Nemty ransomware (Removal Instructions) - May 2020 update
Nemty virus Removal Guide
What is Nemty ransomware?
Nemty ransomware is a crypto-malware most variants of witch are not decryptable due to AES-256 key scheduling bugs along with CBC block mode implementation
Nemty ransomware is a malware strain that researchers spotted in mid-August 2019 spreading via exposed Remote Desktop connections. The virus uses a combination of sophisticated encryption algorithms to lock up pictures, music, videos, and other files and appends .nemty, ._NEMTY_[random 7 characters]_, or ._NEMTY_[random 7 characters]_! extension to each of them. It even uses the never-before-seen in use RSA-8192 algorithm to achieve the goal of changing the original code of various common files found on the machine.
After locking all personal data, Nemty virus then drops a ransom note NEMTY-DECRYPT.txt, which explains that users need to visit a particular Tor site, upload a configuration file that is loaded by the ransomware on the host machine, and then pay the ransom of 0.099 BTC (which is approximately $1,000 at the time of the writing). It additionally can provide contact emails for victims that can be used to reach malware developers to get an opportunity to pay. However, neither contacting criminals nor paying the ransom is recommended.
On October 10, 2019, security researchers from Tesorion released great news to Nemty ransomware victims – a new decryptor is ready for them to use for free.[1] While not all versions and all file types are currently decryptable, the security team is working on the decryption tool improvement and is planning to release a tool that works for Nemty ransomware 1.5 (all variants up to 1.4 and 1.6 are decryptable).
However, a month or so after that, the new Nemty version got released with the self-named ransom note stating about Nemty Revenge 2.0 ransomware attacks. This was the updated release that is not possible decrypt. The more recent variant was spotted in April 2020 with slight alterations: removal of the contact email option entirely; personalized extension and ransom note patterns with NEMTY and unique string from ransom characters.
These .NEMTY_[random] patterns were introduced before and newer versions rely on a similar template changing the underscore to a common dash before the ID of the victim. Ransom note text in NEMTY_[random_string]-DECRYPT.txt is also not much different from previous messages and offers test decryption, includes Tor browser URL and promises that victims data affected by NEMTY REVENUE 3.1 can be completely recovered with the offered decryption tool.
Less than a month after Nemty Revenge 2.0 release, at the beginning of May 2020, cybersecurity experts[2] detected a new Nemty Special Addition ransomware campaign. This time, criminals are targeting South Korean users with a double combo of ransomware and Vidar info-stealer. The payload is actively distributed via spam email attachments. The virus appends .NEMTY_AJORCUS file extension and drops a NEMTY_AJORCUS-DECRYPT.txt note. The current version is relying on AES-128-CTR and RSA-2048 encryption algorithm, which currently cannot be deciphered.
| Name | Nemty ransomware |
|---|---|
| Type | Cryptovirus |
| Also known as | NEMTY PROJECT |
| Cipher used | AES-128, RSA-2048, RSA-8192 (the latter being quite an unusual algorithm and possibly never used by ransomware authors previously) |
| Ransom note | NEMTY-DECRYPT.txt, _NEMTY_[random 7 characters]_-DECRYPT.txt, NEMTY_[random string]-DECRYPT.txt, NEMTY_AJORCUS-DECRYPT.txt |
| Ransom amount | The amount is revealed for each victim after the contact initiation and can go up to $1,000 in Bitcoin |
| Distribution | Trojans, exploit kits (Rig and Radio), unprotected RDP, spam email attachments infected with macros[3], fake PayPal sites, etc. |
| File marker | .nemty, ._NEMTY_[random 7 characters]_, or ._NEMTY_[random 7 characters]_!, .NEMTY_[random], .NEMTY_AJORCUS |
| Infection exemption | In the latest versions, Nemty retreats without infecting users from Russia, Belarus, Ukraine, Kazakhstan and Tajikistan, Azerbaijan, Armenia, Kyrgyzstan and Moldova |
| Elimination | Get the anti-malware tool and remove Nemty ransomware completely. Use FortectIntego for virus damage removal and system function repair |
| File recovery | Free decryption may be possible with the help of security researchers from Tesorion – contact details here. Unfortunately, Nemty variant that goes after 1.6 version, are not currently decryptable, although at least some of the data may be restored with the help of our guidelines in the recovery section below |
While the developers of JSWorm ransomware took the responsibility of Nemty ransomware project development (which is currently still in progress),[4] security researchers from Fortinet[5] discovered that a link in binary extracted from malware sample was also used by a notorious GandCrab before its developers announced the retirement in June 2019, after an extremely successful year and a half of operation. Nevertheless, no other similarities between the two malware families were found by experts.
