“You need to update your browser to view the content” scam (fake) - Free Instructions
“You need to update your browser to view the content” scam Removal Guide
What is “You need to update your browser to view the content” scam?
“You need to update your browser to view the content” is a fake message that tells people to allegedly update their Chrome browsers
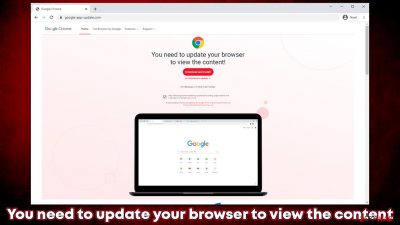
“You need to update your browser to view the content” is a scam that one might encounter accidentally on Google Chrome or any other browser. According to the message, visitors need to download and install an update for the app in order to view the content. It is not clear what type of content is there to view, and that should be the first red flag when dealing with this scam.
The message can come from various fake websites that impersonate the official Chrome page. The well-known logo, formatting, font, and other attributes are used in order to make people believe that the message actually comes from Google. In fact, if not paying close attention, it is easy to get confused and download the fake update.
It goes without saying that “You need to update your browser to view the content” is fake and should be avoided at all costs. If the promoted “update” is downloaded and installed, users could get infected with all sorts of malware, including Trojans, backdoors, ransomware, or keyloggers.
If you have encountered the scam, please take your time to check more about it its operation below and then employ the instructions in order to ensure that there is no adware or other malicious software running in the background of your system (potentially unwanted programs are known to cause users to encounter scams and phishing[1] material more often).
| Name | You need to update your browser to view the content |
|---|---|
| Type | Scam, phishing, redirect, adware |
| Distribution | Malicious link clicks, adware redirects |
| Symptoms | Redirects to suspicious websites that accommodate commercial or scam content; fake messages offer to download malicious software; ads plague every visited website; unknown extension or program installed on the system |
| risks | Installation of other potentially unwanted software or malware, personal information disclosure to cybercriminals, financial losses due to scams, etc. |
| removal | You should not interact with the contents shown by a scam website and instead, check your system for adware or malware infections with SpyHunter 5Combo Cleaner security software |
| Additional tips | Cleaning web browsers is one of the secondary things you should do after PUP/malware removal to secure your privacy. You can use FortectIntego to do it quicker and more effectively |
How scammers trick users into downloading malicious software
There are almost two billion websites[2] on the world wide web, so it is not surprising that not all of them are there to be informative or useful. In fact, there are plenty of crooks who are willing to make use of the anonymity that the internet provides and do malicious deeds for personal benefits – usually, it's the financial benefits that are the reason for all sorts of nasty online.
“You need to update your browser to view the content” is a very typical scam in terms of how it operates and what its goal is. It all starts with creating a website online that hosts the fake message (hxxps:google-app-update.com is one of the websites that is used by cybercriminals), and then means such as adware or insecure advertisement networks are used to spread it around the web.
As soon as users are rerouted to the malicious page, they are immediately shown the message which asks users to download and install the browser update. The site itself is a mere copy of the official Chrome download page, although it does not provide the same functionality – the whole contents are simply used as an image-link and would initiate a download of an ISO file as soon as a mouse-click is made.
The file, under the name of Updt.iso, would be downloaded automatically. Once uploaded to Virus Total, the results were quite alarming, as it was recognized and detected under the following names:
- Win32:DropperX-gen [Drp]
- Trojan.TR/Dropper.MSIL.Gen
- HEUR:Trojan-Downloader.MSIL.PsDownload.gen
- A Variant Of MSIL/TrojanDownloader.Agent.JW
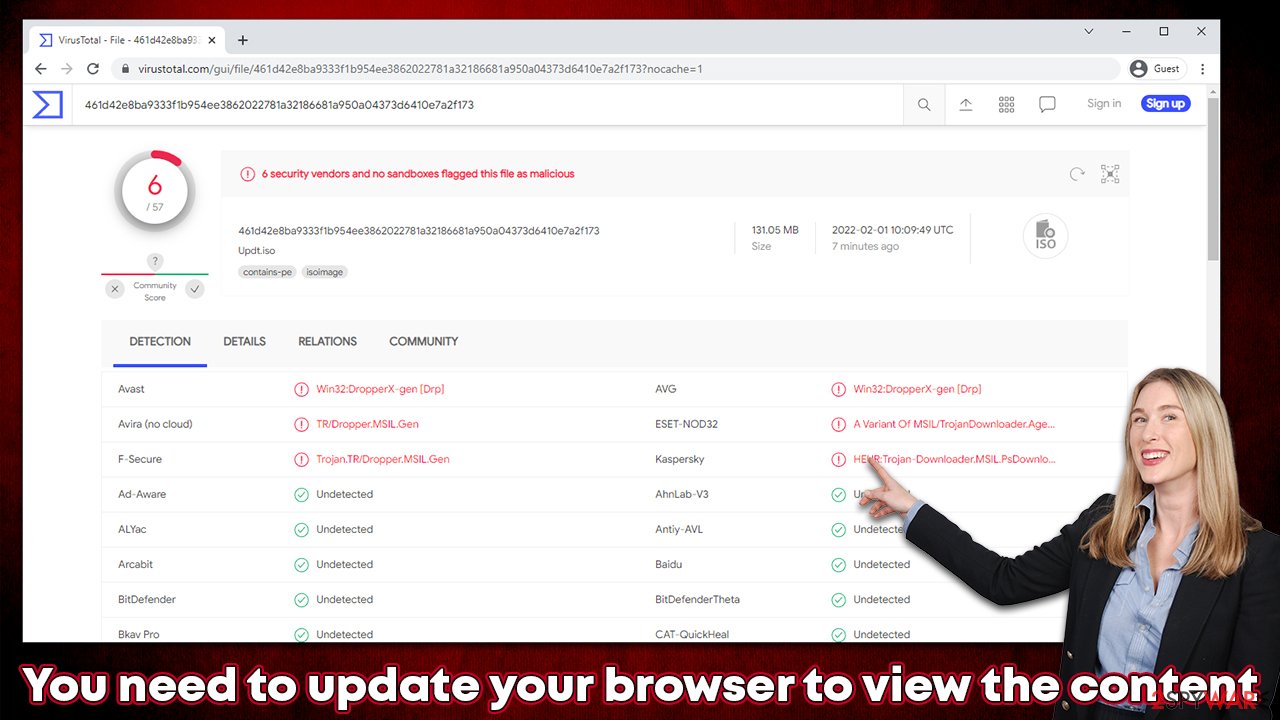
According to these names, it seems to be a typical dropper Trojan which, once installed, could automatically download additional malicious payloads. Please never mount the file, as you could infect your device with malware. The detection rate is relatively low because of the file format – once extracted, it would be detected by most security tools.
Recovery
