Yourzev24.com ads (fake) - Free Guide
Yourzev24.com ads Removal Guide
What is Yourzev24.com ads?
Yourzev24.com ads can bring misleading messages to your desktop

Yourzev24.com is a deceptive website that primarily targets users into subscribing to its push notifications. When users inadvertently subscribe, they may experience unexpected pop-ups on their desktops, irrespective of their ongoing tasks.
These intrusive pop-ups often carry misleading messages and hyperlinks, which can range from false security warnings to deceptive offers for complimentary software. In certain situations, users might be falsely informed that their security software is outdated or that threats have been detected on their devices, leading them to unintentionally download counterfeit software or reveal private details.
In this article, we will delve deeper into the nature of push notifications stemming from Yourzev24.com and offer guidance on how to counteract them. While push notifications are a genuine and valuable feature on numerous websites and applications, they can unfortunately be exploited by malevolent entities to distribute undesirable or malicious content. Gaining a thorough understanding of how push notifications function and proactively blocking unwarranted ones is crucial in safeguarding oneself from such scams.
| Name | Yourzev24.com |
| Type | Push notifications, pop-ups, ads, scam |
| Distribution | Intrusive pop-ups can start showing up at some point after the “Allow” button is pressed within the notification prompt |
| Symptoms | You may start seeing intrusive pop-ups on your desktop – clicking these may lead to insecure or even malicious websites |
| Risks | If you click on links provided by the website, you might end up infecting your system with malware/PUPs, disclosing your personal information to cybercriminals, or losing money for useless services |
| Removal | You can stop unwanted notifications by accessing web browser settings. If you suspect adware infection, you should use SpyHunter 5Combo Cleaner security software to get rid of it |
| Other tips | To make sure that third parties can no longer track your online activities, we suggest clearing browser caches and other leftover PUP files with FortectIntego |
Difference between push notifications and pop-up ads
Pop-up ads are a specific form of online advertisement that materialize as a window or box within a webpage. Their primary function is to seize the attention of web visitors and persuade them to engage in certain actions, whether that's purchasing a product, subscribing to a newsletter, or downloading software. While pop-up ads can significantly boost conversions, making them profitable for advertisers, they can also be perceived as disruptive and bothersome by website visitors.
In contrast, the ads from Yourzev24.com might initially appear similar to pop-up ads, but they function differently. The key distinction is that they utilize the browser's push notification system.
What this means is that, whereas pop-up ads might appear only when navigating specific websites or when triggered by certain undesired software on a device, push notifications operate at the system's foundational level. They can manifest anytime a request is made by the website – in this scenario, Yourzev24.com. This is why users might encounter these notifications regardless of the websites they browse, or even if they aren't actively using a web browser.
Given that push notifications are browser-centric, one might assume that entirely closing the browser would halt the notifications. However, this is a temporary solution at best. Upon reopening the browser, the ads re-emerge. Furthermore, since these ads could potentially redirect users to harmful sites, it's advisable to avoid any engagement with them. To effectively mitigate this issue, please refer to the instructions provided later in this guide.
The fake messages used by scammers
Push notifications are a standard and authentic feature many websites use to transmit pertinent information directly to users. Regrettably, unscrupulous individuals have recognized this advantage and have contrived methods to persuade users to subscribe to their notifications. Their objective is often to deliver ads or sponsored content, a strategy that results in consistent advertising revenue. As such, it's imperative for users to exercise caution when confronted with such prompts.
