Nooa ransomware (Recovery Instructions Included)
Nooa virus Removal Guide
What is Nooa ransomware?
The main goal of Nooa ransomware: lock files and ask you to pay a ransom
Nooa ransomware emerged in early August 2021 – it continues the malicious business of the Djvu malware family. The virus mainly spreads via contaminated software crack files or program installers, usually downloaded from unofficial third-party sources – the infection begins as soon as the malicious .exe file is opened.
As soon as malware gains access to your Windows machine, it begins its changing process. One of the most devastating traits of ransomware[1] is its file locking capability. This particular threat encrypts all videos, documents, pictures, and other personal data with a strong RSA[2] encryption algorithm and appends. nooa appendix in the process. During file encryption, the virus shows a fake Windows update window to confuse victims and make them believe that no harm is being done.
However, as soon as this is complete, users can soon realize that none of their files can be opened anymore. Note that this does not actually corrupt files but rather locks them behind a special, unique key accessible to the attackers. At this point, if the proper encryption process fails and an offline key is used, there is a chance of restoring files for free in the future – check the bottom sections for more details.
As it turns out, the reality is pretty grim after the infection has spread and files get encrypted – cybercriminals are quick to inform victims via the _readme.txt note. In there, it is explained that all the personal data has been locked, and the $980 ransom, to be paid in Bitcoin, has to be transferred to a particular online wallet. To create a sense of urgency, a discount of 50% is also offered to victims (as long as they contact hackers within 72 hours of the infection). Crooks also leave contact emails to be used for communication purposes:
- manager@mailtemp.ch
- managerhelper@airmail.cc.
As evident, contacting the attackers is rather risky, as you may never see the decryption software that they are promising. Even if they do fulfill their promises, the payments only prompt them to create more malware and infect more people. Therefore, forwarding the money should be an absolutely last resort.
Besides, few alternative methods might help you restore files for free, so please do not make rash decisions. Read through this article and find out the best course of action when dealing with a ransomware infection like this one.
| name | Nooa ransomware |
|---|---|
| Type | File-locker, cryptovirus |
| Family | Djvu ransomware/ STOP |
| Detection | Win32:MalwareX-gen [Trj], Trojan.MalPack, HEUR:Trojan.Win32.Chapak.gen, Ransom:Win32/STOP.BS!MTB, Packed.Generic.525, Trojan.GenericKD.46721018. More results on Virus Total |
| Appended file extension | .nooa |
| Ransom note | _readme.txt explains how victims can recover their files and how to pay for such a service |
| Distribution | This well-known family spreads via pirated software platforms, game cheats, other pieces carrying the payload of the threat silently |
| Data recovery | Data can be recovered with data backups, software that could restore affected files. Instructions are provided below. Unfortunately, decryption is very limited and depends on the version, but it is also possible |
| Elimination |
If you want to remove a cryptovirus, scan the affected computer with a reliable antivirus program and completely remove the threat with a powerful anti-malware tool |
| System health | Malware also changes important settings on the computer. We recommend running system diagnostics with the FortectIntego repair tool |
Do not trust cyber criminals. Hackers who are responsible for the Djvu family release new viruses several times a month. By paying a ransom, you will only encourage the creation of new threats. Ransom note may seem convincing, but pay no attention to these words:
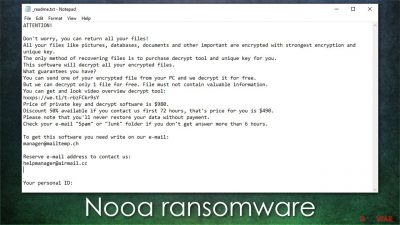
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-9CYW99VhUR
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
manager@mailtemp.chReserve e-mail address to contact us:
helpmanager@airmail.ccYour personal ID:
Since we’ve been helping people get out of sticky situations for over two decades, we’ve compiled a lot of knowledge about ransomware and ways to recover .nooa files. Keep reading and following our instructions, and you might be able to recover your files without contacting these criminals. In fact, even contacting people behind this threat can result in additional virus infiltration. Therefore, we do not recommend writing to them.
Before removing the virus, save all important encrypted files on a separate medium. You can use a USB flash drive or SSD. Encrypted data does not hold any malicious code, so it is safe to transfer to other devices. However, be sure to disconnect the medium after copying the files.
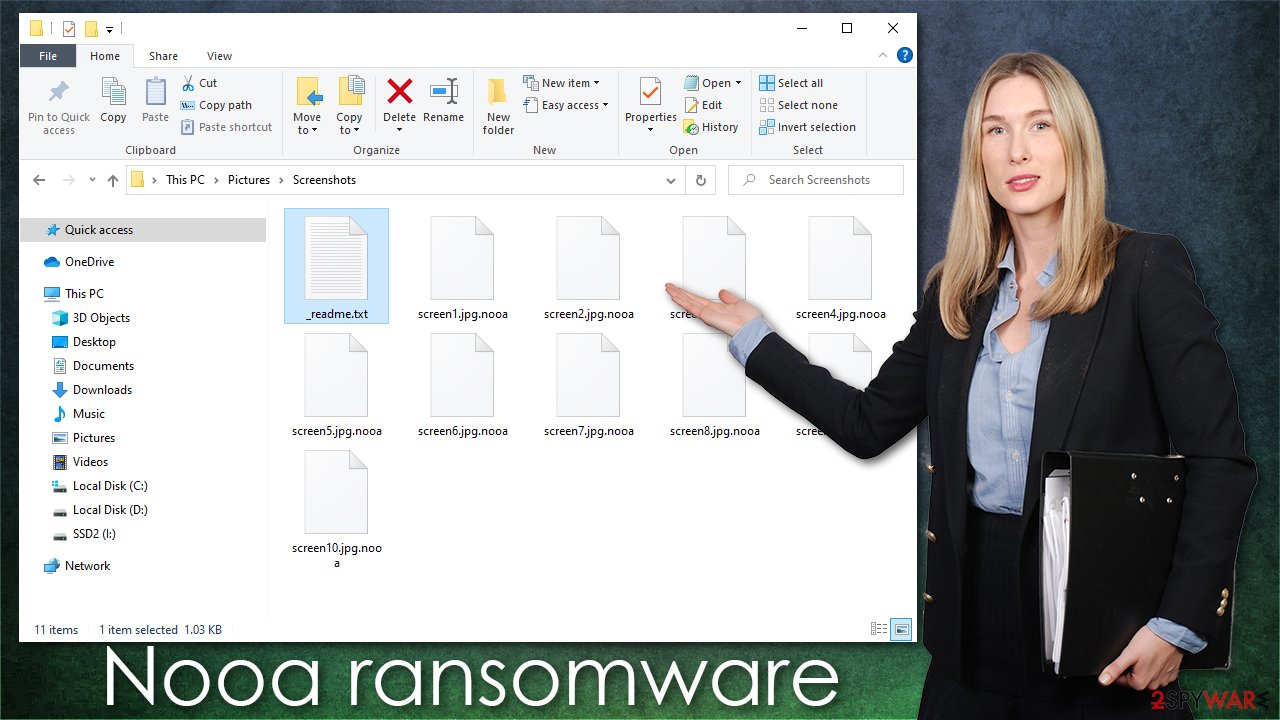
Unfortunately, the newest ransomware versions are created with the impossible decryption opportunity because the virus uses online ID when encoding data. This means that each victim gets a unique ID and a simple decryption tool won’t help to unlock the files. But even don’t give up just yet. Below you will find different methods that may help to recover some encrypted files.
Malware removal and system fix
This virus not only locks personal files but also alters data placed in system folders, so functions and activities needed for the proper performance get altered and controlled by cybercriminals.
Additionally, when you download new files to the computer, all data will be encrypted too. Therefore, you won’t be able to use your device normally until it is infected. If you want to get rid of the threat, you need to use reliable tools like SpyHunter 5Combo Cleaner. Powerful anti-malware software can help terminate the cryptovirus properly. This program will help to remove other viruses too.
Only after successful ransomware removal, you can try to recover encrypted files. However, before starting the recovery process, make sure that the system is completely clean from the virus. Any leftover files can trigger issues with secondary encryption of malicious processes. Programs like Malwarebytes can scan the system fully and detect everything, so the cryptovirus is no longer active. After that goes the system cleaning and recovery.
It is very important to follow all the steps because you cannot leave an active Nooa file virus on your device. Without proper virus removal, you will not be able to use your computer normally or restore affected files.
Once a computer is infected with malware,[3] its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup, and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstallation is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage scan Reimage scan]()
![Reimage scan Reimage scan]()

