REvil ransomware (Removal Instructions) - Recovery Instructions Included
REvil virus Removal Guide
What is REvil ransomware?
REvil ransomware is a sophisticated malware family that uses RaaS scheme to proliferate the threat worldwide
REvil ransomware is a data locking virus that was first spotted back in April 2019 by security researchers from Cisco Talos.[1] Otherwise known as Sodinokibi/Sodin, the threat started off by exploiting zero-day vulnerability CVE-2019-2725.[2] It allows attackers to remotely connect to the host machine with the HTTP access to the Oracle's WebLogic server and inject the malware manually. Initially, the payload was delivered with the notorious GandCrab 5.2 ransomware, which is now believed to be its successor.
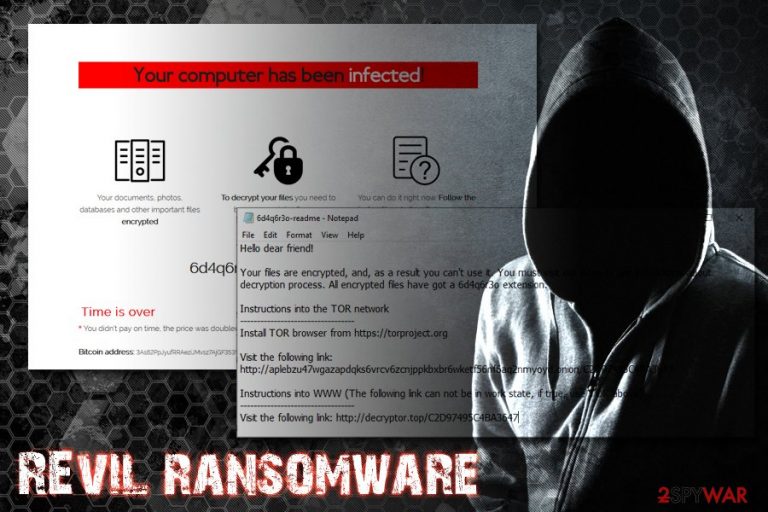
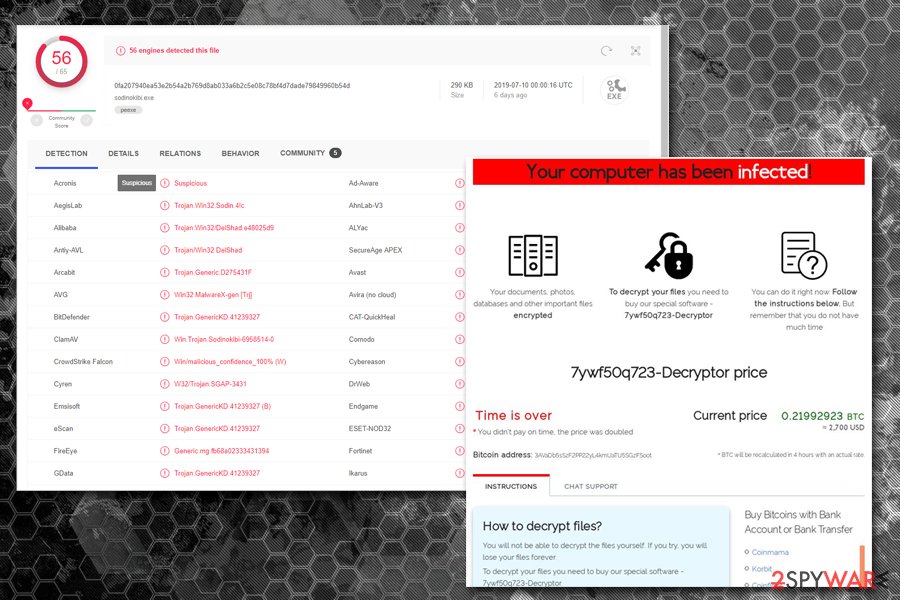
Once inside, REvil virus uses Salsa20 encryption algorithm (based on ECDH[3] key exchange method) to encrypt all data on the hard drive and the connected networks. It appends a randomly-generated extension to databases, documents, pictures, and other files.Additionally, it drops a [random]-readme.txt or HOW-TO-DECRYPT.txt ransom note and changes the desktop wallpaper. The text files explains that victims need to install TOR web browser and visit a provided link. Hackers then ask for $2,500 ransom in Bitcoin, and the demand is doubled if it not paid within five days.