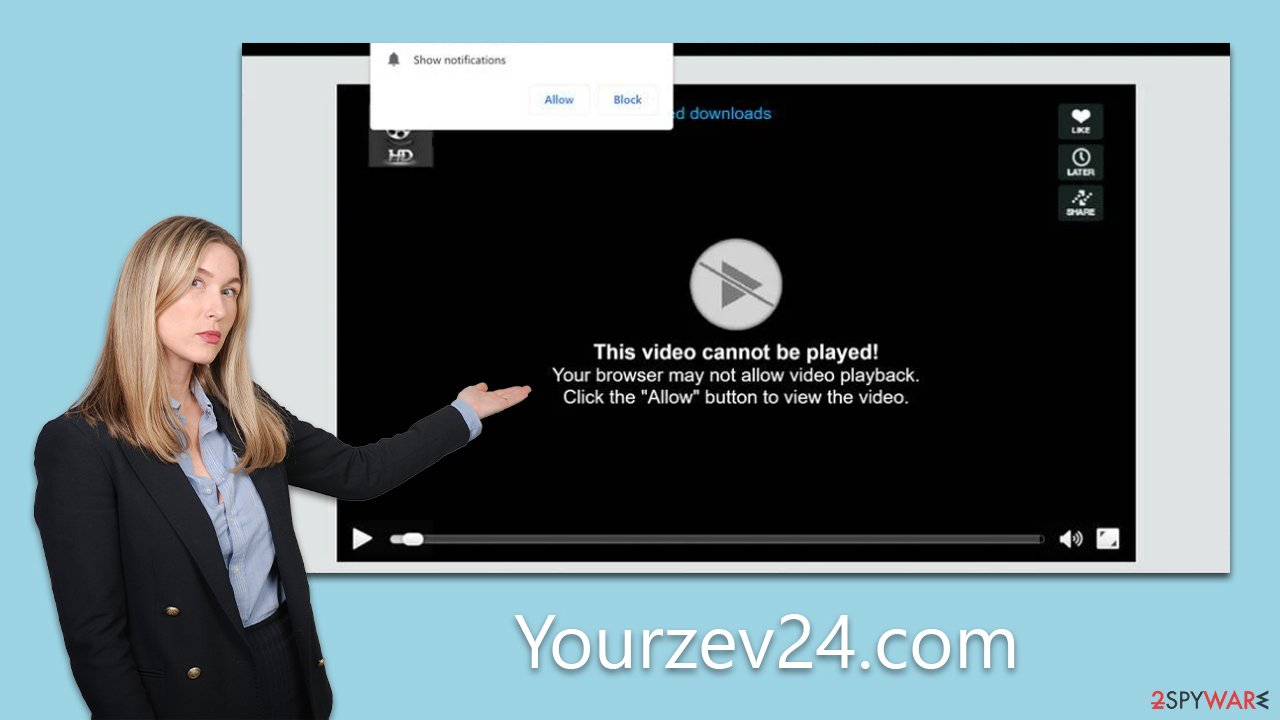
Scammers employ various tactics to lure users into subscribing to these notifications. One common technique is to mislead users by camouflaging the push notification request as a different functionality. An example includes manipulating users into thinking they're completing a routine robot verification process to progress on a site. Given that many are familiar with captchas, they might inadvertently believe this assertion and click the “Allow” button. Other deceptive messages to be wary of include:
- Click Allow to confirm that you are not a robot
- Click “Allow” to win the prize and get it in our shop!
- Can't play this video! Perhaps your browser doesn't allow video playback. Please click the Allow button to watch the video
- Your file is ready to download – press Allow to continue.
- If you are 18+, click Allow
Although deceitful techniques are rampant online, familiarity with these tactics can aid in their swift identification. Legitimate websites do not withhold their content contingent upon push notification approval, irrespective of any statements to the contrary on the page.
By pressing the “Allow” button, you grant the website unhindered access to send information directly to your device. Always remain alert, and bear in mind that reputable websites do not resort to such manipulative practices.
Check your system for infections
Adware is software specifically designed to display unsolicited advertisements on a user's device, commonly within the browser. Though some adware may merely serve ads with the intention of revenue generation, others can be particularly invasive or even have malicious intent. The repercussions of adware range from an impaired browsing experience to system slowdowns and potential security breaches.
For a thorough and efficient removal of malicious software, adhere to the steps below:
- Employ Anti-malware tools: For a comprehensive sweep of threats, it's advised to use potent anti-malware solutions such as SpyHunter 5Combo Cleaner or Malwarebytes. These utilities are designed to detect and obliterate threats efficiently. Before initiating the scan, ensure that your software's threat database is current to maximize detection rates.
- Clean your browsers: After ridding your system of potential threats, it's essential to clear out your web browsers. This step ensures the removal of any lingering files that might facilitate the recurrence of ads or allow data monitoring by third parties.
- Utilize a PC repair tool: Consider using a dedicated PC repair application like FortectIntego. Such tools not only help in eliminating traces of malware-induced harm but also tackle other prevalent system issues. By addressing these issues, the tool can stave off critical system failures, such as the dreaded Blue Screen of Death, and rectify any registry inconsistencies.
By following these steps, users can ensure their systems remain clean, optimized, and free from the nuisances and potential dangers of adware and related threats.
