ICSPA virus (Free Guide) - updated Feb 2020
ICSPA virus Removal Guide
What is ICSPA virus?
ICSPA virus is the threat that uses false law enforcement agency messages to scare people into paying the demanded amount
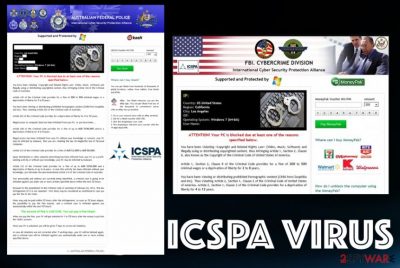
ICSPA ransomware virus also gets distributed via other methods like malicious websites or hacked domains, exploit kits, and malicious files that include the payload of this virus. Spam emails often are the ones that deliver infected files to victims and lead to infections like this. Once such a script is installed on the system, the malware displays a bogus notification and states that the computer is blocked due to the content you visited or other illegal activities that you allegedly are guilty of. The screen becomes locked, and it is not the easiest thing to exit the window and get back to a normal working machine, so you need to react as soon as possible and somehow terminate this program.
| Name | ICSPA virus |
|---|---|
| Type | Screen-locker, ransomware[1] |
| Symptoms | The screen gets locked and delivers a questionable notification from a law enforcement agency or other institution that claims that you have done something illegal. Therefore, you need to pay a particular fine. This message encourages people to pay using online payment platforms, or your device gets permanently blocked |
| Danger | The extortion-based threat asks for money transfers, so people can lose huge amounts of money if they decide to pay up. Machines can get the damaged during the time when the screen is fully locked by the processes happening in the background |
| Tactics | Scaring people into paying up to hundreds or even thousands of dollars with all the false claims of illegal actions |
| Known since | 2014 or even earlier |
| Distribution | Throughout the years of existence, this virus was distributed with the help of trojans, other malware, malicious sites, hacked domains, and infected files attached to emails |
| Elimination | ICSPA virus removal process should be quick and successful if you use proper anti-malware tools and terminate the malware automatically |
| Repair | When the screen is locked by the virus other processes can be launched, including damaging activities, so get FortectIntego or a similar tool that should find and fix virus damage for you |
ICSPA virus will lock your screen and the computer itself, so it blocks any access to the operating system, applications, and features. You need to log in on the machine to do anything, so Safe Mode is the way to go. By rebooting the OS in Safe Mode, you ensure that the computer is not controlled by the malware.
However, it may not be possible and instead of normal Windows boot you receive the same lock screen with the following or a similar ICSPA virus ransom-demanding message:
ICSPA International Cyber Security Protection Alliance
U.S. Department of Justice – Office of Justice Programs
ATTENTION! YOUR COMPUTER HAS BEEN LOCKED BY ICSPA. All activities of this computer have been recorded. The recent actions performed on this computer have been recorded and analysed. Due to evidence of illegal activity found on this computer (“Downloading and distribution of illegal content – illegal Pornography”), this computer has been locked. Read the Important Information below.
The penalty set (“$400 – US dollars”) must be paid within 48 hours of this notice. On expiration of the term, 48 hours that follow will be used for automatic collection of data on yourself and your misconduct, and criminal case will be opened against you.
You are accused of viewing/storage and/or dissemination of banned pornography (child pornography/zoophilia/rape etc.) You have violated World Declaration of non-proliferation of child pornography. You are accused of committing the crime envisaged by Article 161 of United States of America criminal law.
Article 161 of United States of America criminal law provides for the punishment of deprivation of liberty for terms from 5 to 11 years.
Also, your are suspected for violation of “Copyright and Related rights Law” (downloading of pirated music, video, warez) and of use and/or dissemination of copyrighted content. Thus, you are suspected of violation of Article 148 of United States of America criminal law.
Article 148 of United States of America criminal law provides for the punishment of deprivation of liberty for terms from 3 to 7 years or 150 to 550 basic amounts fine.
The illegal actions that have been recorded on this computer (“Downloading and distribution of illegal content – Illegal Pornography”) could have been actioned by yourself purposely, or without your knowledge and consent, provided your computer could have been affected by malware. Consequently , you are suspected – until the investigation is held – of innocent infringement of Article 215 of United States of America criminal law (“Law on negligent and reckless disregard of computers and computer aids”).
Please note, that personal identities of users who are suspected of committing the illegal actions on this computer have been identified and the evidential data has been recorded. The criminal case can be opened in course of 96 hours as of commission of crimes per above Articles. Criminal case can be submitted to court.
However, pursuant to Amendments to the United States of America criminal law dated January 14, 2015, and according to Declaration of Human Rights, you disregard of law may be interpreted as unintended (if you had no incidents before) and no arraignment will follow. However, it is a matter of whether you have paid the fine to the Treasury (to the effect of initiatives aimed at protection of cyberspace).
Current status: “Case can be classified as occasional/unmotivated, according to 17 (U.S Code) 512. Subject to a fine ($400 – US dollars).” – this case can be closed without prosecution. The computer will be unlocked automatically.
The message can be written in an appropriate language and target victims in a specific area, so it seems more legitimate and scary. However, you are not charged for any of those claims like visiting pornographic content sites or downloading pirated software. Any agencies like that cannot collect fines by invading your primate network. It may seem that ICSPA virus removal is not possible due to the screen-locking and all the payment demands, affected functions of the machine.
