Wallet ransomware / virus (Free Guide) - Quick Decryption Solution
Wallet virus Removal Guide
What is Wallet ransomware virus?
Wallet ransomware is a crypto-virus that can be decrypted for free
Wallet virus is among all the other ransomware infections which lock up files and demand a ransom to be paid for their release. This file-encrypting[1] cyberthreat belongs to the group of Dharma and Crysis ransomware. It uses AES and RSA[2] cryptography and appends either .wallet or .wallet.lock extension to targeted data. Fortunately, victims can restore their files using free decryption software. If you are dealing with this virus, note that not all locked files can be decrypted. Developers of BTCWare decided to use the same extension in December 2017.
| Summary | |
| Name | .Wallet ransomware |
|---|---|
| Type | Crypto-virus |
| Connections | Dharma and Crysis ransomware |
| Cipher used | AES and RSA |
| Extension | .wallet, .wallet.lock |
| Decryptable | Yes |
| Distribution | Spam emails, unprotected RDP, malicious links, and sites, etc. |
| Elimination | Employ anti-malware software such as SpyHunter 5Combo Cleaner |
| System fix | After ransomware is eliminated, use FortectIntego to fix virus damage automatically |
Once inside the system, the virus initiates changes in the computer's registry and adds numerous processes which disrupt the whole system. Additionally, the ransomware starts encrypting the victim's files and then drops the ransom note asking to pay from $500 to $1500 as a ransom. Besides, the virus changes the desktop image with a ransom note presenting file recovery instructions. The full ransom note reads the following:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 3 files for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
Also you can find other places to buy Bitcoins and beginners guide here:
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Another type of the ransom note states:
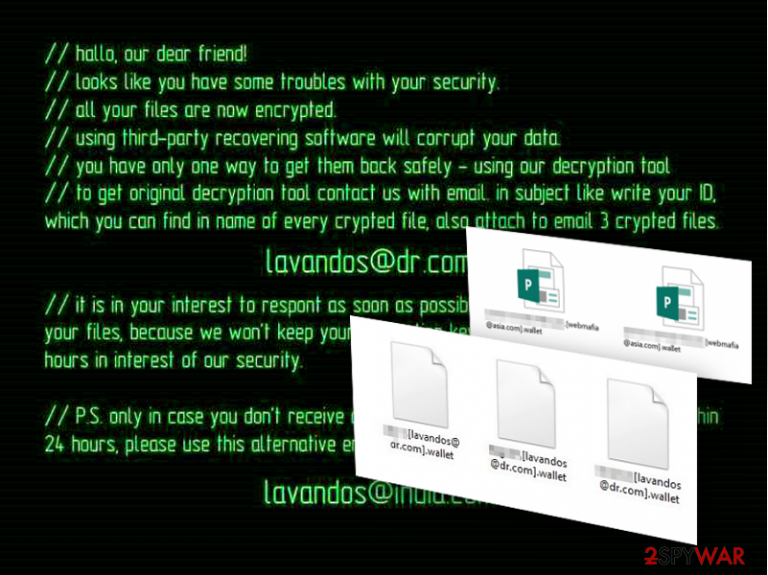
“//hallo, our dear friend!
//looks like you have some troubles with your security.
//all your files are now encrypted.
//using third-party recovering software will corrupt your data.
//you have only one way to get them back safely – using our decryption tool.
//to get original decryption tool contact us with email. in subject like write your ID, which you can find in name of every crypted file, also attach to email 3 crypted files.
lavandos@dr.com
//it is in your interest to respond as soon as possible to ensure the restoration of your files, because we won’t keep your decryption keys at our servers more than 72 hours in interest of our security.
//P.S. only in case you don’t receive a response from the first email address within 24 hours, please use this alternative email address.
amagnus@india.com
Because of the clumsy syntactic constructions and spelling mistakes, it becomes obvious that the hackers behind the virus are non-native English speakers[3]. Nevertheless, their targets are users who speak the language and can understand the situation.
Note that hackers standing behind Crysis and Dharma ransomware families are known for releasing decryption keys for old variants of the malware, especially when they start using a new file extension to distort users’ data. Thus, there’s no surprise that 198 master decryption keys were published[4] as soon as the ransomware family started using .onion file extension, which is known as a previous version of the Crysis.
However, victims can restore files with the help of a free decryptor created by Avast, Eset or TrendMicro. However, before trying to decrypt the ransomware, you should remove Wallet ransomware from the device using SpyHunter 5Combo Cleaner or another malware elimination program. Also, using FortectIntego will ensure that malware damage done to Windows system files is reverted.
BTCWare uses the same extension
Security researchers reported that a new version of BTCWare ransomware started using .[paydayz@cock.li]-id-11B0.wallet file extension to encrypt files on the targeted computer. However, the free Avast or similar decryptor won’t help to restore files corrupted by this virus.
It’s not the first time when authors of the malware use this file extension too. GlobeImposter and CryptoMix viruses were also using the same extension. However, these ransomware families use different filename patterns.
However, if you ever find this extension appended to your files, you have to check which malware family attacked your device by checking provided contact email address and reading provided ransom note.
Ransomware operation
Once this virus is deployed on the system, it activates its malicious executable, which then initiates a system scan of the entire computer. During the scan, the virus searches for specific file extensions that are mainly related to the user’s documents, media files, archives, etc.[5]
When located, these files are encrypted right away and marked with [email address].wallet or [email address].wallet.lock file extensions. Usually, they feature extortionists' email addresses that should be used to contact them. They are known for using 358 different email addresses, including:
- Mmk.scorpion@aol.com,
- orlegionfromheaven@india.com,
- destroed_total@aol.com,
- stopper@india.com,
- bitcoin143@india.com,
- mkgoro@india.com,
- mkliukang@india.com,
- lavandos@dr.com.
