Xorist ransomware / virus (Free Guide) - Decryption Steps Included
Xorist virus Removal Guide
What is Xorist ransomware virus?
Xorist is a file-locker that demands a ransom for the questionable decryption process
Xorist is a ransomware-type virus built on Encoder Builder v.24 from [Pastorok][1], which is sold on the underground forums. Since its emergence in 2016, it remains active and new versions are still actively spreading. There are over 15 different versions with the predominants .PrOtOnIs and .PrOtOnIs.VaNdElIs, .EnCiPhErEd, .1ss33ggur, and .LOCK, . ZoNiSoNaL file extensions.
It is known for forming randomized extensions for each new version, so researchers are not easily indicating that the virus belongs to this particular family.
To encrypt users' files, all members of this ransomware family have been using the same encryption strategy. Typically, they rely on XOR or TEA cryptography, but each version might append a unique file extension and deliver a ransom note in the text file where victims are asked to transfer a specific amount of Bitcoins for data recovery.
Luckily, this ransomware was not the toughest nut to crack. In 2016, Fabian Wosar of Emsisoft deciphered ransomware code and released a free decryption software, which was soon situated among other ransomware decryptors in the NoMoreRansom project managed website. The .73i87Am, .p5tkjw, PoAe2w, and .EnCiPhErEd file extensions are susceptible to the decryptor.
| Name | Xorist |
|---|---|
| Type | Ransomware |
| Versions | .Team Xrat, .XPan, .Zixer2, .Imme, .AvastVirusinfo, .Crypto1CoinBlocker, .Hello, .Cerber_RansomWare@qq.com, .Cryptedx, .Xorist-Frozen, Xorist-.XWZ, .PrOtOnIs, .VaNdElIs,.Mbrcodes, .73i87Am, .p5tkjw, PoAe2w, .EnCiPhErEd, .LOCK, .CerBerSysLocked0009881, .error77002017111, .Blocked2, .TaRoNiS, .brb, .RusVon, .fast_decrypt_and_protect@tutanota.com, .xdata, .SaMsUnG, .antihacker2017, .error, .errorfiles, .@EnCrYpTeD2016@, .pa2384259, .encoderpass, .fileiscryptedhard, .6FKR8d, .EnCiPhErEd, .73i87A, .p5tkjw, .PoAr2w, .1ss33ggur, .ava, |
| Danger level | High (initiates unauthorized system's changes and can cause permanent data loss) |
| Detection | 2016 (actively spreads up in 2021) |
| Distribution | Malspam, exploit kits, drive-by-download, fake software updates, |
| Symptoms | Most of the personal files appended with one of the file extension (the list down below), .txt file as a ransom note available on the desktop, the system runs slower, multiple suspicious files misusing CPU resources, etc. |
| Encryption methods | XOR and TEA |
| Redeem size | Varies from 0.3 to 2 Bitcoins |
| Decryptable | Yes. A free Xorist decrypter is available, but it may not be capable of decrypting the newest versions |
| Elimination | Automatic. Install a professional anti-malware and run a deep scan with it |
| Repair | Since the threat is known for using the powerful functions and evading detection, damaging other parts of the machine, you should repair the damage using FortectIntego |
Previously, the virus was appending .DATA_IS_SAFE_YOU_NEED_TO_MAKE_THE_PAYMENT_IN_MAXIM_24_HOURS_OR_ALL_YOUR_FILES_WILL_BE_LOST_FOREVER_PLEASE_BE_REZONABLE_IS_NOT_A_JOKE_TIME_IS_LIMITED extension to target files on victim's computer. In June 2018, researchers reported about a version that appends a long file extension to each of the targeted documents, pictures, or other files:
.PAY_IN_MAXIM_24_HOURS_OR_ALL_YOUR_FILES_WILL_BE_PERMANENTLY_DELETED_PLEASE_BE_REZONABLE_you_have_only_1_single_chance_YOU_NEED_TO_PURCHASE_THE_DECRYPTOR_FROM_US_FAST_AND_URGENT
When all data is locked, it delivers a ransom note in the same READ ME FOR DECRYPT.txt. file where victims are asked to contact them via repair_data@scryptmail.com and pay 0.8 Bitcoin for Cerber decryption software. However, paying the ransom is not recommended. It's clear that creators of malware are just trying to make as much illegal money as possible by developing new versions of the same virus.
