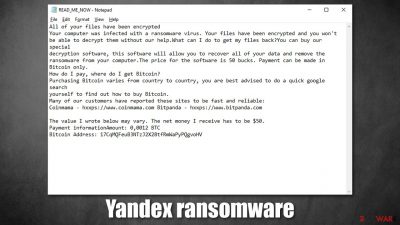
According to the ransom note READ_ME_NOW.txt (which is placed into each of the folders where the encrypted data is located), hackers demand $50 ransom, to be paid in Bitcoin cryptocurrency. It is also mentioned that this sum might vary, depending on the victim's location. The money should be transferred to 17CqMQFeuB3NTzJ2X28tfRmWaPyPQgvoHV, although there is no contact information provided, which is just one of the reasons not to pay to cybercriminals.
| Name | Yandex virus |
|---|---|
| Type | Ransomware, data locking malware, cryptovirus |
| File extension | .yandex, appended at the end of each file name |
| Ransom note | READ_ME_NOW.txt |
| Contact | None provided |
| Ransom size | $50/0,0012 BTC (might vary) |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Malware removal | Manual virus removal is not recommended, as it might be difficult for regular users. Instead, using security software is advised |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
How does ransomware spread?
Most users who get infected with ransomware have no idea what it actually is or how it works. In fact, many victims have not only never encountered it before but also never even heard the name of malware before. Unfortunately, the experience of having your PC infected with one of such parasites is anything but pleasant.
Ransomware is a file-locking type of computer infection that usually targets Windows systems, although there are variants that previously infected macOS, Android, and Linux. Thus, if you use Windows operating system (especially if it's an older version such as 7 or XP),[1] you are more likely to get infected.
With adequate security measures and proper file backups, you can be completely sure that you will never have to suffer from the devastating consequences of a ransomware attack. Security experts[2] advise being extremely vigilant when performing tasks when using a computer. Here are a few tips that would be useful to avoid being infected in the future:
- Always use powerful anti-malware software like SpyHunter 5Combo Cleaner or Malwarebytes, and never ignore warnings or automatically assume it is a false positive;[3]
- Keep all your software updated and set Windows to install updates automatically;
- Always treat email attachments with caution, especially those that include MS Office attachments (don't let those documents run macros on your system!). Some emails might even be seemingly sent from your own email or from somebody's that you know;
- Use complex passwords for all your accounts;
- Never download software cracks, pirated program installers, and similar insecure executables;
- Be more careful when browsing the web and clicking links.
Yandex virus in detail
Most users don't realize that they let ransomware into their systems, and what they see is only the aftermath – destroyed files. This can demoralize many, but being devastated will not result in any positive outcomes. As we explained above, you should take all the necessary precautionary measures to avoid ransomware attacks.
As soon Yandex ransomware breaches the computer, it changes the way it operates. It modifies the Windows registry, deletes Shadow Volume Copies, drops multiple malicious files, and performs other tasks. Only after that malware starts the file encryption process, which usually lasts a short period of time (depending on the size of data located on the PC).
After completion, victims immediately can see that their desktop wallpaper is altered, it says:
YOU HAVE BEEN HACKED
This is done to make sure that victims notice what has happened; a wallpaper is just a first warning, as soon the ransom note READ_ME_NOW.txt also shows up, which reads:
All of your files have been encrypted
Your computer was infected with a ransomware virus. Your files have been encrypted and you won't
be able to decrypt them without our help.What can I do to get my files back?You can buy our special
decryption software, this software will allow you to recover all of your data and remove the
ransomware from your computer.The price for the software is 50 bucks. Payment can be made in Bitcoin only.
How do I pay, where do I get Bitcoin?
Purchasing Bitcoin varies from country to country, you are best advised to do a quick google search
yourself to find out how to buy Bitcoin.
Many of our customers have reported these sites to be fast and reliable:
Coinmama – hxxps://www.coinmama.com Bitpanda – hxxps://www.bitpanda.comThe value I wrote below may vary. The net money I receive has to be $50.
Payment informationAmount: 0,0012 BTC
Bitcoin Address: 17CqMQFeuB3NTzJ2X28tfRmWaPyPQgvoHV
It is not worth paying the attackers, even if the sum of $50 doesn't seem like a lot to you. Keep in mind that there is no contact information provided, so you are likely to never hear from them again, even after you transfer the requested bitcoin. Instead, proceed with the steps below to remove malware and recover data in alternative ways.
1. Remove Yandex ransomware
There are plenty of ransomware-type infections which self-destroy after they are finished with data encryption. However, this is not the case for all malware, and it well might be that Yandex ransomware will continue running in the background in order to lock the incoming data. Besides, it might drop several modules that could be designed for some other malicious activities, such as data gathering or further malware delivery.
Therefore, the first step you should do after being infected with ransomware is to remove it with powerful security software. You can perform a full system scan with an updated anti-virus application and it should delete all the related files and other items automatically. There are plenty of tools that recognize
In some cases, ransomware might interfere with security software operations in one way or another (for example, it can immediately shut it down). Accessing Safe Mode with Networking can bypass this issue:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
Once your computer reboots, your desktop background should be black, with “Safe Mode” markings in all four corners of the screen. Launch SpyHunter 5Combo Cleaner or another powerful security software and perform a full system scan. Your machine should be clean after that, and you can then restart it to go back to normal more to proceed with the next step.
2. Use alternative ways to recover .yandex files
Having your files encrypted by ransomware can be particularly devastating, especially if data consists of important work documents or schoolwork. As already mentioned, paying criminals is not recommended – these people can simply not be trusted. They might never send you the required key, especially when there are no contact details provided (they might not know who you are – usually crooks provide a personal ID they can identify victims by).
Thus, you should instead rely on other methods. There is no guarantee they will work for you, but you should definitely try it.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Yandex ransomware Yandex ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Security researchers are constantly working on battling malicious actors and helping victims by creating free decryptors. Unfortunately, such a tool is not yet developed for this malware family. There are several places where you could look for decryptors in the future:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors
3. Repair damaged system files
Malware, such as ransomware, can negatively impact Windows system files, damaging them during the infection period. New ransomware strains are more prone to bugs due to malware creators' inexperience, so it can mess things up really quickly. Unfortunately, security software is not capable of fixing damaged system components, which might later result in system crashes, errors, and other issues.
If you are experiencing similar problems after Yandex ransomware removal, you should proceed with the following solution to repair damaged system files:
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
By employing this tool, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Zack Whittaker. Despite security risks, older Windows versions plague thousands of businesses. ZDNet. Technology News, Analysis, Comments.
- ^ Dieviren. Dieviren. Cybersecurity website.
- ^ Cybersecurity 101: What You Need To Know About False Positives and False Negatives. Infocyte. Managed Detection and Response.