Since its initial debut, the malware already managed to reach headlines of multiple security news sites several times, and for a reason. Besides using RDP, RIG[6] and Radio[7] exploit kits, fake PayPal websites[8], and other sophisticated methods for propagation, it also has multiple interesting features.
Nemty ransomware also uses strange clues in its code, gathers additional details about users from Russia and other four countries, has a process and service kill function,[9] a mutex called “hate,” and, oddly, includes a link to a picture of Vladimir Putin which also contains a vulgar pun.
Regardless of its features, the most devastating one is file encryption, and, as the decryption tool has not yet been developed by the security community, it might result in permanent data loss to victims. Nevertheless, users should hurry up and remove Nemty ransomware with the help of security tools like SpyHunter 5Combo Cleaner, Malwarebytes, or any other anti-malware software that detects this computer threat.[10]
As for Nemty ransomware file recovery, users should try a free decryption help from Tesorion, use third-party tools or Windows Previous Versions feature. For more detailed instructions, please check the recovery section below.
Nemty ransomware operation analysis
Just like many other ransomware viruses, Nemty Project targets random computer users, as the infection is based on vulnerable systems. Before beginning the infection process, the malware checks if the victim is from Russia, Belarus, Ukraine, Kazakhstan, and Tajikistan using the command “isRU.”[11] However, this check is not used to prevent users from these countries from being infected, but rather for information gathering as it collects the following information to the attackers:
- Username;
- Computer name;
- Computer ID;
- Operating system.
In the later versions, however, the check process was changed: four more countries were added to the list (Azerbaijan, Armenia, Kyrgyzstan, Moldova) and, instead of gathering the information about the victims from these countries, Nemty retreats without infecting them.[12]
Nemty ransomware uses the base64 encoding process along with the RC4 encryption algorithm to obfuscate its execution, preventing it from being detected by multiple security tools. Nevertheless, AV engines now recognize most of the malware's variants, so it is vital to run a comprehensive security application at all times in order to prevent the infection.
Security experts at Fortinet found several bugs within the encryption process of Nemty file virus. For example, a coding line “boot.ini” is loaded twice, which is a mistake. Also, the way the encryption algorithm looks for particular extensions to encrypt is quite unusual and, as called out by researchers “rather inefficient.” These defects led the Fortinet team to believe that Nemty ransomware is still in the early development stages. However, it does not diminish the impact this malware can do to the infected victims' computers and files.
Nemty Project ransomware also generates a configuration file for every victim that needs to be uploaded to the Tor site specified in the ransom note. The introduced file stored in JSON format and placed into %USERPROFILE% folder – it can give all the details about the victim the hackers might need. It includes IP address, country, computer name, user name, malware version, operating system, etc.
The stored data also includes a UserID entry, which most likely refers to the affiliate ID. This leads to the conclusion that Nemty Project might be using the affiliate program known as Ransomware-as-a-Service (RaaS), which was also used by hacking groups like Pinchy Spider – a gang that released the notorious GandCrab ransomware.
Besides file encryption process, Nemty virus also deletes Shadow Volume Copies, modifies Windows registry, runs PowerShell commands, creates new mutexes, establishes TCP[13] connections, etc.
The latest variant of Nemty ransomware (1.4) allows the attackers to shut down several processes and services in order to encrypt files that are currently in use. It includes MS Word, MS Excel, Outlook, WordPad, SQL, VirtualBox, and others. VirtualBox is an open-source multi-platform application used by various corporations, and its shut down might indicate that companies are also a valid target for Nemty Project creators.