In the second half of March 2018, Xorist-XWZ version appeared. It uses XOR, cipher, and appends .xwz file extension to each encrypted file. Upon encryption, the victim is presented with a ransom note READ ME FOR DECRYPT.txt. Recently, experts announced about PrOtOnIs file virus which is capable of corrupting 111 file types, including:
.1cd, .3gp, .7z, .a06, .ac3, .aleta, .aol, .ape, .arena, .aspx, .avi, .b64, .bak, .bd, .bmp, .cdr, .cer , .csv, .dat, .db, .dbf, .divx, .djvu, .dl0, .dl1, .dl2, .dl3, .dl4, .dl5, .dl6, .dl7, .dl8, .dl9,. doc, .docx, .dwg, .flac, .flv, .frf, .gdb, .gif, .gzip, .htm, .html, .ibk, .ifo, .jpeg, .jpg, .kwm, .ldf, .lnk, .m2v, .max, .md, .mdb, .mdf, .mkv, .mov, .mp3, .mp4, .mpeg, .mpg, .mt0, .mt1, .mt2, .mt3, .mt4 , .mt5, .mt6, .mt7, .mt8, .mt9, .net, .odt, .p12, .pdf, .pfx, .png, .ppt, .pptx, .ps1, .psd, .pwm,. .wk, .wk1, .wk2, .wk3, .wk4, .wk5, .wk6, .wk7, .wk8, .wk9, .wma, .wmv, .xls, .xlsm, .xlsx, .xml, .zip.
All extensions that it has ever used were included in this list:
.antihacker2017; .pa2384259; .hello; .brb; .RusVon; .fast_decrypt_and_protect@tutanota.com; .xdata; .SaMsUnG; .zixer2; .error; .errorfiles; .@EnCrYpTeD2016@; .encoderpass; .fileiscryptedhard; .6FKR8d; .EnCiPhErEd; .73i87A; .p5tkjw; .PoAr2w; .PrOtOnIs; .PrOtOnIs.VaNdElIs; .ava; .xwz; .mbrcodes. .TeamXrat, .XPan, .Imme, .AvastVirusinfo, .Crypto1CoinBlocker, .Cerber_RansomWare@qq.com, .Cryptedx, .Xorist-Frozen, .Xorist-.XWZ, .PoAe2w, .LOCK, .CerBerSysLocked0009881, .error77002017111, .Blocked2, .TaRoNiS, .1ss33ggur.
As you can see, the virus has been updated numerous times. At the beginning of February 2018 is dubbed as Xorist-Frozen. It appends .frozen_service_security@scryptmail.com file extension, generates HOW TO DECRYPT FILE.TXT ransom note, and demands a ransom for a decryptor.
