CloudMensis Mac virus (Free Guide)
CloudMensis Mac virus Removal Guide
What is CloudMensis Mac virus?
CloudMensis is a dangerous Mac infection that operates as a backdoor

CloudMensis is a Mac virus that was recently spotted by security researchers by the ESET security team[1] in the second half of July 2022. The first attacks emerged back in February, and it seems like all of them are targeted, which means that infecting regular computer users is unlikely to be cybercriminals' goal.
CloudMensis operates as a backdoor; once installed on the system, it is capable of performing cybercriminals' commands remotely. Its main goal is to steal various valuable information, including emails, documents, keystrokes, and even screen captures. Data theft of such magnitude can result in various personal security and privacy issues, thus the infection should be found and eliminated as soon as possible.
The virus is brand new and has never been discovered or analyzed before, which may result in serious challenges for security software initially. Luckily, because of the discovery, malware can be easily analyzed, detected, and removed from the system. In this article, we will explain how to do just that.
| Name | CloudMensis |
| Type | Malware, backdoor, data stealer |
| Naming pattern | Researchers named malware after its ability to use cloud storage services for communication |
| Distribution | The main propagation techniques are still not verified, but the malware was found to abuse software vulnerabilities |
| Programming language | Objective-C |
| Removal | Perform a full system scan with SpyHunter 5Combo Cleaner to eradicate all malware components effectively |
| System optimization | After you terminate the infection with all its associated components, we recommend you also scan your machine with FortectIntego for the best results |
CloudMensis overview
Since malware is relatively new in the security landscape, little is known about its developer and distributor. According to security experts, the distribution of CloudMensis is relatively limited, which suggests that it is used as a part of a targeted attack. The authors of this one choose to target individuals of interest exclusively, and they do that with the help of software vulnerabilities on some of the Mac machines.
Researchers said that, despite malware exploiting unpatched macOS systems, there were no zero-day flaws[2] used at the time of the research. This means that most of the attacks can be mitigated by ensuring that all the available updates are installed on the system and the existing vulnerabilities patched.
One of the unique features of malware comes from its communication with a remote C2[3] server – it is located on cloud storage with three supported providers (Dropbox, pCloud, and Yandex Disk). This fact prompted the researchers to name the virus CloudMensis.
From the Command and Control server, cybercriminals can issue as many as 39 commands for the malware to execute. Several of those are dedicated to performing data exfoliation functions, which may target private documents, emails, pictures, databases, and other files. It can also record keystrokes and gain access to the camera and microphone, increasing the scope of spying conducted. Keystroke logs can also help cybercriminals to steal various sensitive data, including account passwords, credit card details, and more.
There are speculations that malware was developed by less experienced hackers, or maybe those who are less familiar with Mac development, as there is very little obfuscation during the intrusion and the operation of the virus. Despite this, if no adequate security solution is used, CloudMensis can serve as a relatively advanced spying tool that can exfoliate crucial sensitive information from its targets.
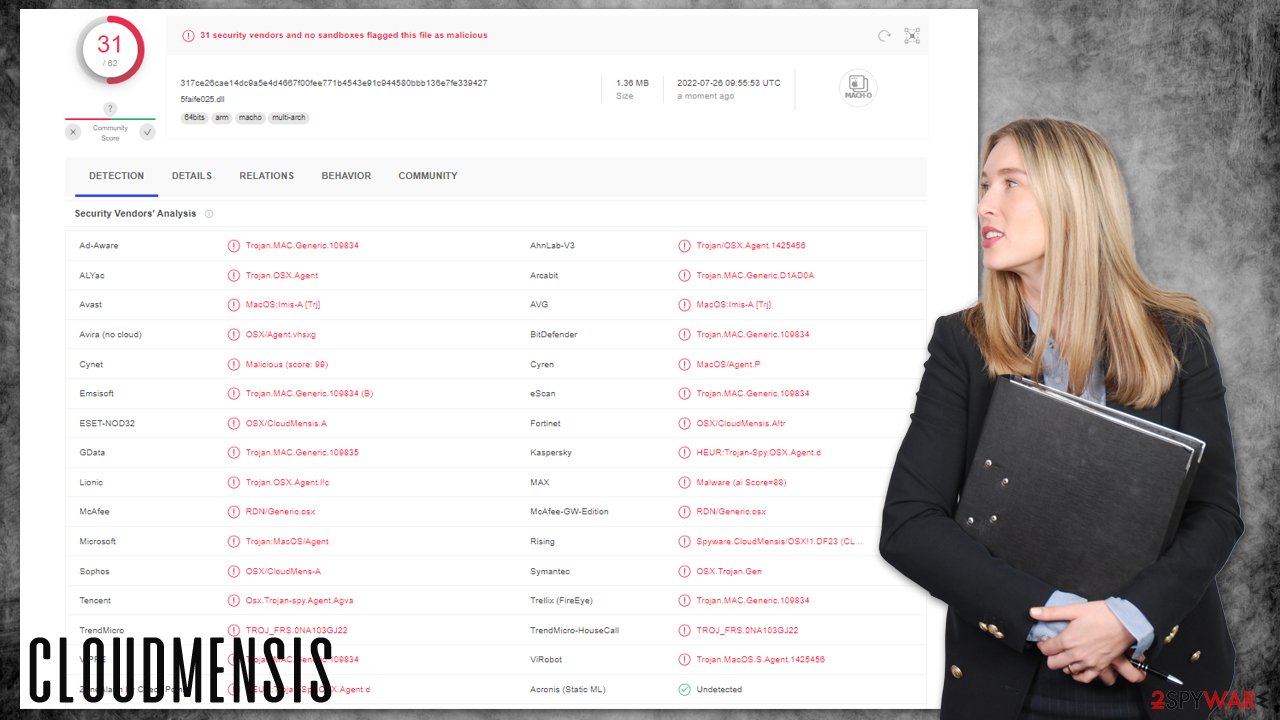
CloudMensis removal
As previously mentioned, the malware does not use sophisticated evasion methods during its operation. Nonetheless, once the existing Mac's vulnerabilities are exploited, it can place a malicious daemon on the system, which can significantly prolong its silent operation in the background if not taken care of.
Therefore, we recommend using sophisticated security tools, such as SpyHunter 5Combo Cleaner or Malwarebytes, to deal with the infection. Unlike any other regular Mac application, you won't be able to simply drag the CloudMensis app into Trash, as the entry would simply not exist in this place. Malware is a complex software that often uses various ways to disguise itself, preventing users from successfully finding and removing it.
Once the operating system is breached and the built-in security systems of Mac bypassed, the malware can run in the background unnoticed, stealing very sensitive user data in the meantime. This is why it is important to perform a full system scan with anti-malware and then make sure that all the system updates are patched.
Clean your browser
Upon infiltration, the virus may affect Safari or another web browser as well. For example, it was determined that it meddles with files within Safari's cache folder and may insert its own files. Therefore, we highly recommend you clean your browsers after you remove malware from your system. You can either employ FortectIntego for the job (which can also clear various junk files from the system) or use the manual method instead:
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ ESET Research discovers new threat to Mac users: CloudMensis spies on them in targeted operation. ESET. Security research press release.
- ^ What is a Zero-day Attack? - Definition and Explanation. Kaspersky. Security research blog.
- ^ Robert Grimmick. What is C2? Command and Control Infrastructure Explained. Varonis. Data protection service.


