Yoursecuritydatabase.com ads (Free Instructions)
Yoursecuritydatabase.com ads Removal Guide
What is Yoursecuritydatabase.com ads?
Yoursecuritydatabase.com shows fake pop-ups that resemble security software scans
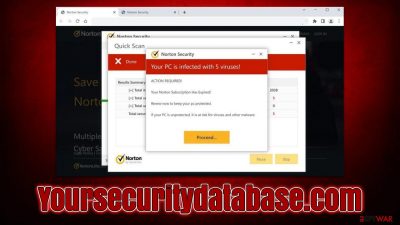
Yoursecuritydatabase.com is a malicious website designed to trick users into doing something they otherwise wouldn't. Scammers create such websites to catch people who are less aware of online fraud, and the financial profits from such activity can be significant. The more users fall for the scam, the more money crooks earn.
Users access scam websites accidentally – usually after clicking a link on a malicious site or after they get redirected by an automatic script. While more rarely, users may also be infected with adware that causes them to encounter various misleading and fake content, along with intrusive ads, online.
Once on the page, visitors are shown fake virus alerts that allegedly come from a well-known security software maker Norton. People are being told that their machines are infected, and if they want to get rid of the viruses, they need to purchase a security software license, which may or may not be fake.
We recommend not interacting with Yoursecuritydatabase.com ads, as you might end up exposing your personal data to unknown parties, installing suspicious software on your device, or losing money on an application you never needed in the first place. If you want to get rid of unwanted redirects or find out what to do upon encountering a scam message, we will explain everything in the next paragraphs.
| Name | Yoursecuritydatabase.com |
| Type | Scam, phishing, redirect, adware |
| Operation | Shows a message which claims that the antivirus subscription has expired and needs to be updated; it also asks to enable notifications |
| Distribution | Redirects from other malicious websites, adware |
| Risks | Installation of PUPs or malware, sensitive information disclosure, financial losses |
| Removal | You should not interact with the contents shown by a scam website, check your system for adware or malware infections with SpyHunter 5Combo Cleaner security software |
| Other tips | Third parties can employ cookies to continue tracking your online activities, so we recommended clearing browser caches and other leftover PUP files with FortectIntego |
How did you end up on a scam site?
Torrents, adult-oriented, YouTube video converters, illegal video streaming, and similar websites are often one of the primary methods for how users encounter phishing and other malicious material online. These places are often poorly regulated since they tend to deal with content that is considered inappropriate or even illegal.
This makes a perfect place for cybercriminals to spread malicious files that sometimes would install ransomware[1] or similar hazardous malware. Besides, users can also be exposed to malicious ads and fake buttons that would redirect them to various scam sites, including Yoursecuritydatabase.com.
In other cases, potentially unwanted or malicious software could be the cause of scam encounters. This is especially true if you also notice ads on most websites that don't belong there. Since adware and malware are distributed using deceptive methods such as bundling,[2] you may not be aware it is installed on your device, so it is vital to check it.

Remove Yoursecuritydatabase.com ads
To stop redirects to suspicious and fake websites, we recommend checking the system for infections. This can be any type of software installed on the system as a program or an extension installed on the web browser. The former is generally much more dangerous, as its operational capabilities are more widespread than those of a browser extension.
Most malicious software can be removed automatically, so if you don't want to bother with manual steps, you should perform a full system scan with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful anti-malware. Besides, some malware types are almost impossible to delete manually, so even if you choose to perform PUP removal yourself, you should still ensure that a full system scan with security software is performed.
To remove programs installed on the system, go to Programs and Features in Windows and Applications section in macOS.
Windows
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
While moving apps into Trash is how you delete most normal applications, adware tends to create additional files for persistence. Thus, you should look for .plist and other files that could be related to the virus. If you are not sure, skip this step entirely.
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
To get rid of add-ons from the browsers, simply click the “Extensions” button next to the Settings menu, click More actions, and select Remove. After this, we recommend using FortectIntego PC repair and maintenance utility that can fix any damage done by adware or other malware, and also take care of your privacy by cleaning your browser caches, including cookies[3] and other trackers, from the device.
Take care of push notifications [if applicable]
Upon website entry, Yoursecuritydatabase.com asks whether you would like to enable push notifications from the site. It is another way for crooks to benefit from advertising revenue, as those who accept this offer would be later spammed with inappropriate or even dangerous ads, which would be shown directly on users' desktops at random times.
Do not click on the promoted links, as you may end up on misleading or even malicious websites, where you could be told that your system has been infected (similarly to the scam promoted by Yoursecuritydatabase.com) and that you need to download software or call the alleged tech support. You could also encounter get-rich-quick scams, survey scams, or even malware-laden download links.
Instead, you can quickly and easily remove push notifications from this website – all you need to do is access the site settings of your browser. Proceed with the instructions we provide below.
Google Chrome
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
MS Edge (Chromium):
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
Safari:
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Ransomware. Imperva. Application and data protection.
- ^ Bundled software. Computer Hope. Free computer help.
- ^ What are cookies? | Cookies definition. Cloudflare. The Web Performance & Security Company.