Tesorion cybersecurity researchers may provide free decryption solutions for Nemty ransomware victims
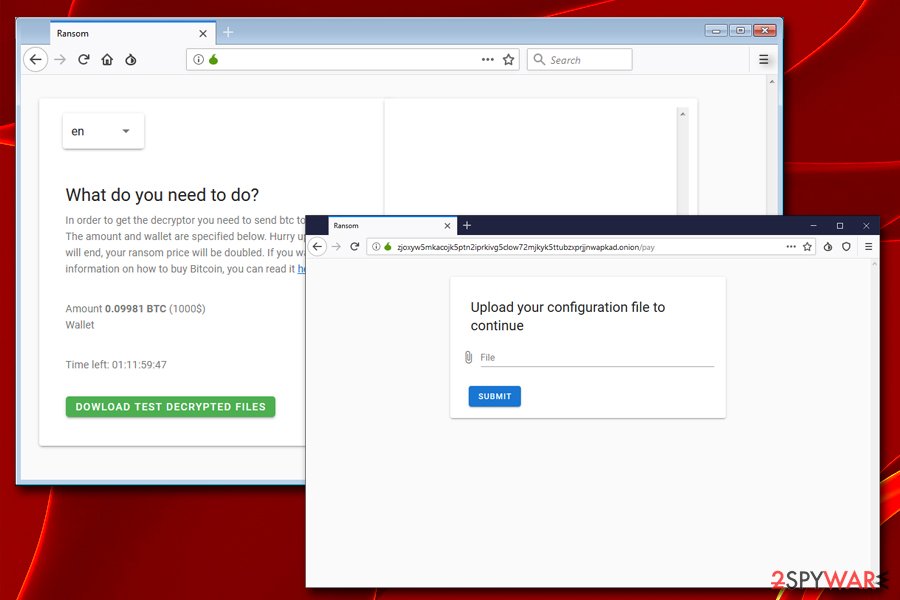
Nemty ransomware demands payment immediately after file encryption and displays the extortion message in a text file, which brings users to the Tor site zjoxyw5mkacojk5ptn2iprkivg5clow72mjkyk5ttubzxprjjnwapkad.onion/pay. Nemty virus authors use Tor for communication with the victims due to the anonymity aspect the platform provides – it became a trend among the most prolific malware developers. There, victims are asked to upload the encrypted configuration file found in C:\Users\admin directory.
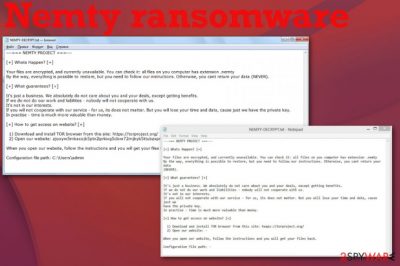
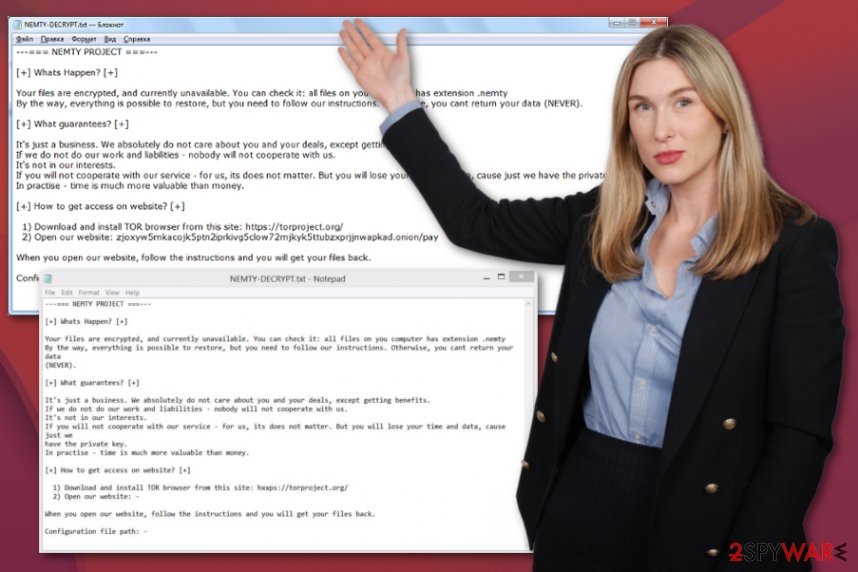
NEMTY-DECRYPT.txt is the ransom note file that shows the initial message informing about the attack and encryption:
—=== NEMTY PROJECT ===—
[+] Whats Happen? [+]
Your files are encrypted, and currently unavailable. You can check it: all files on you computer has extension .nemty
By the way, everything is possible to restore, but you need to follow our instructions. Otherwise, you cant return your data (NEVER).[+] What guarantees? [+]
It’s just a business. We absolutely do not care about you and your deals, except getting benefits.