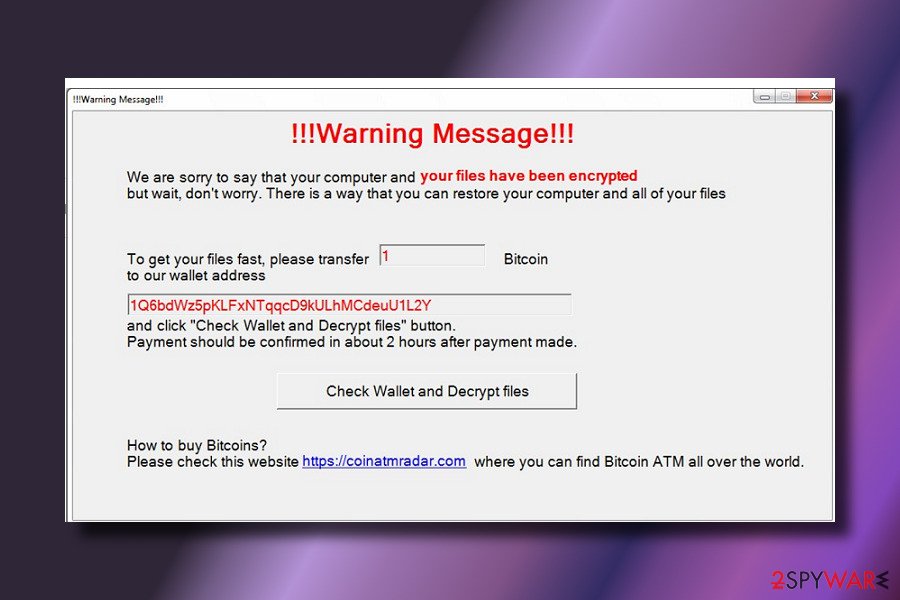
In comparison to other ransomware viruses, this one uses a quite strange communication method. The victims of the original ransomware virus have to send the SMS message to the provided numbers instead of using the Bitcoin payment system.[2]
When the developer of the virus supposedly sends a unique decryption password for the victim. The victim needs to enter this password into a Password Prompt, and then the files should be decrypted. However, the number of attempts to enter the password is limited by the creator of the virus. If the victim exceeds the number of attempts to type in the right password, user’s data is doomed.
In the meanwhile, one of ransomware's versions, called Frozen virus, does not intimidate people by a number of an excessive number of attempts to enter the code. The victim is informed that the server will destroy the key within 36 hours after the encryption, but the payment has to be transferred within 24 hours.
Following these orders is neither necessary nor recommended[3] because ransomware is already decryptable. Even its latest variant Cryptedx ransomware can be beaten. Thanks to security researchers, you can use free software to recover corrupted data. Not all the versions can get decrypted, so make sure to fully clear the threat off of the PC before running any additional processes or adding external devices. 
Variants of Xorist ransomware virus
Team Xrat version was discovered in August 2016. It has been targeting Portuguese[4] computer users by encrypting files with RSA-2048 encoding system and hiding the decryption key. Malware appends .C0rp0r@c@0Xr@ file extension to the encrypted data, and delivers a ransom note “Como descriptografar seus arquivos.txt.”
Victims are told to contact authors of this virus via corporacaoxrat@protonmail.com email address and learn how to obtain the decryptor. However, doing that is unnecessary because ransomware can be decrypted for free with Team Xrat decryption tool.
XPan ransomware emerged in September 2016. It uses AES-256 encryption and appends either .____xratteamLucked and .one file extensions. The unique feature of the ransomware is that after infiltration it check the default language of the computer.
The ransom-demanding message does not inform how much Bitcoins victims have to transfer. However, some people claim that they were asked to pay 0.3 BTC. However, this piece of crypto-malware is poorly written, and users can recover their files for free after XPan removal.
Zixer2 ransomware variant of the Xorist uses Tiny Encryption Algorithm and appends .zixer2 file extension. Following data encryption, it delivers a ransom note in HOW TO DECRYPT FILES.TXT file. Here victims are asked to contact cybercriminals via datares@india.com email address.
It’s unknown how much money crooks ask in exchange for the decryption key. However, victims do not need to waste their time chatting with hackers. Once the malware is wiped out from the system, people can recover their files with Xorist Decrypter.
Imme ransomware is using XOR encryption algorithm and is appending .imme or .imme.teras.completecrypt file extensions to the target data. In the ransom note, hackers are demanding 2 Bitcoins which should be paid within 72 hours. However, the data recovery tool might not work. The threatening message also reveals a unique user’s ID that victims have to send supfiles@inbox.im or supfiles@gmx.com as soon as they pay the ransom. However, just like the other variants, this one is also decryptable.
Avastvirusinfo variant aims at Russian-speaking computer users. It appends .[8 random chars] extension to each of the targeted file after the encryption procedure and installs a ransom note called “КАК РАСШИФРОВАТЬ ФАЙЛЫ.txt,” Here crooks ask to contact them via avastvirusinfo@yandex.com and pay only $15.Nevertheless, the ransom is small; there’s no need to pay it because ransomware is decryptable for free.
