62IX ransomware (virus) - Free Instructions
62IX virus Removal Guide
What is 62IX ransomware?
62IX ransomware is a malicious program that locks all data on the system and then demands a ransom
62IX ransomware is a type of malicious software that is designed to extract money from its victims. Immediately after entry, it infects the systems and begins data-locking preparation. All photographs, documents, databases, videos, and other files are encrypted using a strong encryption algorithm and appended with the .62IX extension.
At this time, all the data becomes unreadable and inaccessible to users. When trying to open files, they would simply receive an error message saying that the file format is not recognized. Even if trying to use alternative applications to open a file, they would still have no success – this is because encryption is a secure method of locking data.
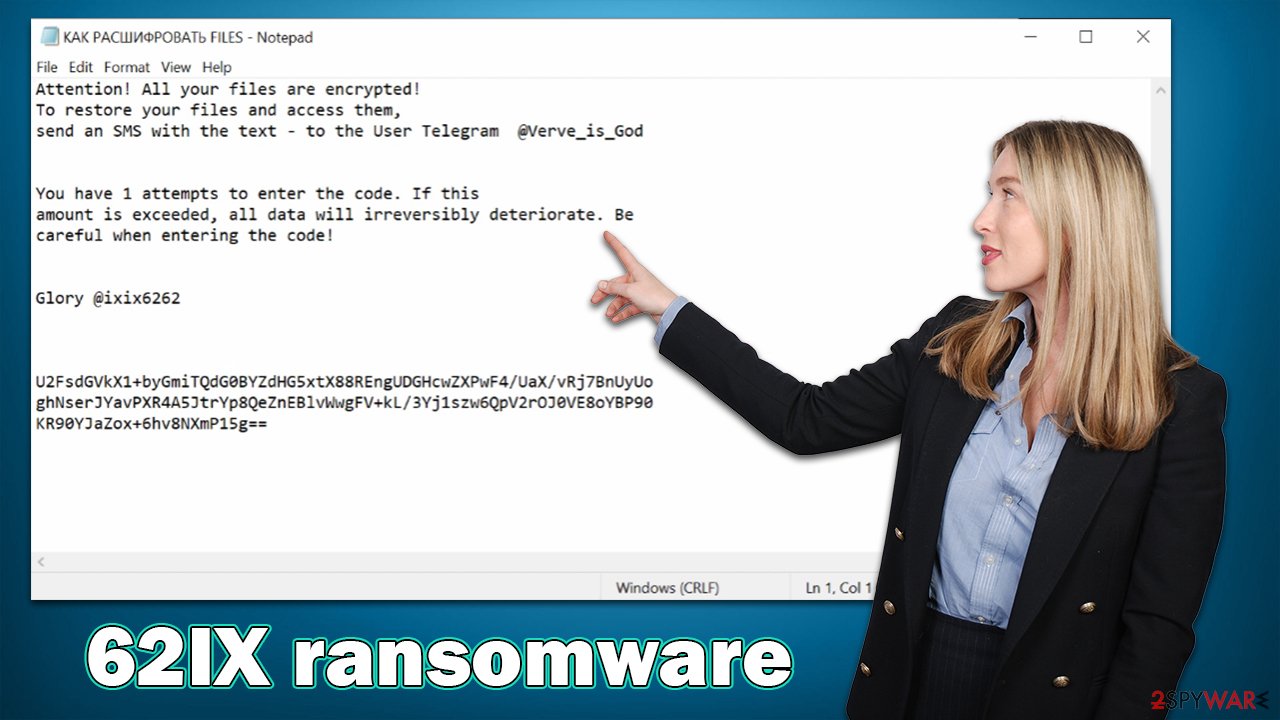
Once done, the 62IX virus would deliver a ransom note КАК РАСШИФРОВАТЬ FILES.txt, which is a small ransom note from the attackers. It claims that victims have to contact crooks via the Telegram account @Verve_is_God and pay the requested sum of money (likely in bitcoin) for a decryption key.
