RaZiO ransomware (Free Instructions)
RaZiO virus Removal Guide
What is RaZiO ransomware?
RaZiO ransomware: a version of a well-established malware family
RaZiO is a ransomware-type virus that was first spotted in mid-December of 2021. It belongs to the Xorist malware strain, which was created back in 2012, and since then has been increasingly active, with many new versions coming out on regular basis. Considering how successful ransomware attacks have been in recent years in the wake of a global pandemic, it seems like this trend will not change any time soon, so companies and regular PC users should take all the available precautionary measures to prevent this devastating threat from entering their systems.
The main goal of the RaZiO virus is to find and encrypt all non-system files on a Windows machine and those connected to the breached network. In some cases, cybercriminals also target backup systems through vulnerabilities within locally-used software for management. Likewise, there are many other ways malware would be implemented on regular computer users' machines, e.g., software cracks, spam emails, malicious ads, fake updates, etc.
Upon being installed on the system, ransomware does not start data encryption, however. It first needs to make a lot of changes for the whole process to be smooth and successful – deletes shadow copies, creates new processes and tasks. As soon as Windows is compromised, it begins the encryption process with a TEA encryption algorithm, which locks access to pictures, documents, databases, and other personal files, happening the .RaZiO extension in the process.
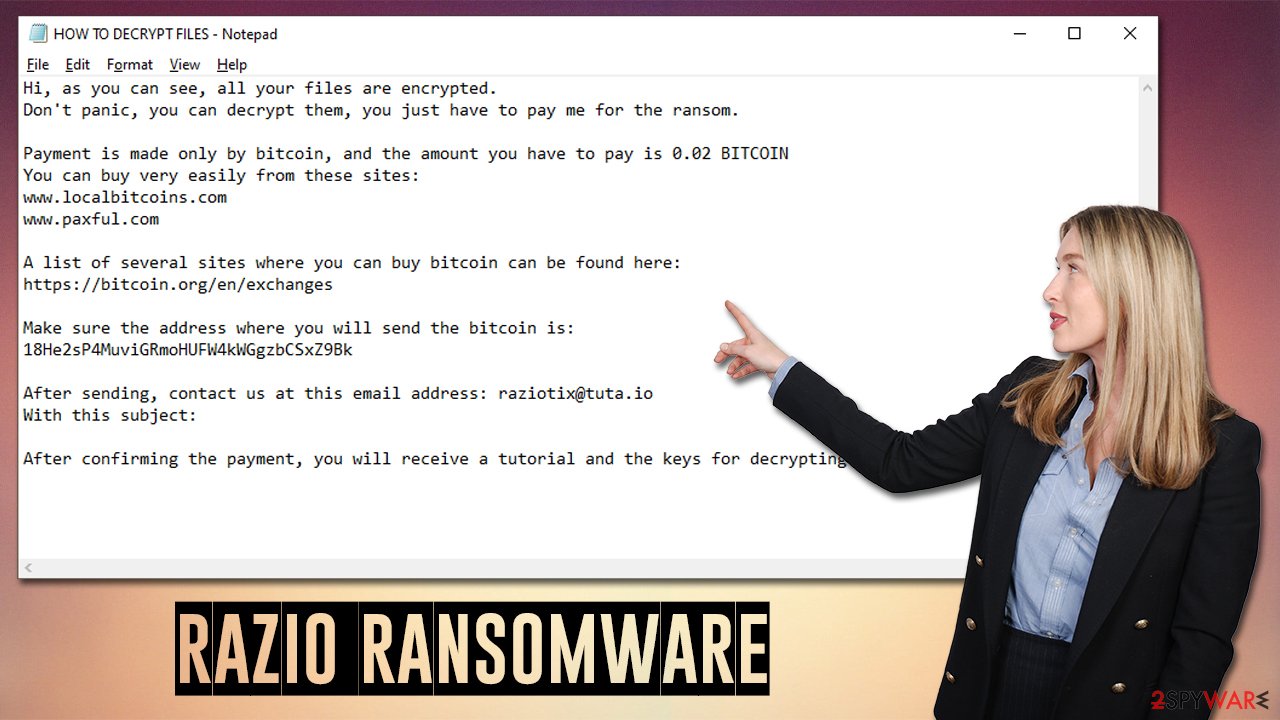
As soon as work is done, the ransomware delivers a note titled HOW TO DECRYPT FILES.txt, changes the desktop wallpaper, and shows a pop-up titled “Error.” All of these include the same message text, which represents cybercriminals' demands. They ask victims to deliver 0.02 Bitcoin to the 18He2sP4MuviGRmoHUFW4kWGgzbCSxZ9Bk address and then contact them via the raziotix@tuta.io email to allegedly retrieve the decryption tool.
We strongly recommend you avoid contacting the attackers, as they might be lying about providing you with a working decryptor. Instead, we recommend checking the instructions below on how to remove the virus and restore files using alternative methods.
| Name | RaZiO ransomware |
|---|---|
| Type | Ransomware, file locking virus |
| malwre family | Xorist |
| File extension | .RaZiO |
| Ransom note | HOW TO DECRYPT FILES.txt, “Error” pop-up window |
| Contact | raziotix@tuta.io |
| File Recovery | If no backups are available, recovering data is almost impossible. However, we suggest you try the alternative methods that could help you in some cases – we provide them below |
| Malware removal | Perform a full system scan with powerful security software, such as SpyHunter 5Combo Cleaner |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
The ransom note in detail
We have previously discussed ransomware such as Yjqs, Mljx, Ubrhnqznw, and many others – all of them employ the note, as it is vital for any ransomware to be successful. Without the details provided within it, victims would not be able to contact crooks and send them the requested money, which would obviously not benefit them.
