Odaku ransomware (virus) - Free Instructions
Odaku virus Removal Guide
What is Odaku ransomware?
Odaku ransomware uses a string of four random characters or files it encrypts
Odaku is a ransomware-type computer infection that targets Windows users. First spotted in the first half of May of 2022, the malware was determined to be a variant of Chaos ransomware, which was first spotted mid-last year. It is derived from a prominent malware known as Ryuk, and some of its versions are known to work as wipers[1] rather than ransomware.
The main goal of cybercriminals behind it is to make users pay a ransom of $25 in Bitcoin, as, upon infiltration, Odaku ransomware encrypts[2] all personal files located on the system. All suchlike files are then appended with randomly-generated four alphanumeric characters, for example, “.04m0” or “.pugg,” which makes them unusable.
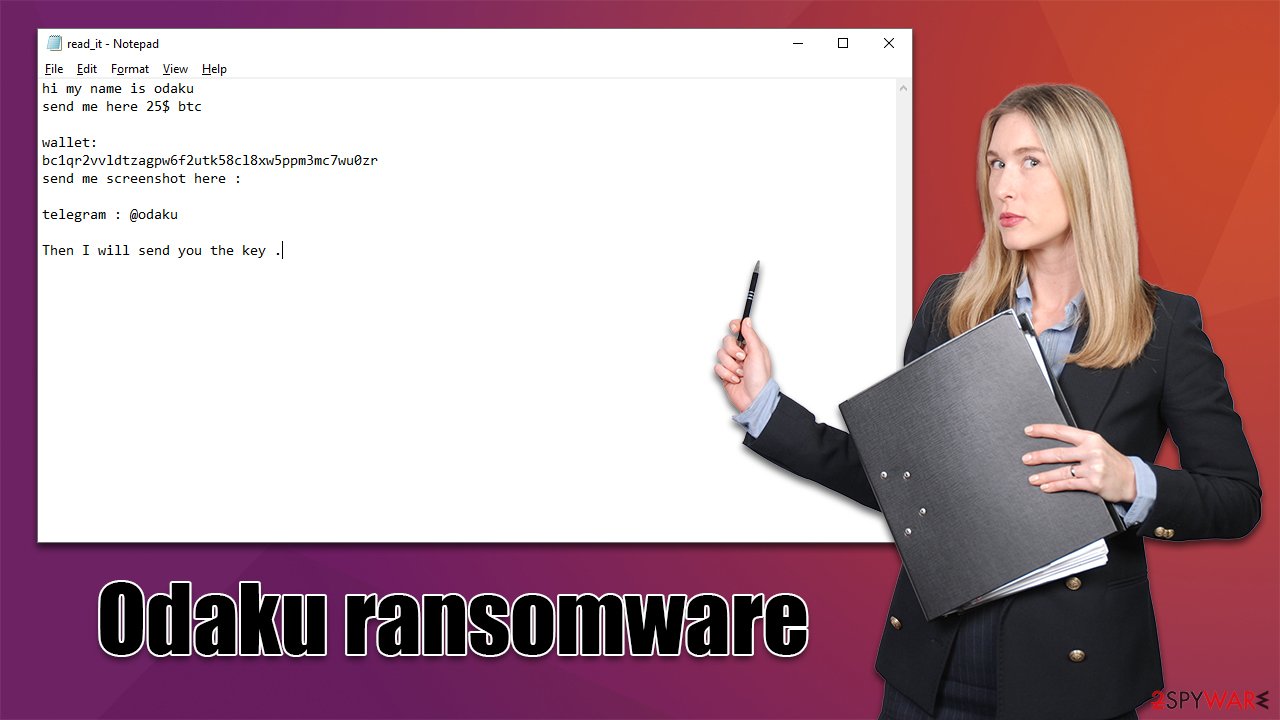
Crooks provide a ransom note read_it.txt that is immediately opened upon the data encryption completion. In a brief message, the attackers claim victims need to contact them using the @odaku account in Telegram after paying the requested sum in Bitcoins to bc1qr2vvldtzagpw6f2utk58cl8xw5ppm3mc7wu0zr crypto wallet.
