Conti ransomware (Removal Guide) - Decryption Steps Included
Conti virus Removal Guide
What is Conti ransomware?
Conti ransomware is the cryptovirus that uses AES and RSA encryption algorithms to lock files before asking ransom for the alleged recovery of them
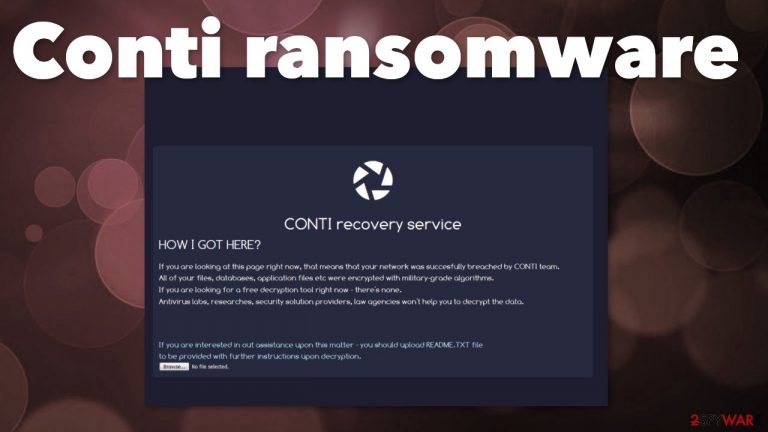
Conti ransomware – a threat that encodes files and claims to publish stolen data, so the victim is encouraged to pay the ransom in Bitcoin cryptocurrency. This is why the threat can also be called a publisher since developers created a site[1] to publish stolen details from the infected machines. It is possibly related to Ryuk ransomware that, at one moment, was one of the most notorious crypto-extortion-based threats. Developers associated with TrickBot malware are the ones that deploy this ransomware.
Conti ransomware virus name is from the indication on the data leaking site and some of the variants in this family. .Conti is also a file extension that was the first to appear when the threat started to spread worldwide. The initial ransom note also appears in the text file named CONTI_README.txt, but there are various versions of this threat already. It is believable that this family can become more dangerous with each version.
| Name | Conti ransomware |
|---|---|
| Type | Ranssomware-as-a-Service[2] or human-opearated ransomware |
| Versions | .CONTI, .COSWH, .UAKXC, .RHMLM, .TJODT, .XNMMP |
| Issues | The threat actors claim to publish data stolen from the device on the leak site to encourage victims to pay up and contact criminals as soon as possible. Stolen data can be used for more direct extortion purposes |
| Distribution | The threat spreads around with other malware like trojans, worms, malicious applications, and hacked sites. It can also rely on malicious macros placed on spam email attachments |