Therefore, cybercriminals try to always ensure that the ransom note reaches the victims. The absence of a ransom note after being infected might indicate one of the two things – it is of a destructive nature, or it was failed to be delivered. The latter can occur due to various circumstances, e.g., bugs[1] within the malicious code.
Therefore, RaZiO ransomware authors made a user that the message reaches users – they change the desktop wallpaper, show a pop-up message, and deliver a text file. All of these include the same message, which reads:
Hi, as you can see, all your files are encrypted.
Don't panic, you can decrypt them, you just have to pay me for the ransom.Payment is made only by bitcoin, and the amount you have to pay is 0.02 BITCOIN
You can buy very easily from these sites:
www.localbitcoins.com
www.paxful.comA list of several sites where you can buy bitcoin can be found here:
https://bitcoin.org/en/exchangesMake sure the address where you will send the bitcoin is:
18He2sP4MuviGRmoHUFW4kWGgzbCSxZ9BkAfter sending, contact us at this email address: raziotix@tuta.io
With this subject:After confirming the payment, you will receive a tutorial and the keys for decrypting the files.
Just as it is typical, cybercriminals try to pretend to be friendly just to increase the chances of victims paying them. However, keep in mind that they are not your friends, and all they care about is getting the bitcoin. Trusting them is highly dangerous, as you might end up losing not only your personal files but also a big chunk ok money.
It is important to note that only cybercriminals have the decryption key for your files, as it is unique to you. Thus, while they might be correct about this, trusting them is very risky – authorities such as the FBI[2] and security researchers advise not cooperating with crooks in these situations.
The correct removal steps explained
Most ransomware victims have never experienced a ransomware attack before. This is not surprising, as users are commonly unaware of malware distribution techniques or sometimes choose to deliberately risk it when visiting high-risk websites or downloading software cracks.
This is why, the infection often comes as a shock, although panicking is the worst you can do. It is important to perform remediation actions in the correct order, or you might risk losing your files forever. As we already explained, trusting cybercriminals is not advisable, as it might cause even more losses.
Once implemented, ransomware often establishes a connection with a remote server, known as Command & Control. With the help of these connections, the attackers can send various commands to be executed remotely. Thus, before you do anything else, make sure you disconnect your PC from the internet and network.
Malware removal
If you use a computer network and need to disconnect many machines, you should do it in the following way:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Once the network access is terminated, you should now prepare backups of the encrypted files (otherwise, they might be corrupted during the remediation process). Of course, if you have working files on a separate medium you can recover from, this step is not mandatory. Having original copies of encrypted files can serve you as a real way out once security researchers developer a working RaZiO ransomware decryptor.
The next step is very important – it is the correct removal of malware, which should be performed with powerful security software, such as SpyHunter 5Combo Cleaner or Malwarebytes. In some rare cases, the virus might prevent your security software from doing its job, so accessing Safe Mode can fix this issue.
Data recovery
Once you have backups ready, you should then attempt to recover your data. It is important to note that antivirus would not restore your files back to normal – it simply deletes the infection and all its malicious files so that the unwanted activity can no longer continue. Your best bet is trying data recovery software:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![RaZiO ransomware RaZiO ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Check for other decryptors
There are hundreds of security companies and organizations that are working hard to battle ransomware creators. In some cases, servers where decryption keys are held, might get seized,[2] which allows them to be released to the public. Below you can find the most prominent parties that are involved in free data decryption services, which have already helped millions of victims. Keep in mind that an alternative decrytpion tool might take a while to create (if it is possible at all).
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Tips for post-elimination
There are several things you can do after you have dealt with ransomware infection. First of all, we recommend you take care of your Windows computer health. After malware infection, some files and components might get damaged, which antivirus software can't remediate. This could result in system crashes, errors, and other stability issues. To remediate this issue automatically, we recommend you employ FortectIntego PC repair software. Alternatively, you might have to reinstall Windows altogether, which might be a tedious process.
Second, you should ensure that you have working backups that you keep on a separate medium. While you can manually transfer files onto a USB flash or another storage device, we recommend you set up OneDrive or Google Drive:
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.
![Go to OneDrive settings Go to OneDrive settings]()
- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.
![Add OneDrive account Add OneDrive account]()
- Once done, move to the Backup tab and click Manage backup.
![Manage backup Manage backup]()
- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.
![Pick which folders to sync Pick which folders to sync]()
After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
- Download the Google Drive app installer and click on it.
![Install Google Drive app Install Google Drive app]()
- Wait a few seconds for it to be installed.
![Complete installation Complete installation]()
- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.
![Google Drive Sign in Google Drive Sign in]()
- Click Get Started.
![Backup and sync Backup and sync]()
- Enter all the required information – your email/phone, and password.
![Enter email/phone Enter email/phone]()
- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.
![Choose what to sync Choose what to sync]()
- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Another useful tip would be reporting the crime to your local authorities. Cybercriminal organizations are often caught and penalized thanks to the tips that are received from victims. Recently, the threat actors behind REvil ransomware were arrested[3] and are likely to face long years in jail. Here are a few links you could use:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Software Bug. Techopedia. Professional IT insight.
- ^ Ransomware. FBI. Federal Bureau of Investigation.
- ^ Ryan Gallagher. Police arrest five people tied to ransomware group REvil. Fortune. Official website.
