This program is a good choice if you want to have a tool that can help with various viruses and damage that cyber infections typically cause. With this tool, you would not have to worry about serious computer issues in the future too. If you run FortectIntego and the tool shows many damaged and altered pieces, you simply need to follow suggestions and fix everything. Only after a fully fixed system, you can try to recover .nooa files.
It might be possible to perform .nooa file decryption if offline keys were used
If you want to recover encrypted files after the Djvu/STOP ransomware infection, you should try to use the Emsisoft decryptor. Unfortunately, this tool only works if the data is locked with an offline ID. The cryptovirus usually uses an online ID but sometimes malware fails to communicate with its remote servers. So, it is worth checking if the Emsisoft decryptor will help in your case.
However, to decrypt .nooa files with this tool, somebody from the victims has to pay cybercriminals, retrieve an offline key, and then share it with security experts at Emsisoft. It can also happen if researchers manage to get a key from the virus developers. But until the ransomware is quite new, the chances of this happening are extremely slim.
If the decryptor says your data was locked with an offline ID but cannot be recovered currently, you should try later. Cybersecurity experts may be able to get the key in the future. Please follow these illustrated instructions if you decided to use the decryptor:
- Download the app from the official Emsisoft website.
![Nooa ransomware Nooa ransomware]()
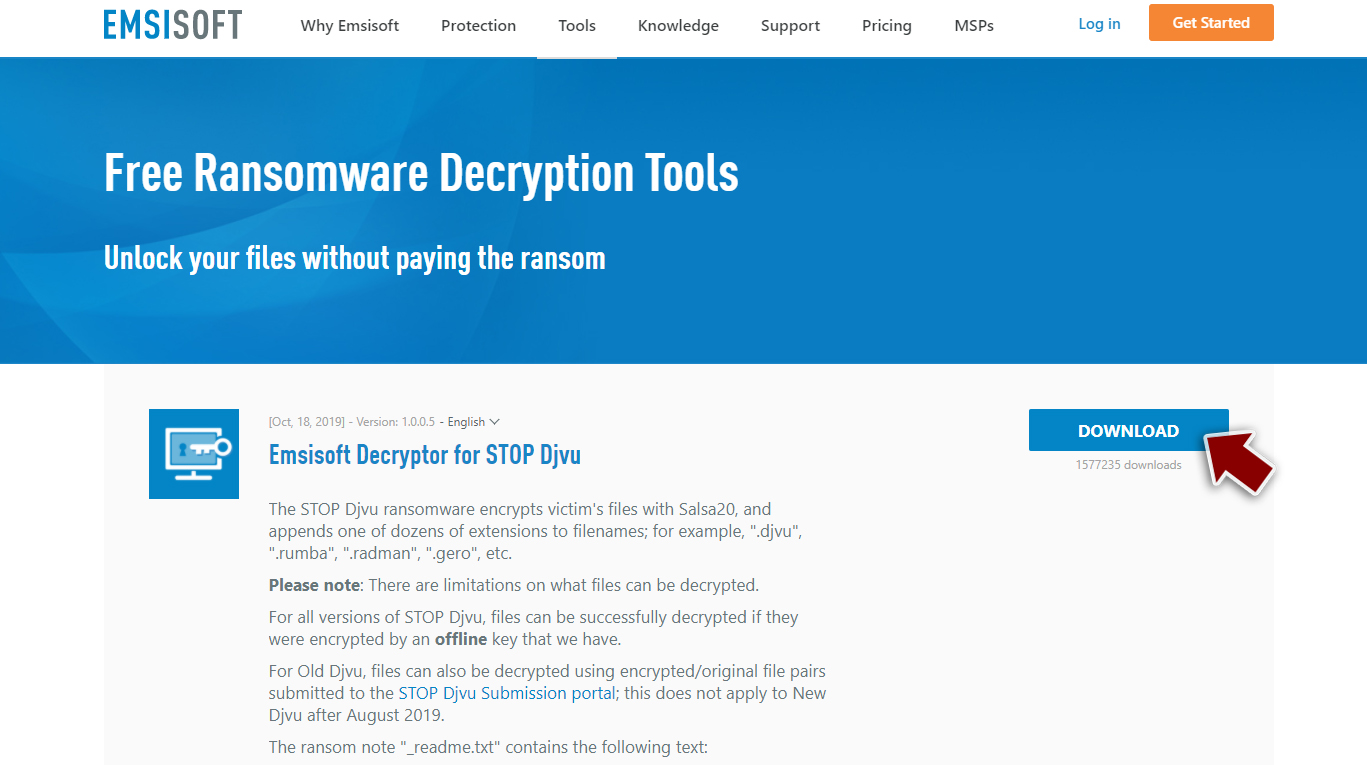
- After pressing the Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.
![Nooa ransomware Nooa ransomware]()

- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
![Nooa ransomware Nooa ransomware]()
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.
![Nooa ransomware Nooa ransomware]()

- Press Decrypt.
![Nooa ransomware Nooa ransomware]()

From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
If decryption is not helpful, try another option
Since the Emsisoft decryption tool is helpful only for some of the versions and many users do not prepare proper data backups before being attacked by ransomware, they might often lose access to their files permanently. Not wanting this to happen, users often try to look for other ways to recover files. Sometimes victims even try to pay a ransom but paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, you shouldn’t think that all is lost because data recovery software might be able to help you in some situations. You may be able to recover at least some of the data (each case is different, so there is no guarantee), so it’s worth a try. Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Nooa ransomware Nooa ransomware]()

- Follow on-screen instructions to install the software.
![Install program Install program]()

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()

- Press Scan and wait till it is complete.
![Scan Scan]()

- You can now pick which folders/files to recover – don’t forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()

Getting rid of Nooa virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.


Windows 10 / Windows 8
- Right-click on Start button and select Settings.


- Scroll down to pick Update & Security.


- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.


- Select Troubleshoot.


- Go to Advanced options.


- Select Startup Settings.


- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.


Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.


- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.


- Go back to the process, right-click and pick End Task.


- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.


Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.


- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.


- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Nooa using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Nooa. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Nooa and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Ransomware. Wikipedia. The free encyclopedia.
- ^ Josh Lake. What is RSA encryption and how does it work?. Comparitech. Tech researched, compared and rated.
- ^ Robert Izquierdo. 10 Types of Malware and How to Spot Them. Fool. Software reviews and recommendations.