Crypto1CoinBlocker malware uses RSA-2048 cryptography to encode files on the affected computer. When all data is encrypted, ransomware delivers a pop-up window with a ransom-demanding message. The same data recovery instructions are provided in the HOW TO DECRYPT FILES.txt file too.
Cybercriminals ask to transfer 1 Bitcoin to the provided wallet address. What is interesting, that Bitcoin wallet address is the same as the appended file extension – .1AcTiv7HDn82LmJHaUfqx9KGG55P9jCMyy. However, paying the ransom is not recommended. After Crypto1CoinBlocker removal, users are advised to try alternative recovery methods.
Hello cryptovirus emerged in August 2017. Malware spreads and is executed from the iji.exe file. Once this file is run on the system, it starts scanning the system and looking for the targeted files. To all of the encrypted data it appends .HELLO file extension.
The virus also delivers a pop-up window informing about encrypted data. What is more, it also installs a ransom note called HOW TO DECRYPT FILES.txt where victims are asked to transfer 0.05 BTC to the provided address. Users are given 12 hours to complete this task. After the deadline, the price will double. However, after 24 hours, corrupted files are said to be deleted.
Despite the reference to the notorious Cerber ransomware, the malware happens to be another version of Xorist virus. It is a common technique among cybercriminals to threaten users with more menacing virtual threats. On the other hand, this malware is still capable of encoding users' files, appending .cerber_RansomWare@qq.com extension and demanding ransom.
The malware is still under development, so it only presents demands in HOW_TO_DECRYPT.txt file. No specific sum of ransom is indicated. Users should not consider paying the ransom as they might make use of free Decrypter.
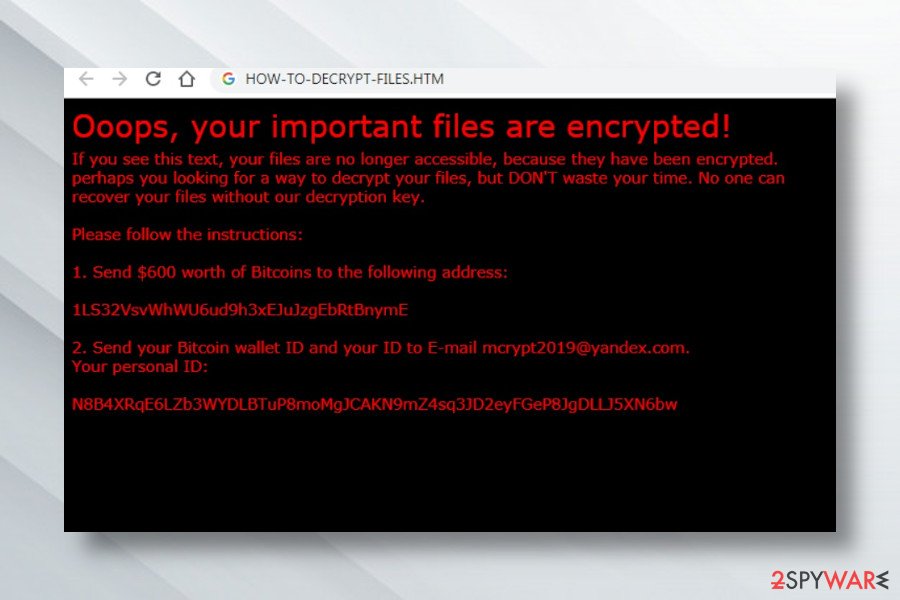
Cryptedx is one of Xorist's versions which has already been detected by 53 security software vendors as dawdawd.exe. Fortunately, just like previous its versions, it can be decrypted with the help of Emsisoft decrypter.
When infected, you can find that all of your files are inaccessible. Besides, their endings will be changed to .cryptedx file extension. In this case, you should ignore the warning message which is also dropped by malware developers, and remove Cryptedx ransomware from the system. Then, move on to files' recovery guide posted at the end of this description.
