Paradise ransomware / virus (Virus Removal Instructions) - Jul 2020 update
Paradise virus Removal Guide
What is Paradise ransomware virus?
Paradise virus is a ransomware that is using .xyz as the newest extension to mark encrypted files

Paradise ransomware is a crypto-virus known as a dangerous cyber threat that has more features than typical ransomware. It does not only encrypt files using RSA-2048 encryption algorithm on the victim's computer but has also been operating as ransomware-as-a-service (RaaS).[1] The original version of the virus appends .paradise file extension to the targeted data. However, it has been updated several times, so its variants append one of these extensions: [id-].[yourencrypter@protonmail.ch].b29; .{help@badfail.info}.paradise; .sell; .ransom; .logger; ._V.0.0.0.1{paradise@all-ransomware.info}.prt, .VACv2, .CORP, .xyz. Once it's done, malware delivers ransom-demanding instructions in PARADISE_README_help@badfail.info.txt, #Decrypt My Files#.txt, #DECRYPT MY FILES# .html, PARADISE_README_paradise@all-ransomware.info.txt or Instructions with your files.txt files. The more recent version VACv2, came out during the Holiday season of 2018 and is using RSA-1024 cryptography for file-locking and __{}.VACv2 as a pattern for the file extension.
| Summary | |
| Name | Paradise |
|---|---|
| Type | Ransomware |
| Danger Level | High. Makes system changes, can install malicious components, encrypts files. |
| Symptoms | Inability to open files due to the unknown extension, programs or files are installed on the computer, general slowness of the machine. |
| Cryptography | RSA-2048 and RSA-1024 |
| File Extensions | .paradise, .sell, .ransom, .logger, _V.0.0.0.1{paradise@all-ransomware.info}.prt, .{help@badfail.info}.paradise, [id-].[yourencrypter@protonmail.ch].b29, __{}.VACv2, _%ID%_{alexbanan@tuta.io}.CORP, .xyz, .666 |
| Ransom note | #Decrypt My Files#.txt, #DECRYPT MY FILES# .html, PARADISE_README_paradise@all-ransomware.info.tx, ID_CLIENT_help@badfail.info.txt, PARADISE_README_help@badfail.info.txt, $%%! NOTE ABOUT FILES -=!-.html, Instructions with your files.txt, noood.txt |
| Elimination | Use FortectIntego Paradise ransomware removal and virus damage termination |
Nevertheless, Paradise ransomware operates as RaaS; its activity is still quite low, the fact that it is distributed as RaaS might be an ominous sign since other less experienced crooks might pick up the code and boost its distribution. However, during its lifetime, researchers haven't detected its dangerous variants. Though, developers released a new version themselves.

However, the original version of Paradise malware encodes data with the RSA-2048 algorithm[2] and appends .paradise or other file extensions along with the email referrer, e.g., sample1.jpg[random characters].[info@decrypt.ws].paradise. Additionally, malware overwrites the RSA key which was used for data encryption with a master key and leaves the new file %UserProfile%\DecriptionInfo.auth. Though data recovery becomes nearly impossible without backups.
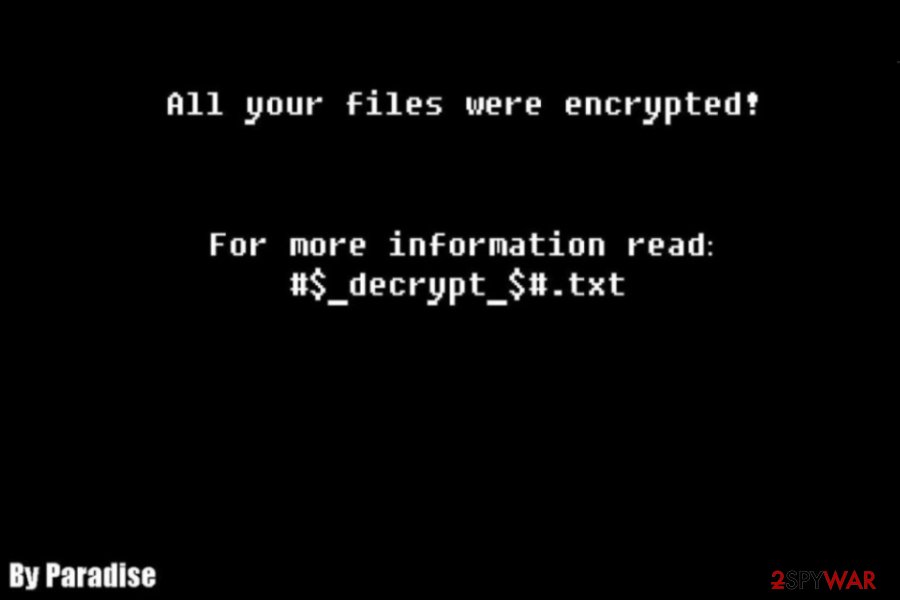
Following the encryption, ransomware launches a black wallpaper with a few words:
All your files were encrypted!
