Dkey ransomware (virus) - Free Guide
Dkey virus Removal Guide
What is Dkey ransomware?
Dkey ransomware is a malicious computer virus that locks personal files and prevents users from opening them until a ransom is paid
Dkey is a type of malware known as ransomware, the purpose of which is to extract money from innocent victims. After accessing the Windows system silently (usually via spam emails or cracked software installers), it begins the encryption process and appends the .dkey extension to every personal photo, document, database, etc. This renders all files useless, meaning that owners are unable to modify or even open them.
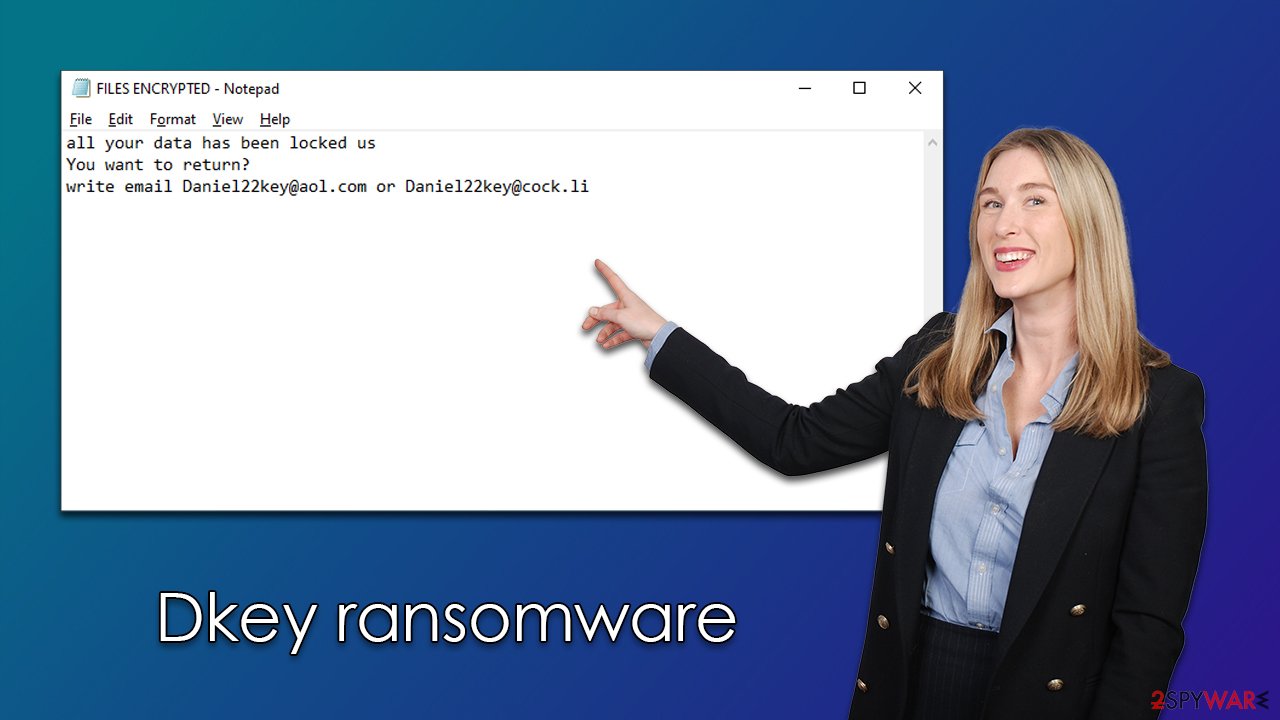
After finishing encryption, malware delivers FILES ENCRYPTED.txt and a pop-up window, both of which are used to provide information on what victims should do to recover access to files. Apparently, they need to write an email to Daniel22key@aol.com or Daniel22key@cock.li and pay a ransom in bitcoin to retrieve the decryptor. We don't recommend doing so, as crooks may never fulfill their promises, resulting in money loss and file loss.
| Name | Dkey |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .id-ID.[Daniel22key@aol.com].dkey |
| Malware family | Dharma |
| Ransom note | FILES ENCRYPTED.txt and a pop-up window |
| Contact | Daniel22key@aol.com or Daniel22key@cock.li |
| File Recovery | The only secure way to recover data is through backups. If such isn't accessible, or if it has been encrypted, recovery alternatives are extremely limited; we'll go over all of them below |
| Malware removal | Remove the computer from the network and the internet, then run a comprehensive system scan using SpyHunter 5Combo Cleaner security software |
| System fix | If malware is installed on your system, it could potentially delete or damage vital system files, which often leads to crashes, errors, and other stability issues. You can use PC repair FortectIntego to fix any of these problems automatically |
The ransom notes and what to do next
The Dkey virus stems from a well-established malware family known as Dharma. It's been around since at least 2016, so cybercriminals operating it had quite a bit of experience over the years. Maybe because of that, so many new variants regularly emerge, including those we discussed already, e.g., Iq20, Gnik, or MLF.