| Name | REvil |
| Also known as | Sodinokibi/Sodin |
| Type | Ransomware |
| Cipher | Salsa20 |
| File extension | Randomly generated |
| Related files | sodinokibi.exe |
| Ransom note | [random]-readme.txt or HOW-TO-DECRYPT.txt |
| Ransom size | $2,500 which doubles after 5 days |
| Distribution | CVE-2019-2725, CVE-2018-8453, Rig exploit kit, spam emails, unprotected RDP, etc. |
| Decryption | Files can only be decrypted with the help of backups. Alternatively, users can try using third party recovery software (we provide download links and instructions in the recovery section below) |
| Termination | Use reputable anti-malware software, such as FortectIntego or SpyHunter 5Combo Cleaner |
REvil ransomware is believed to be the next GandCrab, as security researchers managed to find many similarities between the two. Besides, the developers of malware might be the same as well, even if they claimed to be retired by now. The malware uses more sophisticated techniques for its distribution, obfuscation, and operation, so it seems like hackers upped their game, and are going for more profits.
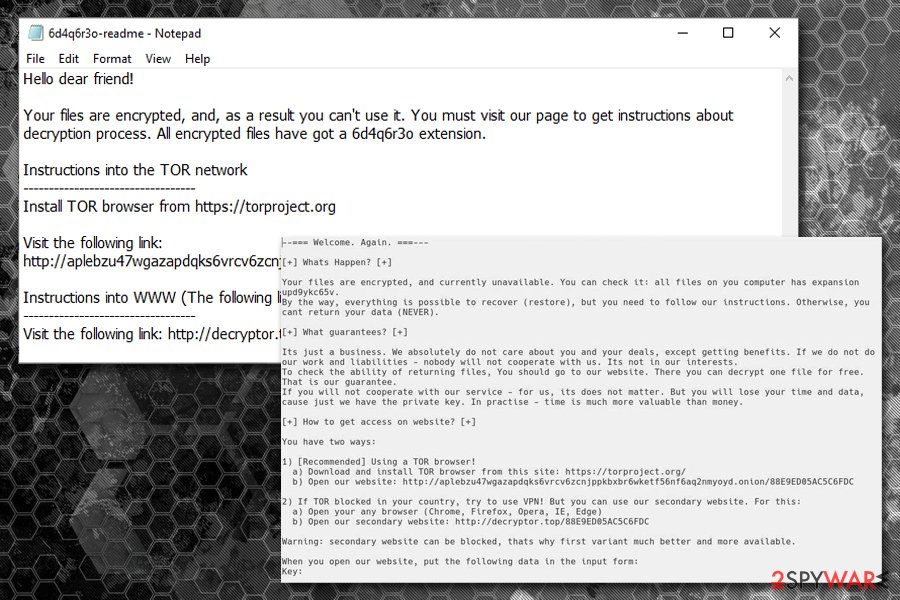
The ransom note [random]-readme.txt states the following:
Hello dear friend!
Your files are encrypted, and, as a result you can't use it. You must visit our page to get instructions about decryption process. All encrypted files have got a 6d4q6r3o extension.