For more information read: #_decrypt_$#.txt
By Paradise
The mentioned file is a ransom note where crooks urge victims to pay as soon as possible since the price directly depends on how fast they will contact the perpetrators. However, the final deadline is 36 hours. Victims are asked to contact authors of Paradise virus using on the following emails:
- tankpolice@aolonline.top
- edinstveniy_decoder@aol.com
- info@decrypt.ws
- paradise@all-ransomware.info
- paradise@all-ransomware.info
- decryptdocs@msgsafe.io
- decryptdocs@firemail.cc
Cybercriminals also grant a chance to decrypt a couple of files for free. However, such promises should not be trusted.[3] It might be the only files that you managed to get after the virus attack. Thus, it's better to remove Paradise from the computer and use backups or alternative recovery solutions.
Regarding the latter email address, it is possible to assume that that the malware is related to BTCWare family of ransomware threats as one of the subsidiary versions, Master virus, delivers the same email address. If that is the case, then there are chances that free BTCWare decrypter might be of use in dealing with this cyber threat. However, in order to try this tool, you have to remove Paradise ransomware from the computer first.
We want to discourage you from manual Paradise virus removal because it may lead to irreparable damage to the system. Malware consists of countless files, might bring other malware to the system and affect legit Windows processes. Hence, only reputable security software, such as FortectIntego or Malwarebytes, can help to clean the PC.
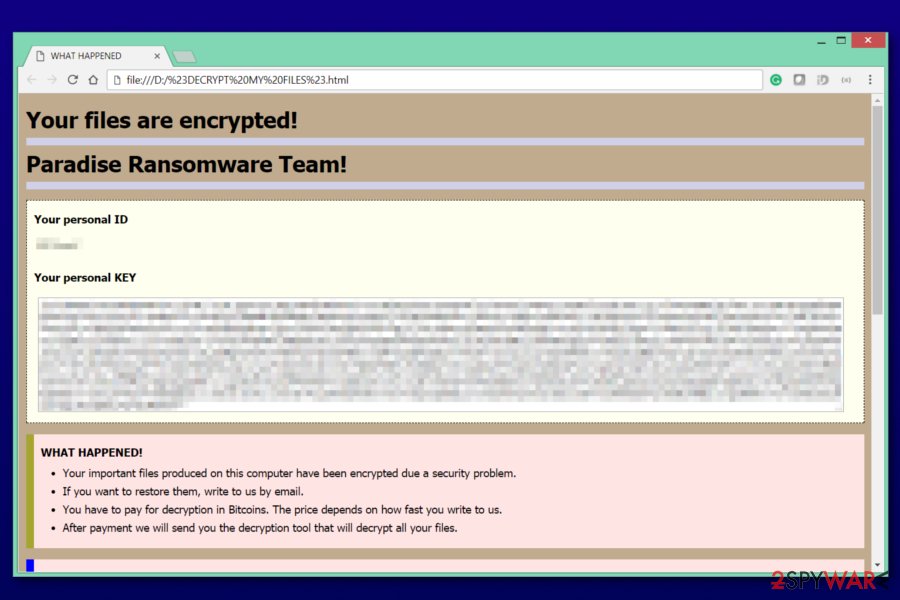
Paradise virus was updated in March 2018
Paradise malware has never been among the most dangerous cyber threats. However, developers of ransomware decided to come back with a new version. Security experts uncovered that in early March the new virus version started appending [id-].[support@all-ransomware.info].sell file extension. Later that month, two more extensions were added – [id-].[].ransom and [id-].[].logger.