This malware always delivers a set of ransom notes – one comes as a typical TXT file, while the other shows up as a pop-up window. The pop-up window is the more important one (and it's unsurprising considering its visibility), as it details more information about the attack:
YOUR FILES ARE ENCRYPTED
Don't worry,you can return all your files!
If you want to restore them, follow this link:email Daniel22key@aol.com YOUR ID
If you have not been answered via the link within 12 hours, write to us by e-mail:Daniel22key@cock.liAttention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
This note also claims that users should not rely on alternative data recovery methods, which is not surprising considering that hackers have all the incentive to do so, as they simply want to get paid. We highly recommend not communicating with the attackers, as it would only confirm to them that their illegal business actually works.
Instead, check out the details below that would help you remove Dkey ransomware from your system and then attempt to recover files using alternative methods.
Remove malware and recover data without paying
It's crucial to follow the right steps while battling ransomware since failing to do so might reduce the likelihood of data being restored to its original state. When dealing with malware, your first task is to get rid of it, copy any encrypted data, and then try data restoration.
The first thing you need to do is make sure all the compromised PCs have the virus removed. You only need to worry about your personal computer if your device is not linked to a network. To disconnect it from the internet, simply pull the ethernet cable or disconnect your WiFi via the taskbar. Alternatively, follow these steps:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Some ransomware disappears after it finishes encrypting your files, so you might not find anything. However, that's not always the case since ransomware is often bundled with other malware which may continue stealing personal information or deliver additional payloads. Therefore, you should download and install SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable security software and perform a full system scan with it.
You can try to restore the encrypted data if you're confident that your computer is free of virus and ransomware infections. Paying hackers is a bad idea since, as we've already explained, you can lose your money in addition to your files. Before moving on, you should be aware of the following:
- Anti-malware scan will not restore your files, and they continue to be inaccessible;
- If no backups are available, it is crucial you make a copy of the encrypted files. Otherwise, you may corrupt them beyond repair;
- While the following decryption method might not be effective right now, it might be in the future if security experts discover vulnerabilities in the Dkey ransomware's encryption algorithm.
Thanks to the work of security experts, decryption solutions may potentially be developed for specific ransomware variants. In some circumstances, law enforcement agencies seize the servers of criminals, allowing the keys to be made public. Thus, you might find the following links useful:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

You shouldn't give up just yet if a decryptor is unavailable, as is frequently the case with emerging ransomware strains. The employment of specialized data recovery software is still feasible. Shadow Copies might remain on the computer after malware has been removed, making it possible to restore earlier versions of data. Data recovery software may restore at least some of your files:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Dkey ransomware Dkey ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Fix system damage
Windows is no longer the same after malware infection since some system files may get corrupted or even deleted. This can lead to system instability, which can contribute to crashes, failed application launches, BSODs,[1] and a variety of other problems. After removing the virus, if you are still experiencing these issues, apply recovery software as detailed below.
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
How to avoid and mitigate ransomware in the future
You might acquire ransomware in a number of ways. Most frequently, hackers use a variety of distribution strategies, however certain strains exclusively use one. For example, spam email attachments continue to be one of the most popular ways to send dangerous payloads. When opened, booby-trapped documents run malicious code. You shouldn't connect with strange emails since links inside malspam[2] may also be used.
Websites for the distribution of software cracks and pirated applications are also widespread, as those sites are frequently inadequately safeguarded. In reality, some of them exist simply to infect visitors with any number of malware (they also made it appear like real torrent sites).
In other situations, hackers use more complicated methods, such as security vulnerabilities,[3] to deliver ransomware to users. To protect your computer, we recommend that you always have updated security software running and that the operating system (OS) and all applications are patched with the latest updates.
The best protection against ransomware attacks is reliable data backups that should be held on a separate medium. For example, OneDrive or other cloud services could be used. Below you will find the instructions on how to create backups of your important files never to have a problem restoring them when the time comes.
Getting rid of Dkey virus. Follow these steps
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Dkey and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Chris Hoffman. Everything You Need To Know About the Blue Screen of Death. How-to Geek. Site that explains technology.
- ^ Malspam: A simple and traditional attack technique that continues to be favorite among bad actors. Cyware. Threat Intelligence Solution Company.
- ^ Thomas Holt. What Are Software Vulnerabilities, and Why Are There So Many of Them?. Scientific American. Science Magazine.





