| Name | Odaku virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | A combination of random four characters is appended to each of the files, for example, a picture.jpg is turned into picture.jpg.xygh |
| Contact | @odaku in Telegram |
| Ransom note | read_it.txt |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
The unusually small ransom request
The ransomware strain the Odaku virus belongs to is relatively new, so it is not uncommon for it to deviate from version to version. While previous versions were found to corrupt or straight out delete personal files, it doesn't seem to be the case here. What is exceptionally unusual here is the request ransom amount, as most crooks usually ask for payments between $500 to $1,000 from the affected computer users. Also, the ransom note is very brief and straightforward:
hi my name is odaku
send me here 25$ btcwallet:
bc1qr2vvldtzagpw6f2utk58cl8xw5ppm3mc7wu0zr
send me screenshot here :telegram : @odaku
Then I will send you the key .
Allegedly, users can receive a decryptor at some point after they transfer the requested money to hackers. However, there are plenty of reasons why security researchers, the FBI,[3] and other authorities do not recommend paying or even contacting the malicious actors.
Why you shouldn't pay
Even though the ransom request is exceptionally low, you shouldn't consider paying. First of all, remember that these people aren't your friends, and they don't particularly care about your well-being. This means that they might not fulfill their promises and not deliver the decryption tool even after the payment is made. While some larger ransomware gangs have a reputation for delivering what they promised, there is simply never a guarantee, especially if the malware strain is new.
Second of all, victims who pay ransoms are unintentionally supporting the cybercriminal activities, as it only proves that the illegal business model works, and the incentive to attack other users increases. There have also been reports that some ransomware authors don't even have a working decryptor themselves.
Odaku ransomware removal and data recovery
Your main goal before proceeding with data recovery is the removal of the infection. Before that, we recommend disconnecting the system from the internet and the network.
1. Disconnect from the internet
Once established, ransomware can be configured to communicate with a remote server, where cybercriminals could start sending commands. For example, they might be able to update malware or even send additional malware payloads. Therefore, until Odaku virus removal is completed, we recommend disconnecting the affected system from the internet.
The easiest way to do this is by plugging out the internet cable or disconnecting the WiFi via the taskbar. If you want to do this on the system level, you can proceed with the following instructions:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
2. Scan with anti-malware
The next step is possibly the most important one – malware removal. While uninstalling ransomware or other malware manually is possible under certain circumstances, it should be left to security experts. Regular computer users should always employ security software, such as SpyHunter 5Combo Cleaner or Malwarebytes, to handle the elimination process of any type of malware.
It is worth noting that some ransomware might self-destruct after its initial job of data encryption is complete, although there is plenty of malware that continues to encrypt everything that is brought in after the initial infection point. Also, malware is commonly distributed in bulks, and ransomware is not an exception.
3. Attempt to recover files
File encryption and ransomware infection are two independent processes (although the latter would not be possible without the former). However, it is important to understand that malware performs various changes within a Windows operating system, fundamentally changing the way it works. If these changes are not reverted by the security software, successful data recovery could be compromised once more.
That being said, the opposite is true: if specialized software would be used on encrypted files, it can permanently damage them, and even a working decryptor would no longer be successful. Thus, before proceeding, make sure you copy all the encrypted data onto another medium. Of course, if you have backups, you don't need to do any of this – as long as the malware is terminated from your device, you can restore files right away.
If you did not have working backups, the possibility of restoring Odaku ransomware-encrypted files is relatively low. Data recovery software might be able to restore at least a portion of the data:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Odaku ransomware Odaku ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Security experts are known to work on decryption tools for major ransomware strains. In some cases, bugs[3] within the encryption process can be found or criminals' servers seized by authority agencies. In any case, you could look for decryptors on the following websites, although keep in mind it might take a while until there's a working one made.
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors
![No More Ransom Project No More Ransom Project]()
Attempt to fix your system files
Malware can cause tremendous damage to Windows systems to the point where a complete reinstallation could be required. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Antivirus software can't repair damaged files, and a specialized app should be used instead.
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Kinza Yasar. What Is the Wiper Malware? Is It Worse Than a Ransomware Attack?. MakeUseOf. Hardware reviews and tech news.
- ^ What is Data Encryption?. Kaspersky. Security research blog.
- ^ D. Howard Kass. FBI Director Wray Tells Ransomware Victims Not to Pay Up. MSSPAlert. A Cyber Risk Alliance Resource.













