Qscx ransomware (Decryption Methods Included) - virus
Qscx virus Removal Guide
What is Qscx ransomware?
Qscxfile virus – a file-locking parasite that demands a ransom of $490 to $980 to regain access to encrypted data
Qscx ransomware is a new malware variation from the Djvu family that aims to lock your personal files and demand a ransom in Bitcoins. If your device gets infected, all non-system data (databases, documents, archives, etc.) is encrypted and rendered useless within a couple of minutes. Please rest assured that this cryptovirus can be removed and your data restored using alternative means, not involving the evildoers behind it.
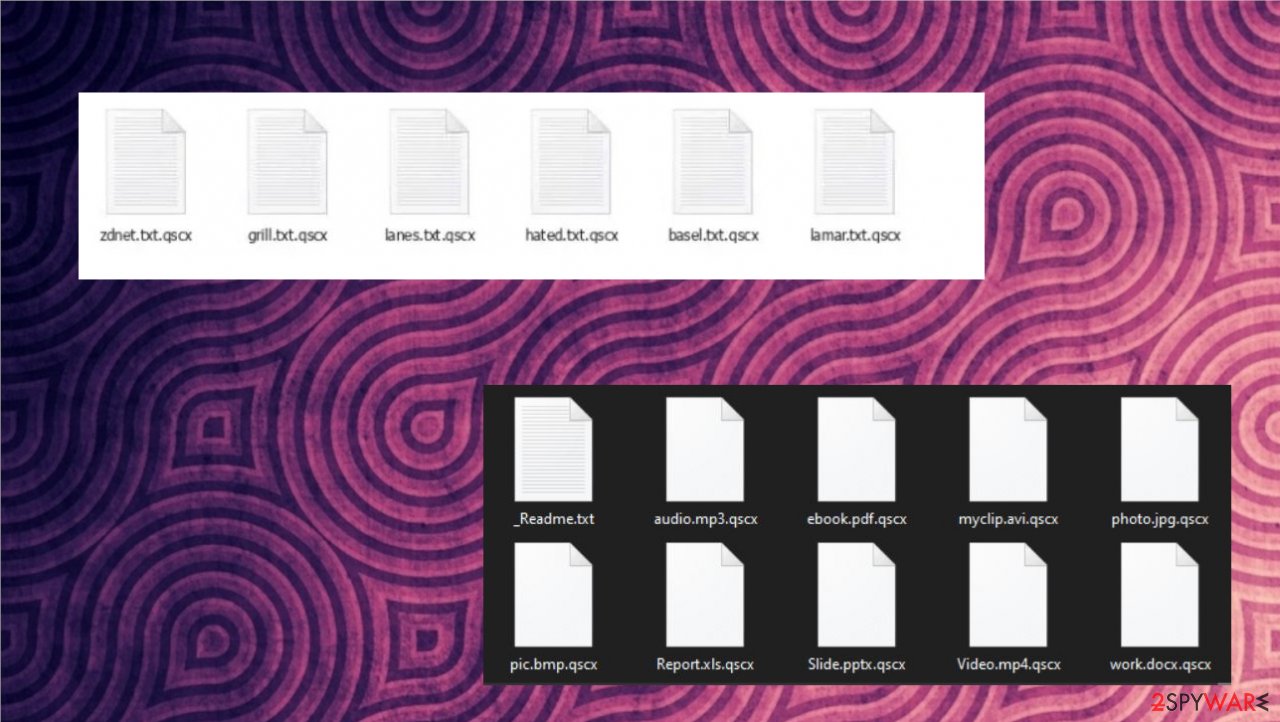
It's easy to determine if this file-locking parasite encrypted your files, as the .qscx extension is upended to all original filenames. Thus if you had a file named asd.pdf, it would now appear as asd.pdf.qscx. One other infection symptom is the _readme.txt file, which can be found on the desktop and in some affected folders.
That's a ransom note in which the developers of the malware state their instructions and demands. Here's the message that they send to their victims:
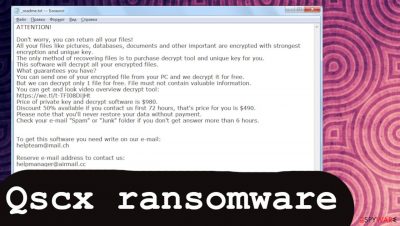
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-9CYW99VhUR
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
helpteam@mail.chReserve e-mail address to contact us:
helpmanager@airmail.ccYour personal ID:
As you can see, the cybercriminals' preferred method of communication is email. Therefore, they provide two of them (helpmanager@airmail.cc or helpteam@mail.ch) and encourage victims to contact them immediately to start the negotiations.
The message contains persuasion techniques to trick victims into making rash decisions. The most notable of which is the 50% discount on the ransom amount offered for people that contact the developers of Qscx virus within three days of the attack.
This benevolent seeming offer would reduce the amount needed to purchase the necessary decryption software in cryptocurrency Bitcoin from $980 to $490. Although this amount doesn't seem very high, please keep in mind that threat actors thought of this sum for the same reason.
But by succumbing to their demands, you would contribute to expanding their illegal business empire. With your money, they could research more effective ways to attack more innocent people's devices and develop more devastating computer infections.
