Onion ransomware (Removal Guide) - updated Apr 2017
Onion virus Removal Guide
What is Onion ransomware?
Onion ransomware developers keep releasing new virus versions
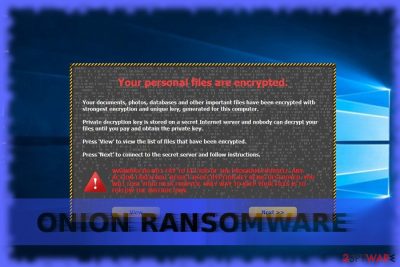
Onion virus belongs to the group of file-encrypting viruses called ransomware [1] which encode files and present 72-hour elapsing time clock to make the payment. It presents its unique email address – ttk@ruggedinbox.com for the victims to contact in case they wish to get back the access to their encrypted files.
The infection has been affiliated with infamous CryptoLocker and Dharma ransomware ransomware families [2] which suggests this parasite is not just a random PC threat, but a potentially destructive virus which you must banish from your PC as soon as possible. Luckily, this article is dedicated to helping people remove Onion from their computers, so you can start the elimination process immediately. You will find useful suggestions on how to do it safely at the end of the article.
The malware targets PDF, XLS, PPT, DOCT, TXT, JPEG, JPEG, and JS file types and encodes them with RSA-21024 algorithm. After successful data encryption, the user finds MW_ IN FILES.txt or KK_ IN YOUR DOCUMENTS.txt ransom files in every folder. They instruct how to access To2Web network, purchase 3 bitcoins (3754.12 USD) and transfer them to the given bitcoin address.
Once the payment is made, the user is provided with a unique code and has to send it to indicated email address. According to the ransom note, victims should obtain the decryption key. However, there are few reports about the returned data.
If you get tempted to download Onion Decrypter, you might inflict more severe changes to the computer. Even if the decryption software decodes the files, it may leave corrupted files on the system which, later on, “detonate” themselves and facilitate Onion hijack. It's not recommended to pay the ransom as you only encourage hackers to continue their misdeeds. There are no guarantees that they will play fairly.
Recently, discussions flared up again as one after the other new derivative versions of the malware including OnyonLock, Gebdp3k7bolalnd4.onion, help@onyon.info started to emerge on the web. These viruses were quite independent, though. For instance, .onion file extension virus version which showed in 2014, drew experts attention for its tendency to disguise its Command and Control server with the help of Tor network[3]. At the time, such feature was quite unusual.
Within time, the virus subsided. However, not for long. it has been spotted again spreading in the new form. However, the latter improved version is not fully analyzed, which prevents from creating an effective decrypter. Nonetheless, we do not recommend you to nurture hopes on data-recovery as there are few chances that the hackers will return the files. Therefore, it is better to focus on Onion removal. One of the solutions is to rely on FortectIntego or Malwarebytes.
Onion virus versions:
.onion file extension virus. Is the latest variant of Onion ransomware. It spreads around the web similarly to its predecessors (via spam mail, exploit kits, malicious javascripts and various phishing schemes). Once on the computer, the virus starts scanning it for predetermined types of files and encrypts them using AES ciphering key. Filenames of the affected files will have .onion file extensions appended to their file names. Extensions of the affected files can also feature an email address, typically its the felix_dies@aol.com.
In the last stage of the hijack, the ransomware drops a .txt, .hta, .jpg or similar files on the computer. These are the ransom notes which explain how to the victims can recover their files. In particular, the victims are instructed to contact the criminals via email address features in the file extensions.
OnyonLock virus. This is yet another malicious parasite belonging to the Onion virus family. When it makes its way on the computer, this virus targets specific types of files, enciphers their contents using strong encryption algorithm and appends them with .onyon exensions. It drops a note called !#_DECRYPT_#!.inf on the victim's computer, once the encryption process is finished. The note is meant to inform the victims of the ransomware attack about what happened to their computers and how they can step out of the unfavourable situation.
The victims of this ransomware are urged to contact the criminals as soon as possible, as the criminals promise to lower the data decryption price for those who reach out to them quicker. Decrypter@onyon.su and tk.btcw@protonmail.ch email addresses are typically associated with the virus.