Get rid of unwanted push notifications
Even if you've inadvertently allowed notifications from a suspicious website, there's no need to panic. Disabling such activity is straightforward through your browser settings. It's crucial, however, to avoid clicking on links from these unreliable sources. Engaging with them might expose you to risks like malware attacks, data compromises, or potential financial fraud.
Google Chrome (desktop)
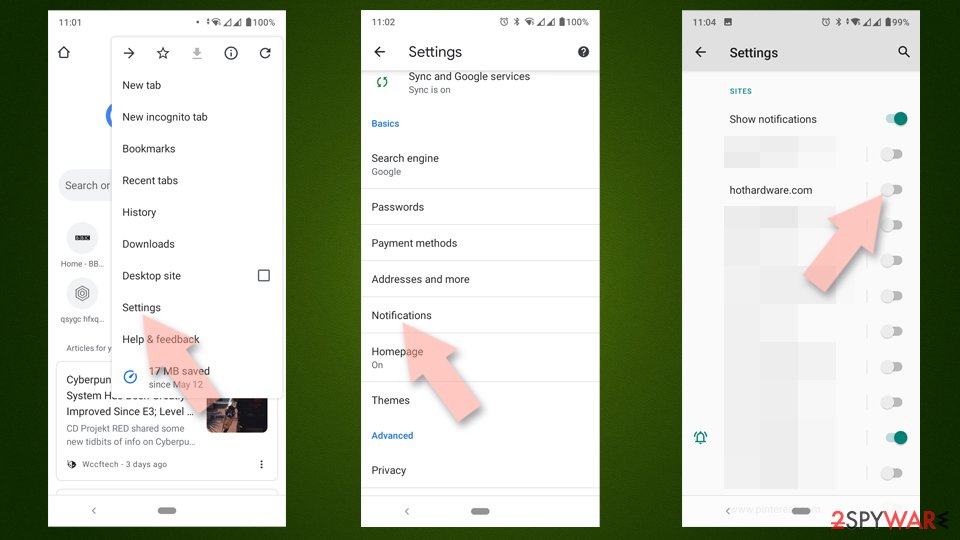
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Google Chrome (Android)
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to the Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).
![Stop notifications on Chrome Android Stop notifications on Chrome Android]()
Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
Internet Explorer
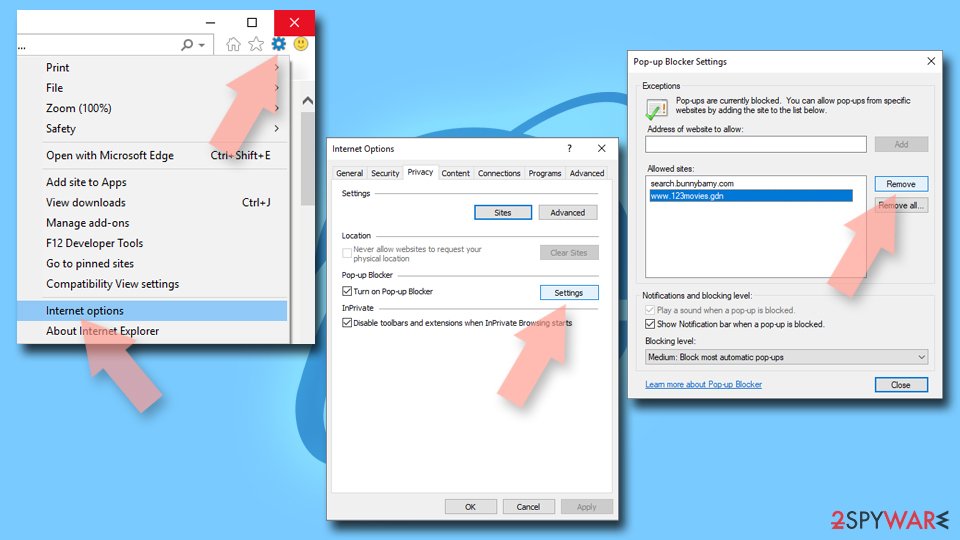
- Open Internet Explorer, and click on the Gear icon at the top-right of the window.
- Select Internet options and go to the Privacy tab.
- In the Pop-up Blocker section, click on Settings.
![Stop notifications on Internet Explorer Stop notifications on Internet Explorer]()
- Locate the web address in question under Allowed sites and pick Remove.
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.