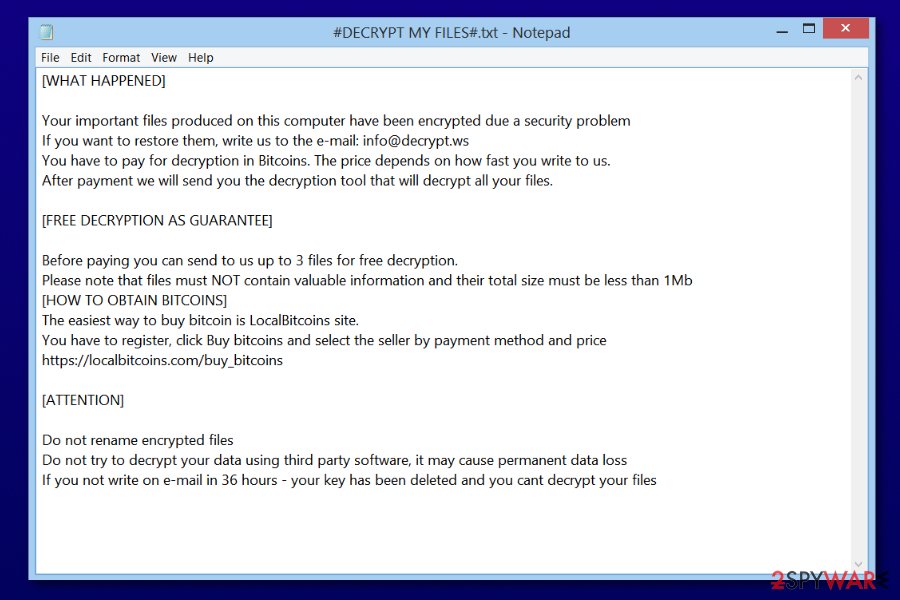
However, these versions still use the same unbreakable encryption method. Hence, only backups can help to fully survive after Paradise virus attack. Following the encryption, it also delivers a ransom note called #DECRYPT MY FILES# .html. Crooks ask to pay the ransom in Bitcoins:
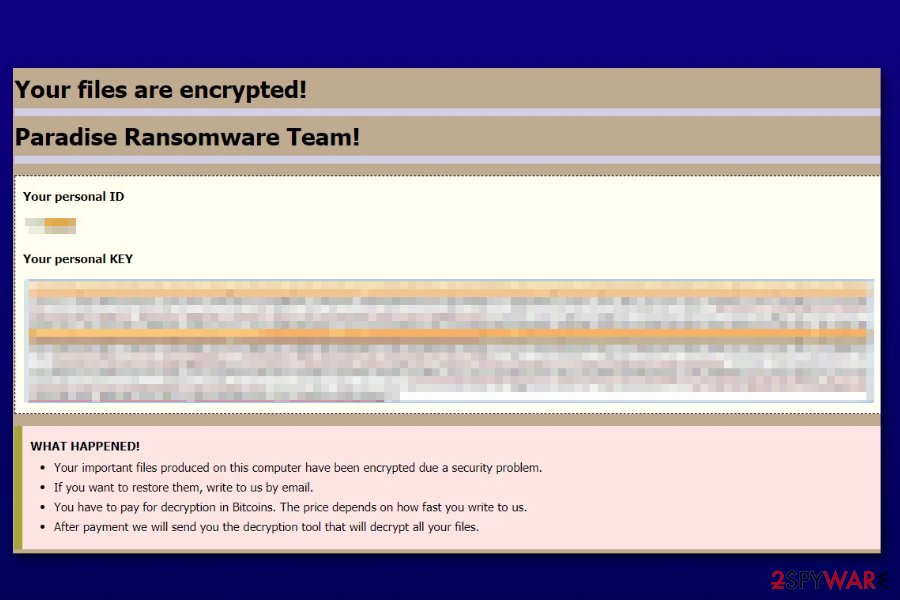
WHAT HAPPENED!
