Dt69sx.xyz ads (scam) - Free Instructions
Dt69sx.xyz ads Removal Guide
What is Dt69sx.xyz ads?
Dt69sx.xyz is a fake website that encourages downloads of potentially unwanted programs
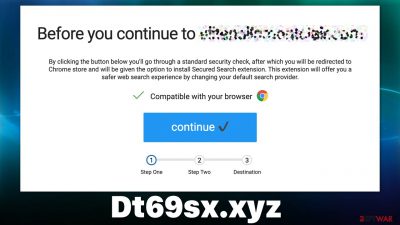
Redirects and ads to Dt69sx.xyz might be one of the adware or malware infection signs, although most commonly, users access this site when browsing insecure places, such as illegal torrent downloads, gambling, etc. Adware installed on the device can manifest as a browser extension or program installed on the system level, hence both locations should be investigated thoroughly.
Once users land on Dt69sx.xyz site, they can be presented with a variety of scams, including those that ask them to download insecure software, subscribe to useless services, or participate in a survey/giveaway. We recommend not interacting with anything promoted on the scam website, as it could result in malware infections, personal data disclosure to malicious parties, or financial losses.
| Name | Dt69sx.xyz |
|---|---|
| Type | Scam, phishing, adware, redirect virus |
| Goal | Make people provide personal information, subscribe to useless services, download malicious software or subscribe to push notifications |
| Distribution | Redirects from other malicious websites, adware |
| Dangers | Installation of potentially unwanted or malicious software, personal accounts loss, monetary losses, etc. |
| Removal | You should not interact with the contents shown by a scam. Instead, check your system for adware or other malware with SpyHunter 5Combo Cleaner security software |
| Other steps | To clean your browsers and the system from leftover files and trackers, employ a powerful repair and maintenance utility FortectIntego |
Infection symptoms
There are two may ways how you might end up on Dt69sx.xyz scam website – either you can get redirected after clicking a link on some other website (automatic redirects could also occur, although that is more common on less secure websites) or due to aggressive form of adware installed on your system.
Adware is spread via insecure channels, including misleading advertisements and freeware[1] installers downloaded from third-party sources. This is one of the main reasons why those infected are unaware that adware is regulating their traffic, and encounters with ads and phishing[2] websites become a more frequent occurrence.
To conclude, just because you ended up on a scam website, it does not automatically mean that you are infected. However, if you have noticed more strange symptoms, such as pop-ups, deals, offers, coupons, and other types of advertisements showing up randomly when browsing the web, you should get concerned.
Likewise, if you have downloaded software from Dt69sx.xyz or any other website it could link you to, your computer could also be infected. In most cases, it would be a browser hijacker or a similar unwanted application, although one can never guarantee a security level of software downloaded from unknown websites (especially those that use fake messages).
Scam message examples
As mentioned before, several different scam messages could be accommodated by the same website. For example, if you land on such a page and refresh it, you might be rerouted further to Se29.biz, Clean-your-pc.xyz, Columbusstream2.xyz, or similar websites, where further scamming acts could take place.
