Idp.helu virus (Free Guide) - Removal Instructions
idp.helu virus Removal Guide
What is idp.helu virus?
idp.helu virus is the problematic cyber threat detection that creates tons of pop-ups and alerts from AV tools and can be related to serious malware
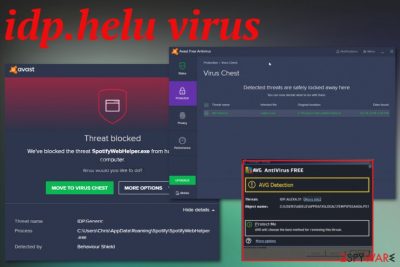
Although there is no specific information about idp.helu virus, you should be prepared for multiple scenarios. Trojan horses, worms, and malware are one of the more common cyber threats that can run in the background and hide behind this detection name. Unfortunately, without any particular symptoms, it is difficult to find the malware itself without damaging the device.
| Name | IDP.helu virus |
|---|---|
| Type | Malware/ virus detection |
| Possible reasons for the detection | Trojan horse,[1] worm, malware or a false detection |
| Distribution | Spreads with other shady tools, software, can get on the PC with the help of trojans, backdoors, corrupted sites |
| Possible danger | Can be an indication of serious malware infection that targets users' personal information or damages the device permanently |
| Elimination | Get a reliable anti-malware tool and scan the machine fully to remove IDP.helu virus. Clean the system from virus damage with FortectIntego |
This suspicious threat that appears as a possible danger alert can also appear with different names, like any other generic detection result. IDP.helu.jsdown18 virus is one of the more particular names possibly belonging to the same cyber infection.
No matter what particular file or detection name appears instead of idp.helu virus, you should pay attention and react as soon as possible, it is especially important when antivirus tools and other security programs or features shows such warnings continuously.
Various experts[2] call such infections silent danger because even though the detection can be false this IDP.helu.MSEx4 virus fileless malware[3] is one of the more dangerous types of threats because of the fact that no particular files are needed for this virus to work.
Since IDP.helu virus can be one of the threats that work in the background, it can run under a common name of the system file that hides malicious purposes even more. When you encounter a file with the dll or exe ending in the Task Manager and using high CPU, other resources of the computer, you should consider a more in-depth malware elimination immediately.
- cryptocurrency mining using resources of the system;
- infecting the machine remotely;
- opening backdoors for intruders;
- creating redirects to sites and generating views;
- stealing data from the machine or other sources associated with the victim.
You should consider that this IDP.helu virus detection is possibly related to real attackers, malware creators, and people considered criminals. They can obtain information, files, and other details valuable later on.
Make sure to avoid anything that can lead to permanent damage and remove idp.helu virus from your machine as soon as the detection name shows up on the screen. Follow up suggested steps of the antivirus program that detected this threat in the first place, because other tools may not even detect the same virus due to different databases.
However, we recommend ensuring the best IDP.helu virus removal results by scanning the system with FortectIntego tool additionally. Such software can show virus damage, indicate left traces, or even detect additional malware hiding on the machine already. By double-checking, you can clean the computer and improve the overall performance. 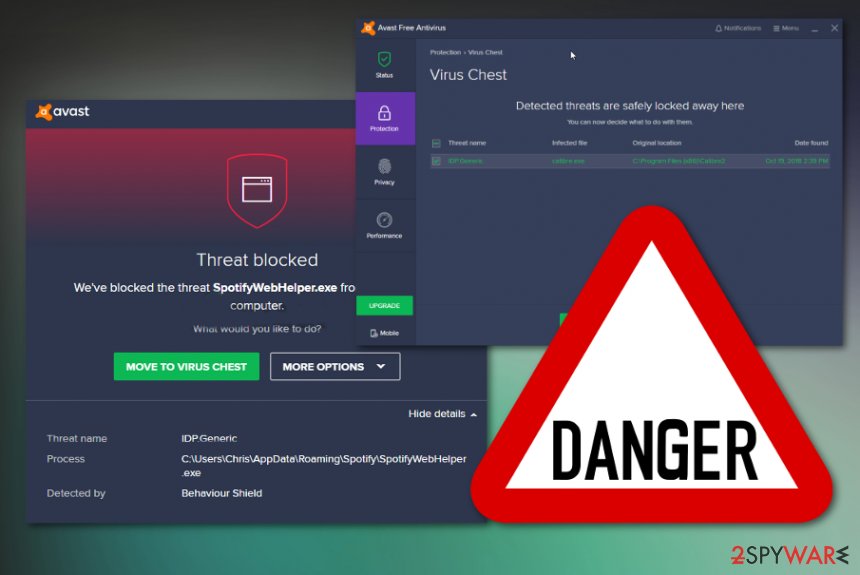
Shady installations and malicious files deliver silent cyber threats
Your computer may get extremely damaged by cyber threats that run in the background because you cannot notice them right away. The infiltration of any other potentially unwanted program may be noticed immediately if symptoms occur after the infiltration.
However, those threats that run in the background infect the machine in the background. The whole process of getting on the system may cause some speed or performance issues, but users cannot put two and two together to determine that this is caused by malware.
Fortunately, when your antivirus programs run on the machine, you can get warned about the possible threat or a direct malware drop. This way, you may react to the issue as soon as possible. However, when you don't pay enough attention to received emails, freeware sources, and installation processes, in general, you allow infections without even noticing.
Since this detection may be either false either related to any of the cyber threats you should note:
- choose Advanced or Custom installation options and then de-select anything suspicious from the list to avoid PUP infections;
- delete emails from the inbox that include shady senders' addresses or file attachments and hyperlinks.
The only solution for IDP.helu virus infection – thorough system cleaning
If you encountered the pop-ups and alerts with warnings about idp.helu virus, or additional malware infiltration risks, you should react to these immediately. Although there is a possibility that detection is false and triggered by misconfigurations or corruption in the operating system or applications, you need a diagnosis.
IDP.helu virus removal can be performed after the detection and thorough check on the machine. Fortunately, you cannot do that yourself and manually because detection shows the possible risk, not the particular file or program that can be removed to end the frustration.
To end all the suspicious pop-ups, other activities, you need to remove idp.helu virus completely. This is achievable with the same AV tool that shoed you those pop-ups and detection alerts, or additional anti-malware tools. You should install FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes and run the full check on the system. Once the detection results appear, you can determine what needs to be done on the computer further. Rely on trustworthy tools and think before eliminating any crucial system files.
How to prevent from getting malware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Trojan horse. Wikipedia. The free encyclopedia.
- ^ Virusai. Virusai. Spyware related news.
- ^ The Rise of Malware-less Attacks. CarbonBlack. Transforming endpoint security.