If we do not do our work and liabilities – nobody will not cooperate with us.
It’s not in our interests.
If you will not cooperate with our service – for us, its does not matter. But you will lose your time and data, cause just we have the private key.
In practise – time is much more valuable than money.[+] How to get access on website? [+]
1) Download and install TOR browser from this site: hxxps://torproject.org/
2) Open our website: – zjoxyw5mkacojk5ptn2iprkivg5clow72mjkyk5t***zxprjjnwapkad.onionWhen you open our website, follow the instructions and you will get your files back.
Configuration file path:
Cybercriminals offer a free test decryption service that is meant to guarantee file recovery after the payment of $1,000 in BTC is transferred to them. However, nobody can guarantee anything when it comes to the criminal world, including the digital one. Nemty ransomware creators are working on a project that is designed to extort innocent users' money, and they do not care about the well-being of theirs.
Thus, there is no guarantee that paying the ransom will provide you the decryption tool. Besides, the action will only encourage criminals to develop the project further and infect more victims. Security experts[14] and infosec community advise not paying the ransom, although, in some cases, it might be the only choice victims have left.[15]
The good news is that Tesorion security experts released a free decryption tool that works for most versions of Nemty ransomware. Researchers managed to find bugs within the implementation of the AES-256 key scheduling and the CBC block mode implementation techniques. However, because Tesorion did not want to release the findings in case ransomware authors would find out about them, they opted to help each of the victims individually, offering the generation of the key on their servers instead of the host machines. This help was applicable for all variants released at the time – up to 1.4.
In the midst of this operation (Tesorion was very busy helping all the victims), Nemty ransomware 1.5 and 1.6 were released by cybercriminals. Because 1.6 was the newest variant, experts decided to start from it and develop a working tool. The decryptor for 1.5 is scheduled to be released a week after the initial release.
Nemty ransomware decryptor only works for the following file types:
avi, bmp, gif, mp3, jpeg, jpg, mov, mp4, mov, mp4, qt, 3gp, mpeg, mpg, doc, docb, dot, ole, pot, pps, ppt, wbk, xlm, xls, xlsb, xlt, pdf, png, tif, tiff, nef, , doc, txt, docm, docx, dotm, dotx, jar, potm, potx, ppsm, ppsx, pptm, pptx, xlsm, xlsx, xltm, xltx, zip
Tesorion team said that it is closely working with Europol to release the tool on its No More Ransom Project.
Alternatively, those infected with Nemty ransomware can instead try using alternative file recovery methods, such as third-party tools or Windows Previous Versions feature. Under certain circumstances, data retrieval can be successful, although it is relatively low. For details on all the solutions, please check the recovery section below.
Before trying to recover data, however, users should take care of Nemty ransomware removal. Otherwise, all the recovered data will be encrypted repeatedly, making the whole process worthless.
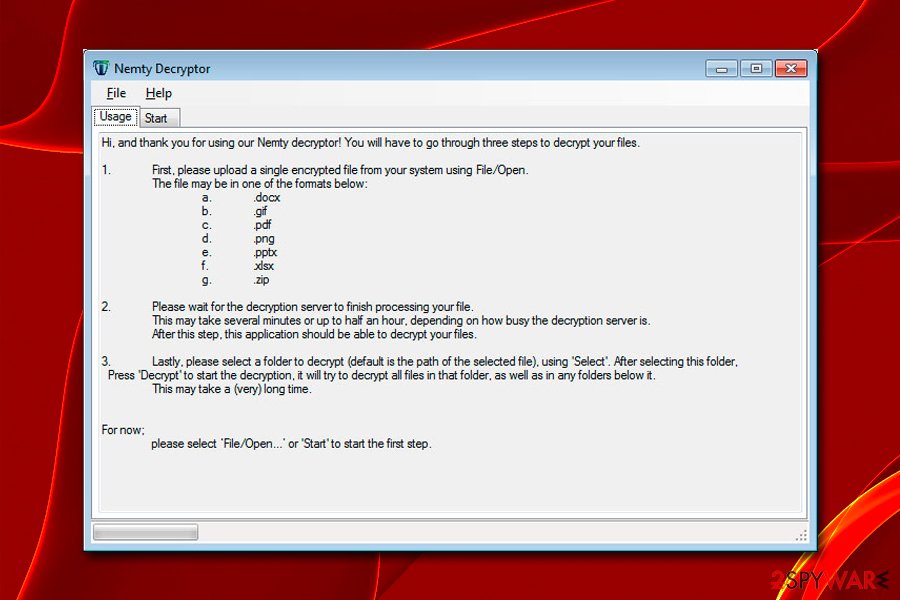
Nemty ransomware variants
There are many Nemty ransomware variants release by cybercrooks. As the malware is in state of development, such a scenario is nothing uncommon. Besides, bad actors are willing to patch possible bugs within the code in order to prevent researchers from working on Nemty ransomware decryptor.