| File marker | The initial malware sample used .conti as the marker for encoded files. Later samples came with different randomly formed appendixes |
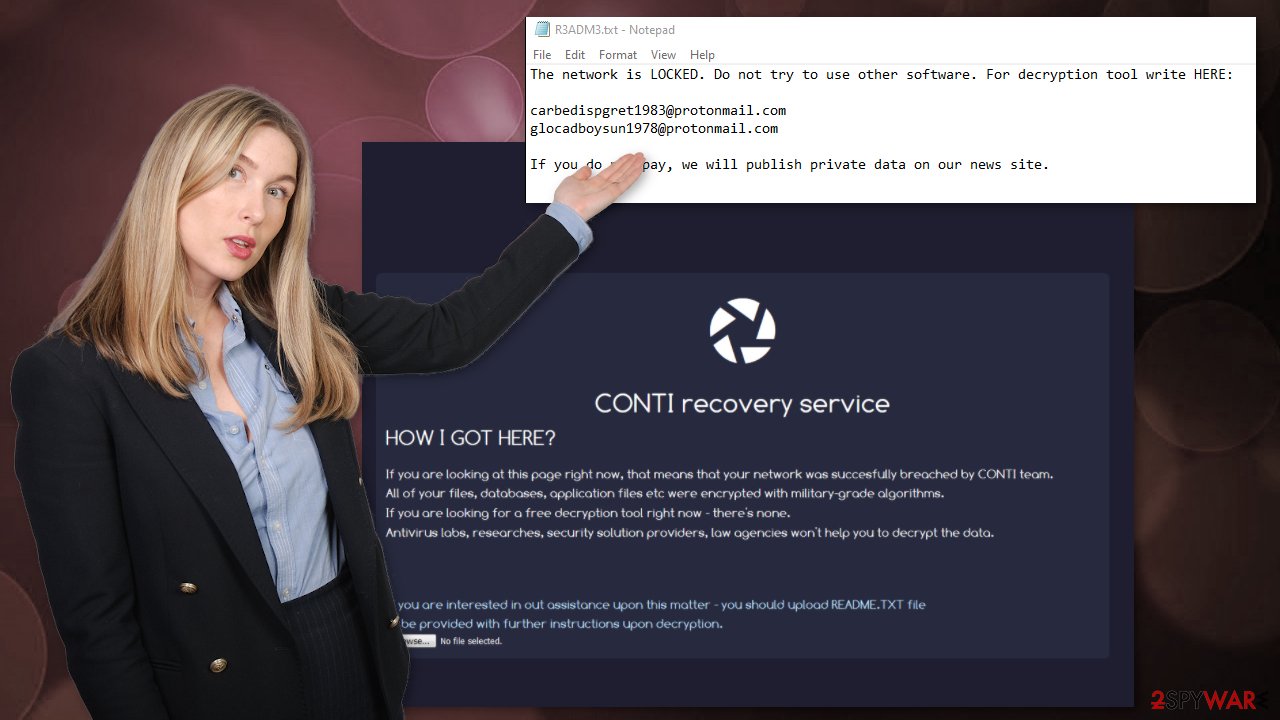
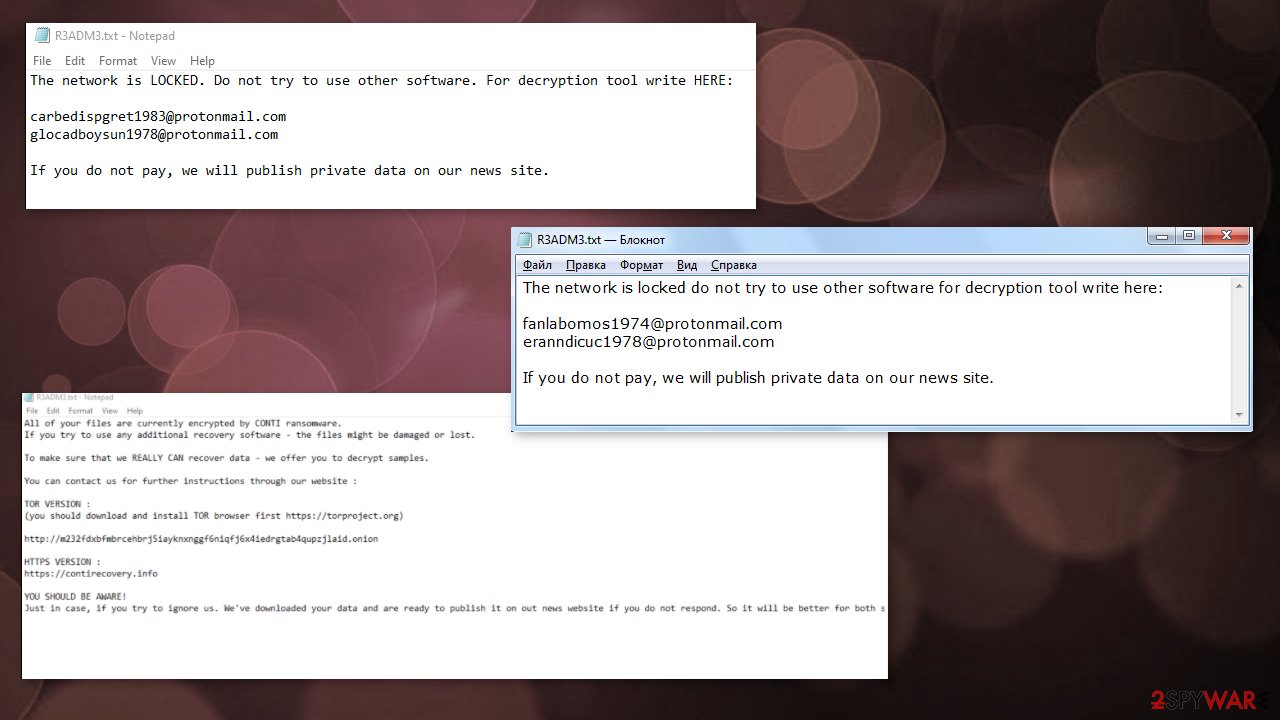
| Ransom notes | CONTI_README.txt and R3ADM3.txt |
| Elimination | To remove Conti ransomware properly, you should get an anti-malware tool that can detect the infection[3] |
| Repair | Rely on tools that can help with file damage and corrupted programs or alterations made in the system like FortectIntego |
Conti ransomware virus first came out at the end of 2019, but soon after that, new versions surfaced, and researchers found more samples of the threat. After the release of a few initial .CONTI variants, developers created a site for the information leakage.
At first, the ransom-demanding message in the text file encouraged people to stay away from decryption tools and third parties. Later variants directly claim to publish information obtained from the system.
The family has at least 6 versions of the file extensions that get formed randomly with 5 characters. R3ADM3.txt is the more recent file name used for money-demanding message distribution with the latest versions. The message is short and simple because developers explain that you either contact them and pay the ransom or experience a data leakage.
This virus tactic is borrowed from many threats like Snatch, Nemty, REvil, and others, that aim to profit from victims as much as it is possible. It only makes the process of Conti ransomware removal more difficult because people might not get the needed anti-malware or security tool in time and get their data leaked.
Even though the main targets of the virus are companies, you need to go straight to finding options helping to remove Conti ransomware. SpyHunter 5Combo Cleaner or Malwarebytes can scan the machine and find threats that trigger the encryption or further spreading of the cryptovirus.