However, if you choose the right tools, you can terminate this ICSPA virus. It is a highly complicated process, so you should get advanced tools and prepare for serious malware removal. Tools like anti-malware software can get on the machine and find these traces of the malicious programs. Install the AV tool on an external drive and launch it on the infected PC. Make sure to ignore the pop-up virus message and try to not click on anything, so you can at least avoid additional malware infiltration. 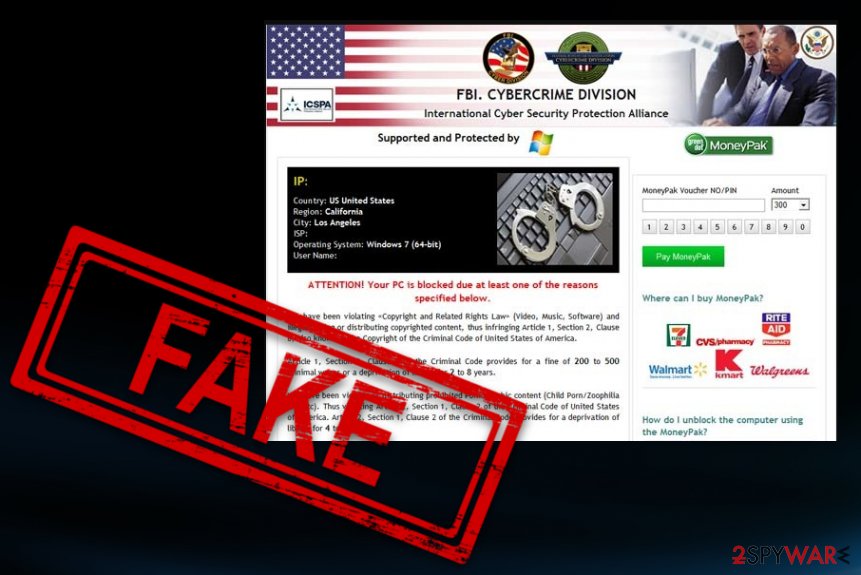
It's clear that ICSPA ransomware virus is designed to steal the money from unaware PC users, and it must be removed from the system without any delay. Of course, it won't be as easy as you may expect because this ransomware blocks legitimate applications, including anti-virus and anti-spyware programs. However, keep on reading, and you'll see how you can overcome that.
Once it gets inside, this ransomware locks the desktop and disables the computer's functions without any permission asked. Even more, it replaces PC's screen with an alert that pretends to be from the International Cyber Security Protection Alliance and reports about various crimes, like the use of illegal software or distribution of malware. Please, keep in mind that all this activity is a huge scam that seeks to rip you off, and you should never pay a fine using Ukash or Paysafecard prepayment systems.
Instead of that, you must remove ICSPA virus as soon as possible, and the best option would be to scan the machine using a professional anti-malware tool that is capable of detecting and deleting threats running in the background of the device. You cannot find the payload of such malware manually, so automatic software is helping you.
However, since ICSPA virus itself can affect important settings of the computer and install additional threats to do that, the already infected device can get more damaged. Besides terminating the ransomware, you should also go through those altered parts and repair virus damage. Rely on system software like FortectIntego that can find and repair such parts on your computer. 
Methods used to spread malware around
The particular screen lockers get distributed through the same methods as malware and spyware: threat can be downloaded together with fake updates, media codecs, non-registered software, spam, and through similar ways of distribution that involve files injected with malicious script.
Malicious files can be delivered via spam emails, other notifications sent via the internet to you. In most cases, criminals pose as companies, institutions, or services that people commonly use, so victims fall for the scam and open the email, download the attachment or visit the link added on the email itself.
Unfortunately, the attachment can come in the format of a document, executable, and other typical files that may not raise too many questions. Microsoft documents include macro viruses[3] that trigger the direct drop of the virus script and lead to infection like this immediately. Make sure to ignore any of the emails that you were not expecting to receive, so there is no opportunity for the malware to end up on the PC.
Get rid of the ICSPA ransomware virus as soon as possible
When trying to remove ICSPA virus, you may find that your security features, anti-malware programs, and other system functions are blocked. That's normal because threat changes various settings on the machine to affect the performance significantly. In order to overcome this situation, you should use one of the features that the Windows operating system has.
Before you proceed with the automatic ICSPA virus with an anti-malware tool, reboot the system in Safe Mode with Networking and then run the AV detection program. By doing it this way you can ensure that the virus is not affecting the process, and malware can get detected. We can rely on SpyHunter 5Combo Cleaner or Malwarebytes for such a job.
ICSPA virus can be more persistent and affect other crucial parts of the system, so the victim can't access the needed tools and functions that help terminate the threat or recover the machine. We can recommend getting a PC repair or system optimizer software like FortectIntego since it can find and fix affected files, data in system folders that allow the locker running.
Getting rid of ICSPA virus. Follow these steps
Manual removal using Safe Mode
Get rid of ICSPA virus and make sure to clean the machine fully by rebooting the system in Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove ICSPA using System Restore
Try System Restore that can help to disable the threat automatically
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of ICSPA. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from ICSPA and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Ransomware. Wikipedia. The free encyclopedia.
- ^ Limary Cruz-Rubio. FBI Warns the Public About Ransomware Internet Scam. FBI. FBI San Juan official report.
- ^ Liam Tung. Microsoft tackles macro malware with new Office-antivirus integration. CSOonline. Cybersecurity and technology news.





