Gebdp3k7bolalnd4.onion virus. The virus is a relatively new Onion ransomware follow-up which is also known by the name of Cry128 ransomware. Following the footsteps of its predecessors, this parasite appends files with different extensions to indicate that they have been encrypted.
We can find versions adding .onion._, .onion.to._ ext. Js, and gebdp3k7bolalnd4.onion._, which also has been used when labelling this threat. Following the infiltration and data encryption, virus drops a .html or GUI files on the infected computer's desktop. These files provide instructions which the victim has to follow in order to be able to access encrypted files again.
We should warn you that paying the ransom does not guarantee anything, meaning you might be left without your files and your money if the hackers decide to do so.
help@onyon.info virus is another version of the Onion virus which appends [help@onyon.info].master extensions to the encrypted files. The email address featured in this extension placed there by the cyber criminals on purpose. It serves a double purpose.
First, it helps indicate what specific version of the malicious virus family has encrypted the victim's computer and second, it points to where the victims might find information about the data recovery. Most likely, though, the victims will contact the perpetrators via this address only with their ransom payment applications as all data recovery instructions are listed in a separate document — a ransom note called “!#_RESTORE_FILES_#!”.
Methods of ransomware dispersion
Like any other ransomware, Onion ransomware tends to spread via exploit kits[4], spam email attachments[5], illegal websites and so on. According to the recent malware research, the virus spreads in the disguise of ZIP file attachment of spam email. Such email messages are supposedly brought by various authorities and presented as invoices, tax fees, and other important documents. Verify the sender and only then review the content.
Furthermore, avoid visiting illegal websites, clicking on the pop-ups that offer to update Java, Flash Player, Media Player or another software out of nowhere. File-sharing, specifically, torrent sharing domains often get compromised with malware, such as exploit kits. In order to reduce the risk of getting infected with them, install FortectIntego or Malwarebytes. They are also practical tools in dealing with other sorts of malware. Now let us move on to the final section which explains how to remove Onion.
Experts' advice on Onion virus removal
Despite how menacing ransomware seizes the device, it is crucial to put an end to the malware right away. Thus, remove Onion virus with the assistance of malware elimination tool. Do not get surprised if the device may not be fully responding. Malware may modify registry files which result in non-responding functions. In that case, the below guide will come in handy.
Bear in mind that Onion removal must be completed in order to advance to another stage. You may also interfere with the malware processes, by completing its initiated tasks in the Task Manager.
Getting rid of Onion virus. Follow these steps
Manual removal using Safe Mode
Follow the steps to launch Safe Mode with Networking. This should grant you access to vital system functions. launch the program for it to root out Onion malware.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Onion using System Restore
You may also try to perform a System Restore to gain access to the security utilities and perform system cleanup.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Onion. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Onion from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Onion, you can use several methods to restore them:
Data Recovery Pro mode
This program is one of the solutions for you to recover the files. It might come in handy restoring accidentally deleted emails as well.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Onion ransomware;
- Restore them.
Make use of ShadowExplorer
There are no reports whether the malware removes shadow volume copies beforehand. Thus, you have a viable method to recover files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Onion Decrypter
Since it is related to Dharma virus, you may succeed in decrypting the data with Dharma Decryptor. On the other hand, taking into account its updated features, there are no guarantees that the former option will work out.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Onion and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Andrew Stuart. Ransomware: when the movies become reality. ITProProtocol. News and Guides for Business and Enterprise IT.
- ^ Ian Murphy. Dharma ransomware unlocked. EnterpriseTimes. Business Technology News, Latest Tech News.
- ^ Jamie Hinks. Onion: The new ransomware that is even harder to stop. ITProProtocol. News and Guides for Business and Enterprise IT.
- ^ Criminals Prepare For Global Cyberattack With Sundown Exploit Kit. The Merkle. IT news andcomments.
- ^ Limor Kessem. The Necurs Botnet: A Pandora’s Box of Malicious Spam. Security Intelligence. Analysis and Insight on Information Security .





