Xorist-Frozen version was detected at the beginning of February 2018. According to the latest reports, the ransomware is very similar to its predecessors. It uses XOR file encryption algorithm and creates a HOW TO DECRYPT FILES.txt ransom note. Currently, the file extension appended to the encrypted files is not known.
Frozen ransomware is asking 0.5 BTC ransom, which is currently equal to 3400 USD. Extortionists claim that all locked files will be removed from the server within 34 hours after the encryption.
In comparison to its predecessor's communication method, this version has switched from the SMS to email, so people who opt for a unique decryption code has to send a code to frozen_service_security@scryptmail.com. Based on the prevalence of the virus, it's oriented toward English-speaking countries.
Security experts haven't developed a decryptor. Therefore, there's only one way out – to remove the virus with a professional anti-virus and then try to decrypt data using the methods given at the end of this post.
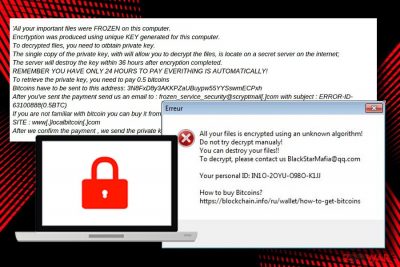
.XWZ Ransomware. XWZ was detected in the second half of March 2018 by a group of ransomware researchers. This variant uses XOR encryption algorithm to render personal victim's files useless. Xorist-XWZ virus is capable of attacking 111 file types. Upon successful unravel of ransomware payload, most of the files on the infected PC get a .xwz file extension. Besides, the virus manifests a ransom note in the form of a text file READ ME FOR DECRYPT.txt. The ransomware is oriented to English-speaking users since it's not translated into any other language:
All your files are encrypted using an unknown algorithm!
Do not try decrypt manualy!
You can destroy your files!!
To decrypt, please contact us BlackStarMafia@qq.com
Your personal ID: IN1O-2OYU-O98O-K1JJ
How to buy Bitcoins?
https://blockchain.info/ru/wallet/how-to-get-bitcoins
Just like its other versions, the virus circulates on the Internet with the help of various social engineering strategies. However, malspam campaigns are considered the most active techniques to promote this malware. It can attack PCs via unprotected RDP configuration, drive-by-download attacks, fake software updates, and similar stealthy methods. Unfortunately, a free Xorist-XWZ decryptor is not available.
In June 2018, another version appeared. The virus adds a long file extension to the targeted files:
.PAY_IN_MAXIM_24_HOURS_OR_ALL_YOUR_FILES_WILL_BE_PERMANENTLY_DELETED_PLEASE_BE_REZONABLE_you_have_only_1_single_chance_YOU_NEED_TO_PURCHASE_THE_DECRYPTOR_FROM_US_FAST_AND_URGENT
When all files are locked, it creates a ransom note called READ ME FOR DECRYPT.txt that contains the following information:
YOUR SYSTEM IS LOCKED AND ALL YOUR IMPORTANT DATA HAS BEEN ENCRYPTED.
DON'T WORRY YOUR FILES ARE SAFE.
TO RETURN TO NORMALLY YOU MUST BY THE CERBER DECRYPTOR PROGRAM.
PAYMENTS ARE ACCEPTED ONLY THROUGH THE BITCOIN NETWORK.
Furthermore, attackers provide instructions on how to make a transaction in Bitcoins and provide a specific wallet address where people have to send 0.8 BTC. They also leave a contact email address repair_data@scryptmail.com for those who need more information. However, it is not recommended to deal with these people.
LOCK Ransomware. According to researchers behind ID-Ransomware[5], the ransomware family members can add 73 different file extensions, so the list that we provided at the top of this article should be much longer. However, not all strains appear to be successful and persistent. Many variants were disabled without a single victim reached.
Just like its predecessors, it's based on the Encoder Builder and programmed to encrypt files using either XOR or TEA encryption algorithms. However, the Xorist LOCK ransomware exhibits a slightly different style of attack manifestation. Note that each virus based on Encoder Builder allows criminals to customize the ransom note, extensions, background image, and other traits.