Your important files produced on this computer have been encrypted due a security problem.
If you want to restore them, write to us by email.
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
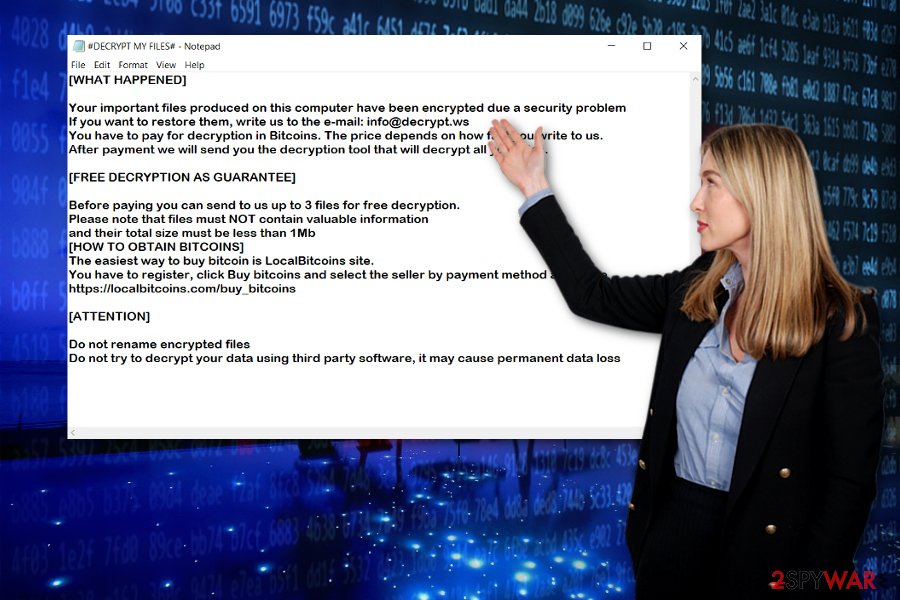
After payment we will send you the decryption tool that will decrypt all your files.FREE DECRYPTION AS GUARANTEE!
Before payment you can send us 1-3 files for free decryption.Please note that files must NOT contain valuable information. The file size should not exceed 1MB. As evidence, we can decrypt one file.
Despite the fact that newest versions are not decryptable too, instead of paying the ransom, get rid of Paradise virus. Third-party tools might help to decrypt your files. Additionally, researchers might soon create a decryptor which might help you with data recovery too. You can find the removal guide and data recovery instructions at the end of the article.
Authors of Paradise ransomware present a new version in June 2018
After a few months since the last update, developers of Paradise virus came back with a new version. The cryptography and operation mechanism do not seem to change a lot compared to the previous versions. However, the significant feature of malware is new file-extension.
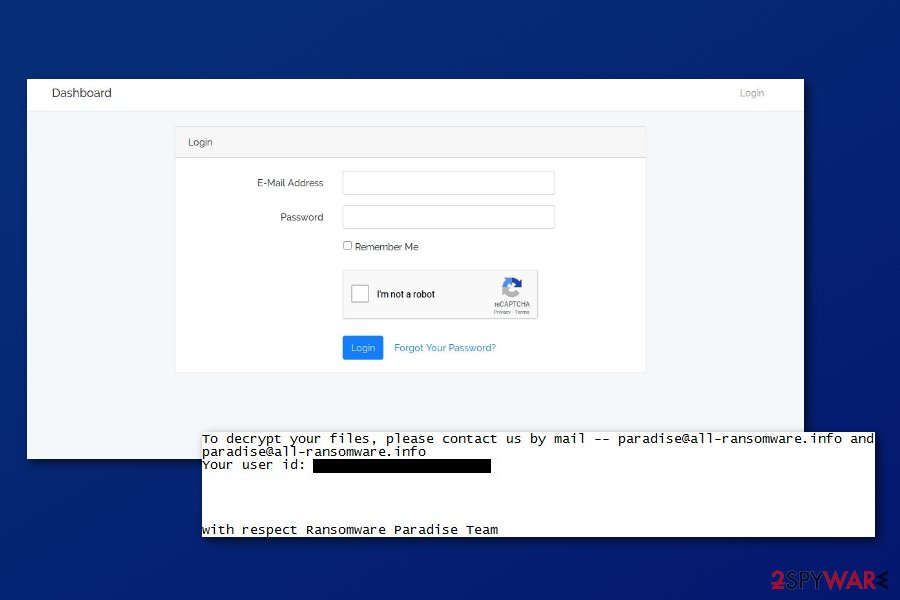
Since June 2018, ransomware has been spotted adding V.0.0.0.1{paradise@all-ransomware.info}.prt file extension to documents, multimedia, databases, and other popular files that are stored on the affected machine. Soon after the encryption, it also delivers a ransom note in PARADISE_README_paradise@all-ransomware.info.txt which gives the following information:
To decrypt your files contact us by email — paradise@all-ransomware.info and paradise@all-ransomware.info
Your user id: [redacted]with respect Ransomware Paradise Team
No matter how respectful malware creators try to be, you should not contact them and follow their data recovery instructions. They will ask to pay in Bitcoins or other cryptocurrencies for the decryptor that might not even exist. Therefore, it is highly recommended to get rid of Paradise ransomware instead of dealing with cybercriminals. After virus removal, you can try various third-party tools or use your own backups and restore encrypted files.
Paradise ransomware virus released two new versions during the Holiday season in 2018