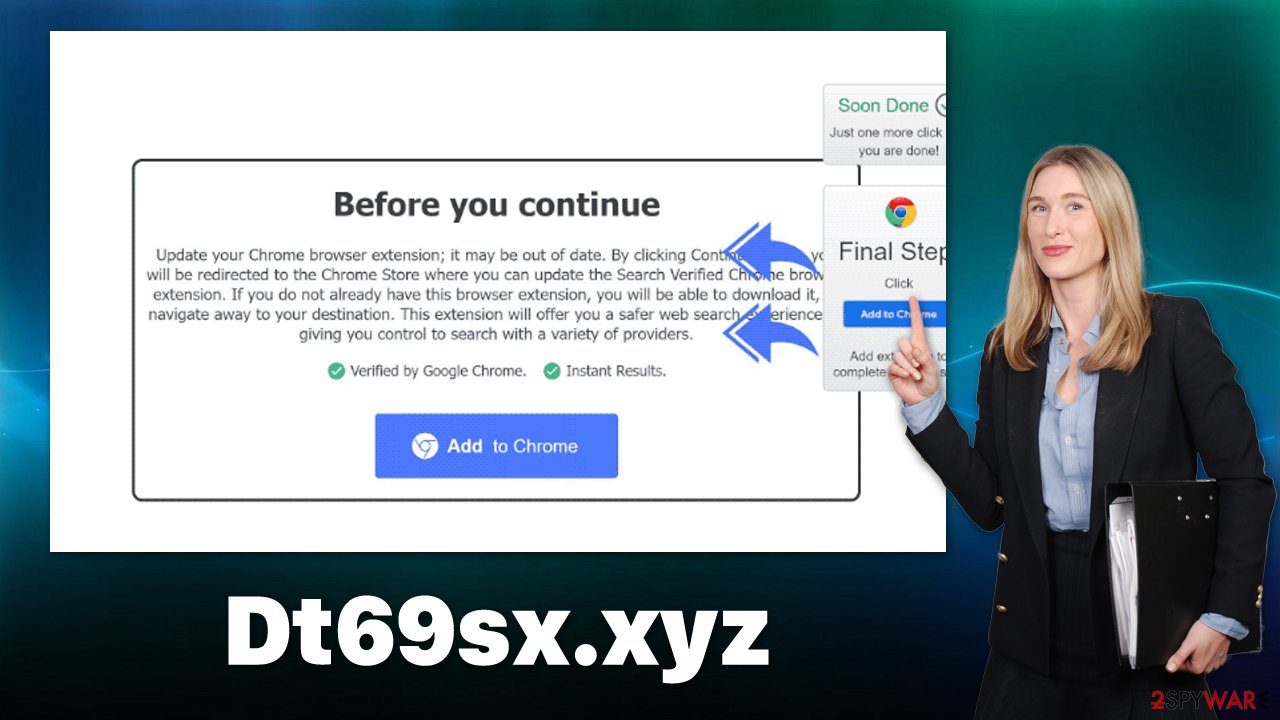
Most commonly, users who are redirected to the page are asked to update browser extensions or programs that aren't even installed on their devices. Here is one of the most common messages that several similar websites also use:
Update your Chrome browser extension; it may be out of date. By clicking Continue, you will be redirected to the Chrome Store where you can update the Search Verified Chrome browser extension. If you do not already have this browser extension, you will be able to download it, or navigate away to your destination. This extension will offer you a safer web search experience by giving you control to search with a variety of providers.
Evidently, the message implies that some extension is already installed on the browser and needs to be updated. It is not the case, however, and it is a simple way to make users download the software they otherwise wouldn't.
If you were already tricked into installing something, you shouldn't worry much as we explain in detail how to eliminate adware and other potentially unwanted programs in detail.
Removal steps explained
If you have not installed any advertised apps from Dt69sx.xyz or similar websites, your computer is likely to be safe. However, since frequent redirects and an increased number of advertisements might be a sign of adware, we recommend you employ the removal instructions regardless of the situation.
First of all, we recommend you download and install anti-malware software, such as SpyHunter 5Combo Cleaner or Malwarebytes, and perform a full system scan. Before proceeding, make sure you update database definitions so that all the newest versions of malware can be identified and removed effectively.
Next, you should check your browsers for unwanted extensions:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Potentially unwanted programs might also be installed on the system level. In this case, their scope of functionality might be much broader, and more system components could be affected by the infection. Malware is installed on a similar principle, although you are unlikely to find it in the installed application list (security software can take care of that).
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
While moving apps into Trash is how you delete most common applications, adware tends to create additional files for persistence.[3] Thus, you should look for .plist and other files that could be related to the virus. If you are not sure, skip this step entirely.
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
After PUP or malware removal, you should delete web data and other leftover files from your browsers. This job can be done much easier with software like FortectIntego, which can also fix any damage that could have been caused to your system files while the malware was active. Otherwise, proceed with the following steps:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
How to prevent from getting adware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Freeware. TechTarget. Data-driven marketing.
- ^ Phishing attacks. Imperva. Application and data protection.
- ^ Persistence-Enabled Attacks: A Technical Deep Dive. Huntress. Cybersecurity research blog.