Instructions into the TOR network
———————————-
Install TOR browser from https://torproject.orgVisit the following link: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/C2D97495C4BA3647
Instructions into WWW (The following link can not be in work state, if true, use TOR above):
———————————-
Visit the following link: http://decryptor.top/C2D97495C4BA3647
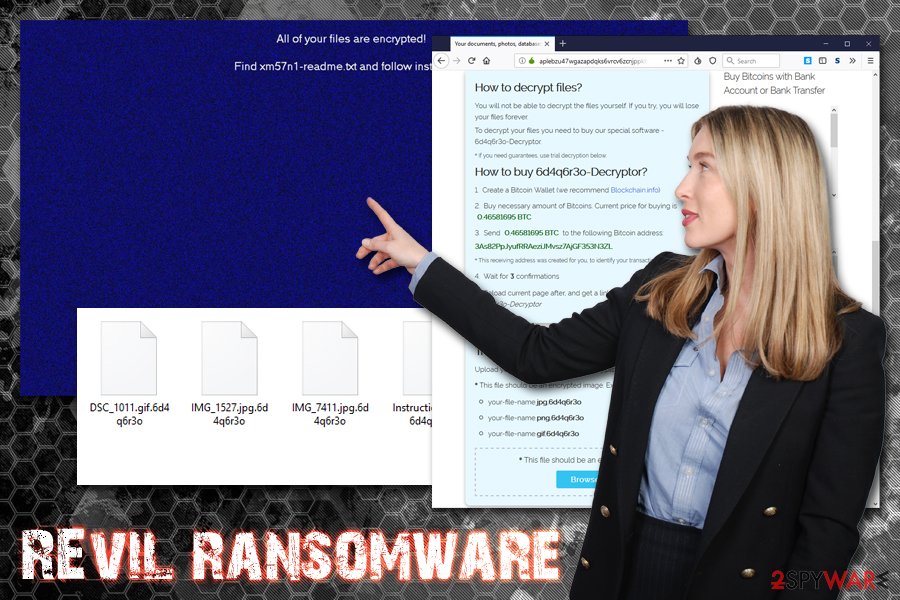
Victims of REvil are lead to a TOR page that presents a ransom amount of $2,500 and the timer which expires after five days. This creates an urgency situation for users, prompting them to pay as soon as possible.
While there is no decryption tool available for this sophisticated threat, there are alternative data recovery methods that you can use. Nevertheless, you need to remove REvil ransomware before you proceed with the file recovery process. For that use anti-malware software such as FortectIntego or SpyHunter 5Combo Cleaner, although other reputable tools can help you as well.
The advanced operation of REvil ransomware is set to retain a maximum amount of profits
While initially the malware was spotted being spread via the WebLogic flaw, REvil ransomware authors later adapted broader techniques, such as:
- Spam email attachments
- Rig exploit kit
- Hacked sites
- Unprotected RDP configurations
- Managed Service Provider hacks, etc.
In one of the campaigns, hackers behind REvil ransomware used a former Windows zero-day CVE-2018-8453,[4] which was also previously used by a state-sponsored hacking group FruityArmor since August 2018.
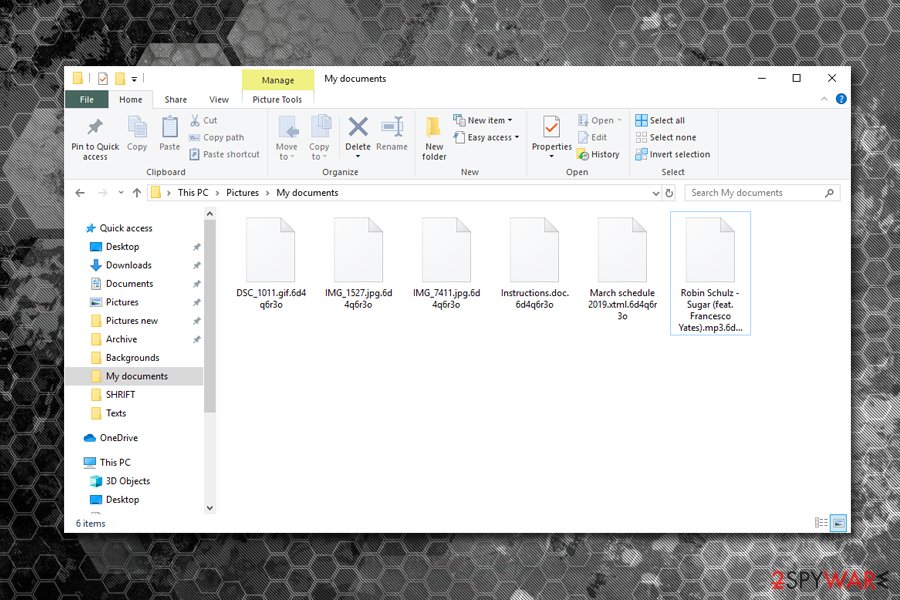
Upon infiltration, REvil ransomware performs a variety of changes to the infected computer before it starts the file encryption. It removes shadow volume copies, modifies Windows registry database, disables Windows repair function, connects to a remote server by using more than 100 domains and elevates its privileges, which is quite uncommon ransomware-type viruses.
