Clean-your-pc.xyz ads (scam) - Free Guide
Clean-your-pc.xyz ads Removal Guide
What is Clean-your-pc.xyz ads?
Clean-your-pc.xyz imitates legitimate security software scans to fool users into downloading malicious programs
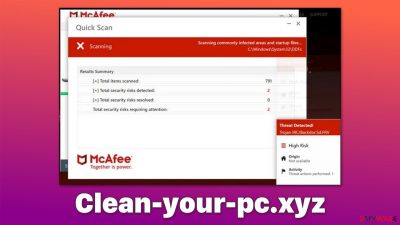
Clean-your-pc.xyz is a deceptive website you might come across when browsing the internet on Google Chrome, Mozilla Firefox, MS Edge, or another web browser. While the reason for its redirect can vary, users never arrive on the scam page intentionally. The redirects to it are commonly initiated by link clicks on other malicious websites or adware that is secretly running in the background of the device.
As soon as people enter Clean-your-pc.xyz, they are immediately presented with what looks like a security scan allegedly performed by a trustworthy security vendor – McAfee or Norton.
Fake scan results claim that several viruses were found on the system and that they need to be eliminated by the security software, the license of which, according to the message, has expired and needs to be renewed.
Crooks attempt to monetize by employing a pay-per-install scheme, although there's no guarantee that offered software is genuine – it might be a fake version or simply a malicious program that, once installed, would perform secret tasks, including installation of other malware or extensive information tracking of keystrokes and other sensitive details.
If you have encountered this scam page, you should not panic, as all the displayed results are fake. Do not interact with any page elements or download software, and instead, use legitimate methods to check your system for infections.
| Name | Clean-your-pc.xyz |
|---|---|
| Type | Scam, redirect, adware |
| Distribution | Third-party scam websites, ads, adware redirects |
| Operation | Claims that viruses have been found and that the anti-malware software license has expired. Asks to upgrade fake license |
| Symptoms | Redirects to suspicious websites that accommodate commercial or scam content; fake messages that offer to download malicious software; ads inserted into every visited website; unknown extension or program installed on the system; |
| risks | Loss of finances due to fake subscriptions; redirects to other malware-laden, scam websites; installation of potentially unwanted or malicious software |
| removal | You should not interact with the content shown by a scam website. Instead, check your system for adware or malware infections with SpyHunter 5Combo Cleaner security software |
| Other tips | You should remove caches and other web data after the elimination of PUPs to prevent data tracking with the FortectIntego repair and maintenance tool. You can also repair damaged system components with it |
Clever scam techniques help crooks reach their goals
Clean-your-pc.xyz is a fake virus scam – a form of online fraud that has been extremely prevalent because it is very effective. In the recent few months, we have seen an incredible rise in fake websites that attempt to imitate legitimate security vendors, including Yourdatasecurityservice.com, Allowpcprotect.com, or Secureform.xyz – these operate in an identical manner, most likely having the same cybercrooks behind them.
Social engineering tricks such as the usage of familiar names in cybersecurity are also not new. It gives people the reason to believe these scams, making them feel like they are legitimate.
As soon as people land on the malicious page, several scans seem to take place. The process imitates the scan performed by legitimate security tools when looking for infections. After a short while, the results are shown as follows:
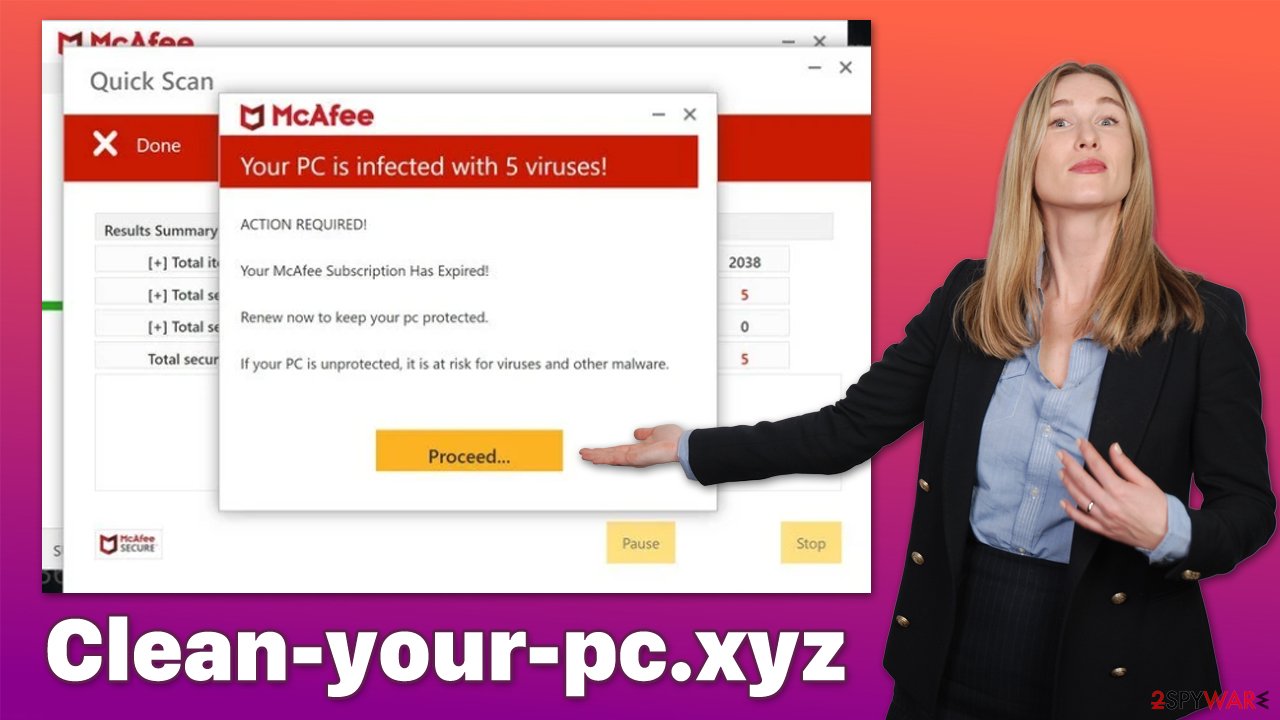
Your PC is infected with 5 viruses!
