3Ex2BJT2aiqDJKPAFeuWMbB4T6MhML384p malware (Free Instructions)
3Ex2BJT2aiqDJKPAFeuWMbB4T6MhML384p malware Removal Guide
What is 3Ex2BJT2aiqDJKPAFeuWMbB4T6MhML384p malware?
3Ex2BJT2aiqDJKPAFeuWMbB4T6MhML384p is the crypto wallet address of clipper malware developers

3Ex2BJT2aiqDJKPAFeuWMbB4T6MhML384p malware is used to steal cryptocurrency, Bitcoin specifically. The malicious program detects whenever users copy a BTC wallet address and replaces it with the one that belongs to the cybercriminals. During the research, it was found that it would be replaced with either 12CLn8QNN7twEuRJSXi8Na4VfzhAxWxDUn or 3Ex2BJT2aiqDJKPAFeuWMbB4T6MhML384p address.
Users then unknowingly transfer their cryptocurrency funds to the attackers. It was also found that the installer used to distribute the clipper malware installs potentially unwanted programs,[1] like adware, and browser hijackers. So people can also notice the browser settings change, like the homepage, new tab address, and search engine. Adware can cause an increased amount of commercial content, like pop-ups, banners, and redirects. It can also collect data, and cause other problems.
| NAME | 3Ex2BJT2aiqDJKPAFeuWMbB4T6MhML384p |
| TYPE | Malware |
| SYMPTOMS | When users paste something into their clipboard, the text changes into a string of letters and numbers; people could also experience an increased amount of commercial content and changed browser settings |
| DISTRIBUTION | Torrent websites; “cracked” software; malicious links |
| DANGERS | The malware can come with bundled software that could cause the installation of other malicious programs and PUAs |
| ELIMINATION | Follow our guide to learn how to remove malware with professional security tools |
| FURTHER STEPS | Use a repair tool FortectIntego to fix any remaining damage and optimize the machine |
Distribution methods
The clipper malware was found through a “cracked” software[2] download page. Security experts strongly advise against installing pirated software for this exact reason. It is impossible to know if the program you want to download is safe and not altered by cybercriminals to perform malicious tasks.
Other common malware distribution methods include peer-to-peer file-sharing and freeware[3] platforms, and third-party downloaders. Freeware installers often include additional programs that monetize user activity. It is important to always choose the “Custom” or “Advanced” installation method, read the Privacy Policy and Terms of Use. The most important part is to check the file list and untick the boxes next to any unrelated applications.
Some threat actors also spread malware using email. Usually, social engineering[4] tactics are used to disguise the emails to look unsuspicious. It may look like a message from a friend or a well-known company. Often there would be a prompt to get users to open the email attachment. Most commonly used files to distribute malware are JavaScript files, executable files, archives (like ZIP, RAR), Microsoft Office, and PDF documents.
It is best not to open any emails from unknown senders. If you receive an email with an attachment you were not expecting from someone you know, it is also best to double-check with them through another platform. Sometimes threat actors can access the friend list and make the email look like from someone you know.
Stop the malicious background process
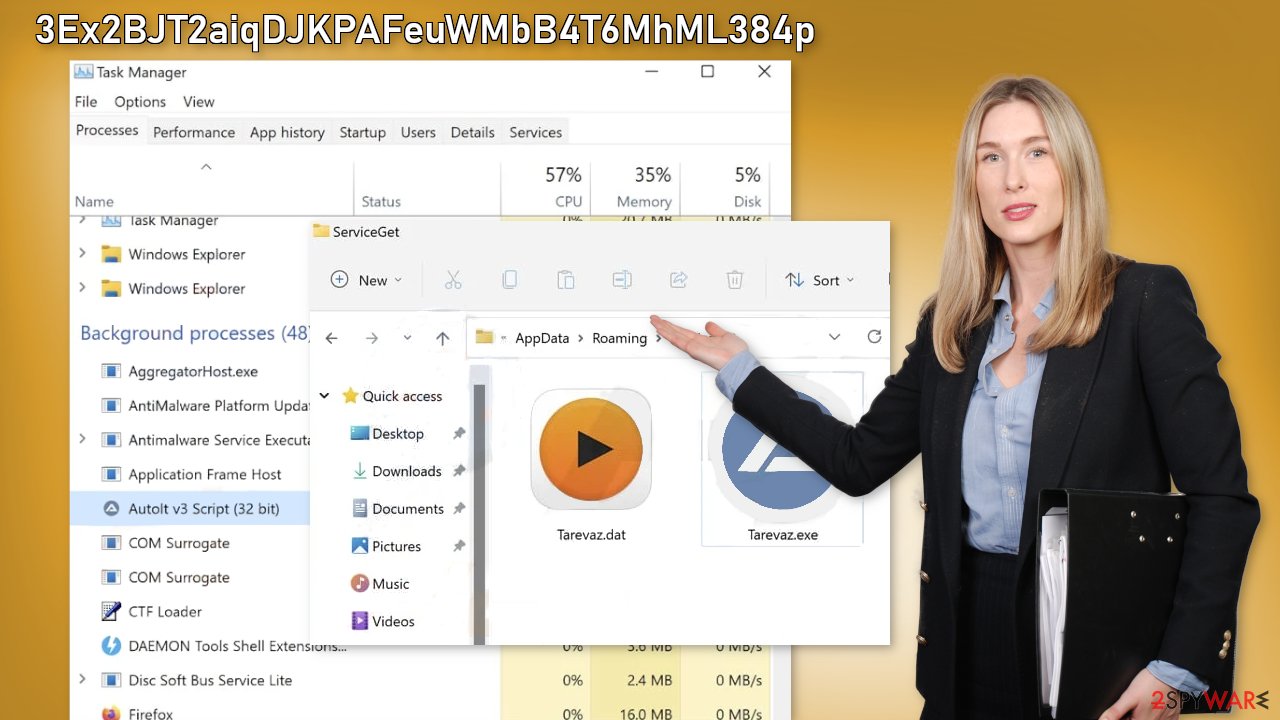
You can stop the disruptive copy/paste actions performed by the 3Ex2BJT2aiqDJKPAFeuWMbB4T6MhML384p malware by ending the process in the Task Manager:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.
![Open task manager Open task manager]()
- Scroll down to Background processes section, and look for AutoIt v3 Script (32 bit).
- Right-click and select Open file location.
![Open file location Open file location]()
- Go back to the process, right-click and pick End Task.
