Gnik ransomware (virus) - Free Guide
Gnik virus Removal Guide
What is Gnik ransomware?
Gnik ransomware is a malicious computer virus that tries to extort money from innocent users
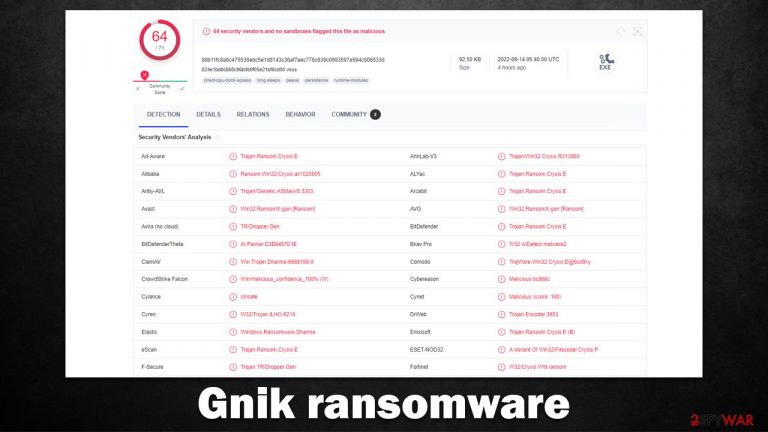
Gnik is a ransomware-type malware that you could infect your system with without intending to do so. However, once the infection settles, there's no way not to notice its presence, as all the personal files on the system, such as important documents or valuable pictures, become encrypted.[1] This means that suchlike data is ciphered and can no longer be modified or even opened by its owners, which gives cybercriminals a pretense to ask for payment.
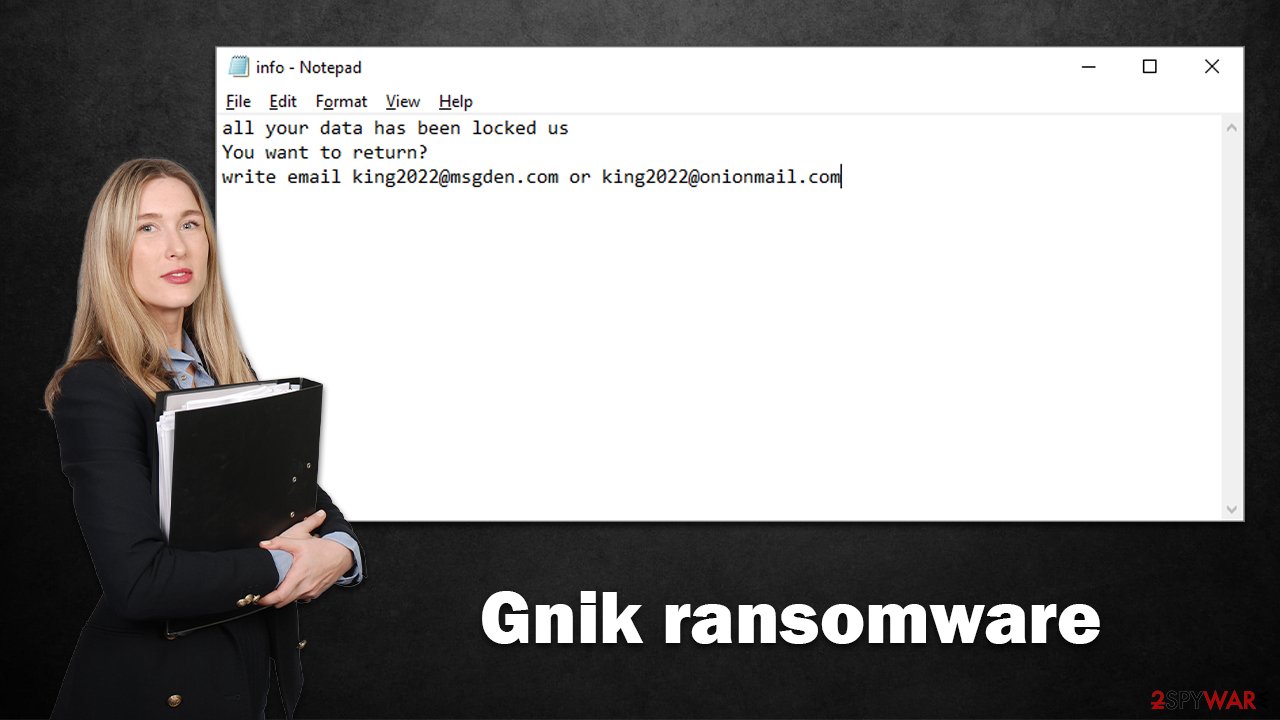
During the encryption process, the ransomware appends a .gnik extension to each of the files, along with the contact email (king2022@msgden.com) and a randomly-generated user ID. It also delivers a ransom note info.txt and shows a pop-up window that explains to users what has happened to their files and how to allegedly restore them.