Malware researchers are not sleeping as well as malicious actors. Thanks to Michael Gillespie ans MalwareHunterteam new versions of Paradise ransomware were discovered during the busiest time of the year – Holidays. Ransomware creators took advantage of the time when people are focusing on their families and presents, so made two new variants and released them to the wild.
The first one dubbed VACv2 ransomware was discovered right before Christmas and came with a few additional features to the family. Firstly, this version seems similar because it displays the same ransom note as other variants. In the HTML window named $%%! NOTE ABOUT FILES -=!-.html virus developers demand the payment in Bitcoin.
Both new versions use RSA-1024 army-grade encryption algorithm to encode targeted files. Then files get appendix in a pattern __{}.additional name of the virus variant. The first version discovered before Christmas adds __{}.VACv2 file extension. And later version discovered on the first week of January 2019 appends data using _%ID%_{alexbanan@tuta.io}.CORP.
No new features added to the mix with these versions, except the different file extensions. Paradise ransomware developers seem to change little parts of the code for each new version only. However, there is no official decryption tool developed and you should focus on virus removal using FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes.
Recently, a cybersecurity company known as Malware Hunter Team discovered yet another ransomware related to the infamous Paradise virus. This one is Xyz according to the .xyz appendix which is added to all encrypted files. As other of its kind, this dangerous cyber threat is also using unique encryption algorithms to lock documents on the targeted computer.
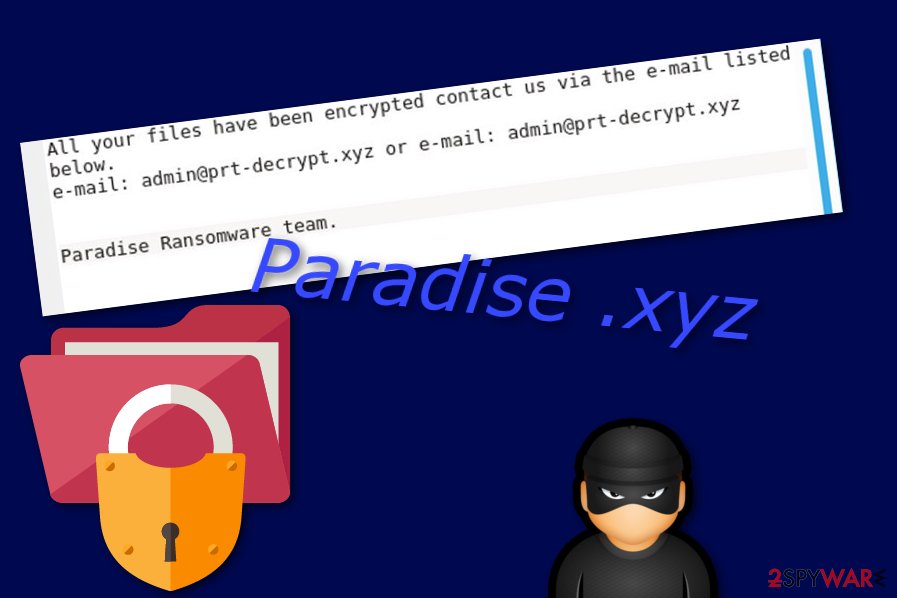
After secret encryption, Paradise – Xyz ransomware provides a message that is named “Instructions with your files.txt”. The note announces about the stealth invasion and provides admin@prt-decrypt.xyz or admin@prt-decrypt.xyz email addresses as ways to make contact with the cybercriminals and discuss all terms related to the ransom price and decryption tool. The ransom message claims:
All your files have been encrypted contact us via the e-mail listed below.