![End task End task]()
- Delete the contents of the malicious folder.
Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on AutoIt v3 Script (32 bit) and pick Disable.
![Startup Startup]()
Terminating the process will not remove the program itself. Therefore, we strongly advise you to continue with our guide to remove the malware completely.
Remove malware and PUPs from your machine
Since the clipper malware was found to be distributed bundled together with other PUAs and malware, you should clean your system thoroughly. PUPs can be disguised as “handy” tools that look like system optimizers, browser extensions, antivirus programs, etc.
Regular users often fail to identify these unwanted applications as they are designed to look unsuspicious. Manual removal can also sometimes result in the renewal of infection as users often do not remove all the related files and entries. It is a meticulous process that we recommend performing with professional security software like SpyHunter 5Combo Cleaner and Malwarebytes
These anti-malware tools will completely eliminate the malicious processes running in the background and will warn you in the future if a suspicious program will try to enter the system. However, if you still want to do this yourself, you can follow the steps below:
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.
![Uninstall from Windows 7/XP Uninstall from Windows 7/XP]()
- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Repair the damaged operating system
Performance, stability, and usability issues, to the point where a full Windows reinstall is required, are nothing unusual after a virus infection. These types of intruders can alter the Windows registry database, damage vital bootup, and other sections, delete or corrupt DLL files, etc. Once a system file is damaged, antivirus software cannot fix it.
Manual troubleshooting of such damage is also very complicated and can take a long time. This is why FortectIntego was developed. It can fix a lot of the damage caused by an infection like this. Blue Screen errors, freezes, registry errors, damaged DLLs, etc., can make your computer completely unusable. By using this actually useful maintenance tool, you could prevent yourself from having to reinstall WIndows completely.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
- The analysis of your machine will begin immediately
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
Fix browser issues
Since the 3Ex2BJT2aiqDJKPAFeuWMbB4T6MhML384p malware might have been bundled together with browser hijackers, you should also take care of your browsers. Browser hijackers are mild infections compared to malware but they can lead to more serious problems. Users who are infected by a browser hijacker might experience a changed homepage, new tab address, and search engine.
Some may also notice an increased amount of commercial content, like redirects, or push notifications. These advertisements can contain links leading to dangerous websites, resulting in personal information disclosure to fraudsters and more installations of PUPs and malware.
If you experience any of this erratic behavior, you can look for instructions on how to deal with it below this article. Guides are available for Google Chrome, Mozilla Firefox, and MS Edge.
Getting rid of 3Ex2BJT2aiqDJKPAFeuWMbB4T6MhML384p malware. Follow these steps
Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

How to prevent from getting malware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Chris Hoffman. PUPs Explained: What is a “Potentially Unwanted Program”?. Howtogeek. Technology Magazine.
- ^ Georgina Torbet. 5 Security Reasons Not to Download Cracked Software. Makeuseof. Tech Reviews and Security Insights.
- ^ Tim Fisher. What Is Freeware?. Lifewire. Internet, Networking, and Security.
- ^ Social engineering (security). Wikipedia, the free encyclopedia.























