Cyber_Puffin ransomware (Free Guide)
Cyber_Puffin virus Removal Guide
What is Cyber_Puffin ransomware?
Cyber_Puffin ransomware attacks Windows systems and locks all files on them
Cyber_Puffin is a ransomware-type virus that specializes in data locking and money extortion. The plan of cybercriminals behind it so to hold all the files on the system hostage until the ransom is paid by the victim. Ransomware is considered to be one of the most dangerous malware types out there, so if you happen to be a victim, you should read through all the information below to make sure you deal with it correctly.
Ransomware operation
On the system, the virus would encrypt[1] photos, videos, music, documents, databases, and other important files using a powerful encryption method to render the data completely useless. Each of your personal files is given the “.Cyber_Puffin” extension during this phase, and all the default icons are stripped away and replaced by blanks.
It's important to understand that files encrypted by ransomware are not actually corrupted, even though they might appear that way. They're just locked with a special password made up of a long string of characters. And there's no way to guess it or get it any other way – the only people with access to the right password are the criminals themselves.
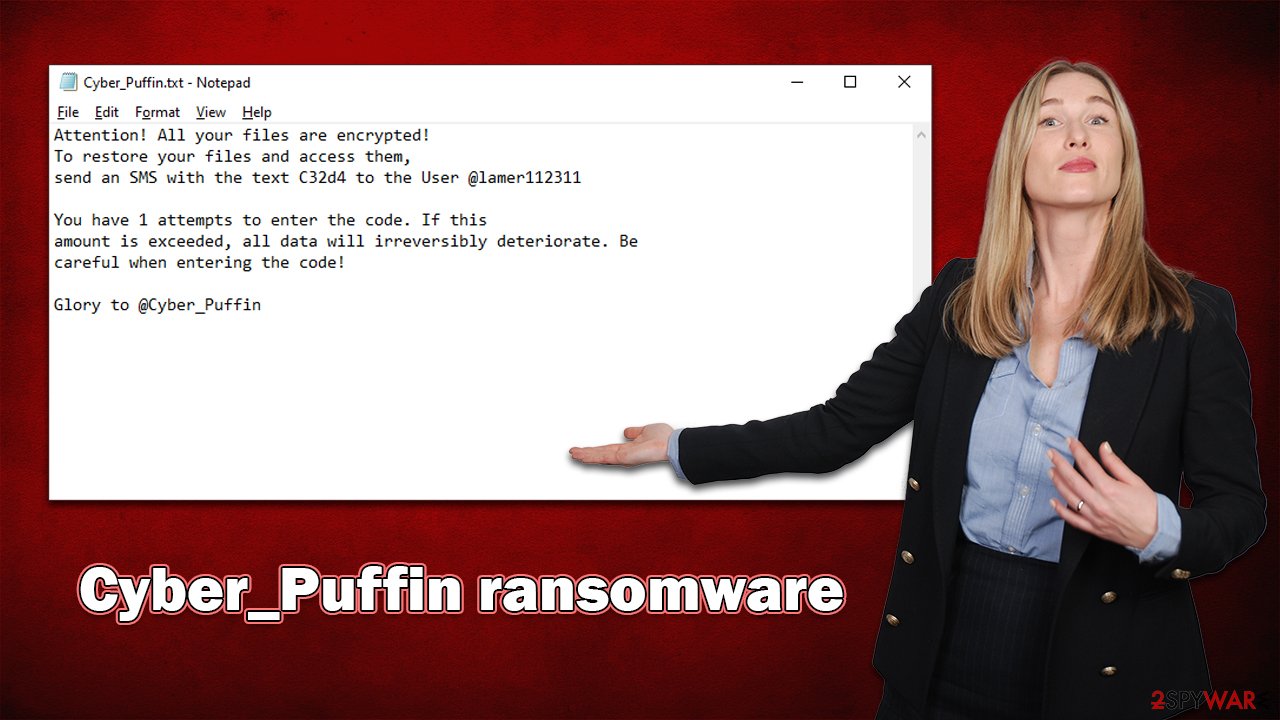
It is unsurprising that the creators of the ransomware are not willing to provide the decryption key for free and instead demand a ransom be paid. According to the ransom note (Cyber_Puffin.txt) dropped on users' desktops, victims should contact @lamer112311 on Telegram.