Nemty ransomware 1.4
This variant was the one that researchers found the weakness inside Nemty ransomware's code. It used the ._NEMTY_[random 7]_ file extension to encrypt all data on the device and dropped a ransom note _NEMTY_[random 7]_-DECRYPT.txt. Researchers found that the dropped files by this variant include h0ecrnc4.exe zazuvu.pdb and risoceha.pdb. The executable file is dropped into C:\ Users\ Admin\ AppData\ Local\ Temp\ location, from where it is executed, and the encryption process begins. Nemty ransomware V1.4 fixed multiple bugs present in previous versions and was spread with the help of Radio Exploit Kit.[16]
Nemty ransomware 1.4 and below helped Tesorion experts to figure out more details about file decryption, and the tool is being improved each day thanks to that, decryption more file types in the process. While currently, the involvement of the CSIRT team is required for file decryption, experts promised to release a standalone decryptor that would work for this variant without experts' help.
Nemty ransomware 1.5
Nemty ransomware 1.5 was one of two variants that were released after security experts from Tesorion released the initial decryption tool. The AES bugs that helped security experts to release the previous decryptor are still present in this version, although researchers said that “other minor differences require some changes to our 1.4 decryption process.”
Just as its predecessors, Nemty 1.5 is mostly using RIG and other exploit kits for its propagation, although it is also likely that hackers opt for multiple distribution techniques. It uses the same encryption method – the encrypted files are changed as previously.
According to Tesorion researchers, they will be releasing a working decryption tool in the near future, so users who are affected by this variant should hurry with Nemty ransomware removal and wait for the decryptor to be released to recover data for free.
Nemty ransomware 1.6
Nemty ransomware 1.6 was distributed with the help of Quasar Remote Access Trojan and a MedusaHTTP DDoS botnet malware.[17] This is another version of the malware that was released after Tesorion announced the decryptor for 1.4 and prior variants of Nemty ransomware.
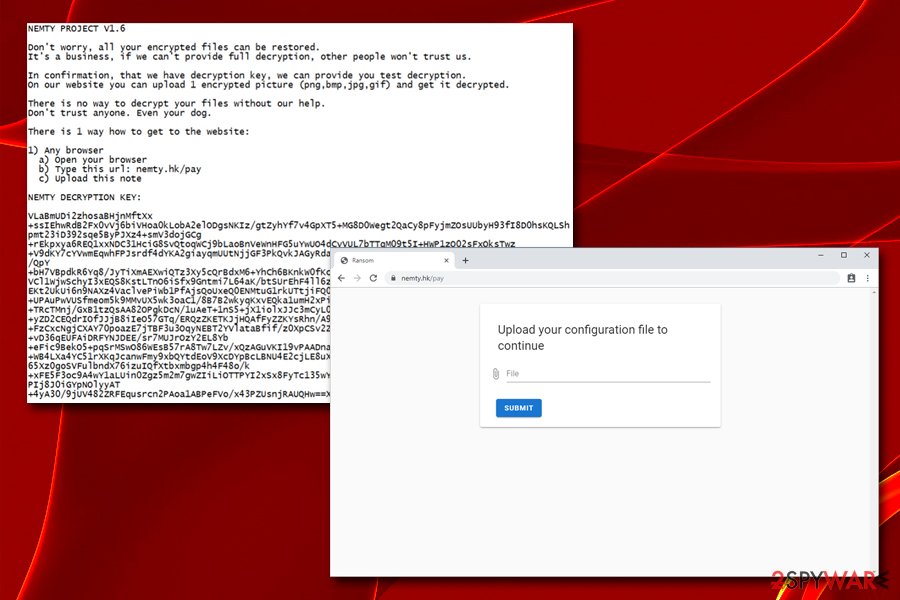
While the encryption methods and file markings did not change, there were changes made to the ransom note, which reads:
NEMTY PROJECT V1.6
Don't worry, all your encrypted files can be restored. It's a business, if we can't provide full decryption, other people won't trust us.
