Cyberpunk ransomware (virus) - Recovery Instructions Included
Cyberpunk virus Removal Guide
What is Cyberpunk ransomware?
Cyberpunk ransomware is a type of malicious software that specializes in money extortion
Cyberpunk is a ransomware-type virus that may infiltrate your Windows one day unexpectedly. Belonging to the broad family of Dharma, it was first seen in the wild in the middle of October 2022. Once installed, the malware immediately looks for pictures, documents, databases, videos, or other personal files to encrypt.
With the help of sophisticated encryption algorithms such as AES or RSA,[1] it locks all files and appends the extension .CYBER (along with cybercriminals' email and user ID) to each, making them inaccessible. Despite that it may seem that the data is corrupted, it is not the case – it can be retrieved with the help of a decryptor that hackers are in possession of.
This is the point that crooks were waiting for: they are willing to sell the decryption software to users for a price. According to two ransom notes delivered upon finished data encryption CYBER.txt and a pop-up window, victims need to write to email cyberpunk@onionmail.org or cyberpsycho@msgsafe.io and include their ID. If victims agree to pay the ransom and transfer the requested amount of bitcoin, crooks promise to deliver the decryptor. We don't recommend communicating with the attackers and following an alternative route instead.
| Name | Cyberpunk ransomware |
|---|---|
| Type | Ransomware, data locking malware, cryptovirus |
| Family | Dharma |
| File extension | .CYBER |
| Ransom note | CYBER.txt and a pop-up window |
| Contact | cyberpunk@onionmail.org and cyberpsycho@msgsafe.io |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| removal | Before proceeding with data recovery solutions, make sure you first scan your system with SpyHunter 5Combo Cleaner, Malwarebytes or another reputable anti-malware software |
| System fix | Malware can wreak havoc on Windows systems, causing errors, crashes, lag, and other stability issues even after it is terminated. To fix the operating system, we recommend scanning it with the FortectIntego repair tool. |
Ransomware delivers two ransom notes with info about the attack
In most cases, malware writers try to ensure that victims are aware of payment and contact information since there is no other way for them to receive the payment. This is possibly why cybercriminals provided two ransom notes: a text file and a pop-up window. Ransomware has traditionally used TXT files as ransom notes, but this isn't always the case.
The pop-up window titled cyberpunk@onionmail.org shows up as soon as data is encrypted and includes a detailed description of what happened to users' files and what they need to do to recover them:
YOUR FILES ARE ENCRYPTED
cyberpunk
Don't worry, you can return all your files!
If you want to restore them, write to the mail: cyberpunk@onionmail.org YOUR ID
If you have not answered by mail within 12 hours, write to us by another mail:cyberpsycho@msgsafe.io
ATTENTION!
We recommend you contact us directly to avoid overpaying agents
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
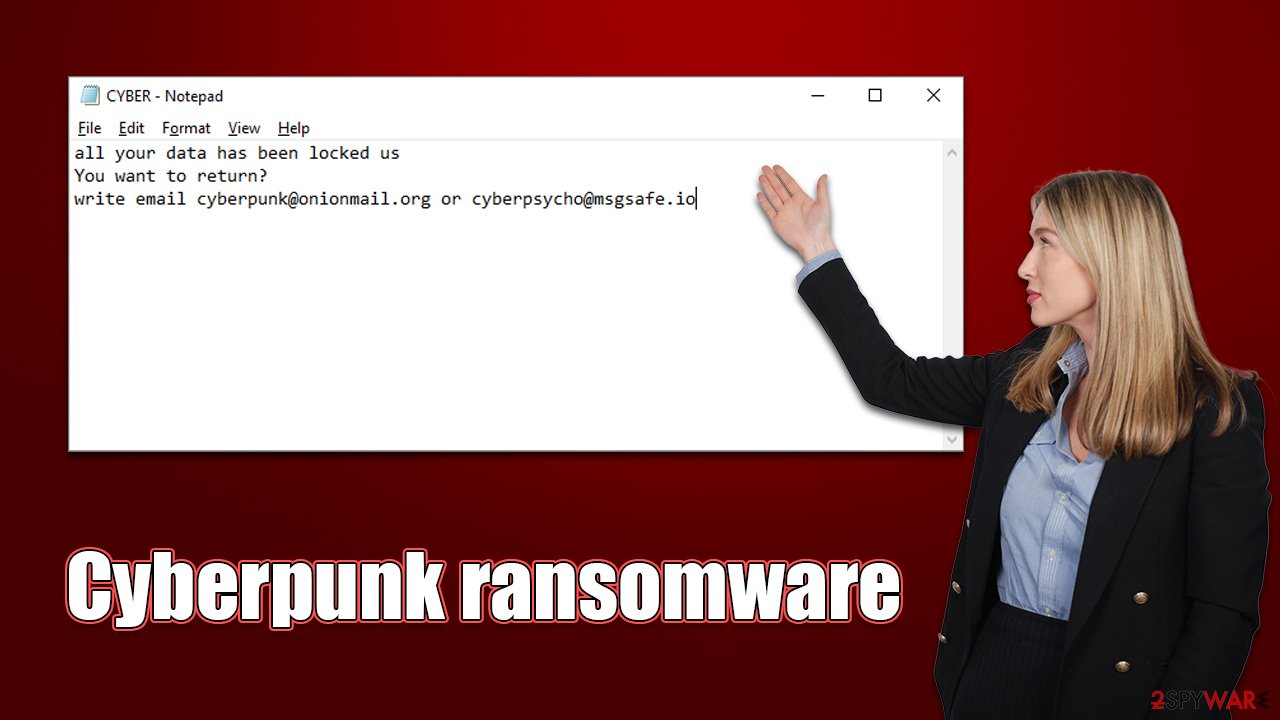
A much shorter version of this note is delivered via the text file, which mainly includes the contact information:
all your data has been locked us
You want to return?