We do not recommend communicating with malicious actors, you may simply never be given the promised decryptor, even if you full all the demands. Instead of trusting cybercriminals, remove malware from your system and use alternative methods for data recovery – we provide all the information below.
| Name | 62IX virus |
|---|---|
| Type | Ransomware, data locking malware, cryptovirus |
| File extension | .62IX |
| Ransom note | КАК РАСШИФРОВАТЬ FILES.txt |
| Contact | @Verve_is_God (Telegram) |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| removal | Before proceeding with data recovery solutions, make sure you first scan your system with SpyHunter 5Combo Cleaner or another reputable anti-malware software |
| System fix | Even after the malware is eliminated, Windows systems may be harmed by it, resulting in problems such as crashes, delays, and other stability issues. We recommend scanning the operating system with FortectIntego to repair it |
Ransomware distribution and tips for avoidance
There are several ways how you could get infected with ransomware. Most commonly, cybercriminals employ several distribution methods, although some strains rely on just one. For example, spam email attachments remain one of the most common delivery methods for malicious payloads, where booby-trapped documents execute malicious code once opened. Links within malspam[1] may also be employed, so you should not interact with suspicious emails.
Torrents and other websites specializing in the distribution of software cracks and pirated applications are also extremely common, as those sites are often poorly regulated. In fact, some of them are created for the sole purpose of infecting people with all sorts of malware (they also made look like the original torrent sites).
In other cases, hackers take a more complex approach and rely on methods such as security vulnerabilities to deliver ransomware to users. This is why we recommend having the updated security software running on the system at all times and ensuring that the OS and all its applications are patched with the latest updates.
Ransom note
The ransom note is particularly important to crooks as it provides all the details relating to how payments for the decryption software can be made, so it pops up as soon as the data locking process is over. 62IX ransomware uses a Russian name of the note КАК РАСШИФРОВАТЬ FILES.txt, which means “How to recover files.txt,” although the note text is written in English and reads as follows:
Attention! All your files are encrypted!
To restore your files and access them,
Send an SMS with the text – to the User Telegram @Verve_is_GodYou have 1 attempts to enter the code. If this amount is exceeded, all data will irreversibly deteriorate. Be
careful when entering the code!Glory @ixix6262
We do not recommend contacting the attackers, as they may never send you the correct key. We also advise you not to concern yourself with what the message says in the first place and remove the virus from the system, then use alternative methods for .62IX file recovery.
Virus removal and file recovery
Once ransomware finishes encrypting data, it immediately connects to a remote server ( known as Command and Control).[2] Crooks can use this to send additional commands for malware execution or even include extra payloads. Therefore, it's important that all affected machines are disconnected from the network and internet. Additionally, make sure you disconnect from cloud storage services such OneDrive.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center
- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
The disconnect from the network can prevent attackers from sending additional commands to malware. Since malicious actors make claims that the data may be immediately corrupted if incorrect code is inputted, we recommend you access Safe Mode before proceeding:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

In Safe Mode, the virus is temporarily disabled, and it can't affect the machine in any significant way (although files will remain locked in this mode too). Your first task here is to make sure that all malware is deleted from the device – scanning it with SpyHunter 5Combo Cleaner or Malwarebytes can assist you with that. Make sure you update the security software before using it.
Once 62IX ransomware removal is complete, you can now make backups of the encrypted data. Otherwise, any attempts to restore it might result in permanent file corruption, thus, you want it to be performed on copies rather than originals. Of course, you don't need to do this if you have backups of original files.
The first recovery option we recommend trying is third-party recovery software that may, in some cases, be useful with the recovery of at least some files.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Although ransomware programs vary in their sophistication, many contain bugs that can be exploited by cybersecurity researchers. By finding these bugs, researchers may be able to create working decryptors that victims can use for free. Keep in mind that this process might not always produce results, and even when it does, it may take some time. We recommend checking the following links for the decryptors regularly:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Other tips
Malware infections can be extremely devastating, especially when we are talking about ransomware, which effects can linger after the threat elimination. Regardless of whether or not you managed to restore your files, we recommend following a few tips that could help you in the future.
First of all, we recommend taking care of your system health, as malware can seriously damage it. Once infected, system files may get corrupted, and antivirus would simply not be able to deal with it. Specialized software such as FortectIntego could easily help you in such a situation – it replaces corrupted files with working ones, remediating issues like Blue Screens,[3], registry errors, and similar stability issues.
Malware assaults are taken very seriously by the authorities, who constantly fight against them. You may assist authorities in capturing the offenders by reporting the incident to responsible parties. The following resources might be useful:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Malspam: A simple and traditional attack technique that continues to be favorite among bad actors. Cyware. Threat Intelligence Solution.
- ^ Command and Control [C&C] Server. Trend Micro. Security research blog.
- ^ Blue screen of death. Wikipedia. The free encyclopedia.