And by the way, there's no need to pay the criminals as you could recover encrypted .qscx files for free. You can try out Emsisoft's free decryption software and other data recovery options that we've listed below. But before trying any of those tools, you will have to remove the infection, and we're going to tell you how.
| Name | Qscx virus |
|---|---|
| Type | Ransomware, file-locker, cryptovirus |
| Family | Djvu/STOP |
| Symptoms of infection | Personal data is renamed and can't be accessed; you can't open some programs and security-related websites; the device is running visibly slower; ransom notes found throughout the device |
| Ransom note | _readme.txt |
| Appended file extension | .qscx |
| Data recovery | To regain your data, please try out our suggested methods listed within the article |
| Elimination | You should perform ransomware removal with trustworthy security tools. Recommended ones are listed below |
| System health check | To evade abnormal PC behavior after you remove the infection, restore Registry keys and values and other core system settings by running a full system scan with the FortectIntego PC repair tool |
The data recovery process begins with Qscx virus removal
We're happy you decided not to pay the criminals and remove the ransomware virus instead. We're even more excited that you've picked us to accompany you on this journey. The removal process, as well as this article, is not very easy, but we've prepared illustrated instructions to get you through it.
First of all, before you remove Qscx file virus, you have to extract all essential files from the infected device. Next, copy what's important to you to an offline storage device, such as a USB drive, SSD, or anything alike. Then disconnect it and store it somewhere nearby.
Then download Malwarebytes. According to tons of user reviews, this free but trustworthy anti-malware software is one of the best security tools on the market. After installing it, make sure to update its virus database with the latest signatures. Then initialize a full system scan.
It should be finished within 5 to 10 minutes, depending on how many system sectors were damaged and how widely the infection spread. When the scan is finished, agree to whatever the reliable tool suggests removing. After restarting your device, the infection should be eradicated.
However, in some cases, Qscx ransomware can block you from opening any security-related software or websites. For example, that happened with Pahd and Paas viruses that derive from the same family. Ransomware does that by modifying core system files to establish persistence. If you can't download the recommended software or open it, you will have to do that in Safe Mode with Networking, and here are instructions on how to access it in Windows 10/8:
- Right-click on the Start button and select Settings.
- Scroll down to Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
- Select Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.
- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.
![Enable safe mode Enable safe mode]()
If your device runs on Windows 7/Vista/XP, you have to restart your computer and start taping on the F8 button as soon as the PC turns on. Different motherboard models might require you to press on F2, F12, or Del buttons constantly. When the Advanced Boot Options window shows up, select the Safe Mode with Networking from it.
Once you reboot your computer in this mode, you can easily access all security-related websites and download any anti-malware software that you prefer. Although by using our recommended software, such as SpyHunter 5Combo Cleaner, you can rest assured that the infection will be dealt with swiftly.
Proper AV engines are needed to remove Qscx virus and similar cyber threats and protect your devices from them. Djvu family ransomware is usually distributed via file-sharing platforms. We would advise not to use them, but people seem to enjoy getting copyrighted material for free.
According to our fellow cybersecurity researchers from LesVirus,[1] most viruses from this lineage were hiding in various software cracks uploaded to most popular torrent sites. Thus, upon downloading a camouflaged file, a dependable security tool would immediately isolate it and prevent it from infecting your system.
Repairing damaged PC sectors
As stated before, Qscx ransomware and other parasites from its family don't encrypt system files. However, it does extensive modifications that, even after the virus removal, could lead to system failures, such as the Blue Screen of Death (BSoD),[2] severe lag, etc.
It would be practically impossible to determine every altered setting, even for IT professionals. Therefore, we recommend using the FortectIntego software – an automatic PC repair tool. By completing a full system scan with it, you will see all system irregularities that the ransomware has caused, and you can fix them with a push of a button.
All you need to do is:
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
- The analysis of your machine will begin immediately
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
The FortectIntego system diagnostics software is a lifesaver when it comes to patching up your device after a serious malware infection. It will resolve all Windows-related inconsistencies, including broken DLLs, Registry keys and values, etc. Make a habit of running it on your device at least once a week to ensure a stable working environment.
Regain access to the encrypted files for free
If you didn't take any shortcuts, meaning you removed the ransomware and resolved system-related issues, you could proceed with this step. However, please note that if any of the previous steps are missed, it's not safe to recover Qscx files as the infection could renew with the next reboot.
If you've kept backups of your data, then there's no need to waste any time. It's safe to restore your files now. As we mentioned before, if you didn't, there's no need to forward any money to the criminals behind this cyberattack. There are alternative ways to restore your files.
The main one is Emsisoft's decryption software. It's completely free, as the company dedicates its time to help Djvu ransomware victims get out of this uncomfortable predicament without losing a dime. Please note that it's not meant for this specific ransomware but the whole family.
Therefore there's no guarantee that it will work 100% of the time. But this free decryption software is your best hope, as it helped numerous ransomware victims to recover their data. You will need to:
- Download the app from the official Emsisoft website.
- After pressing the Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe, should show up – click it.
- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.
![Qscx ransomware Qscx ransomware]()
- Press Decrypt.
![Qscx ransomware Qscx ransomware]()
There are three viable outcomes that this tool can present. First, if a “Decrypted!” prompt appears – needless to say, that your files are unlocked and ready to use. If “Error: Unable to decrypt file with ID:” is shown, that means that the company hasn't yet received a sample of Qscx file virus and hasn't produced a necessary algorithm yet.
The worst-case scenario is when the “This ID appears to be an online ID, decryption is impossible” message appears. That suggests that the Emsisoft decryptor is unable to decrypt the files. But please don't panic as there are other data recovery options, and we've included them in our instructions section at the bottom of the article. Please try them out.
And remember that staying attentive to what's being installed on your device, not using file-sharing platforms to access copyrighted content for free, and scanning your device with a trustworthy anti-malware tool twice a week could save you from nightmares that various malware[3] causes. Stay safe.
Getting rid of Qscx virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Qscx using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Qscx. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Qscx and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ LesVirus. Lesvirus. Spyware news and securty.
- ^ Chris Hoffman. Everything You Need To Know About the Blue Screen of Death. Howtogeek. Online technology magazine.
- ^ Robert Izquierdo. 10 Types of Malware and How to Spot Them. Fool. Software reviews and recommendations.
