In confirmation, that we have decryption key, we can provide you test decryption. On our website you can upload 1 encrypted picture (png, bmp, jpg, gif) and get it decrypted.
There is no way to decrypt your files without our help.
There is 1 way how to get to the website:
1) Any browser
a)Open your browser
b) Type this url: nemty.hk/pay
c) Upload this note
V1.6 is currently decryptable (at least most of the file types are), so make sure you remove Nemty ransomware and then contact Tesorion security experts.
Nemty Revenge 2.0
Nemty Revenge 2.0 ransomware came out in the middle of November 2019 and creators released this version with the .NEMTY_xxxxxxx file marker example and a template of the ransom note – NEMTY_XXXXXXX-DECRYPT.txt. The XXX part stars for the particular victims' ID that is set for each affected device after the encryption procedure. This combination helps malware creators to indicate each separate person that is contacting them for decryption tools.
The name of the version comes from the ransom note that shows up at the first line fo the text file. This note also, as typically, includes contact emails, details about particular types of files that can get decoded for free as the 1 file test decryption. This is a common technique that criminals use when trying to fake trust and legitimacy. The previously released decryption tool was not working for the updated variant Nemty Revenge 2.0, so it is believed that the name at the start of the ransom note is because of the previous decryption tool development.
After this one, a few updated versions with the same ransom note and file extension details came out: Nemty Revenge 2.3 in January 2020 and Nemty Revenge 2.6 March 2020. These are not considered separate versions of NEMTY ransomware because the only alteration is the first line in the ransom note.
Nemty Revenue 3.1 ransomware
Yet again malware developers name their versions, so the one that came in April 2020 is called NEMTY REVENUE 3.1 ransomware in the ransom note. Similar patterns of forming file markers and the ransom-demanding text file still are used. Encoded data gets .NEMTY_[random string] at the end o the original file name and file type appendix. NEMTY_[random string]-DECRYPT.txt is a particular name that is unique for each affected device. criminals place their demands on this note.
The different method of contacting criminals was chosen, in this case, because developers want victims to visit the Tor browser website instead of writing the email via a particular address provided in the ransom note. But the URL is displayed on the short text message.
When you got to the provided URL screen display the form where you should upload the ransom note and encouraging message stating that you can recover all of your files with the help of these criminals. However, before you get the decryption tool you need to pay the ransom and the amount depends on the value and number of files encrypted int he first states of this attack.
=========================
NEMTY REVENUE 3.1
=========================
Your important files were crippled with with military grade algorithms (AES-128 & RSA-2048).
The only way to restore your documents and other files – buy private key.
We ensure that we will provide full-decryption after obtaining key.
Don't try to restore your files using 3rd party services, they will only corrupt your files.
=========================
Use following URLs:TOR (better): zjoxyw5mkacojk5ptn2iprkivg5clow72mjkyk5ttubzxprjjnwapkad.onion/public/pay.php
WWW (mirror): nemty.top/public/pay.php
Nemty Special Addition
Nemty project keeps proliferating presenting cybersociety with new variants almost every month. We had a variant called Nemty Revenge 3.1 in April 2020 and now, less than a month after its release, a new campaign was spotted on the landscape. This time, criminals are targeting a specific country – South Korea, which is actively bombarded by malspam attacks. Written in the Korean language, the emails trick potential victims to open a malicious attachment, which carries the obfuscated 전산 및 비전산자료 보존 요청서_20200506(꼭 자료 보존해주세요)1.exe file[18].