ACTION REQUIRED
Your McAfee Subscription Has Expired!
Renew now to keep your PC protected.
If your PC is unprotected, it is at risk for viruses and other malware.
Do not interact with these messages or shown links. If you have, please read the information below that could help you recover easier.
Tips on recovery
Cybercriminals know a little more about how to trick users effectively, and they employ scare tactics quite often to reach their goals – timers, threats of dangerous consequences, personal account theft, and similar can often frighten users and make them make irrational decisions, such as downloading of malicious applications that are offered as security tools.
Despite popular belief, it is highly unlikely that your system could get infected just by you entering a website that shows fake notifications. If you have your system fully updated and software vulnerabilities[1] patched, it becomes impossible.
However, user actions while on a scam site can determine the level of dangerous consequences. For example, downloads of offered applications might result in malware infections or disclosing your personal information might result in further phishing attempts. If you have disclosed your passwords, make sure you change them on all accounts they are used (never reuse passwords, as it is one of the main security hazards so many security experts[2] warn about).
Make a thorough system check
As explained before, users do not access dangerous websites on purpose but are rather tricked by fake links and automatic scripts hidden on various websites. This can be avoided by not visiting or downloading software from illegal websites – torrents, software cracks, and similar pirated content is often associated with such behavior.
Employing a reputable ad-blocker can also prevent the execution of malicious scripts, although it can have other negative impacts, including broken page elements or prevention of content monetization for legitimate websites.
If you have downloaded any software or interacted with the Clean-your-pc.xyz scam in any other way, we recommend you check your system for infections. Frequent encounters of ads and malicious material online might also be a sign of adware infections, so it is worth taking a look regardless.
You can start by checking programs installed on your system:
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
While moving apps into Trash is usually how you delete most normal applications, adware tends to create additional files for persistence. Thus, you should look for .plist and other files that could be related to the virus. If you are not sure, skip this step entirely.
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
If you are not quite sure what should and what shouldn't be installed on your machine, you should instead employ powerful anti-malware software and perform a full system scan – we recommend using SpyHunter 5Combo Cleaner or Malwarebytes. Not only can security tools locate and remove all the malware-related components, but they can also eliminate the most aggressive adware that causes browser redirects.
You could also check your browsers for unwanted extensions which could have slipped in along with other software. You can usually find them by accessing the “Extensions” section located next to the URL bar o your browser.
Finally, you should also clean your browsers accordingly, as they store cookies[3] and other caches which could result in Clean-your-pc.xyz ads coming back or continuation of unwanted browser tracking. For that, you can employ FortectIntego or find the manual steps below. You will also find steps to remove the extensions from your browser and ways to reset them if such action is required.
Getting rid of Clean-your-pc.xyz ads. Follow these steps
Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Important steps to take before you begin malware removal
File encryption and ransomware infection are two independent processes (although the latter would not be possible without the former). However, it is important to understand that malware performs various changes within a Windows operating system, fundamentally changing the way it works.
IMPORTANT for those without backups! →
If you attempt to use security or recovery software immediately, you might permanently damage your files, and even a working decryptor then would not be able to save them.
Before you proceed with the removal instructions below, you should copy the encrypted files onto a separate medium, such as USB flash drive or SSD, and then disconnect them from your computer. Encrypted data does not hold any malicious code, so it is safe to transfer to other devices.
The instructions below might initially seem overwhelming and complicated, but they are not difficult to understand as long as you follow each step in the appropriate order. This comprehensive free guide will help you to handle the malware removal and data recovery process correctly.
If you have any questions, comments, or are having troubles with following the instructions, please do not hesitate to contact us via the Ask Us section.
IMPORTANT! →
It is vital to eliminate malware infection from the computer fully before starting the data recovery process, otherwise ransomware might re-encrypt retrieved files from backups repeatedly.
How to prevent from getting adware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Thomas Holt. What Are Software Vulnerabilities, and Why Are There So Many of Them?. Scientific American. The science magazine.
- ^ Lesvirus. Lesvirus. Cybersecurity advice and malware insights.
- ^ What are Cookies?. Kaspersky. Resource Center.





