e-mail: admin@prt-decrypt.xyz or e-mail: admin@prt-decrypt.xyz
Ransomware payload is delivered using spam email campaigns
Mostly, ransomware threats are spread via multiple methods:
Ransomware is most likely to infiltrate the computer after opening an obfuscated email attachment. Therefore, you have to be vigilant and avoid opening each received email. Always make sure that you were supposed to receive it and there are no hints that it was sent by criminals.
Malware executable might also spread as fake programs or updates. Such content might be available in shady file-sharing sites, torrents or pop-up on the screen in the form of online ad. Hence, use only reliable sources for downloads and updates.
Finally, keep all the programs and operating system up-to-date. Malware might take advantage of security flaws and get into the system. Additionally, install a reputable antivirus and create backups – they will be very important in case of the attack.
Make sure to get rid of Paradise virus completely
In order to remove Paradise virus from Windows, you will need to scan the device with anti-virus and malware elimination utilities. We recommend using FortectIntego or SpyHunter 5Combo Cleaner. In case you cannot access them or they do not respond because of the ransomware, reboot the system in Safe mode or use system restore to disable the virus first. You need to make sure that each component that is related to the ransomware cyber threat has been eliminated successfully, otherwise, the infection might renew itself with the next computer boot.
After Paradise ransomware removal is completed, you may attempt to decode data with alternative security applications and backups[6]. French user[7] should be wary of the threat as it is likely to target them more actively. Although, there is a high possibility to get this infection no matter where in the world you are since the ransom message is written in English.
Getting rid of Paradise virus. Follow these steps
Manual removal using Safe Mode
Restart the device in Safe mode to launch the security tool and eliminate Paradise malware.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Paradise using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Paradise. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Paradise from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Paradise, you can use several methods to restore them:
The benefits of Data Recovery Pro
This tool is specifically created to restore damaged files after a system crash, but you may try it to recover your files encrypted by Paradise crypto-virus.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Paradise ransomware;
- Restore them.
Will Shadow Explorer help restore files?
The key advantage of the software is its ability to use shadow volume copies for data recovery. Since there is no information on whether the virus deletes the copies beforehand, you may stand a chance.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
The legitimate Paradise decrypter is not available yet
Unfortunately, security experts haven't developed the official Paradise decrypter. Bear in mind that if you purchase the decryption software offered by the ransomware developers, it may only lead your system to even more problems.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Paradise and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Esther Kezia Thorpe. The rise of Ransomware-as-a-Service. IT Pro. Business Analysis and Insight.
- ^ RSA (cryptosystem). Wikipedia. The free encyclopedia.
- ^ Paying for ransomware could cost you more than just the ransom. Trend Micro Blog. Cyber security news.
- ^ Margaret Rouse. Email spam. Search Security. Tech Target.
- ^ Exploit Kit. Trend Micro. Security experts.
- ^ Linas Kiguolis. The Importance of Plan B: Why Data Backups are Necessary. TecoReviews. The Ultimate Destination for News and Reviews.
- ^ Get rid of malware. Lesvirus. Spyware and security news in French.





