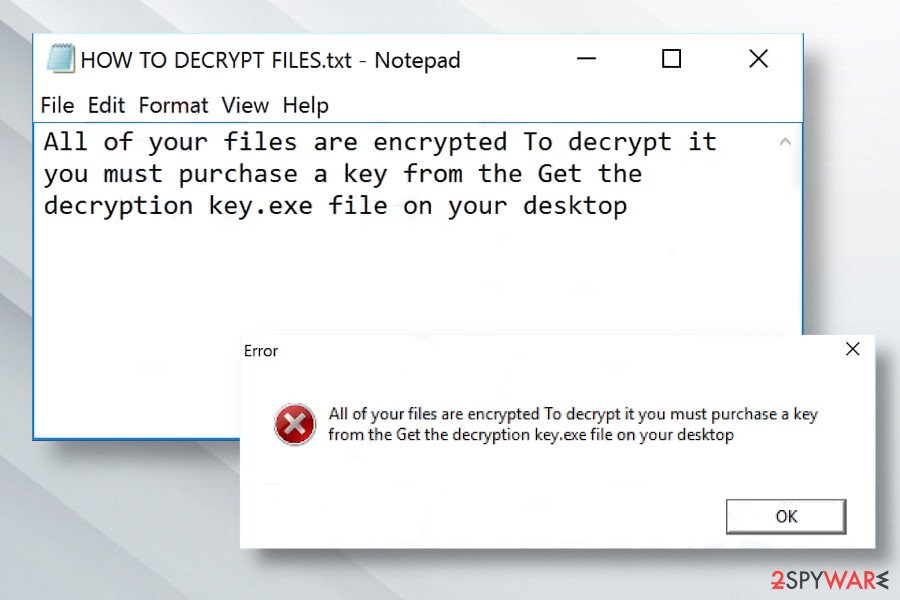
The LOCK ransomware payload is disguised under the decrypt0r.exe file. Once launched, it attacks most of the file extensions on the host machine and appends .LOCK appendix to each of them. The finish of the encryption process is marked by an error pop-up saying:
All of your files are encrypted To decrypt it you must purchase a key from the Get the decryption key.exe file on your desktop
Besides, it creates the HOW TO DECRYPT FILES.txt ransom note, which does not contain explicit information, except the following:
All of your files are encrypted To decrypt it you must purchase a key from the Get the decryption key key.exe file on your desktop
LOCK crypto-malware also changes the desktop background image. Note that this Xorist ransomware family member has been detected in April 2020, so it's decryptor is not available yet. The decryption software presented by Emsisoft in 2016 can restore files encrypted by earlier variants of this ransomware. Nevertheless, paying the ransom is not recommended anyway.
Experts advise victims to remove LOCK ransomware virus from the system asap. For this purpose, a professional anti-virus should be engaged and run while Windows booted in Safe Mode. After that, give a try for the official decryption software or alternative data recovery tools.
Following cybersecurity tips to prevent a ransomware attack
Cybercriminals have been using various techniques to spread this virus, such as malicious spam emails, malvertising, fake or illegal downloads, etc. However, by following a few simple rules, you can reduce the risk of getting a computer virus.
- First of all, never open emails that come from unknown senders. In addition to that, avoid reading emails that fall into the “Spam” category. Sending viruses and trojans via email is one of the most popular ways to distribute malicious computer viruses.[6]
- Do not click on suspicious content while you browse the Internet. If you see doubtfully reliable ads or banners that claim you have won millions or that you are the lucky visitor, ignore them. Such ads are deceptive.
- Download files only from trustworthy web sources. Besides, you should save them to your computer system instead of running/opening them immediately. It gives your computer security software some time to scan the file and test its reliability.
- Back up your files. It is a must! If you do not know why you should do that, please read this post – Why do I need backup and what options do I have for that?
- Protect your computer with trustworthy anti-spyware or anti-malware software.
