DanaBot / Virus Removal Steps - May 2020 update
DanaBot Removal Guide
What is DanaBot?
DanaBot trojan gathers sensitive information from the infiltrated system and includes ransomware-type virus features
DanaBot Trojan started as a typical banking trojan and traveled through users' devices gathering sensitive data, planting other threats, and damaging machines. Later on, in 2019 the threat was upgraded and became a powerful threat that targets companies all over the world.[2] First targets were Australia, and some countries in Europe and malware evolved to modular malware that can download and launch DLL files, inject scripts on banking sites and steal information from various sites and the infected computer.
It is known that the DanaBot virus can manipulate browser sessions and redirect visits to financial services and steal credentials when users submit them to log in. Malware is capable of taking screenshots of the desktop, transfer all the stolen data to the C&C server that hackers control, and use such details to make fraudulent transactions, and steal money from banking accounts directly.
| Name | DanaBot |
|---|---|
| Type | Trojan |
| Targets | Australia and Europe are the most known targets where various info-stealing malware campaigns affected large businesses and companies |
| Tactics | Stealthy infiltration allows the malware to infect machines. Social engineering,[3] phishing emails and other methods allow the trojan to achieve these goals |
| Danger | The virus is capable of stealing sensitive information and making fraudulent transactions when online banking platform credentials get stolen |
| Distribution | Email attachments with malicious macros and scripts, websites with direct malware download functions provide the stealthy infiltration opportunities for the malware creators |
| Elimination | DanaBot removal requires proper tools because not all files and programs associated with the trojan can be found or seen, so anti-malware tools can detect and clear all the malware traces automatically |
| Repair | Some settings and features of the infected machine can get affected by the threat. Especially when system files and folders get affected and corrupted, so run FortectIntego for the best virus damage fixing results |
DanaBot trojan started with attacks targeting Australian banks, and other hackers managed to get the malware as a part of the affiliate system. When malicious actors use, rent or purchase the trojan they share profits with developers, and a team that created trojan in the first place can make a profit no matter what.
DanaBot trojan is compared to Zeus virus because it has many functions as a banking trojan and downloader components, including web injects that the Zeus is known for. It gets upgrades and is used for different purposes since the malware can be used as a tool of exfiltrating data. It is often using browsers and OS fingerprinting to deliver the fake website copies in the place of legitimate banking domains or e-commerce services.
It even masks C2 communications and requests updates by relying on the Tor module. DanaBot virus can target larger businesses and reduce the number of attacks while focusing on quality and choose to profile the victims' worth before running the malware. This is how attackers ensure to make more profit.
DanaBot malware upgrades revealed that threat included some capabilities besides those info-stealing functions:
- stealing browser client credentials;
- collecting logins to crypto wallet services;
- running a proxy on the infected machine;
- web injects;
- requesting updates via the Tor browser.
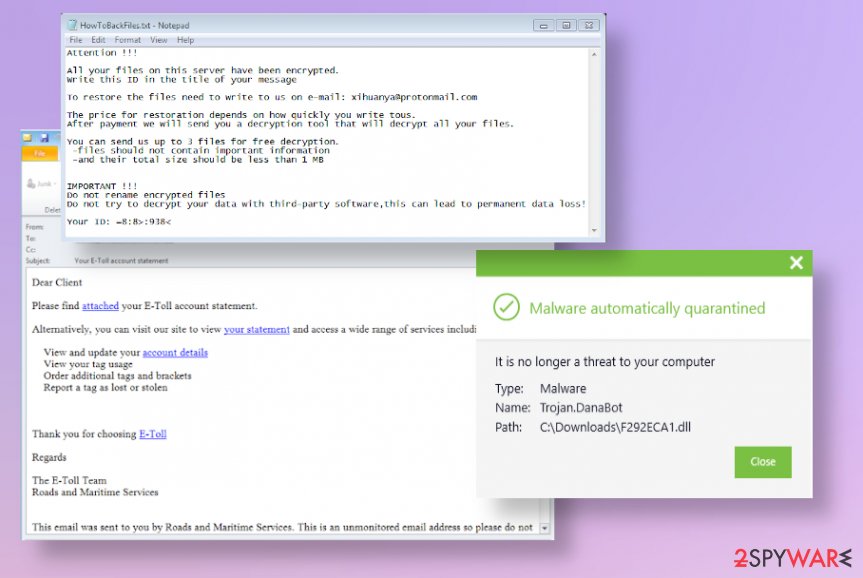
It also involved in ransomware-type campaigns when DanaBot encrypted files. Non-ransomware appended files using .non and .bkc extensions before dropping the HowToBackFiles.txt file containing the message for victims. At the time, this functionality was associated with Blitzkrieg ransomware activities.