However, contacting Gnik ransomware developers is not recommended, as they might fail to fulfill their promises and never deliver the key meant to help to decrypt files, or it may simply not work. You should instead follow an alternative route of trying to restore files using the methods we provide below (only after malware removal).
| Name | Gnik ransomware |
|---|---|
| Type | Ransomware, data locking malware, cryptovirus |
| Family | Dharma |
| File extension | .ID.[king2022@msgden.com].gnik |
| Ransom note | info.txt and a pop-up window |
| Contact | king2022@msgden.com and king2022@onionmail.com |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| removal | Before proceeding with data recovery solutions, make sure you first scan your system with SpyHunter 5Combo Cleaner or another reputable anti-malware software |
| System fix | Malware can wreak havoc on Windows systems, causing errors, crashes, lag, and other stability issues even after it is terminated. To fix the operating system, we recommend scanning it with the FortectIntego repair tool. |
The two notes
Gnik virus stems from a very established ransomware family known as Dharma, which first surfaced in the cybercriminal landscape back in 2016. Since then, malware authors have released hundreds of versions, many of which we have discussed on our website before – K1ng, Zxcvb, or NMO are just a few examples.
As a general rule, malware authors attempt to make sure that users find out about payment and contact details, as there's no other way that they would receive the money. This is probably why cybercriminals, in this case, deliver two ransom notes – in a text file and a pop-up window. Most commonly, ransomware usually uses TXT files for ransom notes, though.
Gnik ransom note does not differ much from many other members of Dharma, with a pop-up window providing a more detailed description of what to do next:
YOUR FILES ARE ENCRYPTED
1024
Don't worry, you can return all your files!
If you want to restore them, write to the mail: king2022@msgden.com YOUR ID
If you have not answered by mail within 12 hours, write to us by another mail:king2022@onionmail.com
ATTENTION!
We recommend you contact us directly to avoid overpaying agents
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
The text file does not provide any additional information, it's just a brief message which includes cybercriminals' contact emails. Nonetheless, we do not recommend contacting the attackers using any communication means, as they might never provide the promised decryptor, even after the payment is made.
Gnik ransomware removal and data recovery
Understandably, users may feel an immediate sense of panic when they can no longer access their files because ransomware has locked them. However, this reaction cannot fix anything because the infection has already occurred. In fact, panicking may cause victims to make mistakes which could lead to even more data loss. To avoid additional damage, it is important to follow some crucial steps in order.
1. Disconnect from the network before performing a malware scan
Cybercriminals generally use a remote connection established with the infected Windows computer through what is known as a Command & Control[2] server. Because the connection takes place over the internet, it's critical that the computer be totally disconnected from any network. Here's how to achieve this quickly:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
After your computer can no longer connect to the internet, it's time to remove Gnik ransomware from your system, and for that, we recommend using SpyHunter 5Combo Cleaner or Malwarebytes, two trustworthy antivirus programs. Antivirus software may locate and delete all harmful files at once, so you can be confident that your system is malware-free.
2. Attempt to recover your data
Because many people do not create proper data backups before being attacked by ransomware, they might permanently find themselves without access to their data. It's also a big risk to pay crooks since they may not follow through on their promises and never provide the required decryption software.
Even though this might sound like bad news, there is still hope – data recovery software could potentially help you in some cases (it varies a lot depending on the encryption algorithm used, whether ransomware was able to complete its programmed tasks, etc.).
Before proceeding, it is important to make copies of encrypted files that are valuable to you. Otherwise, recovery attempts may permanently damage locked data, and even a working decryptor would no longer be viable. Thus, grab a USB flash drive or similar storage and back up all important files.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Security researchers may even develop decryption tools for particular ransomware strains as a result of their research. In certain instances, law enforcement takes control of bad actors' servers,[3] allowing the keys to be published by the general public – reputable security companies generally do this. Here are some links that might help you:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

3. Fix system damage
If a computer becomes infected with malware, its system will operate differently than before. For example, an infection can alter the Windows registry database, damage essential boot-up, and other sections, delete or corrupt DLL files, etc.
If a vital system file is damaged by malware, antivirus software cannot fix it – meaning that users might experience performance issues, stability problems, and difficulty using their computers to the point where they have to reinstall Windows completely. Therefore, we recommend using reputable repair software that can easily remediate these issues:
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

4. Report to authorities
While this step is something most victims tend to skip, it is quite important in the grand scheme of things. With the help of the victims and detailed reports, authorities can trace the attackers in some cases, resulting in their servers being seized and keys being released to victims for free. Thus, if you had an unpleasant encounter with a ransomware infection, you should report it to your local authorities – these are a few links that could be useful:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Command and Control [C&C] Server. Trend Micro. Security solutions.
- ^ Encryption. Wikipedia. The free encyclopedia.
- ^ Justice Department Seizes and Forfeits Approximately $500,000 from North Korean Ransomware Actors and their Conspirators. Justice. The United States Department of Justice.
