Miis file virus (Free Instructions) - Virus Decryption
Miis file virus Removal Guide
What is Miis file virus?
Miis file virus is the ransomware that creates damage on the machine to have a purpose for blackmail
Miis ransomware is a type of malicious program that encrypts the data and asks for payment to decrypt it. Files are appended with a .miis extension, so data as 1.jpg becoming “1.jpg.miis” The encryption process leaves behind a ransom note named _readme_txt upon completion. This piece of the file gets placed in folders containing the encoded data.[1]
The ransom-demanding message informs victims that their data has been encrypted and the only way to restore it is by paying a 980$ ransom. The price for the decryption keys and software can be reduced by 50% if you establish communication with them via email within 72 hours, but there's no guarantee they'll decrypt your files even after payment as this process takes time – so make sure not to risk valuable information when testing!
Since ransomware virus is powerful enough to encrypt your data and hold it hostage for ransom. It's rare that the decryption key will be easily found, but if you've been backing up your files in case of an emergency then there won't be any need to panic because all this information has already been saved! If you have no backups and .miis file virus affected your device, you need to rely on alternate options.
The peculiarity with Djvu ransomware family such as .leex or .neer – they have a set pattern: they lock down one’s computer system until certain demands by hackers are met. Also, the access can only resume once money is given through bitcoin-based transactions.
However, this is the family known since 2016 at least and criminals should never be trusted. The problem of file recovery arises when backups have not been made recently. We are pleased to report that it is possible to remove the threat and recover at least some of those affected pieces.
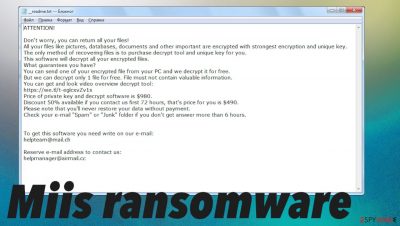
The direct money demand gets displayed in _readme.txt:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-9CYW99VhUR
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
helpteam@mail.chReserve e-mail address to contact us:
helpmanager@airmail.ccYour personal ID:
In order to recover files encrypted by the Miis virus, it is very important that you read this manual guide in its entirety. This will outline all of your options for restoring a system from an infected computer as well as which methods are most effective and easiest to use when decrypting .miis files on a Windows operating system.[2]
There are also some troubleshooting tips at the end of any problems that arise during these processes. However, we highly recommend reading through everything before attempting any of them, so there won't be any hiccups along the way! If you replace encoded files with safe copies when the virus is still present, you may lose your files permanently.
The infection can also lead to the damage done in particular parts of the system. This is even more dangerous because these changes allow Miis ransomware to run processes in the background and control the machine without causing any symptoms. If people overlook this problem, computers can be permanently corrupted.
| name | Miis ransomware |
|---|---|
| Type | File-locker, crypto virus |
| Family | Djvu ransomware/ STOP |
| Infection symptoms | Files like images, documents, video, audio files get renamed and become inaccessible; ransom demanding message appears on the desktop and in some folders; security-related programs get disabled |
| file extension | .miis |
| Ransom note | _readme.txt |
| Distribution | It is known that the threat relies on pirated software platforms, game cheats, other pieces that are capable of carrying the payload of the threat silently |
| Data recovery | Possible with data backups, software that could restore affected files. Decryption is limited to particular versions but possible |
| Elimination | Remove the cryptovirus by scanning your infected PC with reliable anti-malware tool that can remove it fully |
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
When cracking software or grames – pay attention to details
Malware is often delivered to unsuspecting victims via channels like torrent sites and downloaders that can be found on file-hosting websites. The payload of this virus disguises itself as or bundles with ordinary content so it's typically installed unintentionally. The most common way to distribute these Djvu versions – cracked game files, licensed versions of software, torrents of other pieces.
Cybercriminals are becoming more and more advanced with their malware. Unfortunately, in many cases of ransomware infections, without the cyber criminal's involvement – decryption is impossible. It might be if the malware has serious flaws or gets ended by law enforcement. Otherwise, decryption keys cannot be obtained.
As for this ransomware family, the online ID method is used in these recent attacks. It means that each victim gets the unique key after encryption. To revert changes you need to get that one-of-a-kind piece. Other versions before .miis and released earlier than 2019 can be decrypted because the offline ID method provides such an option since all or most of the victims get the same decryption key. In such cases, only one of the victims needs to pay the ransom to save other people.
Djvu decryption option for versions with offline IDs
If you have infected your computer with one of the Djvu variants, you should try using Emsisoft decryptor for Djvu/STOP. It is important to mention that this tool will not work for everyone – it only works if data was locked with an offline ID due to malware failing to communicate with its remote servers.
Even if your case meets this condition, somebody from the victims has to pay criminals, retrieve an offline key, and then share it with security researchers at Emsisoft. As a result, you might not be able to restore the encrypted files immediately. Thus, if the decryptor says your data was locked with an offline ID but cannot be recovered currently, you should try later. You also need to upload a set of files – one encrypted and a healthy one to the company's servers before you proceed.
- Download the app from the official Emsisoft website.
![Miis file virus Miis file virus]()
- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.
![Miis file virus Miis file virus]()
- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
![Miis file virus Miis file virus]()
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.
![Miis file virus Miis file virus]()
- Press Decrypt.
![Miis file virus Miis file virus]()
From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
It is advised against communicating with or paying these criminals as they often do not provide victims what was promised. After receiving ransom demands people often get scared into paying the ransom due to the inability to use important information stored on devices infected by this type of virus which leaves nothing but an inconvenience for consumers.
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
If you rely on Malwarebytes that detection of this malware can help improve the performance of the machine because all possible intruders get fully removed from the system.[3] Miis file virus can leave trojans and other malware to steal the information from the PC directly, so it is crucial to scan the system fully.
Malware can affect files in various formats, including photos, documents, video, audio files. When an infected file is run or opened – the infection chain begins to unfold. Encryption is one of the first processes, but there are many other issues that ransomware creates on the machine. Including system folder alterations.
PDF and Microsoft Office documents are the ones that can be included in the email and result in a ransomware infection. These types of malicious files usually contain a vulnerability that allows them to execute code from within one document. The infection is happening without user interaction with what's on-screen.
Possible file recovery solution
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Miis file virus Miis file virus]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Unfortunately, malicious files also difficult for antivirus software to detect because PDFs use Adobe Flash Player while MS Word uses its own custom plug-in engine called Equation Editor (for example). Rar archives have two parts – a compressed folder containing all your data as normal folders do and it has .rar as an extension. This second part contains metadata about every single piece inside this archive.
Ransomware, spyware, trojans – they're all out there lurking for their next victim looking disguised in the form of a free software update from Adobe Acrobat Reader; seeding themselves among legitimate but outdated files downloaded from an unofficial website offering game patches or movie trailers (among other things). Rely on AV tools like SpyHunter 5Combo Cleaner or Malwarebytes and make sure to clean the system fully before you go for any data recovery option.
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Encryption. Wikipedia. The free encyclopedia.
- ^ Ransomware explained: How it works and how to remove it. CSOonline. Technology news.
- ^ Virus detection rate. VirusTotal. Online malware scanner.