Further instructions on data recovery are given only after contacting the criminals directly. We can presume that criminals demand the victims to pay a ransom amount in Bitcoins and make the transaction via the anonymous Tor network.
However, doing it is not needed because the virus is decryptable, and you can get back access to your files for free after the ransomware removal. However, once your files are decrypted, you should also make backups in order to protect your data from other crypto-malware that might hijack your device anytime.
Malware versions listed
Joker_lucker@aol.com ransomware is one of many versions of this ransomware virus that relies on AES and RSA encryption algorithms. These algorithms have been used to encrypt word, pdf, excel, and similar files and make them inaccessible. You can separate files encrypted by Joker_lucker@aol.com virus or other ransomware by looking at their extensions.
This email address has been used by hackers to mark the target files and warn the victims that they won't be capable of using them. If infected, you can restore your files from backup. According to hackers, you should buy a special decryption key sent to them via Command & Control servers as soon as they finish the encryption process. Please, do NOT act according to hackers' needs as they can leave you with nothing!
Mk.scorpion@aol.com ransomware virus can encrypt most of your files that are saved on your computer. It acts just like its previous versions that start asking for the ransom right after finishing the encryption process. Typically, this ransomware leaves the .[Mk.scorpion@aol.com].wallet file extension to the corrupted files and also drops README.txt file, which is supposed to inform the victim about files' recovery.
However, the recovery steps given by Mk.scorpion@aol.com ransomware are not as detailed as the ones provided by other ransomware authors. However, you should not consider the idea of making a payment to cybercriminals.

Developers rely on malicious spam emails to spread ransomware
Just like the original virus version, Wallet ransomware uses phishing [6] to enter computers. Mostly, scammers rely on spam campaigns to deliver infected files to the potential victims directly into their inboxes. All that the user has to do is download a file attached to a convincing-looking email, and the virus is let loose.
Today, there are still numerous computer users who fall into such traps. It is hard to blame them because hackers always apply advanced social engineering skills to make victims believe they must download supposed plane tickets, invoices, or billing documents.
This only teaches us that we should not take every email for granted, even if it is received from some reputable organization or government institution. You should always check your mail before opening it and prevent ransomware from encrypting your files.
Wallet ransomware removal instructions
Ransomware is one of the leading viruses considering its complexity and impact on the system. Having this in mind, it would be naïve to expect easy ransomware removal either. Of course, there are tools using which ransomware elimination may be incomparably less difficult.
A thorough system scan with professional anti-malware utilities (e.g. SpyHunter 5Combo Cleaner or Malwarebytes) will not take you longer than10 minutes, and after it is done, you will be able to use your computer normally again. Don’t worry if you will fail to remove Wallet virus in the first go. Nobody said the virus wouldn’t fight back when you try to exterminate it. Just go to the end of the article, where we provide decontamination instructions and follow them carefully.
Getting rid of Wallet virus. Follow these steps
Manual removal using Safe Mode
Ransomware removal will go smoother if you carry it out while your device is in Safe Mode. Below you will find instructions on how to boot your PC in this particular mode.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Wallet using System Restore
To ensure smooth ransomware removal, you will need to put some extra work and decontaminate the virus, which you will do by following the steps provided below. Just don't forget to scan your device automatically afterward!
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Wallet. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Wallet from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Wallet, you can use several methods to restore them:
Decrypt files encrypted by the virus easily with Data Recovery Pro
After you eliminate the ransomware from your computer, do not forget to decrypt your data, too! Try out Data Recovery Pro for automatic recovery.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Wallet ransomware;
- Restore them.
When are the Windows Previous Versions feature helpful in recovering data?
Windows Previous Versions feature is a convenient and effective way of recovering encrypted data. Nevertheless, this feature will only be helpful if you had the System Restore function enabled before the virus attacked your PC.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer is a good choice for the recovery of files
ShadowExplorer is a software that uses Volume Shadow Copies of encrypted files to recover them. This recovery method will only work if Volume Shadow Copies are not damaged or deleted by the virus.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Use Wallet Decryptor
In order to use Avast Crysis Decryptor and restore files, you should follow these steps:
- Download the program from here.
- When the download completes, double-click the program and open it.
- Make sure that you have downloaded the 1.0.103.0 version of the program because only it can restore files.
- On the main screen of the program click “Next” button.
- In the appeared screen you need to choose locations and drivers that include encrypted files that you want to decrypt. Once you choose them, click “Next.”
- In the next window make sure you have checked both options “Backup encrypted files” and “Run the decryption process as an administrator.”
- Click “Decrypt” button.
- In the popped up User Account Control prompt click “Yes” in order to continue the decryption process.
The program will start system scan and data decryption procedure. Be patient, this process might take more than 30 minutes. The more files you have stored on the device, the more time decryption will take. Once this procedure is over, the program will provide “Decryption Complete” window.
Besides, you can also use alternative decryptors from Eset and TrendMicro.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Wallet and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Crypto ransomware. Us-cert. United States Computer Emergency Readiness Team website.
- ^ AES and RSA encryption. Boxcryptor. Encryption for cloud storage.
- ^ Kevin Savage; Peter Coogan; Hon Lau. The evolution of ransomware. Symantec. Global leader in next-generation cyber security.
- ^ Lawrence Abrams. Wallet Ransomware Master Keys Released on BleepingComputer. Avast Releases Free Decryptor. Bleeping Computer. News, Reviews, and Technical Support.
- ^ Rick Correa. How fast does ransomware encrypt files? Faster than you think. Barkly. Barkly Endpoint Protection Blog.
- ^ Spear Phishing: Scam, Not Sport. Norton. Antivirus Software and Spyware Removal Blog.