.CONTI virus: started with a bang and not stopping
The initial Conti ransomware versions aimed to directly receive money from victims, so short ransom messages contained the email for contacting criminals and encouragement to avoid third-party decryption. For months, the threat relied on the general ransom notes and tactics aiming to get money from scared victims.
This Conti virus wave came right after when the Ryuk activities stopped, so operators could distribute Conti with a full force. With the release of Conti-2, ransomware developers managed to interfere with the system and victims' minds more. ransomware gang joined the movement of threats that deliver data publicly in August 2020.
Since Conti ransomware spreads around for a long time already and does this widely with the help of many versions, the list of contact emails gets bigger end bigger:
| mantiticvi1976@protonmail.com fahydremu1981@protonmail.com, frosculandra1975@protonmail.com, trafyralhi1988@protonmail.com, sanctornopul1986@protonmail.com | ringpawslanin1984@protonmail.com, liebupneoplan19@protonmail.com, stivobemun1979@protonmail.com, guifullcharti1970@protonmail.com, phrasitliter1981@protonmail.com, elsleepamlen1988@protonmail.com, | southbvilolor1973@protonmail.com, glocadboysun1978@protonmail.com, carbedispgret1983@protonmail.com, listun@protonmail.com, mirtum@protonmail.com |
Data leaking site revealed before the distribution of .TJODT virus
Conti 2 ransomware version of the particular ransomware was indicated at the end of August when developers started leaking sensitive data from users who refused to pay the demanded amount of cryptocurrency. This double-extortion technique became popular due to the usage in other cryptovirus attacks, so ransomware creators can make up to hundreds of thousands per victim.