When this not ransomware function affected files, DanaBot virus added files in system folders could trigger various processes. Malware can disable disk restoration, services, programs, monitoring software, and Windows Defender or other AV tools. Trojan can delete shadow copies and clear EventLog or different folders and directories. Ransomware can be designed to revive itself after the killing by adding the scheduled task using the modified Schtasks tool. At the time researchers explained:
The ransomware enumerates logical drives, visits all the directories except Windows, and encrypts all the files using AES128. The password is a string representation of the system volume serial number. Every file is encrypted in a separate thread.
DanaBot ransomware has a tool that can be launched as a decryptor that you can find here. 
DanaBot is the banking trojan that actively gets updates and techniques targeted towards avoiding the detection[4] and maintaining continuous operations. Attackers aim for financial gain, so financial rewards can be ensured when all the functions run uninterrupted. New tactics and operations can emerge, and since targets mainly are financial institutions and e-commerce, streaming services there are many places where the threat can spread and act further.
DanaBot malware is linked with other threats, and the relations were confirmed in the past, so same injection patterns and progression can show that this trojan will continue to be one of the most dangerous banking trojans in the future. Organizations should be aware of potential targeting and keep these malware campaigns in mind.
To avoid DanaBot removal, organizations can implement fraud detections within their web platforms. Detecting banking trojans and blocking fraudulent transactions can combat phishing attacks ant these fraud tactics that result in losses of money and sensitive data.
As for users that needed to remove DanaBot and fight malware on the machine, changing email addresses, logins and usernames on other platforms could be a great step once the system is cleared. Intrusion detection systems, anti-malware tools, and other antivirus programs are the best for the initial virus termination.
However, there are still issues with virus damage that is leftover after the DanaBot trojan attack. Affected system functions, damaged files or folders, and entries in places like Windows registries can create issues after the malware is terminated. Such alterations often happen to trigger detection avoidance and persistence of the threat, especially when it comes to ransomware-type viruses. Get a proper tool like FortectIntego for PC repair purposes and system optimization to find and fix issues with damage and changed settings.
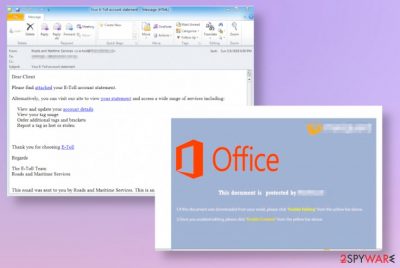
Phishing campaigns spreading malware via employee emails to networks of companies
Email campaigns circulate on the internet with subject lines claiming about invoices, e-tools, order information, and other details that help trick people into opening notifications and download malicious files without batting an eye. Microsoft Word attachments include macro viruses that get enabled by few clicks on the screen and triggers PowerShell or different functions to load malware payload directly on the system.
Then malware triggers all the processes, manipulates browser sessions, pulls other modules and inject sites, steals information without any symptoms created. The infection can be avoided, but not easily noticed if you do not pay attention to the email, sender, and topics of these emails.
When you notice any suspicious emails that you were not expecting to receive and notifications include file attachments or links you need to pay attention to other details because any red flag can indicate malicious behavior and purposes of the email, files included on it. Delete any suspicious messages and do not open files that you are not sure about. Financial-themed emails are not coming randomly from services and platforms, so do not fall for such tricks.
DanaBot trojan termination tips and precautionary measures listed
Since the DanaBot virus can run in the background unnoticed and unexpected it is more dangerous than any other threat. There are many functions in addition to banking trojan and password-stealing features, so full system cleaning is the only solution when dealing with this threat. Do not forget that even though these malware campaigns more targeted towards businesses, everyday users can also receive malicious emails with the trojan payload.
To avoid DanaBot removal in the future, you should have security or optimization tools like FortectIntego on the machine and run them more often, so all the issues, alterations, and damage can get fixed in time. This way there are no flaws in the system that attackers could exploit and spread their products.
When the process of DanaBot removal is inevitable, rely on proper tools, official providers, and sources that distribute SpyHunter 5Combo Cleaner, Malwarebytes, or any other reliable anti-malware tool. These programs can check various parts where the attackers planted their malicious scripts. In addition to the software, you can reboot the machine in Safe Mode with Networking, so the functions that get disabled can freely run, and your AV tool is not blocked.
Getting rid of DanaBot. Follow these steps
Manual removal using Safe Mode
When a threat is affecting the performance and disabling some functions, rebooting the PC in Safe Mode with Networking can help with DanaBot removal
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove DanaBot using System Restore
System Restore is the function that can give the opportunity of recovering machine in a previous state when the trojan was not active
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of DanaBot. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from DanaBot and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting trojans
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ macro virus. Wikipedia. The free encyclopedia.
- ^ Charlie Osborne. DanaBot banking Trojan jumps from Australia to Germany in quest for new targets. ZDNet. Technology news and security alerts.
- ^ Josh Fruhlinger. Social engineering explained: How criminals exploit human behavior. CSOonline. Technology news and reviews.
- ^ Malware detection rate. VirusTotal. Online malware scanner.





















