Error 268d3 xc00037 scam (Decryption Steps Included)
Error 268d3 xc00037 scam Removal Guide
What is Error 268d3 xc00037 scam?
Error 268d3 xc00037 is a fake site designed to look like an official Microsoft alert
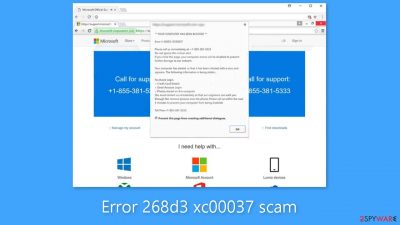
The digital world is riddled with various scams and cyber threats, one of which is the “Error 268D3-XC00037” scam. Similar to other well-known scams such as “Microsoft Warning Alert” and “Your Device Is Under Threat,” this bogus error message preys on unsuspecting users by displaying alarming messages claiming their systems are infected with malware.[1]
In reality, this error is caused by a malicious website, and its purpose is to trick users into seeking fraudulent technical support services. In this section, we'll look more closely at how the Error 268D3-XC00037 scam works and how it endangers users' privacy and security.
PUPs are frequently responsible for redirecting users to the Error 268D3-XC00037 website without their knowledge. These PUPs infiltrate systems covertly, bringing with them an array of intrusive advertisements, data-gathering techniques, and unnecessary background processes.
The deceptive error message claims that the user's system is infected with dangerous malware that threatens their personal information, including sensitive information such as logins, passwords, and credit card information. To address this apparent threat, victims are directed to a toll-free phone number provided as a means of contacting purported “technical support.”
However, Error 268D3-XC00037 is nothing more than a ruse orchestrated by cybercriminals posing as certified technicians. Their primary goal is to dupe users into paying for unnecessary support services and to capitalize on their fears. The alleged malware does not exist, and users should never call the phone number provided.
Scammers can install actual malware and change critical system settings by connecting remotely to the victims' computers. As a result, they claim to have discovered additional issues and to be able to provide additional assistance at an additional cost. To avoid this scam, simply closing the web browser or rebooting the system will remove the malicious website. It is critical not to select the “Restore Previous Session” option, as this will reopen the bogus error page.
| NAME | Error 268d3 xc00037 |
| TYPE | Phishing, scam |
| SYMPTOMS | Fake Microsoft alert that tries to get users to call fake technical support |
| DISTRIBUTION | Software bundling, suspicious ads |
| DANGERS | Might lead to malware infection, sensitive detail disclosure, and lost/stolen money |
| ELIMINATION | Scan your system for PUPs and malware with antivirus tools |
| FURTHER STEPS | Clear browser cookies and repair system damage with FortectIntego |
The intrusive nature of PUPs
PUPs play an important role in the spread of the Error 268D3-XC00037 scam. Aside from their association with such scams, PUPs are a threat to users' online experiences and overall system security. In this section, we will look at how PUPs can disrupt and compromise the integrity of users' computers. One of the most serious problems with PUPs is the delivery of intrusive advertisements.
These advertisements, which can range from coupons to banners to pop-ups, are frequently generated using tools that allow the placement of third-party graphical content on any website. Unfortunately, these advertisements frequently obscure the underlying website content, reducing the browsing experience. Furthermore, clicking on these intrusive ads can have serious consequences, as they frequently redirect users to malicious websites or trigger scripts that initiate the download and installation of actual malware. Even an unintentional click can result in high-risk computer infections.
Another major issue is the tracking of user information by PUPs. Without the users' knowledge or consent, these programs continuously collect data related to their browsing activities and system details. Personal information, including sensitive information, may be harvested by PUP developers, who may then sell this information to third parties, including cybercriminals. Misuse of private information can result in serious privacy issues and expose users to various forms of abuse.
PUPs consume system resources by running unnecessary processes in the background, in addition to privacy concerns. Some PUPs even mine cryptocurrency, further degrading system performance and decreasing overall efficiency. These programs not only impede productivity but also expose users to the risk of system instability and performance degradation by misusing system resources without user consent.
Prevention and protection
It is critical to prevent potentially unwanted programs (PUPs) from infiltrating your computer in order to maintain a safe and secure digital environment. This section will go over some practical steps and best practices for avoiding PUP installation and protecting your system from their intrusive presence.
One of the primary methods used by PUP developers to spread their programs is the use of intrusive advertisements and a deceptive marketing technique known as “bundling.” Bundling is the practice of secretly installing third-party applications alongside regular software, frequently without proper disclosure. Users can unintentionally install PUPs by skipping installation steps and clicking on advertisements, which results in the installation of rogue programs.
To avoid becoming a victim of PUPs, use caution when browsing the internet and downloading/installing software. Intrusive advertisements may appear legitimate at first glance, but they can be identified by their redirection to dubious websites such as survey portals, and gambling platforms. If you encounter such redirects, you must remove any suspicious applications and browser plug-ins immediately.
It is critical to meticulously analyze each window and carefully review the contents of the dialogs during the download and installation process. Opt out of any additional programs that are included and decline offers to download or install them. Furthermore, it is best to avoid using third-party downloaders or installers, as these are frequently used by crooks to spread PUPs via the bundling method. To ensure the security of your downloads, only obtain software from official sources, and use direct download links whenever possible.
Scan your system
If you've come across any scams or suspicious content on the internet, it's critical to scan your system for potential infections, most commonly in the form of adware. SpyHunter 5Combo Cleaner and Malwarebytes are two security software recommendations.
These tools offer comprehensive protection against a variety of threats such as adware, malware, ransomware, and phishing[2] attempts. They have advanced scanning capabilities for detecting and removing infections. Furthermore, their real-time protection features can detect and prevent future threats, keeping your system safe.
However, if you know which applications are causing the unwanted behavior, you can follow the step-by-step instructions below to uninstall them:
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.
![Uninstall from Windows 7/XP Uninstall from Windows 7/XP]()
- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
Clear cookies and cache
After ensuring that your system is infection-free, you should clean your browser caches. This aids in the removal of traces of potentially harmful websites and lowers the risk of future infections. FortectIntego is our recommendation for this task. It's a useful tool for clearing cache, cookies, and browsing history across multiple browsers with a few simple clicks.
You can further secure your system and protect your online privacy by using useful software on a regular basis. Clearing browser caches and checking your system for infections on a regular basis are critical steps in maintaining a secure digital environment. Additionally, it can fix BSOD[3] errors, corrupted files, and registry issues.
How to prevent from getting viruses
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.