Get rid of Xorist virus and recover your files without paying the ransom
Before you try to decrypt your files, you must remove Xorist ransomware from your computer. You can easily find all files that are related to this malware with the help of security software like SpyHunter 5Combo Cleaner or Malwarebytes. If you noticed that the virus blocks your attempts to start any of these programs to prevent its removal from the system, you should follow a detailed removal guide given below that is filled with two different methods that could help you unblock your remover.
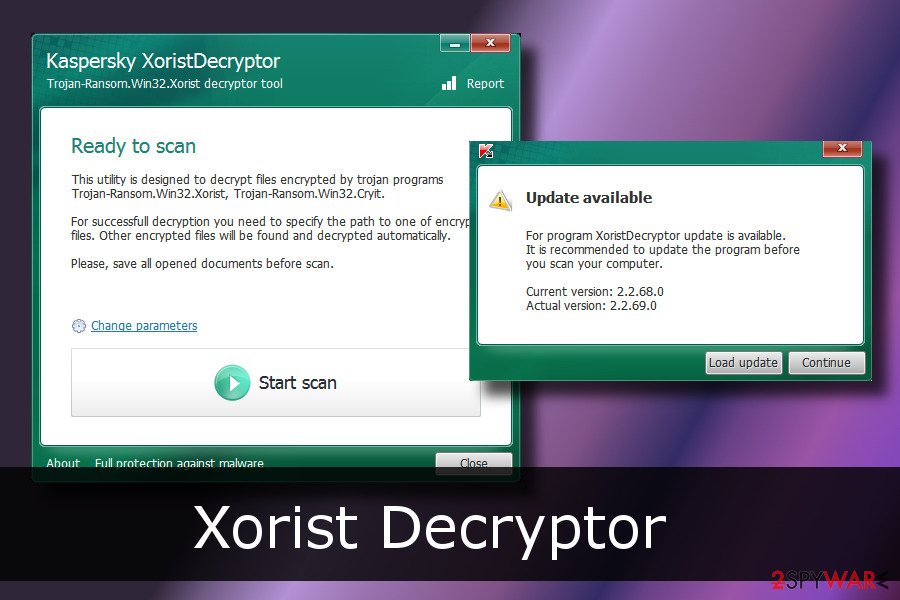
After Xorist removal, you can recover your files using the official decryption software or try alternative recovery methods. Links and a detailed explanation of how to use these tools are presented below. Before the data restoring though. Rely on system repair or optimization programs like FortectIntego, so files affected or damaged by the threat get repaired, fixed, or even replaced from the wide Windows file database.
Getting rid of Xorist virus. Follow these steps
Manual removal using Safe Mode
If you cannot run security software or malware blocks its installation, please follow these steps to disable the virus:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Xorist using System Restore
This method also helps to run automatic ransomware removal
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Xorist. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Xorist from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Xorist, you can use several methods to restore them:
Rely on Recovery tool to recover your files encrypted by the ransomware
Data Recovery Pro is a widely known tool to recover files that were lost. If you want to try it, follow the guide below:
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Xorist ransomware;
- Restore them.
Take advantage of Windows Previous versions feature
If System Restore has been enabled before ransomware attack and you need to recover only few files, you should take advantage of this Windows feature. It allows copying previously saved variants of encrypted files.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Recover files using ShadowExplorer
ShadowExplorer is an additional tool that helps to restore files from Shadow Volume Copies.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Use the decrypter presented by security experts to recover your encrypted files
Security experts from Emsisoft created Xorist decrypter. You can use this tool to unblock your files for free.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Xorist and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Lawrence Abrams. Emsisoft offering decryption services for the Xorist Ransomware Family. Bleeping Computer. Security news.
- ^ What is ransomware and how to remove it?. 2spyware. Security news and removal guides.
- ^ Kevin Haley. Don't Pay That Ransom: Fighting Ransomware In A New Threat Landscape. Symantec Official Blog.
- ^ SemVirus. SemiVirus. Portuguese website about computer viruses.
- ^ Xorist Ransomware (2016-2019). ID-Ransomware. Ransomware virus database.
- ^ How to identify your ransomware infection to find the right decrypter tool. Emsisoft security blog.





