In some cases, the virus might also uninstall security applications, complicating REvil ransomware removal. Additionally, the sophisticated threat uses a relatively old Heaven's Gate technique,[5] which allows a 64-based code to be executed in a 32-bit environment, consequently preventing its detection entirely.
Security researchers believe that this is not the end, and REvil, otherwise known as Sodinokibi, will continue to adopt new techniques to evade the detection, infect more victims and acquire maximum profits from the illegal business run by organized cybercrime groups.
CIS countries excluded from REvil ransomware campaigns, just as GandCrab was
REvil ransomware uses a predetermined list of countries that are excluded from the infection targets. That means that users whose keyboards are set to Armenian, Belarusian, Kazakh, Moldovian, Russian, Kyrgyz, Tajik, Turkmen, Ukrainian and Uzbek, are immune to the infection – as soon as REvil detects these languages, it exits the system without causing any harm.
All the mentioned countries are a part of CIS – Commonwealth of Independent States and are often excluded from various ransomware campaigns. This is because REvil ransomware authors most likely reside in those countries and do not want to attract too much attention from local authorities, making the operation of the threat so much easier and safer.
An interesting fact is that Syria is also excluded, even though it is not a part of CIS. This unusual step was also taken on by GandCrab developers when they released the keys for victims from a war-ridden country back in October 2018. This cost the makers of malware quite a sum, as Bitdefender released a free decryptor shorty after. Nevertheless, the newer version was launched soon after, and victims were unable to decrypt the data again.
Brian Krebs, one of the well-known malware analysts, believes that REvil is just a rebranded GandCrab, following up with this statement:[6]
My guess is the GandCrab team has not retired, and has simply regrouped and re-branded due to the significant amount of attention from security researchers and law enforcement investigators. It seems highly unlikely that such a successful group of cybercriminals would just walk away from such an insanely profitable enterprise.
Protect yourself against ransomware – use comprehensive malware prevention methods
Most of the regular users are convinced that they are safe as long as they have anti-malware software installed on their machines, and, while it one of the most important malware prevention methods, it is by far not enough. As described above, Sodinokibi developers use Ransomware-as-a-service scheme, which allows multiple different hacking groups or individuals to participate in the campaign, making it so much more prevalent and widespread.
The malware is sophisticated enough to use code injections that bypass anti-malware tools. For that reason, using security software only and believing that you are safe is merely silly. For the future, experts from viruset.no[7] advise using the following malware prevention techniques:
- Make sure you update the installed software along with the operating system as soon as new patches are released. Software vulnerabilities are common between sophisticated malware families, so viruses that are proliferated in such method are usually advanced and con result in severe consequences (i.e., data loss, money loss, sensitive information disclosure to cybercriminals, etc.);
- Use ad-blockers. While these tools can prevent monetization for a variety of websites, such tools would guarantee that an ad will not insert a drive-by download that would consequently install the malicious payload automatically. However, we recommend making exclusions for sites you want to support;
- Equip your accounts with two-factor authentication. No matter what techniques hackers would come up with, tho-factor authentication would almost always prevent the unauthorized access to all your accounts;
- Be careful when using Remote Desktop – never use a default port, and protect it with adequate and a complicated password;
- NEVER re-use passwords;
- Be more careful overall: do not click on phishing links on social media like Facebook Messenger, avoid suspicious sites, do not download software from unknown sources, do not pirate, etc.;
- Backup your data on a regular basis – this would negate the most damaging consequence of a ransomware infection.