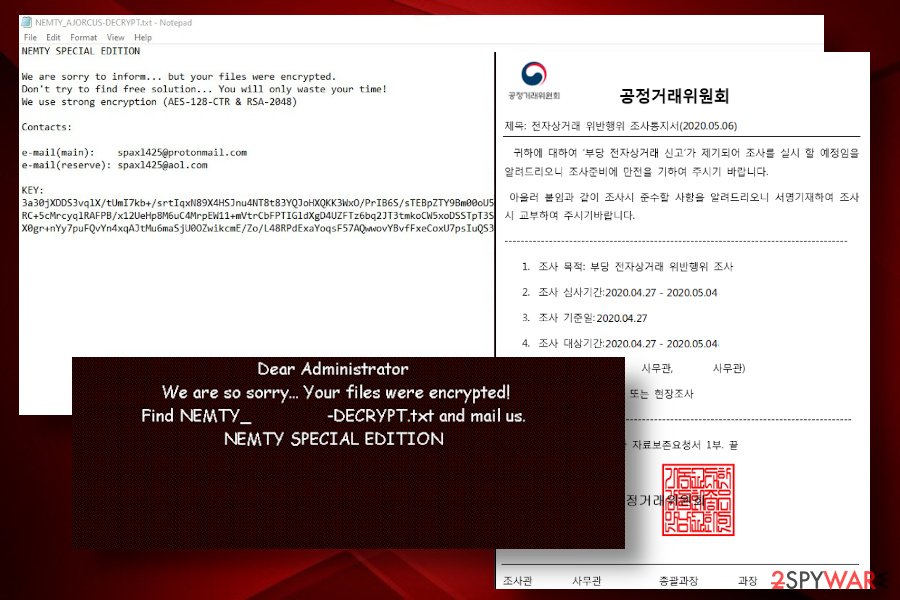
NEMTY SPECIAL ADDITIONWe are sorry to inform…but your files were encrypted.
Don't try to find free solution… You will only waste your time!Contacts
e-mail(main): splax1425@protonmail.com
e-mail(reserve): splax1425@aol.ltKEY
xxxxxxxxxxxxxxxxxx
Ransomware comes breaking through unprotected RDP and other ways
When compared the common distribution methods of ransomware, phishing emails that need to be opened and downloaded are not controlled by the attacker. Breaking through the RDP connection puts the attacker in control because the criminal can act immediately without waiting for the victim to take the phishing bait. This method of infection has been more prevalent in recent years, as more and more criminal gangs use it.[19]
To avoid being a victim of a brute-force attack, make sure you do not use the random RDP port 3389, which renders the machine vulnerable to special software that scans the internet and looks for such connections. Besides, the connection should also be secured with a strong password, and the RDP function disconnected as soon as it is not needed.
Additionally, users should watch out for spoofing websites such as PayPal that virus authors used to deliver the payload via the cashback.exe executable that had to be downloaded by the victims.
To avoid being a victim of exploits, users should also regularly update their systems, as Rig, for example, was patched by Microsoft three years ago. 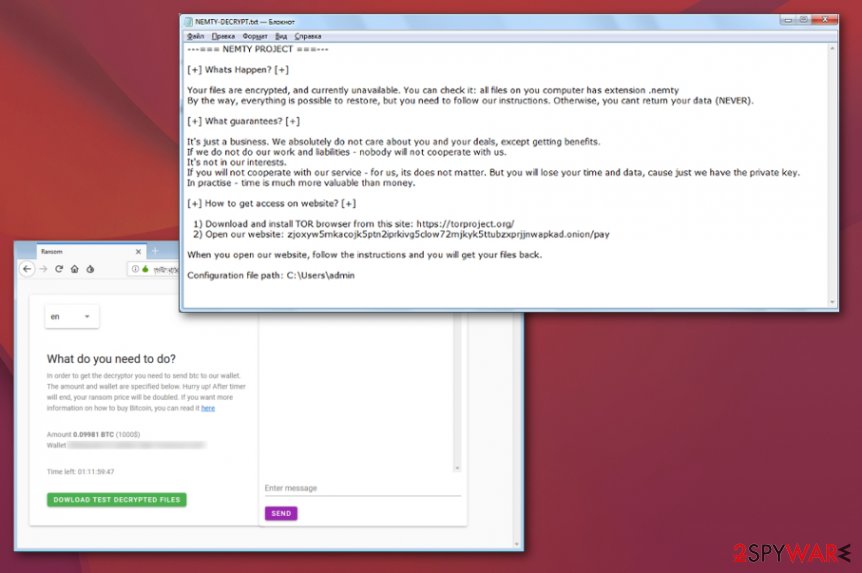
Eliminate Nemty ransomware from the system and only then attempt to get your files back
When people get affected by the malicious virus, all the files on the system get locked, which often results in a shock, as users no longer have access to their precious data. Due to this, some users hurry to pay the ransom and retrieve their files. Unfortunately, that is not the optimal choice, as it is better to remove Nemty ransomware and then use alternative methods to recover data.