It is important to mention that just because you have encountered a scam website, it does not automatically mean that your computer is infected with something. However, there are a few things that you should take into consideration:
- Whether you interacted with the promoted links in any way (clicked on links, downloaded and installed software, entered your passwords or other personal information, etc.)
- If you encounter online scams, malicious ads, and similar suspicious content while browsing the web, there is likely to be a potentially unwanted or malicious program involved.
Thus, below we provide steps that should make sure that your system is infection-free. Some potentially unwanted applications might not be detected by the security software (although this is rare), so we provide manual steps as well.
1. Uninstall PUPs
There are two places where potentially unwanted applications could reside: they could be installed on the system level as a program or as an extension within the web browsers. Therefore, it is worth checking both of these places – let's start with apps installed on the system.
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
On a Mac, removing adware might require a few more steps besides moving the unwanted app into Trash. Adware is known for inserting additional files that might cause the infection to resurface, so we recommend removing them too.
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
Next, you should definitely check what extensions you have on your system installed. You can find them by clicking the “Extensions” button on the right side of the URL bar or by accessing browser settings as follows:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
2. Scan with anti-malware
After you find unwanted programs installed on your browser or system and remove them, you should also ensure that more stealthy malware is also removed. Cybercriminals use all sorts of obfuscation[3] techniques in order to increase the persistence of malicious programs; if not removed in time, there could be other malware downloaded and installed on the system in the background.
3. Check your browsers
The final step is to make sure that cookies and other tracking items are eliminated from your browser. You can either follow the steps below or employ FortectIntego a PC maintenance tool that could also fix any system damage related to malware activities.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Note: if you are using other browsers, check the bottom section of this post.
How you end up on malicious websites
Many users are quite oblivious to the fact that shady websites are dangerous to visit. While it is indeed true that the overall security of most websites has been going up over the years, there are still plenty of places for malicious activities to take place. To be more precise, pirated program distributors, torrents sites, and similar places are some of the most dangerous ones on the internet, as users themselves download malware executables while believing that it is a pirated app.
Once extracted, such files immediately begin the infection process, and, in most cases, everything happens stealthily without users knowing anything about it. That is one of the most common ways of getting yourself infected with ransomware or similar devastating malware.
Another danger about such sites is the redirect tendencies. High-risk websites are loaded with fake Download buttons and booby-trapped links, which, once clicked, might take users to the “You need to update your browser to view the content” or similar scam websites. To conclude, stay away from shady websites altogether, as it might end badly otherwise.
Another tip is to always download software from official sources; third-party freeware distributors commonly bundle software, which results in users installing optional components without realizing it. Always pick Advanced/Custom settings instead of Recommended ones and watch out for pre-ticked checkboxes, fine print, and similar things crooks might abuse in order to make people install additional apps without their permission.
Most importantly, you should ensure that your device is protected with powerful anti-malware such as SpyHunter 5Combo Cleaner or Malwarebytes – not only can security software find and remove malware but also prevent incoming attacks.
Getting rid of “You need to update your browser to view the content” scam. Follow these steps
Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

How to prevent from getting adware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Phishing attacks. Imperva. Application and data security.
- ^ How Many Websites Are There?. WebsiteSetup. Free resource for helping beginners to build, manage and grow their websites.
- ^ Dan Virgillito. What is Malware Obfuscation?. Security Boulevard. Security Bloggers Network.




