You must terminate REvil ransomware from your computer before you attempt to recover your files
To many users, getting their files encrypted might one of the most terrible things that can happen, whether it is the days spent on working documents or precious family photos that cannot be recreated. Unfortunately, REvil decryption tool does not exist yet, as the threat is relatively new, and researchers require time to break a sophisticated code.
If you were thinking about whether you should pay the ransom, we advise you not to. Of course, REvil virus authors setting the 5-day timer is just a trick used to make users to pay the money as soon as possible. However, please rethink the consequences: the transferred Bitcoins would confirm that the illegal business works, so it will prompt hackers to continue. More importantly, you might not even get a working tool in return or receive one that does not work. Remember, they do not owe you anything, as criminals do not care about the well-being of their victims.
Therefore, you should rather remove REvil ransomware virus from your computer and then use alternative file recovery methods. Be aware that the malware strain is sophisticated and might disable anti-malware tools, or bypass their detection.
For that reason, you should enter Safe Mode with Networking – this environment is ideal for tackling problems related to the Windows OS, as well as eliminating even the most dangerous malware. From there, you should use anti-malware software such as FortectIntego, SpyHunter 5Combo Cleaner or another tool to terminate REvil ransomware and repair the virus damage. We explain how to do that below, so please follow the instructions carefully.
Once you perform a full REvil ransomware removal, you can attempt file recovery. If you had backups on an external drive such a Flash stick or backups on a virtual server, you could copy your files. If you did not have backups prepared, you should check our alternative solutions below. If that does not work, you will have to wait till the official REvil ransomware decryptor is released.
Getting rid of REvil virus. Follow these steps
Manual removal using Safe Mode
REvil or Sodinokibi ransomware is known to use sophisticated evasion methods and even disable anti-malware software. To prevent that, access Safe Mode with Networking to temporarily disable malware functionality:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove REvil using System Restore
System Restore can also be used to get rid of the virus (be aware that some ransomware variants might disable this feature):
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of REvil. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove REvil from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Malware authors ask for a significant amount of money for the decryption tool. Be aware that after paying criminals, you might never receive it, however, and lose not only your files but also the paid Bitcoins. Therefore, rather do not risk it and employ these methods that might help you retrieve at least some of your data:
If your files are encrypted by REvil, you can use several methods to restore them:
Data Recovery Pro might be successful when trying to restore data encrypted by REvil
While there is no guarantee that Data Recovery Pro will help you at all, there is a change of restoring at least some of your files. Please follow these steps:
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by REvil ransomware;
- Restore them.
Make use of Windows Previous versions feature
Windows Previous Versions feature is a relatively simple tool to use but is only available if System Restore feature enabled prior to the malware attack. Additionally, this method would allow you to restore files one-by-one so that a full recovery might be impossible.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
In some cases, ShadowExplorer is the answer
ShadowExplorer would work if REvil failed to delete Shadow Volume Copies/
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
REvil decryptor is currently unavailable
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from REvil and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Pierre Cadieux, Colin Grady, Jaeson Schultz and Matt Valites. Sodinokibi ransomware exploits WebLogic Server vulnerability. Cisco Talos. Security research blog.
- ^ Oracle Security Alert Advisory - CVE-2019-2725. Oracle. Official website.
- ^ Elliptic-curve Diffie–Hellman. Wikipedia. The free encyclopedia.
- ^ Catalin Cimpanu. Sodinokibi ransomware is now using a former Windows zero-day. ZDNet. Technology News, Analysis, Comments and Product Reviews.
- ^ Tom Bonner. #Sodinokibi #ransomware leveraging CVE-2018-8453 and heaven's gate to escalate privileges. Twitter. Social network.
- ^ Brian Krebs. Is ‘REvil’ the New GandCrab Ransomware?. Krebs on Security. In-depth security news and investigation.
- ^ Viruset. Viruset. Cybersecurity advice from Norway.