For a comprehensive Nemty ransomware removal, you will need to install powerful anti-malware software, if you do not have one yet (which is a huge hole in your computer security!). You should then access Safe Mode with Networking in case the malware tampers with security program operation – we explain how to do that below. Once inside, perform a full system scan using SpyHunter 5Combo Cleaner, or Malwarebytes, or another reputable anti-malware.
Since Nemty ransomware virus and the most recent NEMTY REVENUE 3.1 ransomware version can interfere with various files int he system, including the ones that manage functions of the machine, you need help from FortectIntego or additional system tools that can find and fix such affected files, repair the PC fully.
Getting rid of Nemty virus. Follow these steps
Manual removal using Safe Mode
Reboot the machine in Safe Mode with Networking to eliminate Nemty ransomware completely without virus interuption
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Nemty using System Restore
System Restore is the feature that can recover the system in a previous state
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Nemty. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Nemty from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Nemty, you can use several methods to restore them:
Data Recovery Pro is the file restoring software that helps with encoded files
Nemty ransomware encrypted files or accidentally deleted data can be recovered with Data Recovery Pro
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Nemty ransomware;
- Restore them.
Try Windows Previous Versions as an alternative for data backupd
When System Restore gets enabled, you can try Windows Previous Versions as file recovery method
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer – a tool used for data restore
Unfortunately, Nemty ransomware deletes Shadow Volume Copies, so data decryption is barely possible
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Cotact Tesorion security researchers for Nemty file decryption
Security experts at Tesorion are actively working on Nemty ransomware decryptor. Currently most of the variants are decryptable, although not all file types are. For help, you need to contact Tesorion directly – you can find the contact details here.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Nemty and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Nemty ransomware based on analysis of its cryptography. Tesorion. Cybersecurity experts' blog.
- ^ GrujaRS profile. Twitter. Social network.
- ^ Macro virus. Wikipedia. The free encyclopedia.
- ^ Michael Marriott. Nemty Ransomware: Slow and Steady Wins the Race?. Digital Shadows. The Leader in Digital Risk Protection.
- ^ Joie Salvio. Nemty Ransomware 1.0: A Threat in its Early Stage. Fortinet. Ransomware threat analysis blog.
- ^ Nemty ransomware is distributed via RIG exploit kit. Cyware. Real Time Cyber Security Products and Alerts.
- ^ nao_sec. Hello again! #RadioEK is dropping #NEMTY Ransomware. Twitter. Social network.
- ^ David Bisson. Fake PayPal Website Distributes New Variant of Nemty Ransomware. Tripwire. The state of security.
- ^ Bill Toulas. Nemty Ransomware Evolving to Kill Processes and Services. TechNadu. Technology news, reviews and roundups.
- ^ 267a9dcf77c33a1af362e2080aaacc01a7ca075658beb002ab41e0712ffe066e. Virus Total. File and URL analyzer.
- ^ Nemty Ransomware Possibly Spreads Through Exposed Remote Desktop Connections. Trend Micro. Security blog.
- ^ Vitali Kremez. Same version "1.4" but new additions. Twitter. Social network.
- ^ Margaret Rouse. TCP (Transmission Control Protocol). SearchNetworking. Networking information, news and tips.
- ^ Virusi. Virusi. Spyware related news.
- ^ Larry Dignan. Ransomware attacks: Why and when it makes sense to pay the ransom. ZDNet. Technology news and cybersecurity reports.
- ^ Vitali Kremez. This is same the #Nemty #ransomware {version 1.4}. Twitter. Social Network.
- ^ mol69. #NEMTY v1.6(#Ransomware) & #Quasar & #MedusaHTTP & Unknown(Tor). Twitter. Social Network.
- ^ 전산 및 비전산자료 보존 요청서_20200506(꼭 자료 보존해주세요)1.exe. Virus Total. File and URL analyzer.
- ^ Jakub Křoustek. Ransomware attacks via RDP choke SMBs. Avast. Security blog.





