write email cyberpunk@onionmail.org or cyberpsycho@msgsafe.io
These notes are very typical of all Dharma variants, such as Dkey, Iq20, or Gnik. Cybercriminals try to convince users not to seek alternative data recovery methods simply because it's in their interest to do so. Communicating with the attackers and paying the ransom would simply prove to them that they can manipulate the affected people and make them pay. In the end, they might not even deliver the promised recovery tool, or it may not work. So, we recommend following the steps below instead and selecting alternative recovery methods.
Ransomware removal
The majority of people who acquire ransomware have never dealt with anything like it before, therefore, they are frequently completely lost. However, following the right procedures while dealing with ransomware is crucial, as it may affect the likelihood of data restoration to its functional state.
If you have your computer connected to a network, it might be that other computers may also be infected. Besides, malware is known to communicate with a remote server known as Command & Control[2] via the internet, so you need to make sure you disconnect your PC from it. You can simply unplug the ethernet cable or disconnect your WiFi. Once the affected machine is no longer connected to a network and the internet, you should immediately perform Cyberpunk ransomware removal – employ anti-malware for that.
Some ransomware can self-destruct after the encryption of the files is complete. Even under these circumstances, malware may leave behind other modules that steal data or work together with other dangerous programs on your device.
All ransomware-related files, additional modules, and other malware that could be hidden on your system can be found and removed using SpyHunter 5Combo Cleaner or Malwarebytes. The security software is quite simple to use, and using it to remove malware successfully doesn't require any prior IT expertise. If malware is tampering with removal, you should access Safe Mode as follows:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
- Select Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
After you are sure that the malware is gone from your system, we also recommend making sure that the Windows system is not damaged. Once installed, ransomware (along with other malware) could compromise files of the system, which may cause all sorts of issues after its removal, as security software is unable to repair them.
As a result, you may offer all sorts of stability issues, such as DLL[3] missing errors, Blue Screen of Death crashes, registry issues, and more. To remediate the operating system and fix damaged files, we recommend using FortectIntego PC repair tool, which is excellent software dealing with malware-related and unrelated computer issues.
Alternative methods for recovering files
Some users are under the impression that after malware elimination, their files will be automatically restored. This is not the case at all, as ransomware performs an encryption procedure on its own, leaving the return of the data to normal impossible after the job is completed.
Although some users assume that when malware removal is completed, their files will be immediately restored, this is not the reality at all. Because ransomware conducts the encryption process on its own, once it is finished, the data cannot be restored to its original state by removing the infection.
The scenario gets more difficult since the encryption locks files with a key consisting of an alphanumeric string. The attackers are the only ones with access to the key. But for the reasons already given, we advise attempting different approaches. Before proceeding, you should make sure you make copies of encrypted files you value, or you may end up corrupting them forever. Begin with data recovery software:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Cyberpunk ransomware Cyberpunk ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Decryption tools might also be created for certain ransomware strains thanks to the efforts of security researchers. In some cases, law authorities seize the servers of malicious actors, which allows the keys to be released by the public – reputable security vendors usually do this. Here are a few links you might find helpful:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Ron Franklin. AES vs. RSA Encryption: What Are the Differences?. Precisely. Data analysis.
- ^ Command and Control [C&C] Server. Trend Micro. Security blog.
- ^ What is a DLL. Microsoft. Official website.