| Name | Cyber_Puffin |
|---|---|
| Type | Ransomware, file-locking malware, cryptovirus |
| File extension | .cyber_puffin, appended to each of the non-system and non-executable files |
| Ransom note | Cyber_Puffin.txt |
| Contact | @lamer112311 |
| Data Recovery | If no backups are available, recovering data is almost impossible. However, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Malware removal | Manual virus removal is not recommended, as it might be difficult for regular users. Instead, SpyHunter 5Combo Cleaner or other anti-malware tools should be used |
| System fix | Malware can seriously impact a Windows computer's performance and stability after it is removed. We recommend scanning the system with FortectIntego to remedy it and avoid significant stability issues |
Ransom note
The fundamental objective of ransomware isn't to damage the system but rather to change user files in such a way that they are unrecoverable. With the aid of this technique, hackers may now demand money from victims – ransomware has emerged to be a very lucrative market with thousands of strains baiting on the internet.
A ransom note provides essential information to users who have had their files taken hostage, such as what happened and how to retrieve the files. Most importantly for cybercriminals, the note also includes contact details, as victims would not know who to contact or how to pay. Here's the message from the crooks behind ransomware:
Attention! All your files are encrypted!
To restore your files and access them,
send an SMS with the text C32d4 to the User @lamer112311You have 1 attempts to enter the code. If this
amount is exceeded, all data will irreversibly deteriorate. Be
careful when entering the code!Glory to @Cyber_Puffin
Looking at the ransom note, it does seem to be almost identical to a few other threats we have recently spoken of, including 62IX and Virus Alert. While it does not prove a connection between this ransomware, it is likely to be the case. Data-encrypting malware is extremely lucrative, so it is not surprising that new variants show up constantly.
Do not attempt to negotiate with or contact malware authors; even if you pay the money they request, there is no guarantee that they will provide a decryption tool. Furthermore, by paying the ransom, you only indicate that their illegal scheme is effective and supports their efforts to create more ransomware and infect additional people.
Automatically remove malware from the system
When malware is installed on a PC, it can no longer be considered safe to use. The infection might spread via the network if such is accessible and even initiate other malicious software's installation. Crooks may also gain remote access to users' PCs under specific circumstances by utilizing a remote connection over the internet. Thus, losing this link is critical before proceeding any further with Cyber_Puffin ransomware removal.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Manual virus removal is possible but not recommended – security software is the better option. SpyHunter 5Combo Cleaner or Malwarebytes can be used to find and remove all malicious components from your system automatically. Security software should be your first line of defense against malware attacks; it's always best to try and avoid infection in the first place.
We strongly advise you to use the FortectIntego PC repair tool after the infection is gone. Windows system files might be damaged by malware, and security software may not be able to deal with it. As a result, users may experience system crashes, BSODs,[2] errors, and other common technical difficulties due to malware removal. The repair tool has the ability to replace damaged system files with fresh ones.
Attempt file recovery without paying
Many users think that once they scan their computer with security software, any encrypted files will be restored. However, that is not the case, as data encryption is usually permanent – at least until a unique key is used. Also, believing that the files are damaged or corrupted is incorrect as encryption does not actually damage files.
It's also not a good idea to contact criminals. Instead, there are other strategies that can assist you in recovering at least some of the lost data. Make sure you back up the encrypted files before continuing because altering them might render them unusable.
The first solution we propose is using third-party data recovery software which, under some circumstances (whenever the virus fails to delete Shadow Volume Copies,[3] for example), could restore the locked data.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Cyber_Puffin ransomware Cyber_Puffin ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
There are hundreds of security companies and organizations battling ransomware creators. In some cases, servers containing decryption keys have been seized, which allows the keys to be released to the public. Below you will find the most prominent parties involved in free data decryption services; these services have already helped millions of victims worldwide. Please keep in mind that an alternative decrytpion tool might take a while to create (if possible).
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Encryption. Investopedia. Sharper insight, better investing.
- ^ Chris Hoffman. Everything You Need To Know About the Blue Screen of Death. How-to Geek. Site that explains technology.
- ^ Shadow Copy. Wikipedia. The free encyclopedia.