.TJODT ransomware is one of the few versions in this family that deliver the ransom note with an additional line about file publication. Just before releasing this malware and .UAKXC or .RHMLM versions of the ransomware, site named Conti News got public. This page, at the time revealed data about at least 26 victims. These victims are companies from various industries.
Conti ransomware leak site pages contain samples of the stolen data from every system that this threat managed to get on. The ransomware operations show that creators may change accordingly to the popular tactics since ransom notes got changed with the newest variants in 2020.
The older version of the text placed in CONTI_README.txt:
Your system is LOCKED. Write us on the emails:
mantiticvi1976@protonmail.com
fahydremu1981@protonmail.comDO NOT TRY to decrypt files using other software.
The more recent ransom note that is delivered via CONTI.txt or R3adm3.txt:
Your system is locked down. Do not try to decrypt, otherwise you will damage fails. For decryption tool write on the email:
wellproxadsit1980@protonmail.com
mabuhyli1982@protonmail.comIf you do not pay, we will publish all private data on hxxp://conti.news/
The latest .XNMMP virus – one of the randomized file extensions
Conti file virus started the distribution in 2019 and managed to affect many systems using the same.CONTI file extension, but tactics got changed, and randomized five-character extensions started to appear at the end of encrypted data. At the same time, news sites started to appear listed in the ransom note, so people get more eager to pay sooner.
The same ransom notes redirect the threat to CONTIRecovery pages that provide the options of paying and recovering affected files. It is not recommended because criminals might use these tactics to get your trust and provide nothing after the Bitcoin transfer. Even though Conti mainly targets large businesses, companies stay away from paying since this is less risky.
Remove Conti file virus instead and try to repair the machine functions with FortectIntego before searching for data recovery options. There are no decryption tools for this family, and researchers only analyzing the samples that are not easy to get, so it may take time. This threat aims for bigger targets, but everyday users should also be cautious.

Limited data recovery options and tips for .Conti ransomware termination
Conti ransomware virus is a dangerous threat that mimics other groups that adopt newer tactics and even encryption techniques. It already uses the double algorithm encryption method, so it can become more notorious and harmful in the future as Ryuk, another possibly similar ransomware.
If you think that the Conti ransomware removal is needed and you received the ransom note, spotted mentioned appendixes, make sure to get SpyHunter 5Combo Cleaner or Malwarebytes as soon as possible. These or similar security tools can find and eliminate the malware from the machine.
To remove Conti ransomware properly, you need to run the full system scan using one of the security or anti-malware tools that can be trusted. A full check on the computer or the whole network indicates all threats, so you might find the malware that started the infection. If so, FortectIntego should be helpful when removing a trojan and other malware damage in the system.
Getting rid of Conti virus. Follow these steps
Manual removal using Safe Mode
The machine can be cleared with the help of Safe Mode with Networking
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Conti using System Restore
Get rid of the Conti ransomware virus with the help from the System Restore feature
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Conti. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Conti from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Conti, you can use several methods to restore them:
Data Recovery Pro can help with some of the encrypted files
If you managed to accidentally delete files or got your device encrypted, you can rely on Data Recovery Pro
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Conti ransomware;
- Restore them.
Try to restore Conti ransomware encoded files with Windows Previous Versions
System Restore got enabled before? You can then rely on this Windows Previous Versions feature and recover individual data yourself
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer feature – a possible way to restore affected files
When Shadow Volume Copies are not affected, you can't store files affected by the Conti ransomware virus
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Conti ransomware is not decryptable
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Conti and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Catalin Cimpanu. Conti (Ryuk) joins the ranks of ransomware gangs operating data leak sites. ZDNet. IT and cybersecurity news.
- ^ Ransomware-as-a-Service (RaaS). Tripwire. News, trends, insights.
- ^ Detection rate. VirusTotal. Online malware scanner.







